Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Inside the LockBit's Admin Panel Leak: Affiliates, Victims and Millions in Crypto
By Jambul Tologonov · June 12, 2025
Introduction
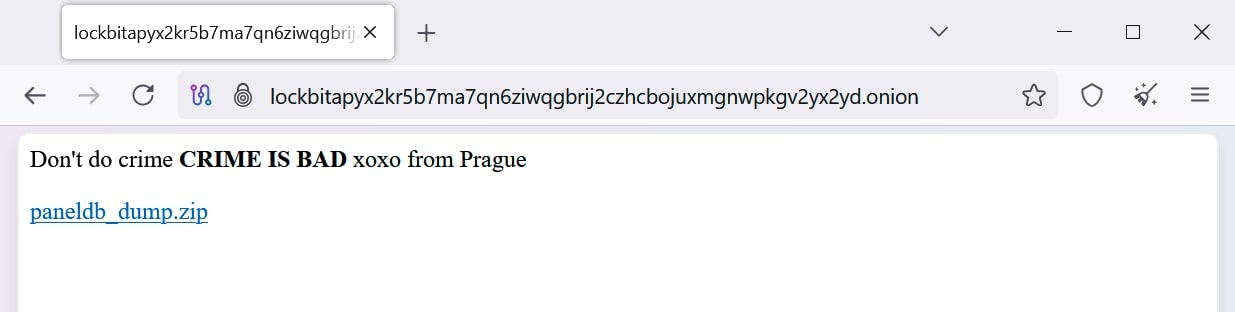
On May 7, 2025, the LockBit admin panel was hacked by an anonymous actor who replaced their TOR website with the text ‘Don’t do crime CRIME IS BAD xoxo from Prague’ and shared a SQL dump of their admin panel database in an archived file ‘paneldb_dump.zip’:
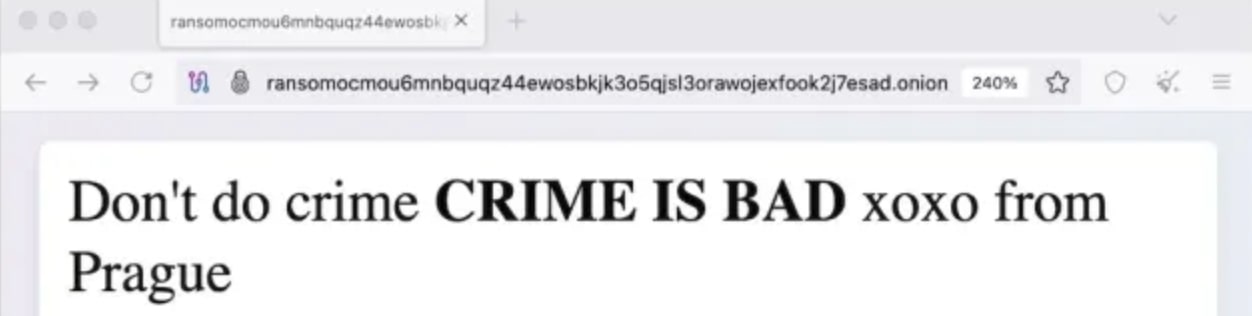
A month prior to that, a similar message was observed on the defaced Everest Ransomware as a Service (RaaS) TOR site:
There is not much information available regarding the individual identified as 'xoxo from Prague' whose objective seems to be the apprehension of malicious ransomware threat actors. It is uncommon for a major ransomware organization's website to be defaced; more so for its administrative panel to be compromised. This leaked SQL database dump is significant as it offers insight into the operational methods of LockBit affiliates and the negotiation tactics they employ to secure ransom payments from their victims.
Trellix Advanced Research Center’s investigations into the leaked SQL database confirmed with high confidence that the database originates from LockBit's affiliates admin panel. This panel allows the generation of ransomware builds for victims, utilizing LockBit Black 4.0 and LockBit Green 4.0, compatible with Linux, Windows and ESXi systems, and provides access to victim negotiation chats.
The leaked SQL database dump encompasses data from December 18, 2024 to April 29, 2025, including details pertaining to LockBit adverts (aka ransomware affiliates), victim organizations, chat logs, cryptocurrency wallets and ransomware build configurations.
Here is an overview of the database schema:
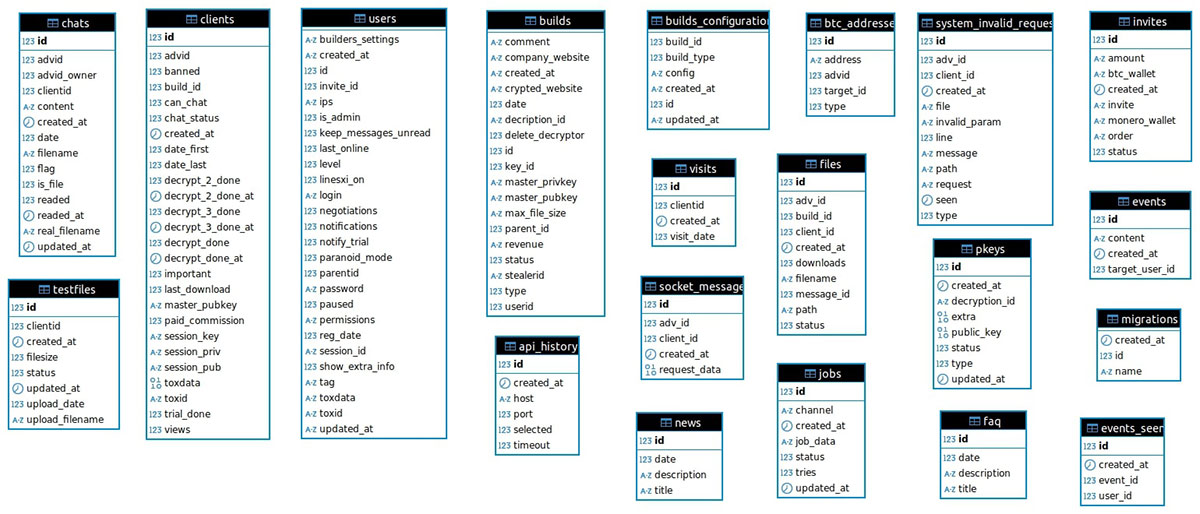
The absence of table constraints in the SQL dump initially raised concerns regarding the authenticity and integrity of the provided data, however, further analysis of the leak data demonstrated substantial intelligence and insights on LockBit’s adverts, victim organizations, negotiation tactics and earnings. The details of these findings are addressed in this blog.
Return of LockBit RaaS
Since the third phase of Operation Cronos on October 1, 2024, the Trellix Advanced Research Center has noted a decline in the operational tempo of the LockBit RaaS gang. This period of reduced activity persisted until December 19, 2024, at which time the group announced the release of their latest ransomware variant, namely LockBit 4.0:
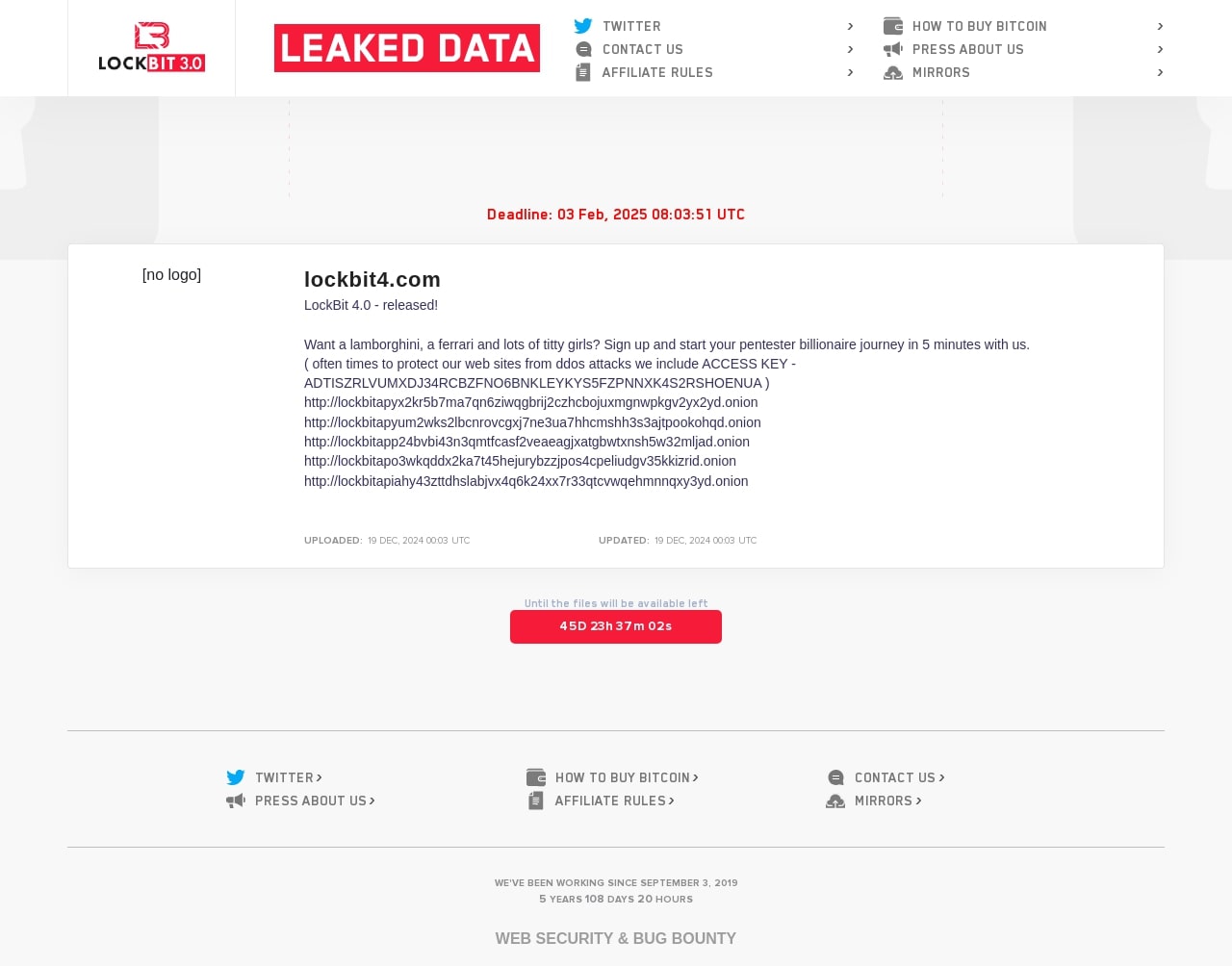
From the leaked admin panel logs, we discovered that around the same time LockBit set up their new affiliate panel they refer to as a ‘Lite’ panel. This panel features auto-registration functionality where LockBit decided to open up their admin panel to public and invite anyone who wants to work on their ‘targets’ (aka potential ransomware victim organizations) to join them for a small registration fee of $777 USD:
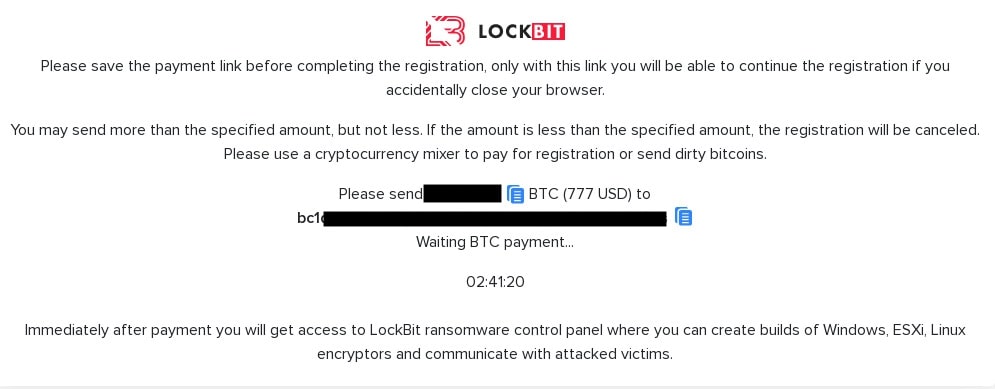
In early April 2025, Trellix observed heightened activity from the LockBit threat actor on underground forums, wherein they promoted a forthcoming update of their ransomware, LockBit 5.0:
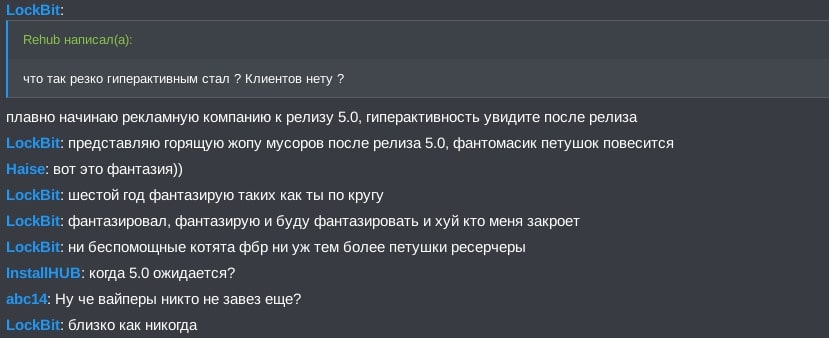
Translation of Figure 6:
Rehub: Why do you become so hyperactive suddenly? No clients?
LockBit: Gradually starting a PR campaign for the release 5.0, you will see the hyperactivity after the release
LockBit: I imagine the burning ass of the cops after the release 5.0
Haise: that is a fantasy))
LockBit: I'm fantasizing already 6 years I have seen people like you
LockBit: neither helpless kittens of FBI nor even roosters researchers
InstallHUB: when is 5.0 expected?
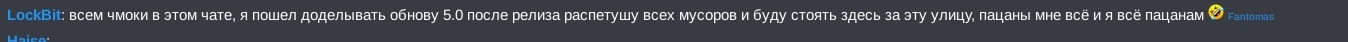
Translation of Figure 7:
LockBit: kisses to everyone in this chat, I'm off to finish the 5.0 update, after the release I'll sing the praises of all the cops and I will stand here for this street, the guys are all to me and I all to the guys
After the LockBit’s admin panel leak, LockBit informed that they were busy with ongoing efforts to develop LockBit 5.0. However, the influx of RansomHUB RaaS affiliates seeking alternative operations due to disruptions caused by FBI intervention necessitated an expedited operational reactivation before the finalization of update LockBit 5.0. The LockBit perpetrator advised that this decision to activate their operations without finishing the LockBit 5.0 was beneficial in identifying LockBit’s infrastructural weaknesses and reinforcing their operational strengths:
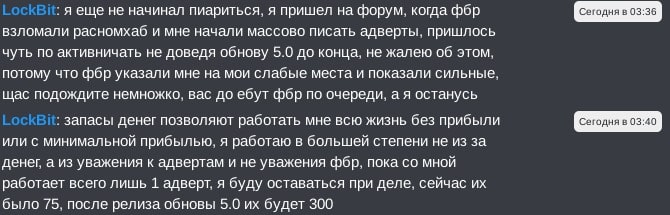
Translation of Figure 8:
LockBit: I haven't started PR yet, I came to the forum when the FBI hacked ransomhub and the adverts started writing to me en masse, I had to be a little more active without finishing the 5.0 update, I don't regret it, because the FBI pointed out my weak points and showed me my strong ones, now wait a little, the FBI will fuck you one by one, and I will stay
LockBit: my money reserves allow me to work all my life without profit or with minimal profit, I work mostly not for money, but out of respect for the adverts and disrespect for the FBI, as long as there is at least 1 advert working with me, I will stay in business, now there were 75 of them, after the release of update 5.0 there will be 300 of them
On underground forums, LockBit attempted to minimize the significance of their admin panel leak, stating that an investigation into the incident's cause is underway. They affirmed that decryption keys and stolen data remained secure, and both their full admin panel and blog remain operational. Furthermore, LockBit advised that all ransomware operations generating revenues exceeding $10 million USD are inherently vulnerable to hacking attempts:
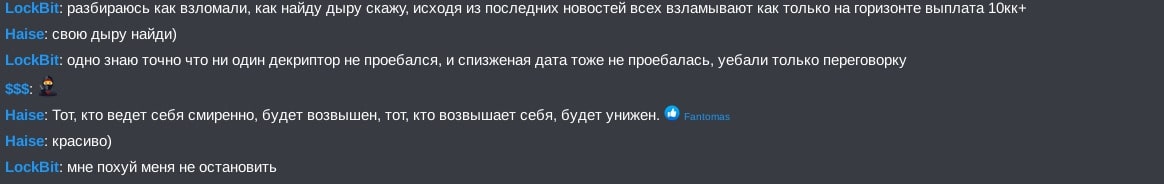
Translation of Figure 9:
LockBit: I'm figuring out how they hacked it, I'll tell you when I find a hole, based on the latest news, everyone gets hacked as soon as a 10kk+ payout is on the horizon
Haise: find your own hole)
LockBit: I know one thing for sure, not a single decryptor was fucked up, and the stolen date wasn't fucked up either, they only fucked up the chat room
$$$: :ninja:
Haise: One who behaves humbly will be exalted, one who exalts themselves, will be humbled.
Haise: beautiful)
LockBit: I dont give a fuck, I am unstoppable
LockBit asserted their invincibility and the continuation of their RaaS operations. They have subsequently announced a monetary reward for verifiable information related to the hacker known as ‘xoxo from Prague’:
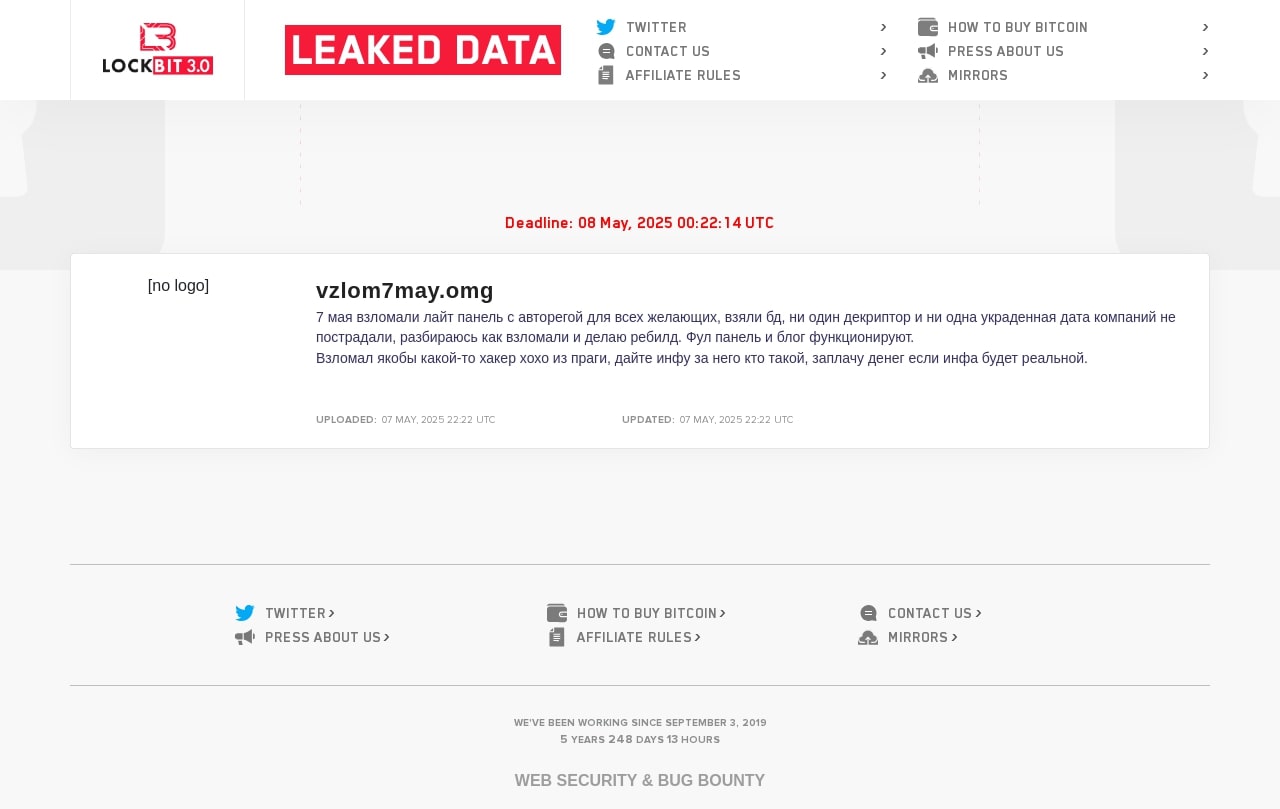
Translation of Figure 10:
On May 7, the Lite panel with auto-registration for everyone was breached, they took the DB, not a single decryptor or any stolen company data was affected. I’m figuring out how the breach occured and rebuilding. The full panel and blog are up and running.
The alleged hacker is someone named xoxo from Prague. I am willing to pay for any info related to him, but only if it’s real.
Trellix maintains continuous monitoring of the development surrounding LockBit's prospective version 5.0. To this point, no active PR activities pertaining to the forthcoming LockBit release 5.0 have yet been observed.
Analysis of the LockBit leaked data
The following sections will present significant findings derived from LockBit's leaked admin panel data. This analysis includes insights into attacks targeting Russian organizations, victimology patterns, affiliate details, negotiation strategies with targeted entities and the overall earnings of the LockBit ransomware operation.
Attacks on Russian entities
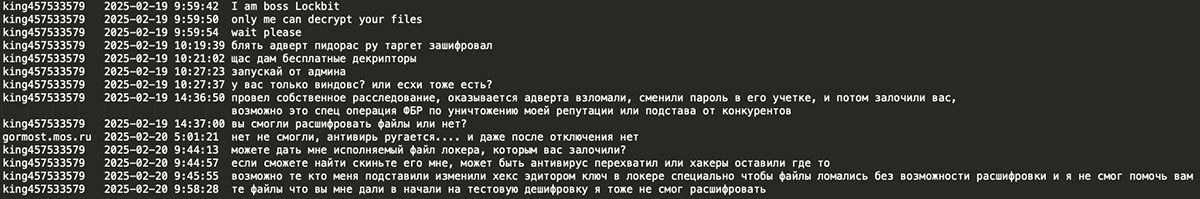
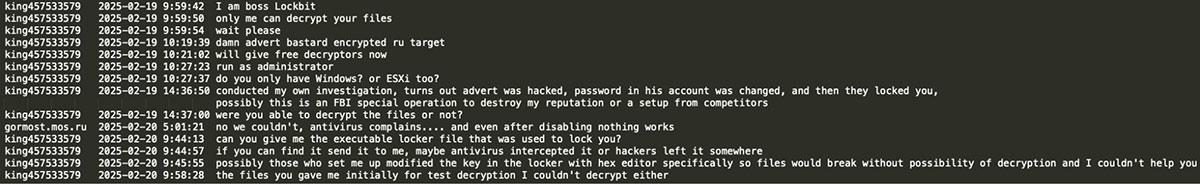
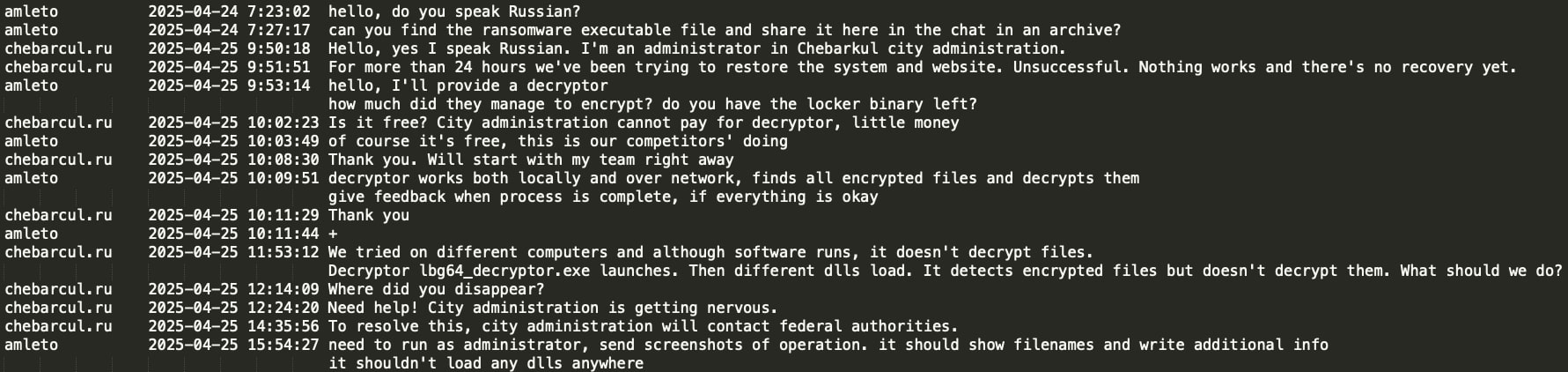
It appears that two LockBit adverts king457533579 and amleto encrypted two Russian government entities, namely the Department of Bridge Constructions of Moscow (gormost.mos.ru) and Municipality of Chebarcul (chebarcul.ru). In both of the cases, LockBit apologized and provided the decryptors for free saying ‘these are tricks and doings of our competitors’ or that the related advert’s account was hacked and their password changed, potentially indicating FBI’s operation to undermine LockBit’s reputation and set them up.It seems that in the case of gormost.mos.ru ransomware attack performed by king457533579, the victim organization was not able to decrypt the files and the LockBit operator himself, who took over the negotiation, advised ‘people who set me up changed the key in the locker using hex editor so that the file can't be decrypted and I could not help you out’:
In the case of chebarcul.ru, the victim was informed they would get the decryption for free, however the provided decryptor did not work and the municipality administration became nervous, saying to amleto ‘help us to recover, otherwise we will contact (Russian) Federal Authorities’:

This is not the first time LockBit ransomware has been used to attack Russian entities. In January 2024 when LockBit imposters attacked a Russian security company, AN-Security, LockBit stated that their competitors use a leaked builder to impersonate LockBit and inflict reputational damage to their ransomware program.
Victimology
Out of 156 unique clients mentioned in the leaked database, we identified 103 victim organizations who engaged in the negotiation with LockBit affiliates. Entities identified as potential victims where negotiation records were absent and only build generations were evident were excluded from the analysis. Similarly, test cases involving affiliate/developer panel assessments as well as instances of third-party organization experimentation, such as vx-underground assessing LockBit admin panel and generating LockBit 4.0 ransomware builds, were also excluded.
Futhermore, out of 103 victim organizations, 12 were victims whose company names appeared on LockBit’s leak blog and one appeared on RansomHUB’s data leak site between the period of January 14, 2025 and May 9, 2025 (even two days after the LockBit’s admin panel leak), authenticating of the dataset analyzed.
Based on the given ‘company_website’ and ‘comment’ fields in the ‘builds_configurations’ table, we attempted to identify the affected victim organizations and where possible to enrich the dataset with the victim organization’s sector/industry as well as their geographic location. The subsequent analysis will focus on the five foremost victim sectors and countries targeted by LockBit ransomware.
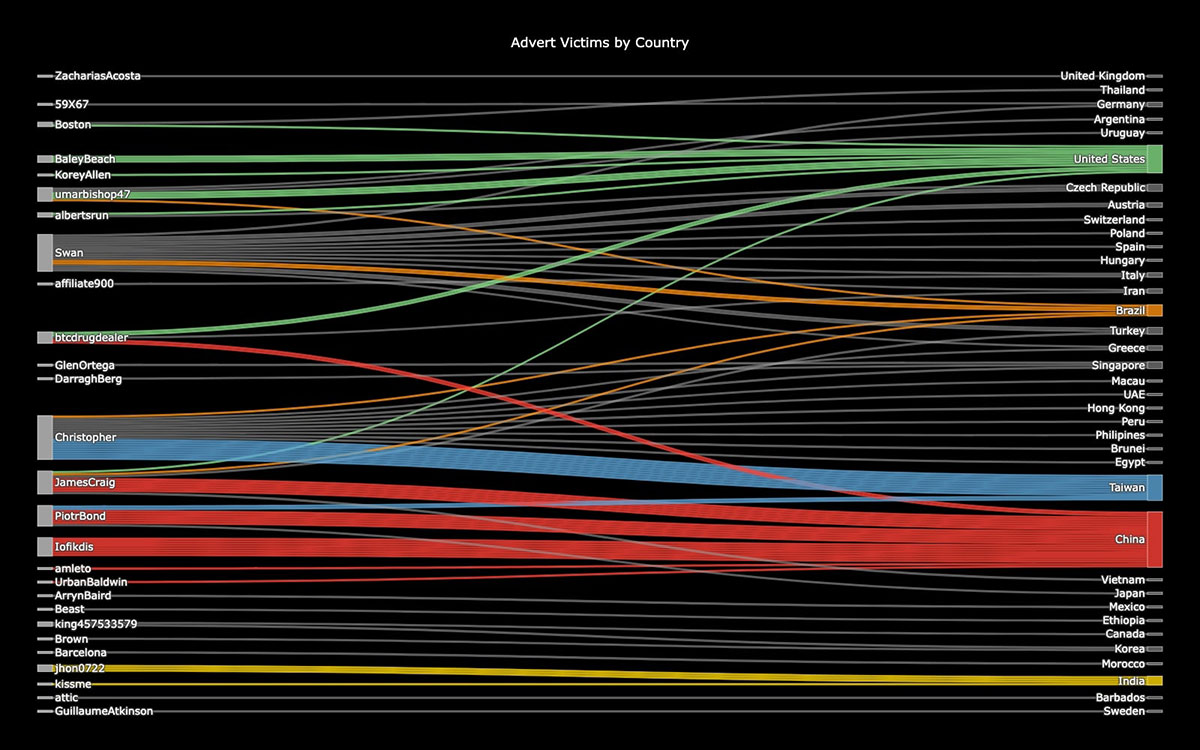
Our analysis of LockBit's geographic targeting from December 2024 to April 2025 reveals China as the most heavily targeted country, with multiple affiliates including Iofikdis, PiotrBond and JamesCraig conducting numerous attacks on Chinese organizations. The concentration of attacks in China suggests a significant focus on this market, possibly due to its large industrial base and manufacturing sector. Unlike BlackBasta and Conti RaaS groups that occasionally probe Chinese targets without encrypting them, LockBit appears willing to operate within Chinese borders and disregard potential political consequences, marking an interesting divergence in their approach.
From the leak data, the United States emerges as the second most targeted nation, with diverse affiliates such as BaleyBeach, umarbishop47 and btcdrugdealer leading these operations. Notably, the attacks in the US appear more distributed across different affiliates, suggesting a more opportunistic approach rather than specialized targeting.
Taiwan stands out as the third most targeted country, with Christopher showing a particularly focused campaign with multiple consecutive attacks. This concentration by a single affiliate might indicate specialized knowledge of the region's networks or specific vulnerabilities being exploited.
Brazil and Turkey round out the top five target countries, with affiliates like Swan, Christopher and JamesCraig conducting operations in these regions. Interestingly, Swan demonstrates a broad geographic reach, targeting multiple European countries including Austria, Czech Republic and Switzerland, suggesting sophisticated capabilities in navigating different regulatory environments.
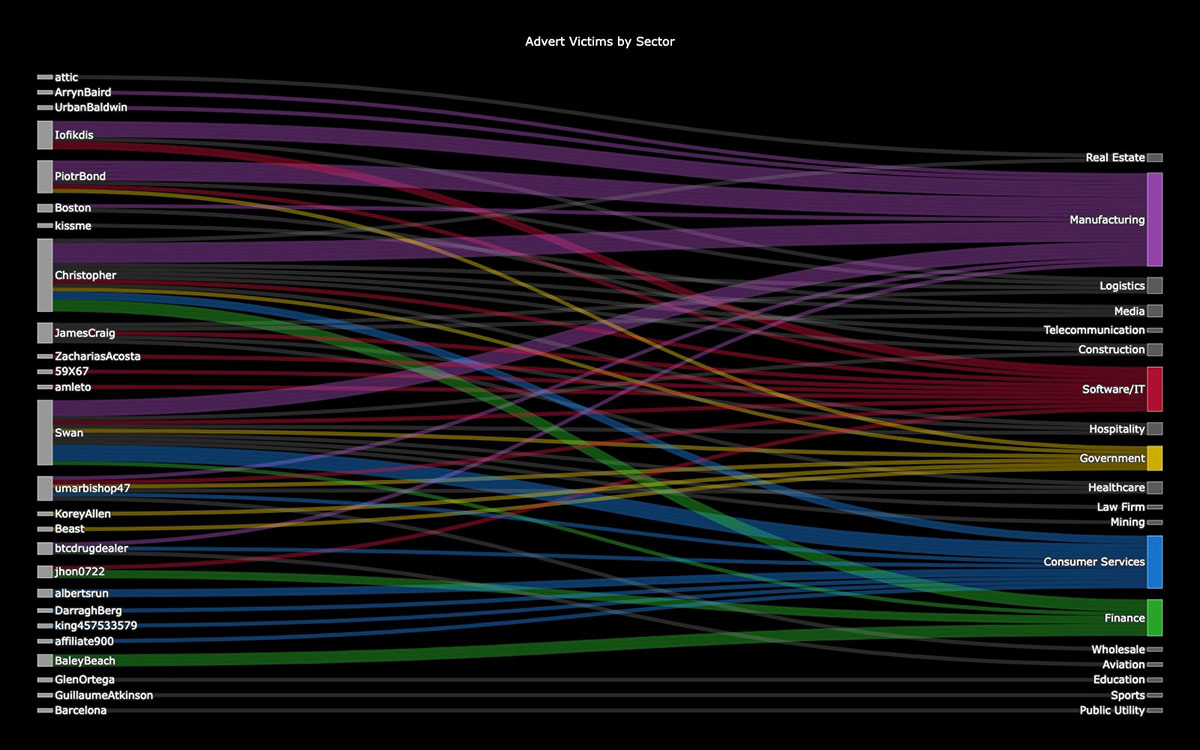
As can be seen in Figure 14, the manufacturing sector is the most frequently targeted sector, with affiliates like PiotrBond, Iofikdis and Swan showing particular interest in this industry. Manufacturing victims appear consistently throughout the leaked dataset, suggesting the sector's vulnerability or potentially higher likelihood of ransom payment.
Consumer Services emerges as the second most targeted sector, with multiple affiliates including Swan, Christopher and albertsrun conducting repeated ransomware attacks. The sector's prominence might be attributed to its broad attack surface and potentially valuable customer data to use in their data extortion campaigns. Software/IT represents another significant target, with affiliates like Iofikdis, ZachariasAcosta and amleto specifically focusing on tech companies.
Finance sector attacks, primarily conducted by BaleyBeach, Christopher and jhon0722, demonstrate LockBit's continued interest in high-value targets with critical time sensitivities. Government institutions conclude the top five most affected sectors, with umarbishop47, Beast and KoreyAllen leading these particularly bold attacks, showing LockBit's willingness to target government agencies despite increased scrutiny.
Prominent affiliates and connections to other RaaS gangs
An examination of the leaked database revealed that the ‘users’ table contained details for 75 affiliates, including cleartext passwords and their classifications as ‘newbies’, ‘pentesters’, ‘scammers’ or ‘verified’ adverts. 25 affiliates possessed TOX IDs, and five of them specifically Brown, btcdrugdealer, Christopher, JamesCraig and Swan were tagged as ‘verified.’ Through the analysis of ‘system invalid requests’ and ‘socket messages’ tables in the leaked SQL DB, an additional 46 potential login details and five TOX IDs of adverts were extracted (refer to Appendix A). Trellix attempted to enrich the total of 121 affiliates' details by correlating them with underground intelligence data and our findings and possible connections can be found under the ‘Extra info’ column of the table in Appendix A.
Most successful adverts
The analysis of LockBit affiliates reveals interesting patterns in ransomware operations. The most active affiliates (Christopher, Swan and JamesCraig) account for 37 victim organizations combined, representing a significant portion of the victim dataset. Success rates vary dramatically, from 9% to 100%, but notably, higher victim counts don't necessarily translate to better success rates. The most successful operators maintain a success rate between 17-50% when dealing with multiple victims. Initial ransom demands range from a few thousand to millions of dollars, with most affiliates offering substantial discounts (10-80%) during negotiations.
In the below table, we’ve summarized the most successful affiliates focusing on how much initial ransom they demand from the victim organization (typically 10% of their annual revenue), the discount the adverts offer during the negotiation as well as their success rate of getting the final ransom payment.
NOTE: Some of the ransom amounts were given in BTC and not in USD. We analysed the historical BTC to USD conversion rates for the period of December 18, 2024 to April 29, 2025 and took the average rate of 1 BTC equal to $92,000 USD. Victims with no negotiation chats and/or ransom demands were discarded from the below analysis.
| Advert | # Victims | Success Rate | Company Revenue Range | Initial Ransom Range | Typical Discount | Final Payment Range |
| Christopher | 14 | 57% | $10M | $25K-120K | 16-67% | $12K-60K |
| Swan | 12 | 17% | $5M-45M | $20K-2M | 10-80% | $23K-2M |
| JamesCraig | 11 | 9% | $10K-3M | $2.8K-276K | 33-67% | $1.5K |
| Iofikdis | 8 | 13% | $5M-108M | $8K-132K | 15-70% | $6K |
| PiotrBond | 7 | 29% | $5M-50M | $18.4K-73.6K | 15-25% | $3.3K-10K |
| umarbishop47 | 6 | 17% | $1M-15M | $50K-400K | 20% | $40K |
| btcdrugdealer | 5 | 20% | $10K-100K | $4K-69K | 20-50% | $2K |
| ArrynBaird | 3 | 33% | $1M-3M | $10K-50K | 30% | $10K |
| Brown | 2 | 50% | $10M | $4K | 10% | $3.6K |
| RiccardoBond | 1 | 100% | $10K | $4.6K | 10% | $4.1K |
Here are profiles of the two LockBit’s most active and successful affiliates:
Christopher (Most Successful High-Volume Operator):
- Geographic Focus: Strong presence in Asia (primarily Taiwan), with strategic operations in Greece, UAE and Philippines
- Sector Diversity: Manufacturing, Finance, Consumer Services and Hospitality
- Target Profile: Consistently targets $10 million USD revenue companies
- Ransom Strategy: Initial demands between $25,000-120,000 USD (relatively modest compared to company size)
- Negotiation Pattern: Aggressive discounting (16-67%), suggesting flexible negotiation tactics
- Success Rate: 57% - highest among major operators
- Key Insight: Success likely due to balanced ransom demands and willingness to negotiate, particularly effective in Asian markets
Swan (High-Volume, Lower Success):
- Geographic Focus: Diverse European presence (Switzerland, Austria, Germany) with some Middle Eastern operations
- Sector Diversity: Wide range - Software/IT, Government, Manufacturing, Consumer Services
- Target Profile: Broad range ($5-45 million USD revenue), including some government entities
- Ransom Strategy: Ambitious initial demands ($20,000-2 million USD), highest among all operators
- Negotiation Pattern: Wide discount range (10-80%), suggesting case-by-case approach
- Success Rate: 17% - moderate success despite high demands. It is noteworthy that Swan has the highest amount of ransom paid by a single company, $2 million USD (21.1 BTC)
- Key Insight: Lower success rate might be due to ambitious initial demands, but achieves high-value payments when successful
Above observations demonstrate successful LockBit ransomware affiliates typically align ransom amounts with the target company's size and focus on specific geographic regions or industry sectors, rather than broadly targeting diverse entities. This implies a calculated method for victim targeting to optimize the likelihood of ransom payment.
RansomHUB LockBit affiliates
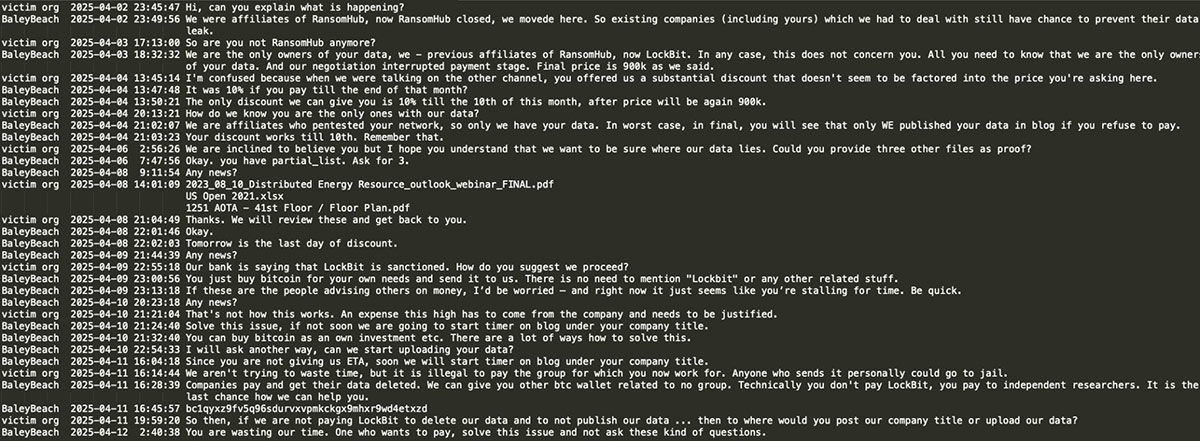
Following the discontinuation of the RansomHUB RaaSprogram in late March 2025, leaked data suggest that certain affiliates transitioned to the LockBit RaaS platform. In fact LockBit stated they reactivated operations primarily due to persistent inquiries from the affiliates. One of those affiliates is BaleyBeach who appears to have taken the RansomHUB RaaS victim to LockBit’s platform. As per the leaked negotiation chats, BaleyBeach, who had negotiation with a victim at the beginning of April 2025, advised them that ‘RansomHUB closed and they moved to LockBit ransomware’. Furthermore, BaleyBeach informed the victim organization that ‘All you need to know is that we are the only owners of your data. Technically you don't pay LockBit, you pay independent researchers’:
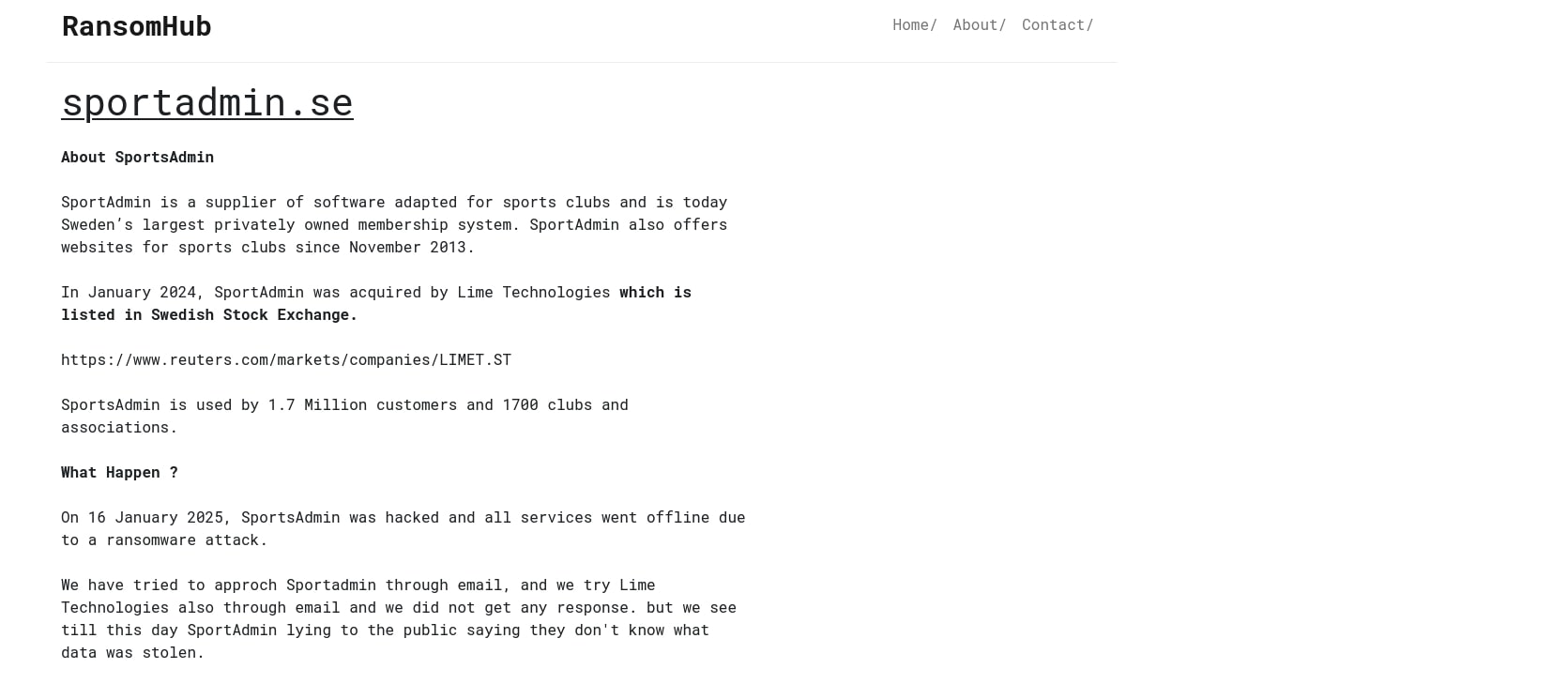
Another affiliate of RansomHUB is GuillaumeAtkinson who attempted to negotiate with a Swedish Sport company SportAdmin at sportadmin.se in mid-January 2025 when RansomHUB RaaS was still active. Although there are no chats available in the leaked LockBit data with the affected company, at the beginning of February 2025 the victim company was posted on the leak site of RansomHUB RaaS proving that GuillaumeAtkinson potentially collaborated with both LockBit and RansomHUB at the same time:
HellCat LockBit affiliates
It appears that the affiliate KoreyAllen works with both HellCat and LockBit ransomware gangs. On March 20, 2025 while chatting with a victim company, KoreyAllen wrote to them ‘LockBit & HellCat Encrypted your network, You 39 Day to negotiate’. HellCat ransomware first appeared in November 2024 and since then listed 20 victim organizations on their TOR leak site, including a large French energy company and a major US telecom provider.
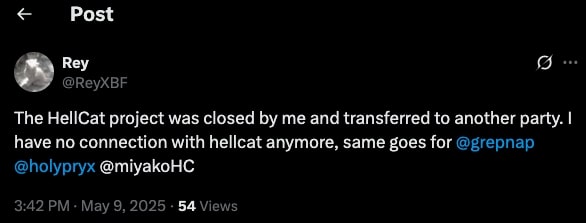
It is probable that KoreyAllen is connected to the moniker Rey who two days after the LockBit admin panel leak posted that the HellCat RaaS was closed and transferred to another party and they have no connection with HellCat ransomware anymore:
Evil Corp LockBit connection
On February 26, 2025, login attempts by two adverts, specifically Evilcorpfuckfishers and Evilcorpwatchyou were logged in the 'system invalid requests' table of the leaked database. These identifications, while potentially tangential, are noteworthy given the previously established connections between LockBit affiliates and Evil Corp as per the NCA Operation Cronos publication:
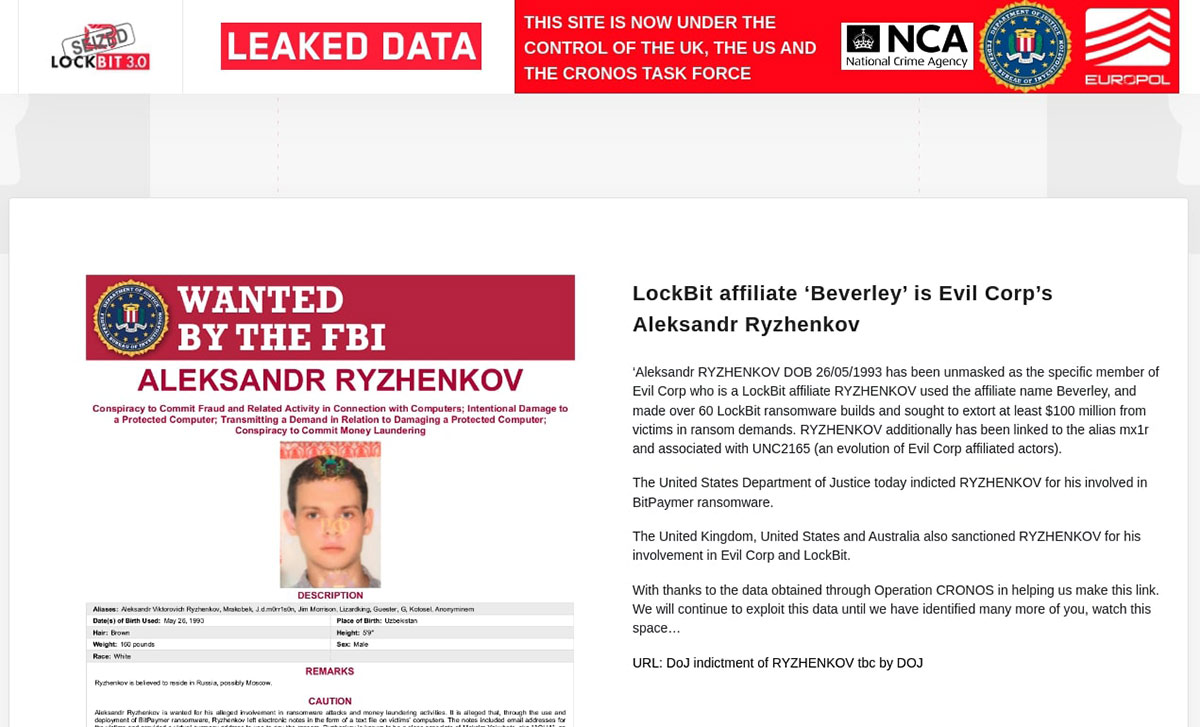
It is plausible that individuals associated with the Evil Corp cybercrime group still maintain an operational relationship with the LockBit RaaS group.
LockBit earnings
Earnings from victims
An analysis of LockBit negotiation chats revealed 18 confirmed payments to cryptocurrency wallets believed to be under the control of LockBit affiliates (see Appendix B). Based on a conversion rate of $92,000 USD per 1 BTC, our findings show that the estimated earnings of the LockBit ransomware operations between December 2024 and April 2025 are approximately 2,337,000 USD.
An analysis of the 'btc addresses' table, containing approximately 60,000 Bitcoin addresses, showed that only 19 addresses had transaction records. These 19 addresses appear to be cryptocurrency wallets under the control of the LockBit owner, designated for receiving 20% of ransom payments as per the LockBit RaaS affiliate rules. Notably, 18 of these addresses correlated with 18 confirmed ransom payments from victim organizations, each representing 20% of the final agreed ransom amount. The remaining transaction, involving $2 USD, was initiated by the affiliate Dezed941 potentially as a test transaction to a LockBit-controlled BTC wallet. Therefore, it can be inferred that the nearly 60,000 Bitcoin addresses were not the intended recipient BTC addresses for victim ransom payments. Instead, these BTC addresses were generated and assigned by the LockBit operator to affiliates for the purpose of remitting their 20% share of the negotiated ransom payment:
| Advert | Successful payment from victim | Advert controlled payment wallet | LockBit share (20%) | LockBit controlled wallet |
| ArrynBaird | 10000 (0.95 BTC) | bc1q8gesucu6k8gcx8etu492744mkjcef2tajn05en | 0.01906015 TBC | bc1qat80jxvlng5gpt2er5ghz42zrd4f3dv36zh5yd |
| Brown | 3600 (0.037 BTC) | bc1qgcfd2evmz4u0fyx3xsv7yft0p9fts06dunc0ec | 0.007422 BTC | bc1q5979ns9zrhtq8j2znkf59ldmd4nxc4hamuq8ut |
| btcdrugdealer | 2000 (0.02 BTC) | bc1qqpqpy2u2wn3u6uhja522zejpsmm0kmw5amg7n5 | 0.00465493 BTC | bc1qkhmyzj4kswwhrkdrt3ww0v2cvqrzcgh2jvpt8q |
| Christopher | 50000 (0.51 BTC) | 1PKzZhK35fvszaHBdyAwHTRtEoJwjR1ocD | 0.104 BTC | bc1qmydvt6xz9rkw36yvw2qztgxexz8dp40pxgklhq |
| Christopher | 24000 (0.23 BTC) | 1BWbqn6xdFat3zLiaHPuFLqnZL7Q4obSKC | 0.04621 BTC | bc1q5xpf5anwuz75vhlc00g2ec6teu3zvud3axeqcw |
| Christopher | 40000 (0.47 BTC) | 1JTCt7wvKiBgT7rba5YZna8irfMvkacqFG | 0.09468 BTC | bc1q5xt7padm8nmytf8h048uaw6el2vdn0h8fj8ju4 |
| Christopher | 0.1567 BTC | 1KNAZRC9ogEEE9doTggQomaswUGygaNDhS | 0.03139 BTC | bc1qthvjqlelj2fkr8d6u06mq27je07j9hek2g0nj2 |
| Christopher | 12000 (0.145 BTC) | 14aVAxPaY22Nj4GpzChrJFWzoJyGSHi9az | 0.02901 BTC | bc1qkusslhuvaxjqcyvk8ql5uzgsx9ql5xsmmr5hfj |
| Christopher | 15000 (0.15 BTC) | 1LZCdUhTZexZoRdS55wTcK1tAZrs8p7384 | 0.03113 BTC | bc1qv4j45knlkeazg0n0ymv3e3rpcv4gc8qqmrhp20 |
| Christopher | 30000 (0.35 BTC) | 12ve4J9x4GYh7iHUpZxrVvz7XqkVn7MAaG | 0.07192 BTC | bc1qh7lptqnm4zzpvrqxumwtup82qq4htnn2qentxd |
| Christopher | 60000 (0.6465 BTC) | 1PSg1u5WvoeJkzekTVJATzpS467NHG5Yyi | 0.1294 BTC | bc1qr0ynspq5aurj23xqw23uc5sd7xpw5qfy5y98ze |
| Iofikdis | 6000 (0.069 BTC) | bc1ql206uurcq4vfpcrz2exr057w4773q2yd2nlsn8 | 0.0138 BTC | bc1q9ks759pfsg7gmrl66qpke8qds4f76l5h822tz9 |
| JamesCraig | 0.017 BTC | bc1qje66jdnsxgz58fafp3kcrj86ap069yv8n52d2y | 0.0034 BTC | bc1q8mhmgckl7afmehe4vj7kmej2yxdj2rzft9juk6 |
| PiotrBond | 0.036 BTC | bc1q2wn37aax40gm0qc34j7qff5acq8k8wgwscv85c | 0.0072 BTC | bc1qszj958vn26yz0pza7ftq9r5g3edfxayf58d32f |
| PiotrBond | 10000 (0.1172 BTC) | bc1qe7zlhpdjc75te4lgzfwyy3ygsnp6shdg9lrt97 | 0.02344 BTC | bc1q760tha4qcccvxvxkwvhtzdjpkdsmknr97sel3j |
| RiccardoBond | 0.045 BTC | bc1qewh7r5ytxq6dqrztz6nelleela4akttdn79ktm | ||
| Swan | 0.25 BTC | bc1qp3cl68v8nstaxpqgjaq50rxmvrzen7lwva0wsl | 0.05 BTC | bc1q8980rpzy9f6meq8hur75ept62aug6dfrxnlwc0 |
| Swan | 2000000 (21.1 BTC) | 4.2211 BTC | bc1q5tanumnzxuhk0vxkmaqvhqgnq6sf0855trrmjw | |
| umarbishop47 | 40000 (0.39 BTC) | bc1q6tqarpua79kwqr0u6np9ac4faqv5hz96rhl92v | 0.07191141 BTC | bc1qx3e4eslyzhclzr4y4yexw3jhyw5n4xe4vakgvt |
| Dezed941 | 0.00002 BTC (2 USD) | bc1qzyrrasx3cgjqme50jfu5kz0xjjheu8smy6del0 |
In total, the LockBit RaaS owner received approximately USD 456,000 in earnings derived from ransom payments. Notably, a substantial proportion of these earnings, nearly $390,000 USD (4.22 BTC), originated from a single victim of the advert Swan who made a ransom payment of $2,000,000 USD (21.1 BTC).
Earning from affiliate invites
The leaked LockBit admin panel database's 'invites' table contained 2,338 BTC and 1,335 Monero (XMR) wallet addresses. Everyone attempting auto-registration for LockBit’s admin panel access were assigned one of these wallets and required to pay a $777 USD fee. On the RAMP underground forum LockBit claimed to have earned approximately $100,000 USD in the last six months from these auto-registration invite fees alone:
Translation of Figure 19:
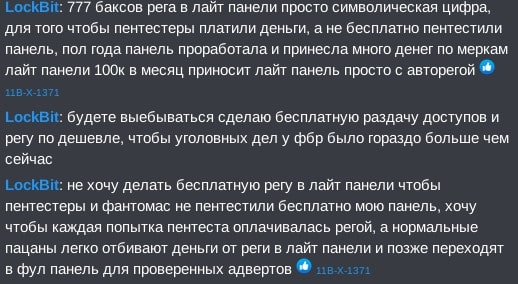
LockBit: $777 registration in the lite panel is just a symbolic figure, so that pentesters pay money, and not use the panel for free, the panel worked for half a year and brought in a lot of money by the standards of the lite panel, 100k per month brings the lite panel with just autoregistration
LockBit: if you annoy me, I will make free distribution of corp accesses and registration fee at a lower price, so that the FBI has many more criminal cases than now
LockBit: I do not want to make free registration in the lite panel so that pentesters and Fantomas do not pentest my panel for free, I want each attempt at pentesting to be paid for by registration, and normal guys easily beat off money from registration in the lite panel and later move to the full panel for verified adverts
An investigation into associated BTC wallet addresses showed that only 12 of the 2,338 wallets exhibited one or two transactions wherein invitees remitted $777 USD to cryptocurrency addresses controlled by the LockBit operator. The remaining BTC wallets demonstrated no transactional activity. Consequently, it is deduced that LockBit accrued $9,324 USD from auto-registration based on Bitcoin wallet transactions, and a mere 0.5% of newly registered affiliates paid the required registration fee.
Due to the inherent privacy features of the Monero blockchain, transaction tracing across 1,335 XMR wallet addresses was not feasible. However, assuming an equivalent 0.5% adverts payment rate for Monero addresses, that would yield LockBit approximately seven XMR, equivalent to roughly $1,500 USD.
To sum it up, we believe LockBit's revenue derived from auto-registration invitations amounts to approximately $10,000-$11,000 USD over the preceding 5-6 months. The assertion made by LockBit on the RAMP underground forum, which claimed monthly earnings of $100,000 USD from auto-registration, is thus considered to be significantly exaggerated.
Furthermore, LockBit suggests that the ‘Lite’ admin panel featuring auto-registration is designated for lower-level affiliates, while verified adverts work with the full admin panel. Our analysis reveals that the Lite panel had verified affiliates who worked on high-value targets with similarly substantial payouts. Therefore we believe that the sole distinction between the Lite and full LockBit admin panels lies in the auto-registration feature of the LockBit Lite panel, which the LockBit operator implemented in an attempt to generate additional revenue by extending access to all parties. Our findings from the leaked database indicated that this strategy for augmented income was not particularly effective.
Conclusion
The LockBit admin panel leak offers a fascinating and unsettling glimpse into the inner workings of a major ransomware operation. Several aspects stand out. The victimology data reveals some unexpected targeting patterns. It's particularly surprising to see such a concentrated effort on Chinese and Taiwanese organizations. Unlike other ransomware groups that might shy away from such politically sensitive targets, LockBit appears to have operated with a different calculus.
Then there's the negotiation process employed by the affiliates. The data paints a picture of varying strategies, with initial ransom demands ranging from modest to exorbitant. What’s clear is that substantial discounts were the norm, often between 10% and 80%, highlighting the haggling that goes on behind the scenes of these cyber extortion attempts. Affiliate success within LockBit varied significantly, indicating differences in skill and potentially specialization in specific familiar industries and/or countries.
Finally, the question of earnings. According to our analysis of the leaked data, LockBit RaaS earned around $2,3 million USD within 5 months. However, LockBit’s claims of pulling in $100,000 USD a month only from auto-registration fees are clearly inflated. The reality, based on traceable transactions, is significantly lower, closer to $10,000-$11,000 USD over several months. This underscores a critical point: you can't trust cyber criminals, especially those engaged in ransomware. They will exaggerate their successes and downplay their failures. What this leak truly shows is the complex and ultimately less glamorous reality of their illicit ransomware activities. While profitable, it’s far from the perfectly orchestrated, massively lucrative operation they’d like the world to believe it is.
Appendices
Appendix A
Possible LockBit affiliates including their contact details and extra information:
| Login | TOX ID | Extra info |
| 200kk | ||
| 59X67 | ||
| AarronBarker | EB257D87D1032534673CE391699B9D46FDD4679119255D44D024DB3AEB7F980FD147601105F9 | |
| admin | A1A6D2ECC8DB18DA0D5F04C5ED01A565B5A46E4012FAE627ACCB5D709BB89477D26BE7EF852C | |
| affiliate900 | 97918B43754F3F7132F5FDD4322933CF3629E926625752ED4C59CA7A07D60E5F95D1AF90C275 | |
| albertsrun | areas of interests include penetration testing and security tools, VPS/hosting services | |
| amleto | attacked RU entity | |
| Anon666 (another handle Anon9543) | 2DE7695448BBDFFE795BEB7C76A3078BF3CF3A4FB793EF577A2472EE229DB174420137694FF6 | provided a malware-crypting service and offered to sell a tool to disable EDR |
| ArdalBlankenship | ||
| ArrynBaird | ||
| attic | ||
| Attik | ||
| BaleyBeach | RansomHub affiliate | |
| Barcelona | ||
| Beast | 6F1C08C24D9EB6579B81BAB005C4D65B918F578A13D287E8489D538C530F1913F5DE30A1A8F4 | |
| blvckcat777 | ||
| blvcksalvatore777 | 33E61B8E5DADFFFA0EAD998F3B717197E637686BF72751E4929244D34D2F1D57855A82A4FEA3 | |
| Boston | ||
| BrannanBlevins | ||
| BroganAlbert | ||
| Brown | ||
| btcdrugdealer | 367593D80D2DE9D5C75F2F0EF6A1806D3A253AE04C59CF07C673525814163F51C2481FAE3ED9, DAC09891C2D0140585D9D99B7FB74FA05F862F5D06E5B3440DA4EF3CA2708705E8BFC7C8D531 | |
| chachacha | ||
| checksum | ||
| chondou | ||
| Christopher | ||
| CraigJamesAlford | ||
| DamonBenton40 | ||
| DaoodBaker29 | ||
| DarraghBerg | ||
| Dezed941 | ||
| Dffxh | ||
| Did14455 | ||
| djokovic | ||
| eq45crdwb54cq6wbVR3rF | ||
| Evilcorpfuckfishers | possible Evil Corp related handle | |
| Evilcorpwatchyou | possible Evil Corp related handle | |
| ExtortionLord | 4DEBEB92B3A547C9F0E563CA015D725D76FE47C30E482B1C42C363D10394160D93AA54DB55A9 | Telegram - https://t.me/INFOcriminal Session - 05a194f2e66701b5e32fb6660638e4a5add8eccb7b087173e9d41c891769c74917 was seeking pentesters on XSS forum (moniker flex) |
| fathfas11 | FAC33EB92F7B3D6A492E0DB8EDB5603ADA8AA23BFF8D7453C50B5B1FFE980C7E7B10A83E53C1 | |
| Fdgcsehcx | ||
| fedor | ||
| FezaanBlanchard | ||
| five | ||
| foster911 | ||
| Frank | ||
| funnyman | ||
| FutbolFreak | ||
| gaac | ||
| getdataback | ||
| getdataback1 | 562CEC0AAA7CBFC010559CE6B3B605DB982E5715C7A739CA6CAF852C39C8E95627DB32CE881A | |
| getmoneylikeag1 | 3085B89A0C515D2FB124D645906F5D3DA5CB97CEBEA975959AE4F95302A04E1D14E41080A105 | alternative LockBit account |
| GlenOrtega | ||
| Godener | ||
| godsjp | ||
| GuillaumeAtkinson | RansomHub advert | |
| hai | ||
| hastalamuerte18 | 6ACF76AA3F654F6687E5E42F5B1BAEC658F45CEE18EA41D5D5DE97A320EDB0340F8EF6758C0B | seeking pentesters to conduct ransomware intrusion attacks |
| hellomtl | ||
| hnurennusbfdejkjkjbJKBDSh | ||
| Hubbabubba | ||
| Iofikdis | 45ED5E7266A1730889345AC9424631AB996866D1AF22150E1E21BD06222BCA4962E329DDEBC8 | |
| Jackson | ||
| JamesCraig | ||
| JamesEdwards | A16F9CFED87FBBC8BF81453E7D44FF8C5E22D76A6F914A920BD4CDD79E82FA693F90484C5F2E | |
| jhon0722 | ||
| Jo2ieveaKu | EABCD0CEB534AB015EAB8CF408C1B5A2DA3DC93001C713C708581B41E9AE4162700AB5C2346B | |
| KeaynBaker | ||
| KianJamesBarr | 1239C42428A21EBB55ECBDDFB0B69AFA8EECD0CC69AEC9EA46881CBAAB3D3D0D18E6D979D182 | Selling RDP Access on XSS (moniker AtomikBot) |
| Kinetik12 | 1239C42428A21EBB55ECBDDFB0B69AFA8EECD0CC69AEC9EA46881CBAAB3D3D0D18E6D979D182 | |
| king | ||
| king457533579 | 4937B18F48CD5884C9124400D321B289E8EBAF68A1DF1920A7813CF2AEE37560D9DADC83BE9E | attacked RU entity, Jabber swarm@jabb.im |
| kissme | A51AB3331F4B2363C5BF6598582417B7F1AEC3C6F0757E0A0D5B265727DB1F0E6DFF2BA62C22 | |
| kkoman | ||
| KlyonShift | F3DBBCA3547CEF26EAB7892483A299A77CDC8D9961D1E9292E2AEE1CCAF7D33DCA512852CFF6 | |
| KoreyAllen | HellCat ransomware affiliate | |
| LoginUEWGVY232 | ||
| Lvckz | ||
| malestru | ||
| matrix777 | A1A6D2ECC8DB18DA0D5F04C5ED01A565B5A46E4012FAE627ACCB5D709BB89477D26BE7EF852C | alternative LockBit account |
| meandmeeverme | 5E52C57898476BDD1786D1BFA9B65092757207020FD125639C7A7D4637DD051DD69C37A03DAF | |
| MrSudo | E3F98E60A4A1F0F62389A1755ADB5F133475772D8F5B329B531B1CB0584F7A57A8F3390BBC29 | |
| Naebalosmotry | ||
| NancyOliver | ||
| NETWORKER | ||
| NorrieAllen | ||
| OranBarnes | ||
| OwenBender | ||
| ozymandias | ||
| pariknson | ||
| Phishingdesheviy | ||
| PiotrBond | ||
| pipokinha44 | ||
| RAFAELCASINOS | C55A0B3DC4C43953016D7F7D578F4A9B9132E3DAED9857BE5CFB9A59385D6271B6AD1AE6A8FF | |
| RafaelCousins | 34D6BCF2667831B5B643EC1AB2DE0B435F764F912AA88E785FFBBC6EADB4F812B9C76B70EC9E | |
| RamsayBowers | ||
| Recardo | ||
| reycorp | ||
| reycorps | 532C6724242C8501335270FEC9BE94A4826CDC821745914D033F1BA2E050B127E8646FD69D2D | |
| RiccardoBond | 99C252A1E1A9CA7442408A3FD11C1CF0F1D1A8A64CE03BC8BED4F21D77F89E4E20A2AE35E09A | |
| RoenBates | ||
| Rooky | ||
| Rueransomware | ||
| Sidim | ||
| sidim12 | ||
| Sidim122 | ||
| Sidim244 | ||
| silly123 | ||
| SIUfk23 | 90FD27C39BFB0DC44AE8E87B0CA5E347E23444933DBA4E1E133C6E731F3764016B45EAF83EB7 | |
| smelly | ||
| Sterb | ||
| succulent | possibly RAMP actor/IAB schwarze_puppen | |
| Swan | 3B5421CC5D6E70CE7AB8C08D3281476766F42B1D46CA892AC5DF6EB1BB1FCE323CF8E4837CDA | |
| TaneBates | ||
| umarbishop47 | ||
| UrbanBaldwin | ||
| VinnieBaker | might be the same as revealed by NCA affiliates list: Vinnie | |
| white | ||
| wlteaml | 3DCE1C43491FC92EA7010322040B254FDD2731001C2DDC2B9E819F0C946BDC3CD251FA3B694A | |
| xbetik | ||
| xorar | 32769B08C152ACE853EE48C9212C78F8B1D87A5BC688368E8667EBE81FC77740D6E6271A4946 | |
| ZachariasAcosta |
Appendix B
Victim payment details extracted from leaked negotiation chats where ransom amounts were explicitly specified:
| Advert | Companyrevenue | Victim country | Victim sector |
Initial ransom amount (default in USD ) | Discount provided (%) | Victim willing to pay (default in USD ) | Final negotiated amount paid (default in USD) |
| 59X67 | 57k | Germany | Software /IT |
110000 | 18% | ||
| affiliate900 | 3kk | Italy | Consumer Services | 90000 | 5000 | ||
| Anon666 | 4kk | 4000 | 5% | ||||
| Anon666 | 4kk | 4000 | |||||
| Anon666 | 4kk | 4000 | |||||
| Anon666 | 4kk | 4000 | |||||
| ArrynBaird | 1kk | 10000 | |||||
| ArrynBaird | 2kk | Mexico | Manufacturing | 10000 | 5000 | 10000 | |
| ArrynBaird | 3kk | 50000 | 30% | ||||
| BaleyBeach | 15kk | United States | Finance | 900000 | 10% | ||
| BaleyBeach | 13kk | United States | Finance | 400000 | |||
| BaleyBeach | 5kk | United States | Finance | 4500000 | 11.10% | ||
| Boston | 10kk | United States | Manufacturing | 40000 | 12.5% | ||
| Brown | 10kk | Korea | 4000 | 10% | 3600 | 3600 | |
| Brown | 10kk | 4000 | |||||
| btcdrugdealer | 10k | United States | Aviation | 0.75 BTC | |||
| btcdrugdealer | 15k | United States | Consumer Services | 4000 | 50% | 2000 | 2000 |
| btcdrugdealer | 100k | Iran | 30000 | ||||
| btcdrugdealer | 20k | China | Manufacturing | 10000 | 20% | ||
| btcdrugdealer | 20k | China | 12000 | ||||
| Christopher | 10kk | Philipines | Finance | 120000 | 66% | 40000 | 40000 |
| Christopher | 10kk | UAE | Real Estate | 50000 | 20% | 1000 | |
| Christopher | 10kk | Taiwan | Manufacturing | 40000 | 62.5% | 15000 | 15000 |
| Christopher | 10kk | Taiwan | Construction | 25000 | |||
| Christopher | 10kk | Taiwan | 30000 | 20000 | 24000 | ||
| Christopher | 10kk | Peru | Media | 50000 | 60% | 2000 | |
| Christopher | 10kk | Singapore | Finance | 120000 | |||
| Christopher | 10kk | Taiwan | Consumer Services | 90000 | 66.6% | 30000 | 30000 |
| Christopher | 10kk | Taiwan | Hospitality | 30000 | 16.6% | 5000 | 0.1567 BTC |
| Christopher | 10kk | Hong Kong | Telecommunication | 40000 | |||
| Christopher | 10kk | Taiwan | Manufacturing | 100000 | 30% | 60000 (0.6465 BTC) | |
| Christopher | 10kk | Taiwan | Manufacturing | 20000 | 40% | 10000 | 12000 |
| Christopher | 10kk | Greece | Finance | 80000 | 37.5% | 30000 | 50000 |
| Christopher | 10kk | Taiwan | Manufacturing | 50000 | 40% | ||
| GlenOrtega | 40kk | Singapore | Education | 500000 | 10% | 50000 | |
| Iofikdis | 60kk | China | Manufacturing | 18000 | 4000 | ||
| Iofikdis | 50kk | China | Manufacturing | 50000 | 70% | ||
| Iofikdis | 10kk | China | Manufacturing | 21000 | 15% | ||
| Iofikdis | 58kk | China | Software IT |
132000 | 62% | ||
| Iofikdis | 5kk | China | 21000 | 15% | |||
| Iofikdis | 108kk | China | Logistics | 100000 | 50% | ||
| Iofikdis | 5kk | China | Software IT |
15000 | 60% | 6000 | 6000 (0.069 BTC) |
| Iofikdis | 5kk | 8000 | 68.75% | 1500 | |||
| JamesCraig | 100k | Turkey | 2 BTC | ||||
| JamesCraig | 10k | United States | Software IT |
0.04 BTC | 57.5% | 0.012 BTC | 0.017 BTC |
| JamesCraig | 100k | 0.15 BTC | 33.3% | ||||
| JamesCraig | 100k | China | Hospitality | 0.2 BTC | |||
| JamesCraig | 100k | Brazil | Healthcare | 1 BTC | 50% | 1000 | |
| JamesCraig | 10k | China | 0.03 BTC | ||||
| JamesCraig | 100k | China | 0.3 BTC | 66.70% | 0.1 BTC | ||
| JamesCraig | 10k | China | 6000 | ||||
| JamesCraig | 3kk | China | Logistics | 3 BTC | |||
| JamesCraig | 10k | Vietnam | Media | 0.05 BTC | |||
| JamesCraig | 10k | China | 0.1 BTC | ||||
| jhon0722 | 7kk | India | Finance | 150000 | 1200 | ||
| jhon0722 | 2226k | India | Software | 70000 | 55000 | ||
| king457533579 | 3kk | Canada | Consumer Services | 210000 | |||
| PiotrBond | 10kk | China | Logistics | 0.75 BTC | 10000 | 0.1172 BTC (10000) | |
| PiotrBond | 10kk | China | Manufacturing | 0.75 BTC | 15% | ||
| PiotrBond | 10kk | China | Manufacturing | 0.8 BTC | |||
| PiotrBond | 50kk | China | Manufacturing | 0.8 BTC | |||
| PiotrBond | 10kk | 0.33 BTC | |||||
| PiotrBond | 5kk | China | 0.2 BTC | 25% | 3000 | 0.036 BTC | |
| PiotrBond | 10kk | Japan | Manufacturing | 0.25 BTC | 10% | 0.225 BTC | |
| RiccardoBond | 10k | 0.05 BTC | 10% | 0.04 BTC | 0.045 BTC | ||
| Swan | 5kk | Austria | Law Firm | 50000 | 3000 | ||
| Swan | 45kk | Iran | Manufacturing | 5 BTC | |||
| Swan | 15kk | Turkey | Consumer Services | 500000 | |||
| Swan | 10kk | Switzerland | Software IT |
2000000 | 20% | 1540000 | 2000000 (21.1 BTC) |
| Swan | 5kk | Germany | Finance | 1 BTC | 0.16 BTC | ||
| Swan | 20kk | Brazil | Consumer Services | 100000 | 20000 | ||
| Swan | 5kk | Czech Republic | Manufacturing | 100000 | 80% | 6000 | |
| Swan | 5kk | Hungary | Manufacturing | 100000 | |||
| Swan | 13kk | Turkey | Mining | 4 BTC | 1 BTC | ||
| Swan | 5kk | Austria | Government | 20000 | 0.25 BTC | ||
| Swan | 5kk | Czech Republic | Consumer Services | 0.7 BTC | |||
| Swan | 5kk | Poland | Construction | 1.5 BTC | 10% | ||
| umarbishop47 | 1kk | Argentina | Government | 50000 | |||
| umarbishop47 | 1kk | Brazil | Manufacturing | 100000 | |||
| umarbishop47 | 15kk | United States | Consumer Services | 150000 | |||
| umarbishop47 | 5kk | United States | Software IT |
50000 | |||
| umarbishop47 | 5kk | 50000 | 20% | 30000 | 40000 | ||
| umarbishop47 | 9kk | United States | Healthcare | 400000 | 20000 | ||
| UrbanBaldwin | 52kk | China | Manufacturing | 175000 | |||
| ZachariasAcosta | 5kk | United Kingdom | Software IT |
1200000 | 8.3% | 100000 |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
