Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
The Impact of Misconfigurations in Security Solutions
By Zak Krider · July 18, 2023
Securing an organization's assets is an ongoing challenge for security practitioners. Risks often arise from misconfigurations in the very security solutions designed to shield the organization from malicious actors. Such missteps can trigger a cascade of negative consequences, from data breaches to costly operational downtime, exacerbating the workload of already overstretched IT and security teams. To address this, Trellix continually evolves its solutions and services to enhance their value to organizations. We've developed an automated tool, Trellix Health Watch, that quickly collects and analyzes an organization's security solution configuration. This tool provides an actionable plan to align the solutions with best practices, thereby ensuring optimal compliance and security.
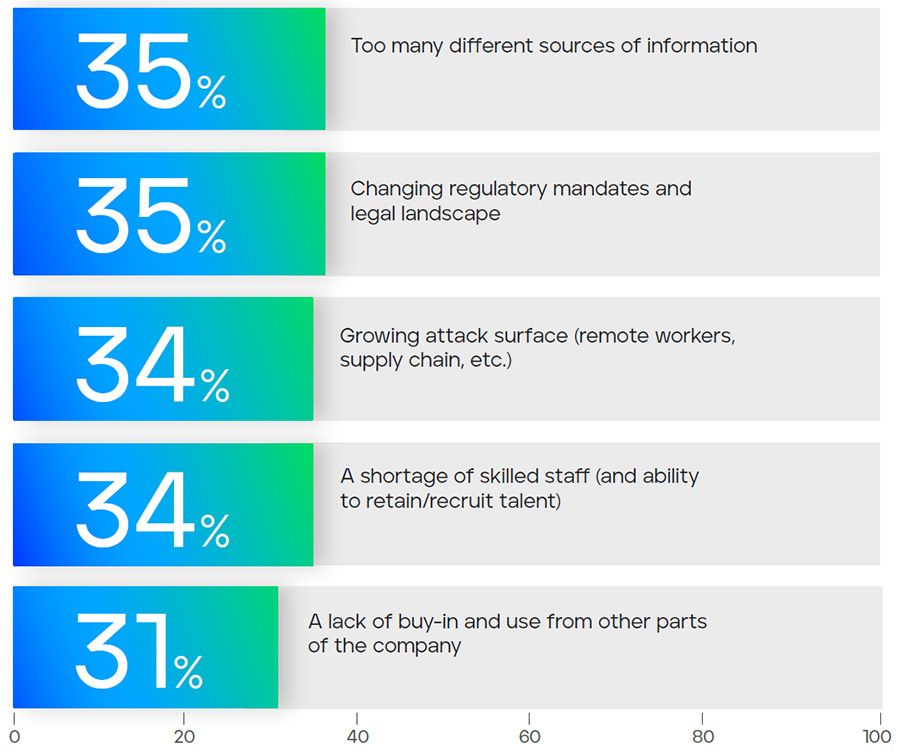
Common misconfigurations in security tools
Security solutions are often implemented with a ‘set & forget’ approach. Relying on out-of-the box settings often results in system configurations and policies not enabled appropriately for your environment. These pre-set configurations, though meant to provide immediate protection, might not be optimally tuned to your organization's needs and environment, potentially leaving gaps in the security posture.
Another frequently encountered misconfiguration is the improper management of access controls. Most security solutions are designed to manage user privileges within the solutions, but incorrect settings can end up granting permissions to the wrong users. Incorrect assignment of permissions to users within the security solutions can lead to misconfigurations and significantly increase the risk of impacting business operations and cyber threats throughout the environment.
Inadequate encryption, particularly in cloud-based storage, is another prevalent misconfiguration. Encryption solutions are often deployed configured in a disabled or even observe state, providing no protection to your data. This lack of encryption can lead to unauthorized data access, and potentially, large-scale data breaches.
Statistics around breaches caused by misconfigurations
The IBM 2022 Cost of a Data Breach report underlines the repercussions of misconfigurations, attributing them as the primary factor in 43% of data breaches with an average cost of $3.86 million per incident. However, the financial hit is just the first layer of damage. Misconfigurations leading to data breaches can also be attributed to lost customer confidence, brand reputation damage, and possible regulatory penalties, all of which can undermine the organization's overall standing and competitive edge.
The aftermath of breaches often involves significant operational downtime. Companies need to identify the source of the breach, rectify the misconfiguration, and deploy or update their security solution – all of which can significantly disrupt business operations, leading to additional costs and potential loss of business.
Burden on understaffed teams
Understaffed IT and security teams are often stretched thin, tasked with managing the organization's entire ecosystem. Misconfigurations only add to their burden. Investigating false positives, rectifying the misconfigurations, and then dealing with the fallout of breaches results in wasted time and increased stress.
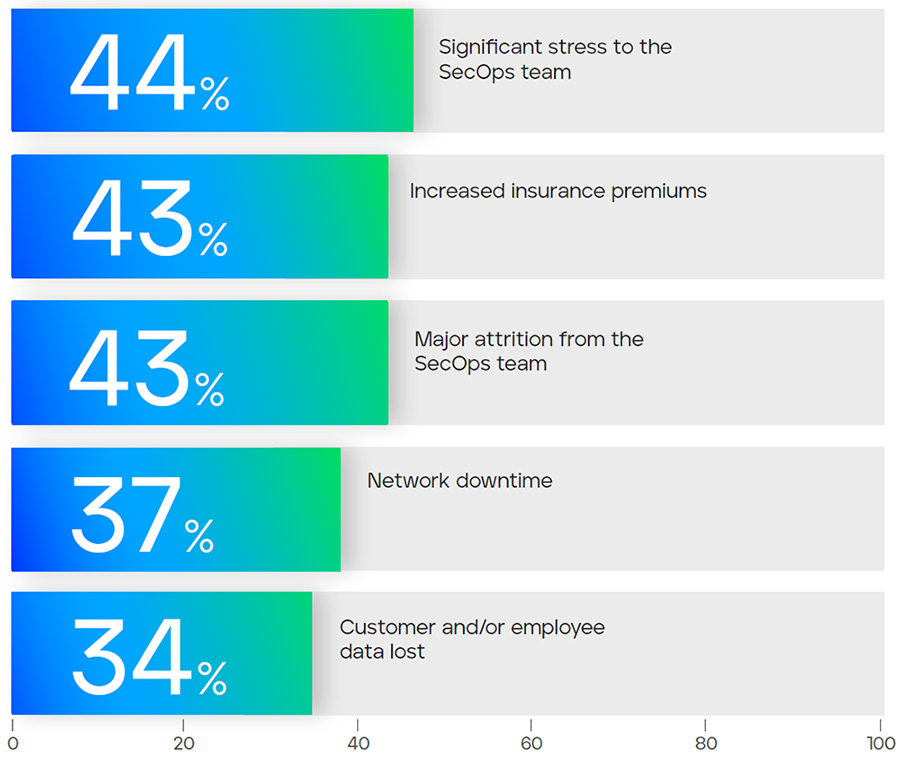
Misconfigurations can also lead to a false sense of security, making teams believe their defenses are adequate when they are not. This can lead to complacency, which can have consequences when actual threats arise. IT and security teams, already burdened with their routine responsibilities, may be caught off guard, leading to delayed detection and response.
We often find the configuration and management of security solutions goes undocumented. This places an additional burden on teams when transitioning solutions from one team to another or taking over the management of solutions from team members that have left the company. Because the configurations are not documented, administrators are often reluctant to make changes to policies or settings out of fear that any change could impact business operations. We often see this with exclusions or critical features such as SSL inspection.
Enhancing alignment between IT and Security
In many organizations, IT and security departments operate independently, often leading to a divergence in priorities and responsibilities. Misconfigurations can create friction between these teams, as operational disruptions can occur due to security breaches, while an overemphasis on operational efficiency may lead to security oversights.
Striking a balance between proper security measures and operational efficiency is a delicate but essential task. Achieving this balance requires fostering a collaborative culture between IT and security departments through open communication and shared metrics. Security considerations should be integrated into IT strategy to avoid conflicts and ensure that security is an integral part of all IT initiatives.
The expanding landscape
The attack surface is constantly expanding with more devices, applications, and networks becoming integral to business operations. This expansion also means more points of potential vulnerability, increasing the chance for misconfigurations.
Adding to the complexity is the growing number of security solutions that organizations use to protect their environments. Each solution comes with its own set of configurations and settings, which can be overwhelming for IT and security teams to manage effectively.
The combination of the increased number of business and security solutions is a complex network to manage and often results in incorrect settings, which can impact end users. The result is a misconception that the solutions are only causing performance issues and are not securing the environment.
The power of regular health checks
By systematically reviewing security configurations and settings, organizations can identify and rectify misconfigurations before they have the chance to become an incident.
Health checks should be comprehensive, spanning all security solutions and encompassing all aspects of the security architecture. This includes access controls, settings, and policies. Regular audits can ensure solutions are continuously aligned with security best practices and any changes in the threat landscape.
Trellix Health Watch
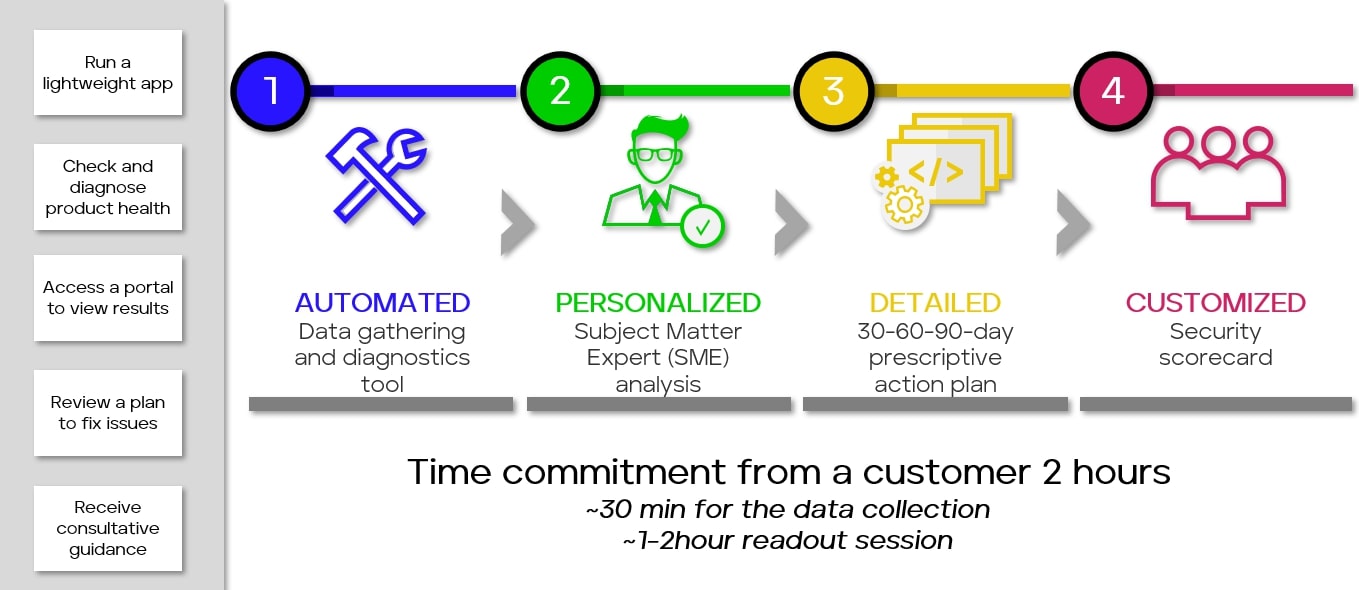
Trellix Health Watch can be invaluable in helping your organization identify potential misconfigurations before they negatively impact your organization. Trellix Health Watch analyzes your security configurations, detecting and providing a 30/60/90-day actionable plan with clear steps for remediating misconfigurations.
Worried about dedicating extensive time to analyze your environment? The Trellix Health Watch engagement typically requires just two hours of your time. The data collection process is fully automated; your only task is to provide your credentials to the environment. Afterward, we handle all the data analysis and create a prescriptive action plan that we'll thoroughly discuss with you in a one-hour session.
Additionally, you'll gain access to the Health Watch portal. Here, you can view all the data collected from your environment, interact with subject matter experts on specific findings within the portal, view documented configurations, and track trending health scores from engagement to engagement.
To learn more about Trellix Health Watch, contact your Trellix sales representative to schedule a time to discuss the benefits and how to get an engagement going.
Health Watch portal demo
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.

