Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Growing Threat of Vishing: How Cybercriminals Are Using Multimedia to Target You
By Mark Joseph Marti and Sandra Pagkaliwagan · May 8, 2025

Introduction
Imagine being hacked through a phone call, and you can't even complain because you were the one who provided your sensitive information or credentials. This is hacking through social engineering, which is essentially hacking without using any malicious code.
That's vishing! Vishing, short for voice phishing, is a type of social engineering attack where cybercriminals use phone calls or voice messages to manipulate individuals into divulging sensitive information, such as passwords, credit card numbers, or other personal details.
In a typical vishing scenario, the attacker may claim that there is an urgent problem with your bank account, a prize you've won, or a technical issue that requires your immediate attention. The goal is to create a sense of urgency and pressure the victim into providing information quickly.
Common vishing techniques via email
- Vishing via email body: Often starts with an email that contains a message designed to manipulate the recipient into taking immediate action. In this type of scam, the email body typically includes a phone number that the scammer wants the victim to call.
- Vishing via PDF attachment: The attacker sends an email with a PDF attachment that contains a message claiming to be from a legitimate organization. The PDF file typically includes the scammer's phone number, making it appear like a legitimate contact for urgent matters.
- Vishing via image attachment: The victim receives an email containing an image file (such as a JPEG or PNG) that appears to be a legitimate document, notification, or official communication. Within the image, the scammer embeds their phone number, which they want the victim to call in response to the urgent situation presented in the email.
Common vishing techniques may have already been addressed by various antivirus programs. Email security tools are continuously updated to detect these techniques by recognizing known threats, suspicious patterns, and abnormal behaviors.
Vishing traits
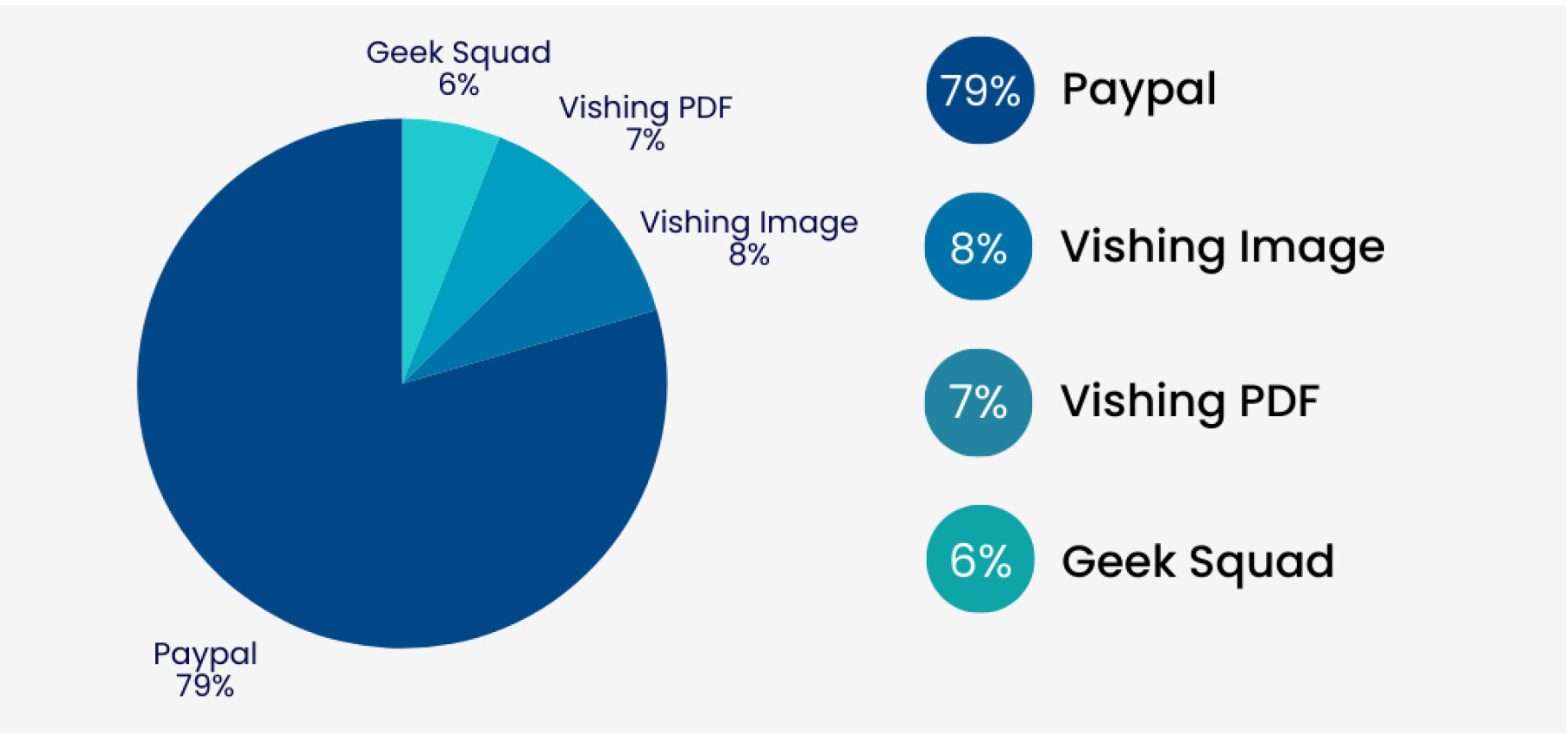
Based on Trellix’s telemetry data, “PayPal” was the most commonly detected vishing trait. PayPal is a frequent trait in vishing scams because it handles sensitive financial information and facilitates online transactions, making it a lucrative focus for scammers. Additionally, the ease of accessing PayPal accounts through phone calls, combined with the perceived legitimacy of a well-known company like PayPal, makes it a prime trait for vishing attempts.
Attack flow
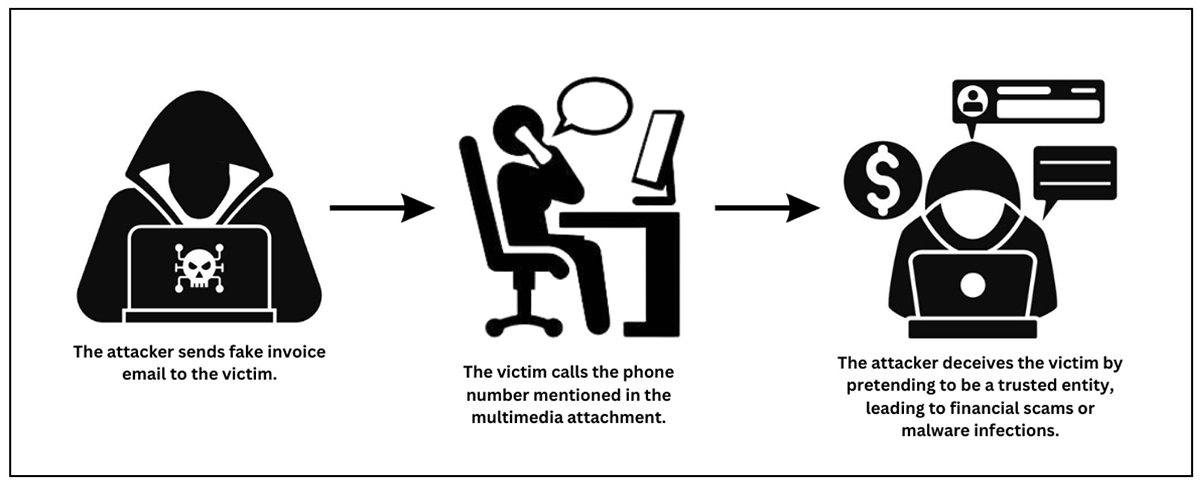
While vishing usually occurs over the phone, many scams begin with emails that entice victims to initiate a call. These emails often provide fake customer support numbers in the body of the email, through image attachments, or in PDF files, making them appear legitimate.
Once the victim dials the number, scammers pose as legitimate representatives and use social engineering tactics to create a sense of urgency. By instilling pressure, the scammer forces the victim to react quickly without carefully thinking, prompting them to provide sensitive information such as credit card details. After gathering the necessary information, the scammer immediately cuts off all communication. The victim may not realize the fraud until they notice unusual activity on their accounts, leading to financial inconvenience.
Vishing via MP4 attachment
A new vishing attack technique has been observed by the Trellix Advanced Research Center, which uses an MP4 file as an attachment to evade detection. This tactic is effective because MP4 files are often viewed as harmless media, causing security systems to be less vigilant in scanning them for malicious content. As a result, attackers can exploit this to bypass traditional detection methods.
The email is often sent from a freemail account which is commonly used by scammers because it’s free and difficult to trace. The content in the email body is typically minimal, often consisting of vague or generic text that doesn’t provide many details, but usually carries a finance-related theme.
The lack of detailed content in the body of the email serves a psychological purpose—it creates a sense of curiosity or urgency. The recipient may wonder why they received such an email or feel compelled to open the attachment to understand the situation better. Scammers rely on this curiosity, knowing that the fewer details they provide in the email, the more likely the victim will feel compelled to take action immediately.
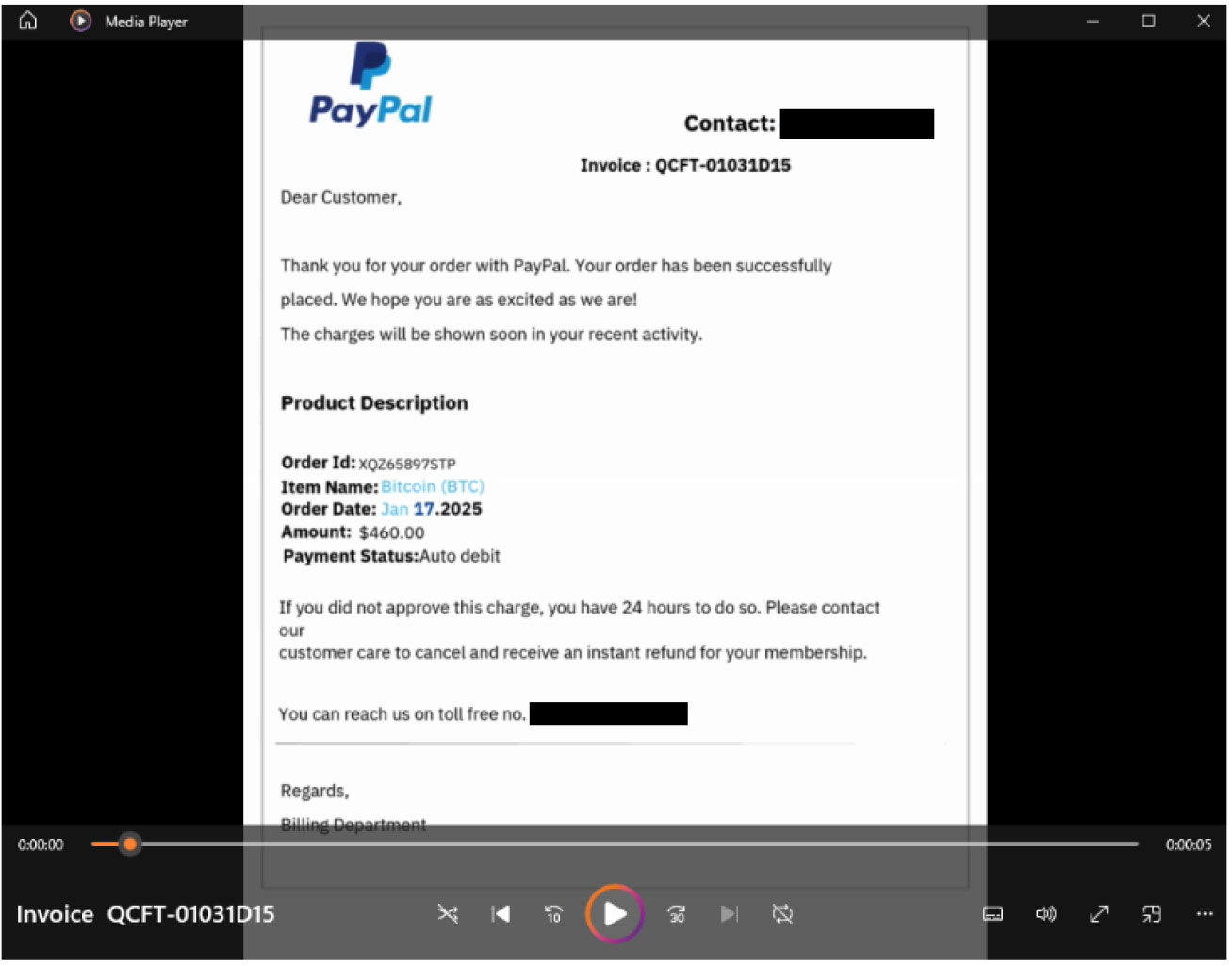
The MP4 attachment, once opened, contains typical vishing content that encourages the user to contact the provided number. This technique is new and marks the first time it has been observed in vishing emails.
Vishing via WebP attachment
Another new vishing attack technique has been observed, which uses a WebP file as an attachment to evade detection. WebP is an image file format that's designed to make images smaller and load faster on the web. The tactic takes advantage of the fact that WebP files are often considered benign by email filtering systems and security software, which typically do not scrutinize image file formats as closely as executable or script files. This tactic is particularly effective because, in most cases, WebP files are harmless and are used for displaying images, making them an ideal cover for malicious content. By exploiting the trust given to common image formats, cybercriminals increase the chances of a successful attack, as many users and automated systems overlook WebP files as potential threats.
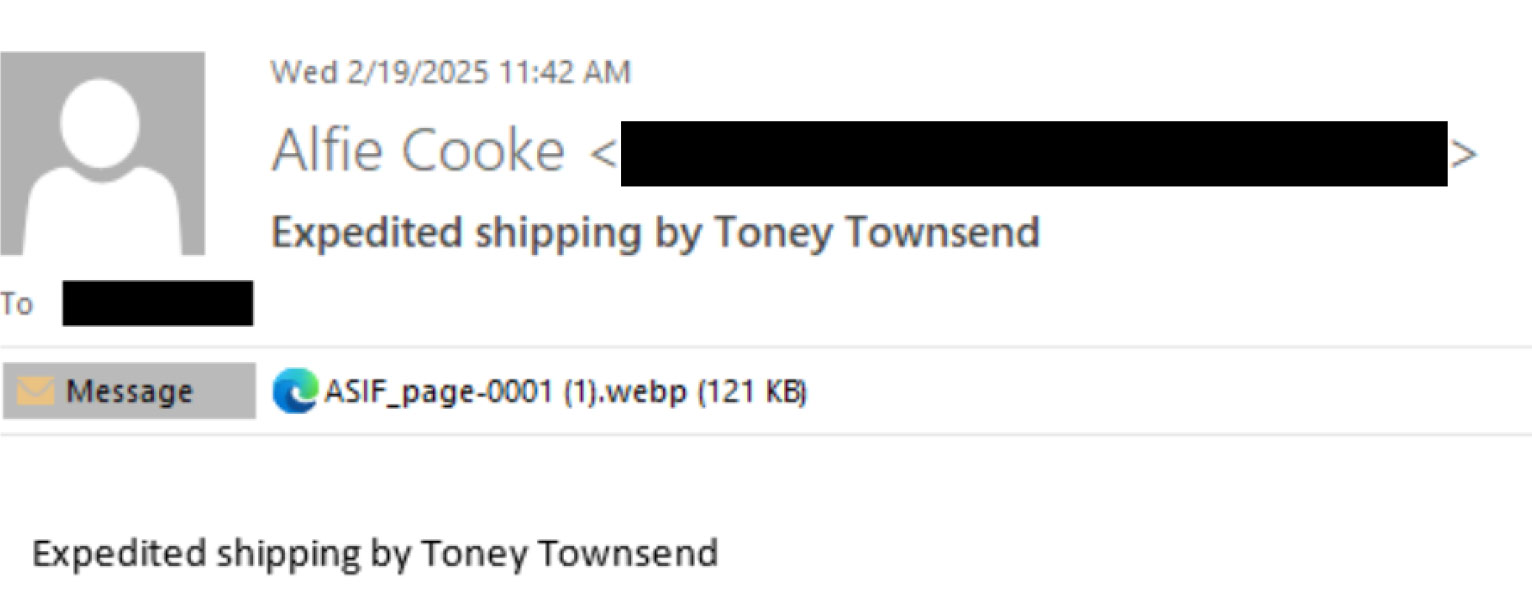
The email is also sent from a freemail account with minimal content in the body, but uses a shipping-related theme. This increases the chance that the victim will open the attachment out of curiosity or urgency.
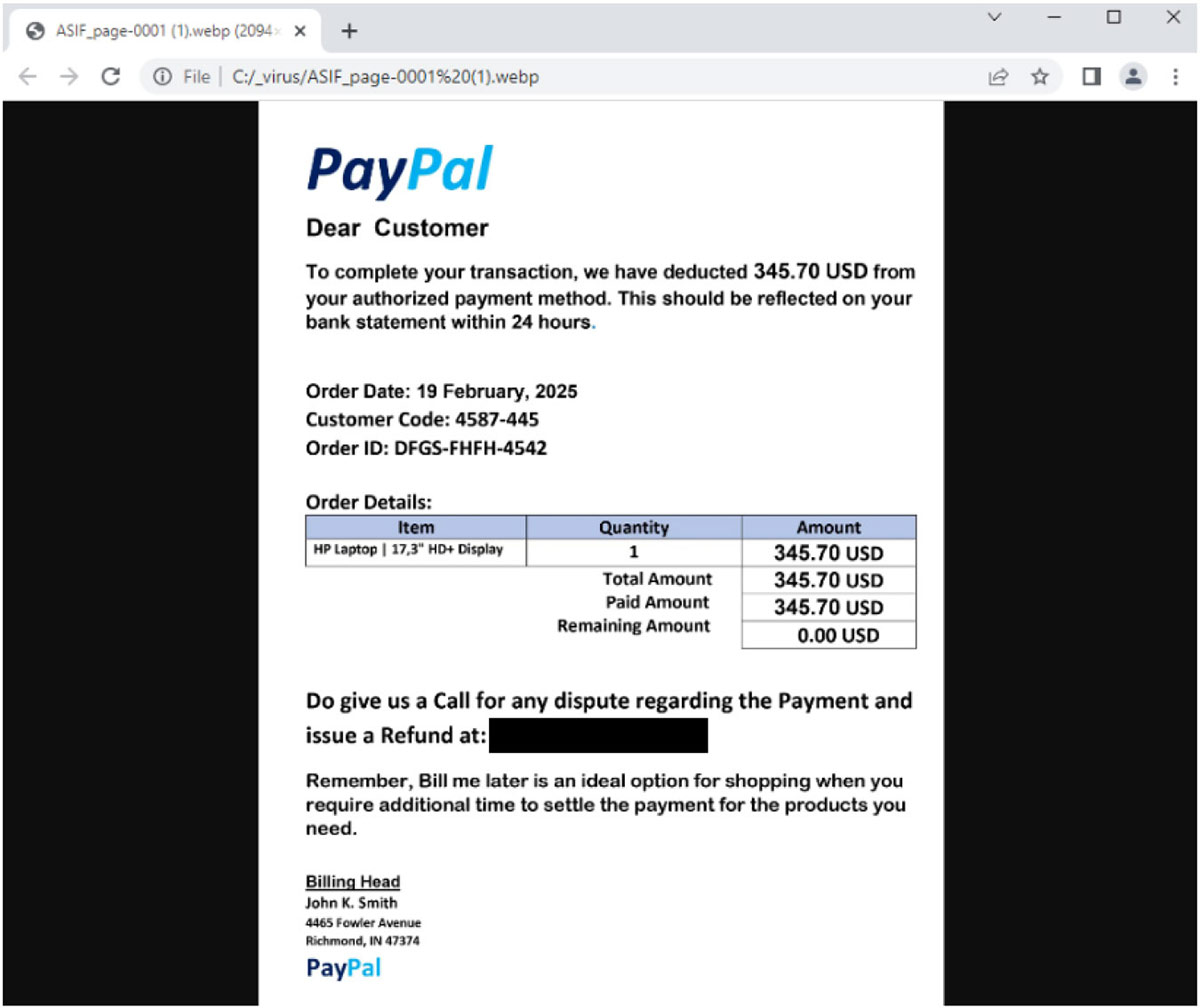
The WebP attachment, once opened, also contains typical vishing content that encourages the user to contact the provided number for any disputes or refunds. This technique is also new in vishing emails.
Conclusion
Vishing is a harmful form of social engineering that exploits trust and urgency. Scammers impersonate legitimate organizations, create urgency, and use misleading channels like phone calls and emails to steal sensitive information. These attacks rely on psychological manipulation, pressuring victims to act quickly without verification. To protect yourself, stay cautious, verify requests, and avoid sharing sensitive information over untrusted channels. Awareness and vigilance are key to avoiding vishing scams. Here are some red flags to help you spot a vishing email:
- One of the key red flags in these sample emails is the use of unfamiliar file attachments, such as MP4 and WEBP, which is highly unusual for legitimate communications. Most reputable companies do not send emails with such attachments for invoices. Instead, they typically provide invoices in PDF format or through secure online portals.
- MP4 and WEBP attachments contain invoices that may appear legitimate at first glance, but upon closer inspection, they reveal fake contact details designed to mislead recipients into calling a scammer. Additionally, there is a sense of urgency created to pressure the recipient into calling the number immediately to cancel the subscription within 24 hours.
- The use of free email services to impersonate trusted organizations is a common tactic. Scammers frequently rely on freemail services to disguise their identity and make their emails seem legitimate. Legitimate companies do not rely on free email services for official communication.
Trellix Product Coverage
Trellix Email Security provides reliable detection from vishing campaigns by preventing such emails from ever reaching your system. Our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats.
MITRE ATT&CK® Techniques
Trellix Protection
| Product | Signature |
| Email Security | EL_INVOICE_BTC EL_SUBJ_VIEW_INV_FREEMAIL EL_FREEMAIL_ORDER_MP4_ATTACH EL_FREEMAIL_WEBP_ATTACH EL_INV_WEBP_GAPI_REST EL_INVOICE_WEBP_FMAIL EL_INV_PDF_SCAM_2 |
Indicators of Compromise (IoCs)
| File Name | SHA256 |
| Invoice QCFT-01031D15.mp4 | 564474210b017fcad57c3ca3a9dd5fc130850ef01182d6dc745d5e2599354be9 |
| ASIF_page-0001 (1).webp | fa578d184cf5f23d2fc5ef9eee45febc4e168edaeef7b1ba13c33124786e57cb |
| TFYUH 9.webp | b38a51a1261994e57847d5efb0dca20ab3ec45ca362876054995b8fd6f095717 |
| 0rderConfirmation#023#WDH3O4M9M7.webp | 02999587ea5442f39ac8cda213ddd7a1c5a1c10a73068799f2d7ee171e381563 |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
