Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Cybercrime Takes Advantage of 2023 Recession with Job-Themed Scams
By Daksh Kapur · February 28, 2023

The current economic climate globally is grim because of the ongoing recession. In this environment, job-themed emails have become a prime target for cybercriminals looking to exploit vulnerable individuals.
Trellix Advanced Research Center has observed cybercriminals using phishing and malware campaigns to target job seekers in a bid to steal sensitive information. In phishing attacks, job seekers receive emails from fake companies or recruitment agencies, asking them to provide personal information or login credentials. These emails look legitimate but are designed to steal sensitive information such as passwords or financial information. In malware campaigns, job seekers receive malicious attachments or URLs to websites that infect their devices with malware or download malicious software. The malware can then be used to steal sensitive information or to gain unauthorized access to the job seeker's device and the information stored on it.
The attackers are also targeting employers by posing as job seekers to exploit them by delivering malware through attachments or URLs that are disguised as resumes or identification documents of the applicant. This type of attack is becoming increasingly common as cybercriminals take advantage of the high volume of job applications that employers receive.
The goal of these attacks is to gain unauthorized access to sensitive information, steal personal data, and disrupt the operation of the organization. In addition to that, we have also observed APT groups leveraging job-themed emails to deliver malware.
Trellix has also observed attacks utilizing fake or stolen documents, such as social security numbers and drivers licenses, to make job-themed emails appear more legitimate. By including fake or stolen documents, cybercriminals aim to increase the perceived credibility of the email, making it more likely that the recipient will fall for the scam.
Typo squatting domains
Typo squatting is a social engineering attack that purposely uses misspelled domains for malicious purposes.
Cybercriminals and even state sponsored groups are creating typo squatting domains of popular job websites to target job seekers. These domains are like the legitimate websites, but with slight variations such as misspelled words or different extensions. The purpose of these domains is to trick job seekers into thinking they are applying for a job through a legitimate website, when in fact they are providing their sensitive information to cybercriminals.
Our researchers have also noticed an increase in registration of new typo-squatted domains for jobs-related domains like LinkedIn, Indeed etc.
The following are some examples of typo-squatting domains observed by Trellix:
- indeed-id.com
- indeed-7.com
- indeed-a.com
- indeed.ch
- indedd.com
- linkhedin.com
- linkegin.com
- linkednn.com
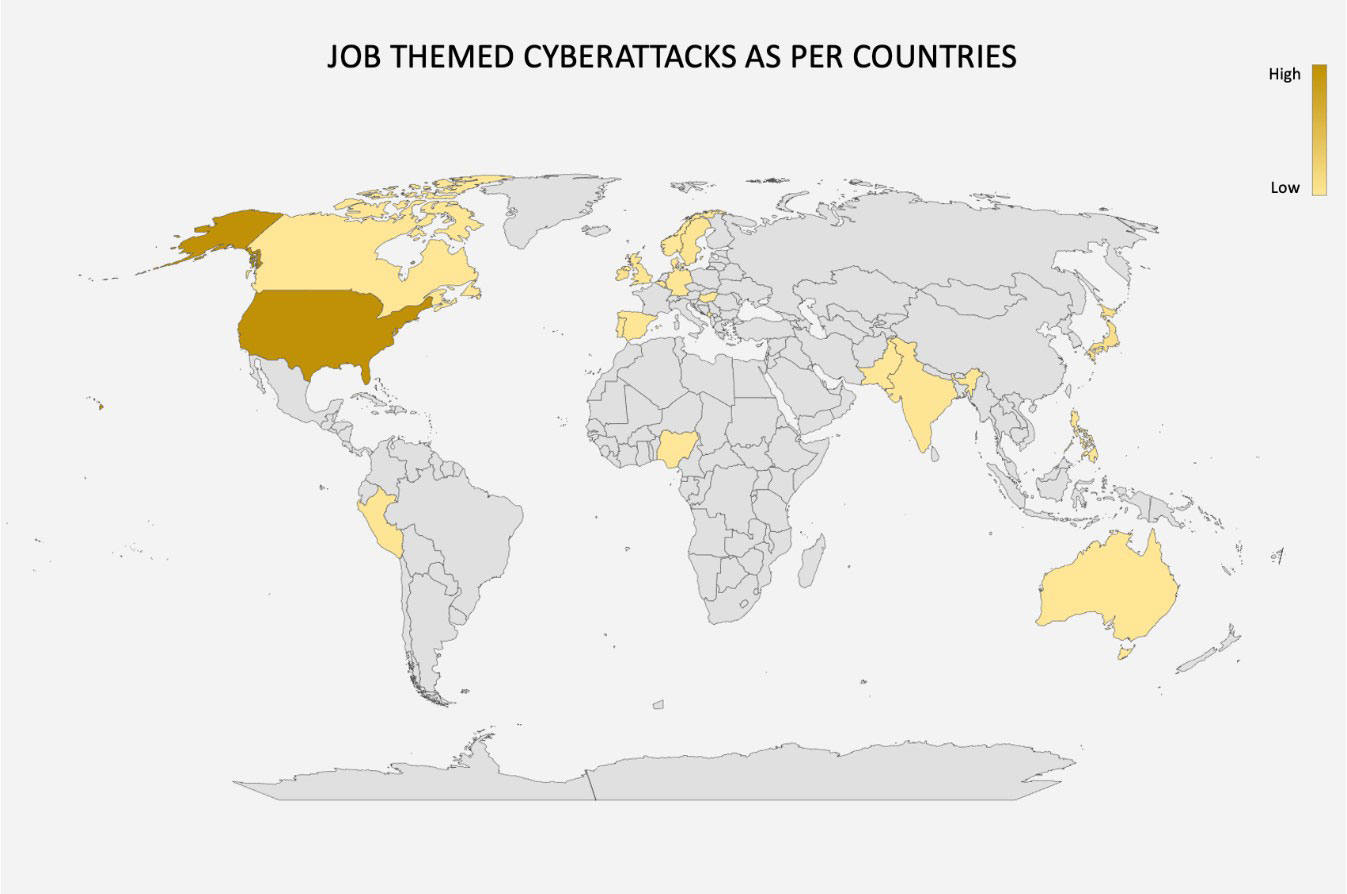
Our researchers have observed that more than 70% of all job themed cyberattacks were targeted towards the United States. The attacks were also observed in other countries like Japan, Ireland, United Kingdom, Sweden, Peru, India, Philippines, Germany to name a few, even though the percentage of attacks towards other countries were significantly lower than the United States.
Malicious emails
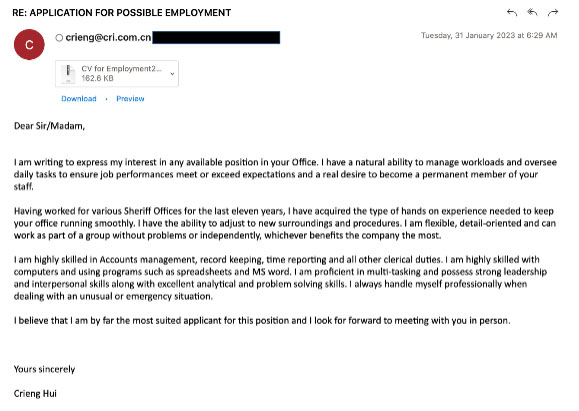
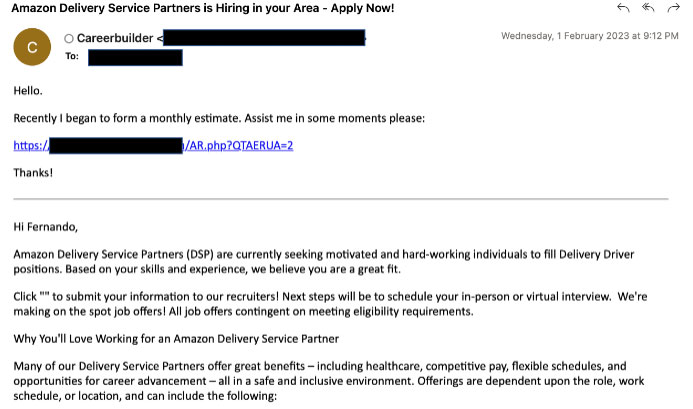
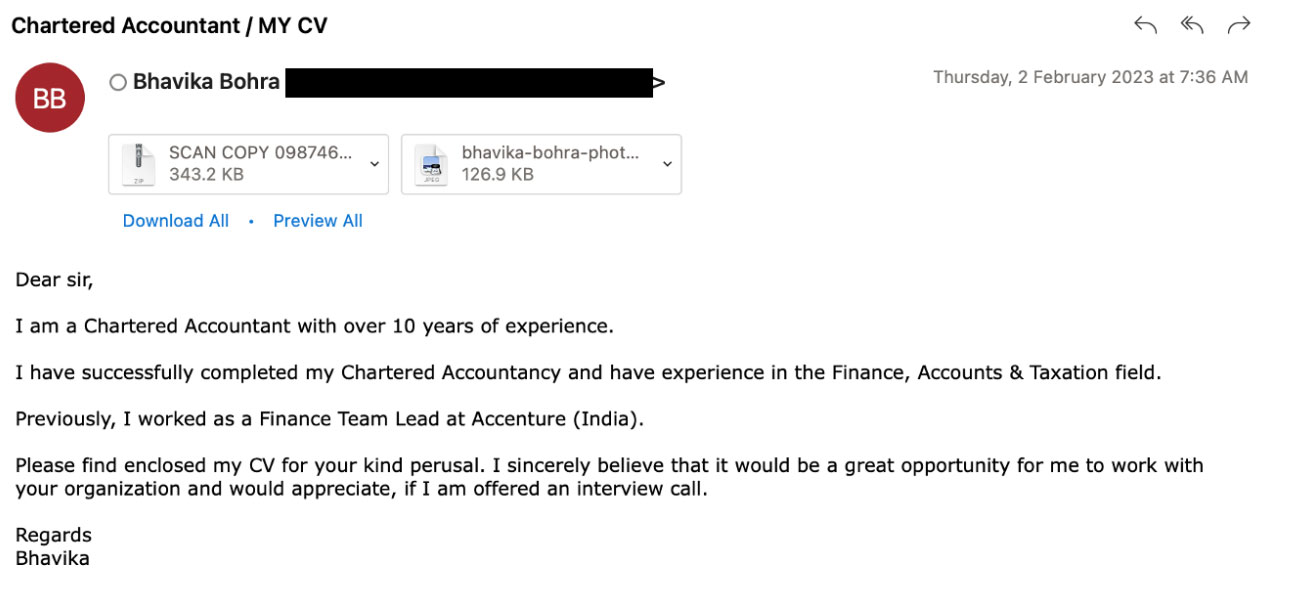
Trellix Advanced Research Center researchers found different styles of job-based malicious email campaigns. The emails either come as a notification of a job vacancy or as a job application which would contain a URL or attachment directing the victim to a phishing page or downloading malware to his system.
Malicious URLs
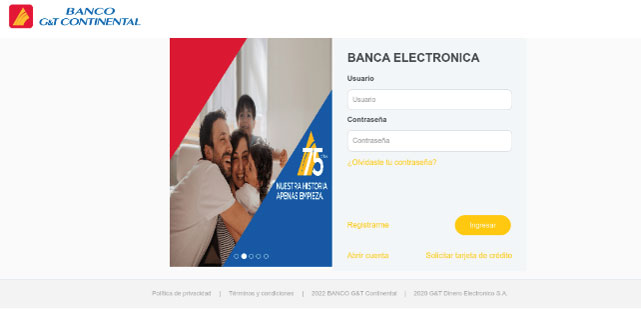
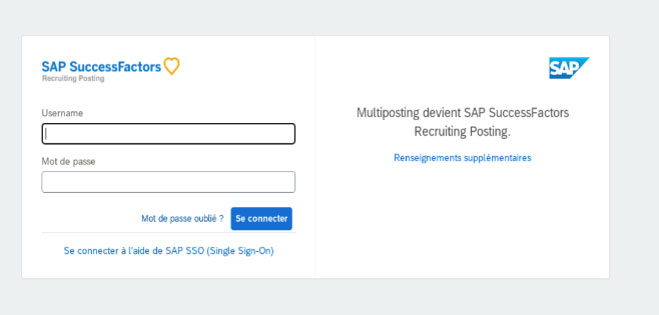
The following are some of the malicious web pages being utilized to target job seekers. Most of the phishing pages follow the same style in which they were made to resemble a login form to proceed with the job application.

Malware
Trellix identified several malware families targeting job seekers and employers. The following are some of the malware families observed by our researchers:
- Emotet – An advanced Trojan primarily spread via phishing email attachments and links that, once clicked, launches a payload. The malware then attempts to proliferate within a network by brute forcing user credentials.
- Agent Tesla – A .NET-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-as-a-Service (MaaS).
- Cryxos Trojans – Displays fake virus infection and data theft and asks you to call a number for removal which connects you to a scam call center.
- Nemucod - Downloads and runs additional malicious files onto the system. The downloaded files are typically info-stealers, though in more recent campaigns Nemucod has also been seen delivering ransomware.
Trellix product protections
Our security product provides comprehensive protection from attacks such as typo squatting domains and malware-laced job application emails. Our multi-layered approach includes checks on the URL, email, network and attachment levels to ensure that any potential threat is detected and prevented from causing harm. Our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats.
The following is a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
| Product | Detection Signature |
|---|---|
| Trellix Network Security Trellix VX Trellix Cloud MVX Trellix File Protect Trellix Malware Analysis Trellix SmartVision Trellix Email Security Trellix Detection As A Service |
FE_Loader_Win32_Emotet_1 FE_Loader_Win32_Emotet_2 FE_Trojan_Win32_Emotet_2 FE_InfoStealer_MSIL_AGENTTESLA_1 FE_Trojan_JS_INTERCC_3 FEC_Trojan_Win64_Emotet_1 FEC_Trojan_Win64_Emotet_2 FEC_Trojan_JS_Generic_42 FEC_Loader_PS1_Generic_14 FEC_Trojan_JS_Generic_27 FEC_Downloader_JS_Nemucod_1 FEC_Downloader_JS_Generic_11 Trojan.Emotet.DNS Phish.URL.Emotet Downloader.Emotet Downloader.AgentTesla Trojan.AgentTesla Trojan.AgentTesla.DNS Trojan.JS.Generic Trojan.JS.INTERCC Downloader.JS.Generic Trojan.Nemucod Trojan.Downloader.Nemucod Suspicious File Document Dropping Executables Suspicious File Dropped by Non Executable Suspicious File Dropper Activity Suspicious Process Powershell Activity Suspicious Process PowerShell Param Suspicious Network By Powershell Suspicious Network Activity Suspicious JSData CC Suspicious Dropped Executable Trojan.JS.INTERCC.MVX JSData Execution JavaScript Malicious Dropper Indicator Malicious Downloader Indicator |
| Trellix Endpoint Security (HX) | EMOTET (FAMILY) EMOTET A (FAMILY) EMOTET B (FAMILY) EMOTET C (FAMILY) EMOTET D (FAMILY) EMOTET E (FAMILY) AGENT TESLA (FAMILY) SUSPICIOUS POWERSHELL USAGE (METHODOLOGY) SUSPICIOUS BINARY EXECUTION VIA MSHTA (METHODOLOGY) SUSPICIOUS WSCRIPT USAGE A Trojan.GenericKD.63349713 Trojan.GenericKD.63332607 Trojan.GenericKD.49391412 Trojan.GenericKD.46096054 JS:Trojan.Cryxos.3089 JS:Trojan.Cryxos.4846 Trojan.JS.Agent.PBN JS:Trojan.Downloader.Nemucod.D Generic.mg.8092ab9cff550650 Generic.mg.90c3c06bf48134f2 Generic.mg.b76c2c2ebb796d91 |
| Trellix Endpoint Security (ENS) | Emotet-FTC Emotet-FGS Emotet-FCZ PWS-FCJT PWS-FDOK AgentTesla-FDOI AgentTesla-FDNG AgentTesla-FDKH JS/Cryxos.a JS/Cryxos.d JS/Downloader.gen.pj JS/Redirector.ek JS/Nemucod.alo JS/Nemucod.aln JS/Nemucod.alj Nemucod.akw |
Conclusion
It is crucial for both job seekers and employers to be aware of this new threat and take precautions to protect their personal and financial information. The best defense against such phishing attacks is to exercise caution when receiving emails from unfamiliar sources, especially those containing links or attachments. It is also a good idea to keep software and anti-virus protection up to date to guard against malware.
While the job market is tough, falling victim to a phishing scam can make an already difficult situation even worse. By being mindful and taking steps to protect yourself, you can stay safe and secure while searching for employment opportunities.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.