
Trellix Global Defenders: Cyberattacks Targeting Ukraine and HermeticWiper Protections
By Taylor Mullins · February 28, 2022
Trellix is monitoring the ongoing cyberattacks targeting the Ukraine and any threat activity targeting entities outside of the Ukraine. Trellix is continuing to add protections to our products via the Global Threat Intelligence (GTI) feed and content updates as new malware variants and behavior indicators are discovered. The Trellix Advanced Programs Group (APG) is also monitoring the threat actors currently targeting the Ukraine and the threat tools being observed in those attacks, monitoring for usage of these tools in your environment can be a proactive step in detecting compromise of your infrastructure.
Analysis from the Trellix Advanced Threat Research (ATR) team into the activity of wipers being deployed within the Ukraine leads them to believe that there is a likely a connection between Whispergate, and the newly identified HermeticWiper.
Recommended Steps to Prevent Initial Access
Organizations should look to review the Initial Access Tactics, techniques, and procedures (TTPs) associated with Russian nation state activity to proactively protect their environment from infiltration.
- Phishing/Spearphishing attacks utilizing shortened URLs of malicious domains.
- Monitor for brute force activity to identify valid account credentials and Microsoft 365 Accounts.
- Enable multifactor authentication (MFA) for all users, without exception.
- Exploiting Public Facing Systems – CISA maintains a full list of CVEs that are known to be exploited: CISA: KNOWN EXPLOITED VULNERABILITIES CATALOG
- Disabling all ports and protocols that are not essential, especially anything related to remote services.
- unt and block open-source tools not related to business activities that have been seen in prior attacks – UltraVNC, AdvancedRun, wget, and Impacket
Trellix Protections for the HermeticWiper Malware
Trellix is currently monitoring the latest wiper malware dubbed "HermeticWiper" that has been observed in attacks against the Ukraine. Trellix Global Threat Intelligence (GTI) is currently protecting against all known indicators associated with "HermeticWiper" and MVISION Insights will note detections in your environment as well.
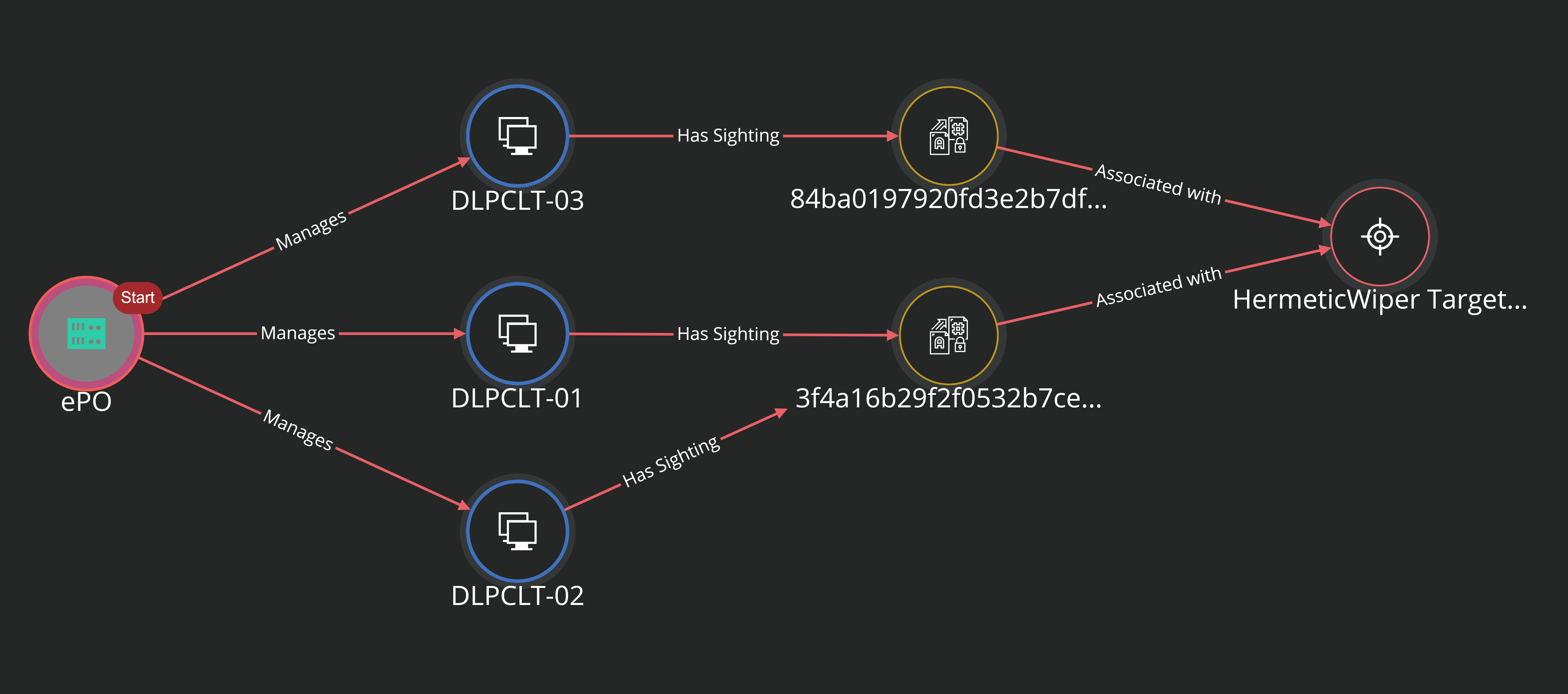
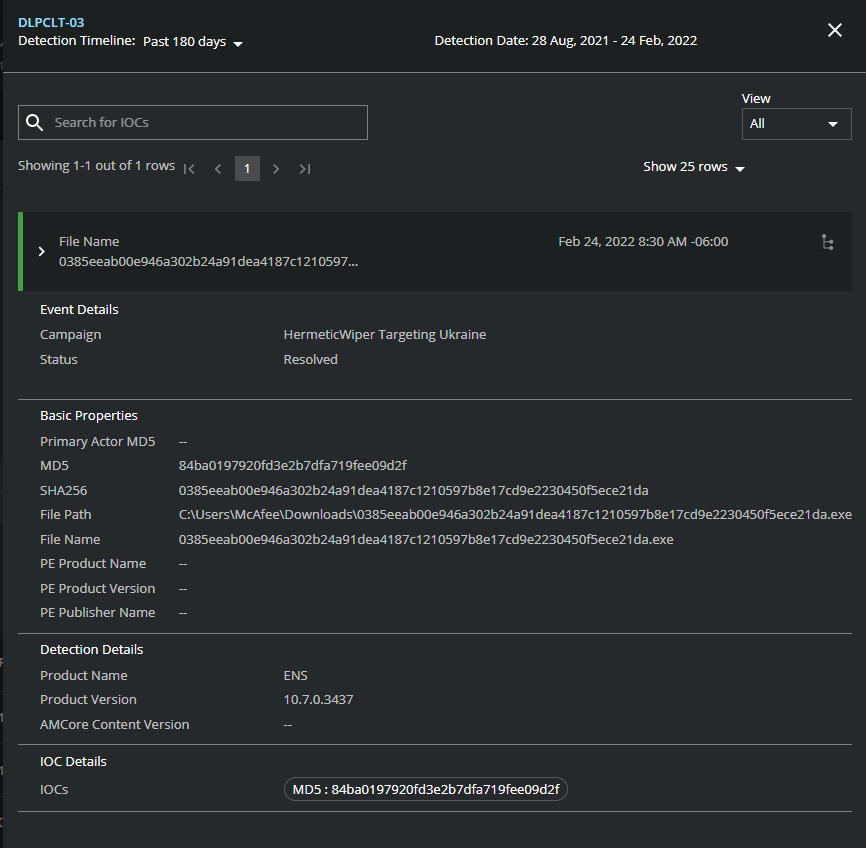
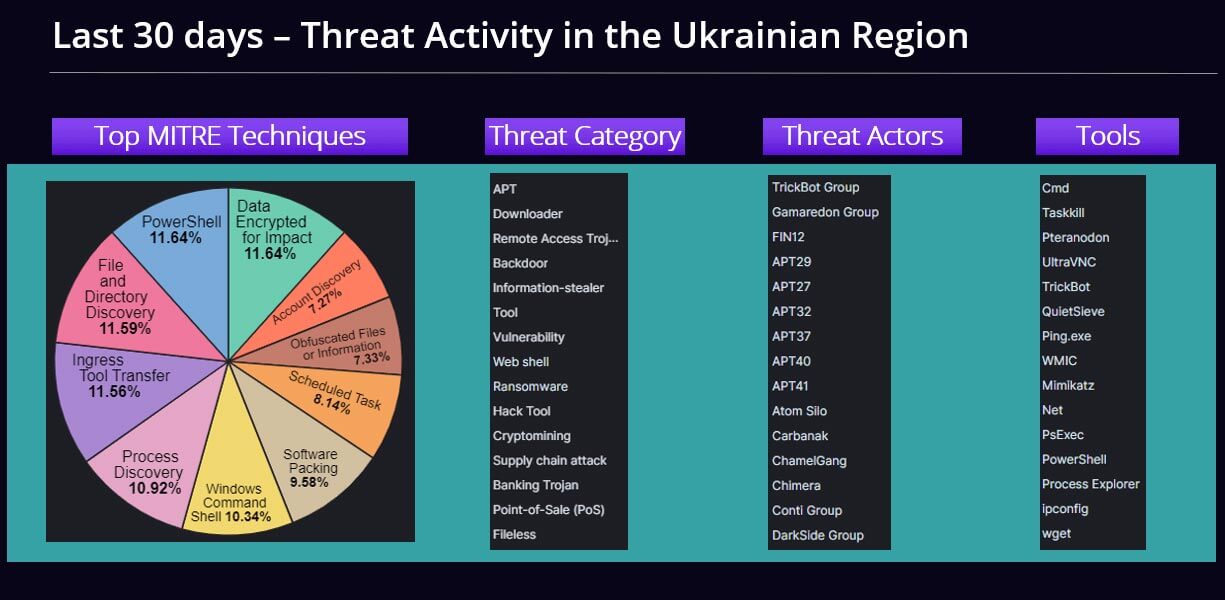
HermeticWiper Threat Intelligence from MVISION Insights
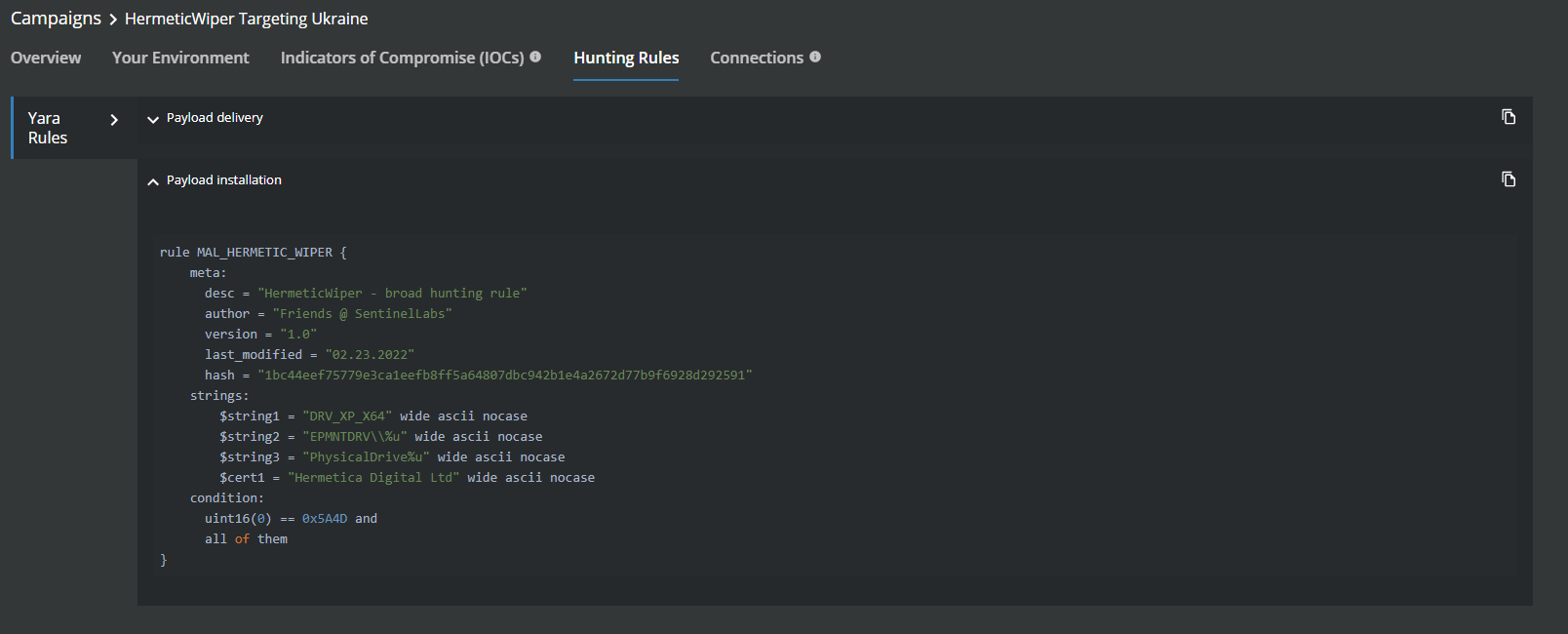
MVISION Insights will provide the current threat intelligence and known indicators for HermeticWiper. MVISION Insights will alert to detections and process traces that have been observed and systems that require additional attention to prevent widespread infection. MVISION Insights will also include Hunting Rules for threat hunting and further intelligence gathering of the threat activity and adversary behind the campaign.
MVISION Insights Campaign Names: HermeticWiper Targeting Ukraine
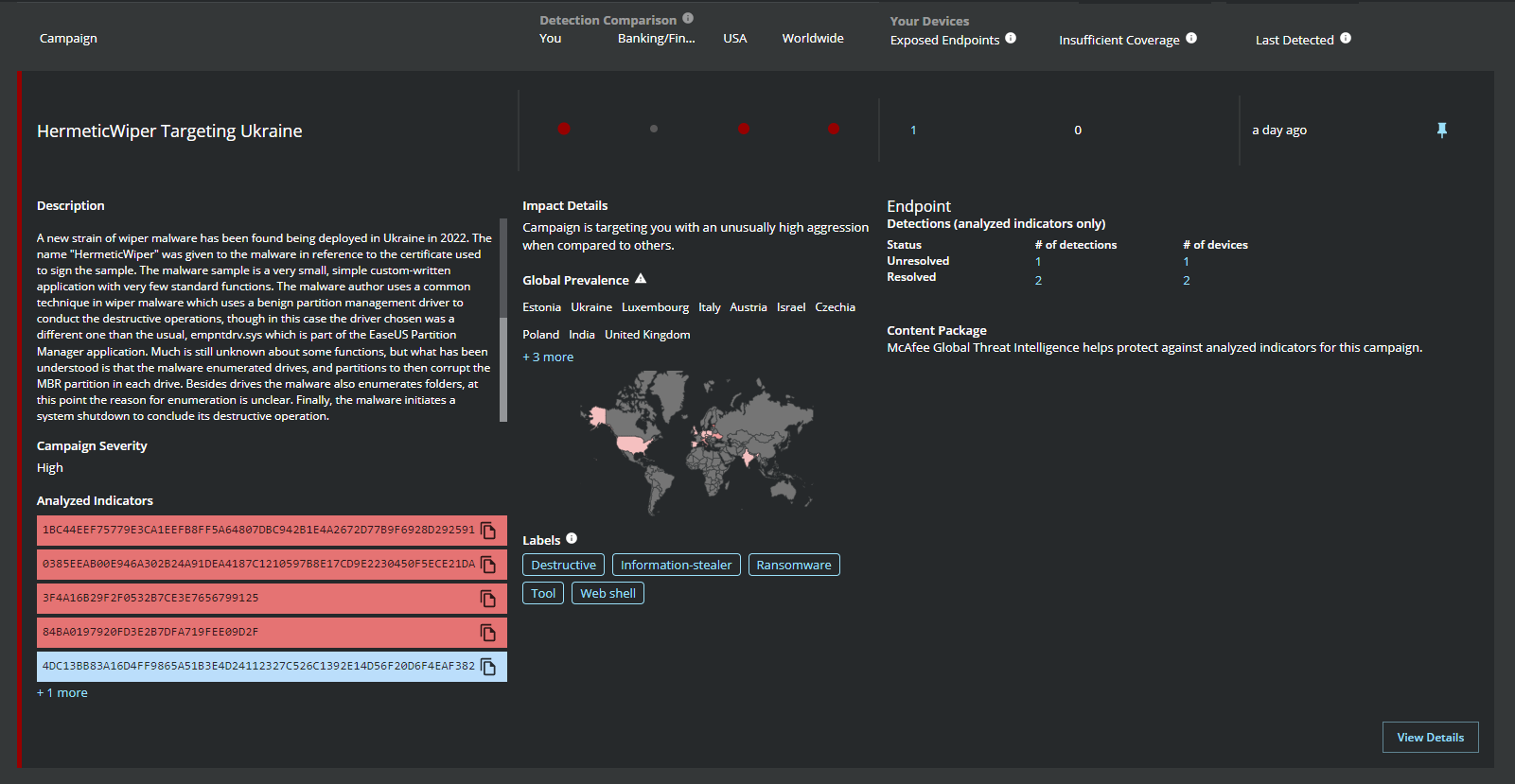
Detecting Malicious Activity with MVISION EDR
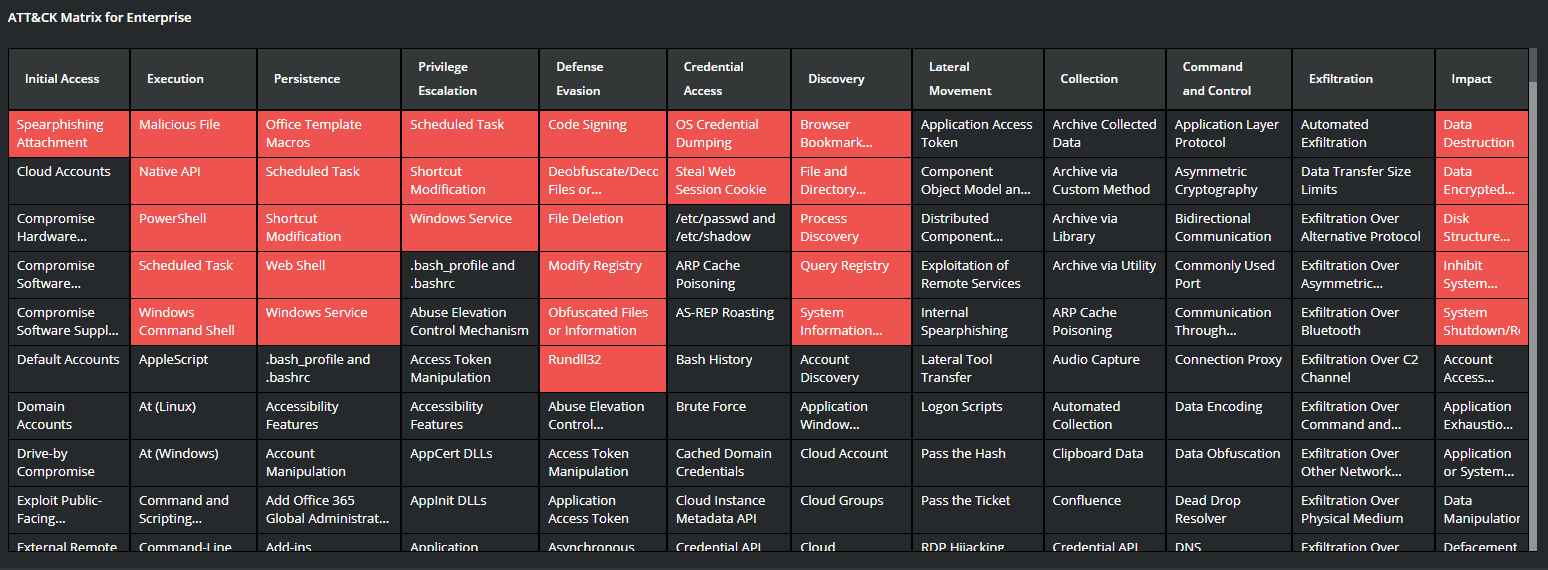
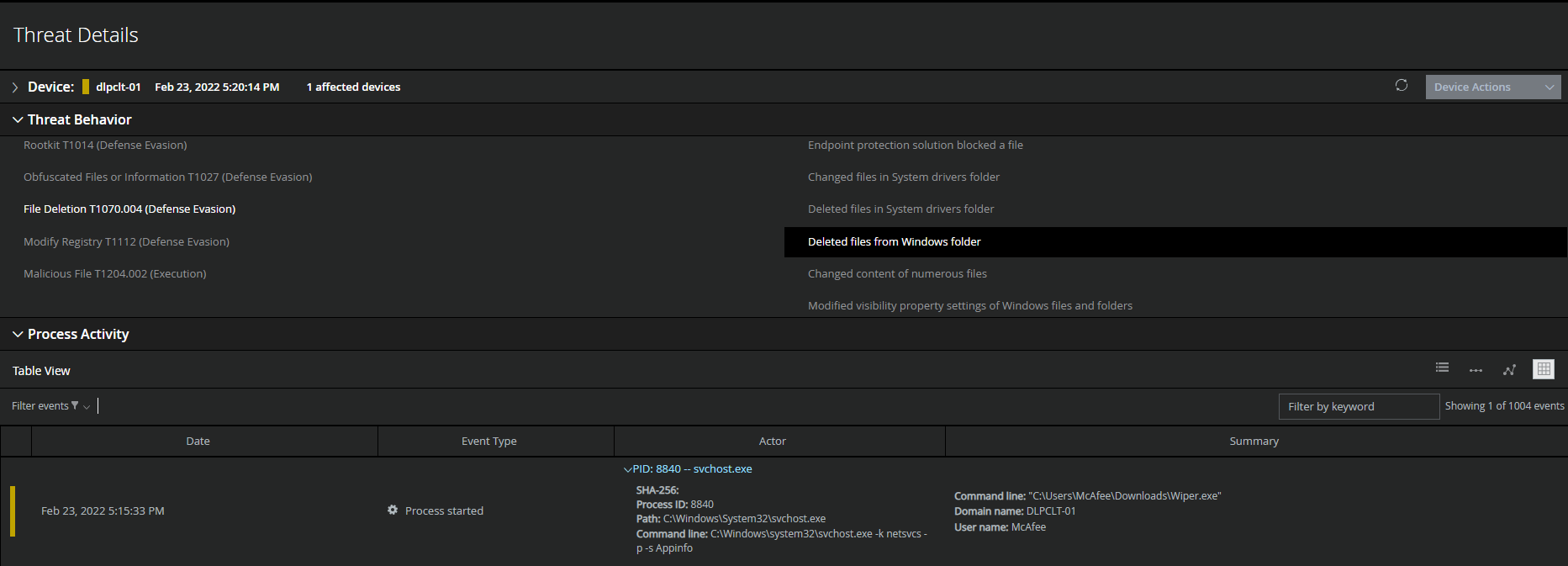
MVISION EDR is currently monitoring for the activity associated with HermeticWiper and will note the MITRE techniques and any suspicious indicators related to the adversarial activity. Detecting and preventing HermeticWiper from spreading throughout your environment is critical due to the destructive nature of the malware, once the HermeticWiper has infected a system it will remove the System Drivers and Windows files leaving the system inoperable.
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.