Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Dark Web Roast - August 2025 Edition
By Trellix Advanced Research Center · September 18, 2025
Executive Summary
August 2025 delivered a masterclass in cybercriminal incompetence that would make amateur hour look professional. From racist social engineering recruiters who prioritize race over actual skill, to ransomware entrepreneurs creating McDonald's-style menus for malware services, this month's underground scene provided endless entertainment through its spectacular displays of operational ineptitude. The real threat isn't just their technical capabilities—it's the secondhand embarrassment inflicted on the entire cybercrime ecosystem, as law enforcement agencies worldwide use their public communications for comedy training sessions.
This Month in the DarkRoast
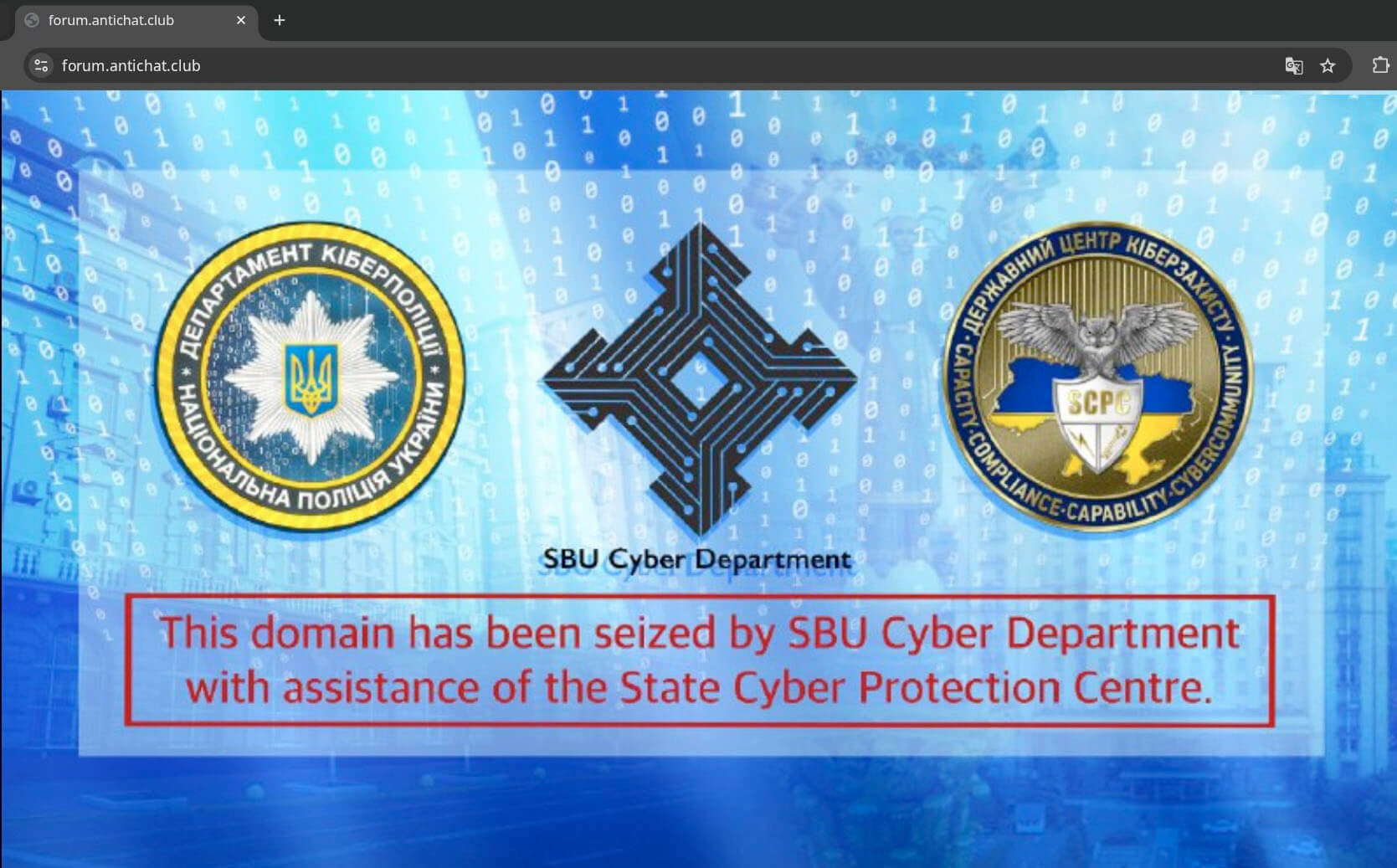
🎪 The Antichat Forum's Oscar-Worthy Performance
The legendary Antichat forum pulled off what might be the most dramatic exit in cybercrime history by staging their own "law enforcement seizure," complete with fake Ukrainian SBU banners. Security researchers quickly called BS when they noticed the "seized" site was still running on German Hetzner servers—apparently, even fake government raids can't figure out basic hosting geography. The forum's admin essentially created the world's first cybercrime theatre production, complete with props and everything, to avoid actually dealing with real consequences. It's like watching someone fake their own death to get out of paying student loans, except with more Cyrillic text and fewer legal ramifications. This performance deserves an award for "Most Creative Exit Strategy in Organized Crime."
🎭 The Racist Social Engineering Recruiter
Some criminal mastermind on the spazzing Telegram channel is recruiting "Gmail callers" with requirements that read like a parody of underground hiring practices. They demand callers "Must Be White or SOUND White" and provide a sample script about "google account safety department" that sounds about as convincing as a three-dollar bill. The best part? They're offering $100—$250 per successful scam while simultaneously demonstrating the intellectual capacity of a soggy pretzel.
This recruitment post perfectly captures why most social engineering attempts fail spectacularly. When your hiring criteria prioritize race over actual competence, you're basically building a criminal organization with the strategic planning of a middle school cafeteria. The operational security here suggests these masterminds think discrimination laws don't apply to criminal enterprises.

🍔 The Brazilian Ransomware Entrepreneur's Menu
Brazilian cybercriminal @DmitryRansom from 𝐊𝐑𝐄𝐌𝐋𝐈𝐍 𝐁𝐑 𝐆𝐑𝐎𝐔𝐏 Telegram channel has created what appears to be a McDonald's menu for malware services, complete with emojis and organized categories. From "🩸𝐑𝐀𝐍𝐒𝐎𝐌𝐖𝐀𝐑𝐄" to "🩸𝐀𝐍𝐃𝐑𝐎𝐈𝐃 𝐑𝐀𝐓," this criminal entrepreneur has systematized cybercrime with the efficiency of a fast-food franchise.
The warning "𝙉Ã𝙊 𝙈𝙀 𝙁𝘼Ç𝘼 𝙋𝙀𝙍𝘿𝙀𝙍 𝙏𝙀𝙈𝙋𝙊" (don't make me waste time) suggests they run their illegal operation with stricter customer service standards than most legitimate businesses. This level of organization in the ransomware-as-a-service market would be impressive if it weren't so thoroughly illegal and morally bankrupt. Apparently, even cyber-extortion needs proper branding these days.
🌐 The WordPress Vulnerability Spam Victim
k4mui on BreachForums was promoting a "new wordpress website takeover vuln" but got banned for spamming before anyone could see the actual vulnerability. The irony is delicious—a cybercriminal getting shut down by forum moderation policies while trying to share website takeover techniques. Even underground forums have standards, apparently. This demonstrates how modern criminal forums maintain operational discipline through community moderation, occasionally resulting in legitimate threat intelligence lost to administrative efficiency. The intersection of criminal enterprise and community management creates unexpected barriers to information sharing.
🏦 The Indian Banking Scammer's Alphabet Soup
Indian cybercriminals have turned banking fraud into an incomprehensible acronym festival that reads like someone sneezed on a keyboard full of bank abbreviations. Posts advertising "ICICI+MQR," "RazorpayX with RBL +VPA," and "DBS IDEAL corporate +MQR" create a word salad so confusing that even legitimate bankers would need a decoder ring.
These scammers promise "High% + Bonus" while demonstrating the communication skills of a malfunctioning autocorrect system. The real threat here isn't their technical capabilities—it's the possibility that someone might actually understand what they're selling and accidentally become their customer through sheer linguistic confusion. The underground banking fraud scene has essentially become a game of financial Scrabble played by people who've never seen the rules.

💰 The "Professional" Money Launderer's Masterclass
NevadaBurger 🍼 from Dread Forum laid out their "foolproof" money laundering plan: receive Bitcoin to Electrum wallet, send to mixer, swap for Monero, then to KYC exchange, and finally to bank account. The baby bottle emoji in their username perfectly captures their operational maturity level. This genius apparently thinks mixing dirty Bitcoin through a KYC exchange is the pinnacle of financial privacy.
Law enforcement agencies worldwide are probably taking notes on this revolutionary "anonymous transaction plan"—mainly for their comedy training sessions. The fact that they're asking for validation on a public forum really seals the deal on their OPSEC expertise. This masterclass in money laundering has all the sophistication of asking directions to a bank robbery on Twitter.
🔧The SharePoint Copy-Paste Warriors
Multiple actors, including fix_problem and nyyp on Exploit, are sharing massive Metasploit modules for CVE-2025-53770 SharePoint vulnerabilities. The hilarious part? One user complains, "on all vulnerable targets it reports 'Exploit completed, but no session was created'"—essentially admitting they're running exploits they don't understand against targets they can't properly compromise. These script kiddies are copying 1,200+ lines of code they clearly didn't write, then wondering why their scripts aren't working. This showcases the current state of exploit development, where sophisticated tools are distributed to users who lack the technical competence to deploy them effectively.
Conclusion
August 2025's underground scene delivered a masterclass in how not to run a criminal enterprise, showcasing threat actors who've somehow managed to combine the worst aspects of amateur hour operations with delusions of professional grandeur. From Antichat forum's theatrical exit to the audacious hiring practices of racist social engineering recruiters, this month proved that while the tools of cybercrime may evolve, the fundamental incompetence of most threat actors remains refreshingly consistent.
The real winner here isn't any particular criminal organization—it's the cybersecurity community, getting endless entertainment watching grown adults run illegal enterprises with all the operational sophistication of a children's lemonade stand during a thunderstorm.
DisclaimerWhile these incidents are genuinely amusing, they represent real criminal activities causing significant harm. This content is for threat intelligence and educational purposes only.
And to all you cybercriminals out there, remember they’re just jokes…

Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
