Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Gang Wars: Breaking Trust Among Cyber Criminals
By John Fokker and Jambul Tologonov · August 5, 2025
Introduction
In the final, unforgettable scene of the film Reservoir Dogs, a group of criminals — once united by a common goal — stand in a Mexican standoff, guns drawn, hearts pounding. Suspicion has shattered loyalty. One betrayal too many, and the trust holding them together collapses. Within seconds, they turn on each other.

This isn’t just Hollywood. It’s what the ransomware underground looks like today.
Over the past few years, the Ransomware-as-a-Service (RaaS) model rose to dominance, structured like criminal empires, complete with brands, affiliate programs, and professional operations. What once looked like organized crime, now more closely resembles a paranoid, fractured ecosystem where loyalty is temporary and betrayal is expected.
Today, we’re watching the RaaS model unravel.
External intervention by law enforcement has shifted tactics from not only arresting individuals to undermining the very foundation of cybercriminal collaboration: trust. The result? A growing storm of infighting, exposure, and fragmentation. Affiliate crews jump ship. Admins double-cross each other. And group rivalry is creating public disputes that expose just how fragile the ecosystem has become.
It is not often that we witness disputes between ransomware groups. The current ransomware landscape has gotten so competitive that ransomware operators are trying their best to retain and recruit affiliates and partners into their programs to keep operations afloat and generate profit for the ransomware owners.
What are we seeing now?
Today, the ransomware ecosystem has become so fractured that it is difficult to determine which affiliates belong to specific RaaS programs, let alone which RaaS gangs are cooperating and/or friendly with each other. Affiliates are easily moving their targets from one RaaS program to another, betraying the trust within ransomware gangs. They chase easy and fast money, therefore, internal or operational issues within a RaaS program only reduce their chances of successful payment from victim organizations.
Consequently, affiliates have become more agile, often operating as “lone wolves” who will not hesitate to pursue their targets with a competitor RaaS gang if necessary. This becomes very clear when we look at the frequency of the different groups posting their victims on their online leak site in January 2024 versus May 2025, with the latter being much more scattered with new groups appearing weekly.
It’s common today for affiliates to wear two or more hats and keep access to multiple competing ransomware gangs. There are many reasons for this.
Recent law enforcement actions against ransomware groups like LockBit, Phobos, and potentially other syndicates have made ransomware affiliates more careful and resilient. These law enforcement operations had a proven impact on trust in the underground ransomware economy. If one RaaS group goes down, affiliates need to quickly recuperate, transfer their targets to another reputable ransomware group to continue victim negotiation, and ultimately secure their ransom payment.
Furthermore, exit scams by ransomware groups like ALPHV have led affiliates to realize that they cannot trust ransomware operators and should rely on themselves, always having a backup plan. Considering the proliferation of RaaS groups with short lifespans, and the constant emergence of new spinoffs and rebrands every couple of months, it's evident that this represents a natural evolution for the ransomware affiliate model. They are becoming independent penetration testers and access and data owners, and will do everything in their power to increase their chances of financial gain.
Another consideration is the current diversity within the ransomware landscape, as every newcomer RaaS operator attempts to differentiate themselves in some way. Qilin RaaS, for instance, offers legal advice to affiliates during ransom negotiation; others focus solely on data-extortion schemes like World leaks RaaS; while some create a ransomware cartel like DragonForce, inviting other RaaS groups to join under their umbrella brand. Nova RaaS recently offered lifetime affiliate access to their RaaS program for as little as $800 USD. These are just examples of creative ways operators stand out and incentivize affiliates to join them.
The instability of the current RaaS model is also causing significant problems for ransomware victims. They face an increased risk of extortion by multiple RaaS groups, as threat actors are proving unreliable and failing to uphold their agreements.
In this blog, we will cover some of the recent feuds and clashes observed by the Trellix Advanced Research Center in underground forums. We’ll describe how far ransomware gangs go in this competitive, fast-evolving ransomware ecosystem and how we’ve seen affiliates being loyal to only themselves and not the ransomware syndicates they work for.
Affiliate notchy versus ALPHV and RansomHub
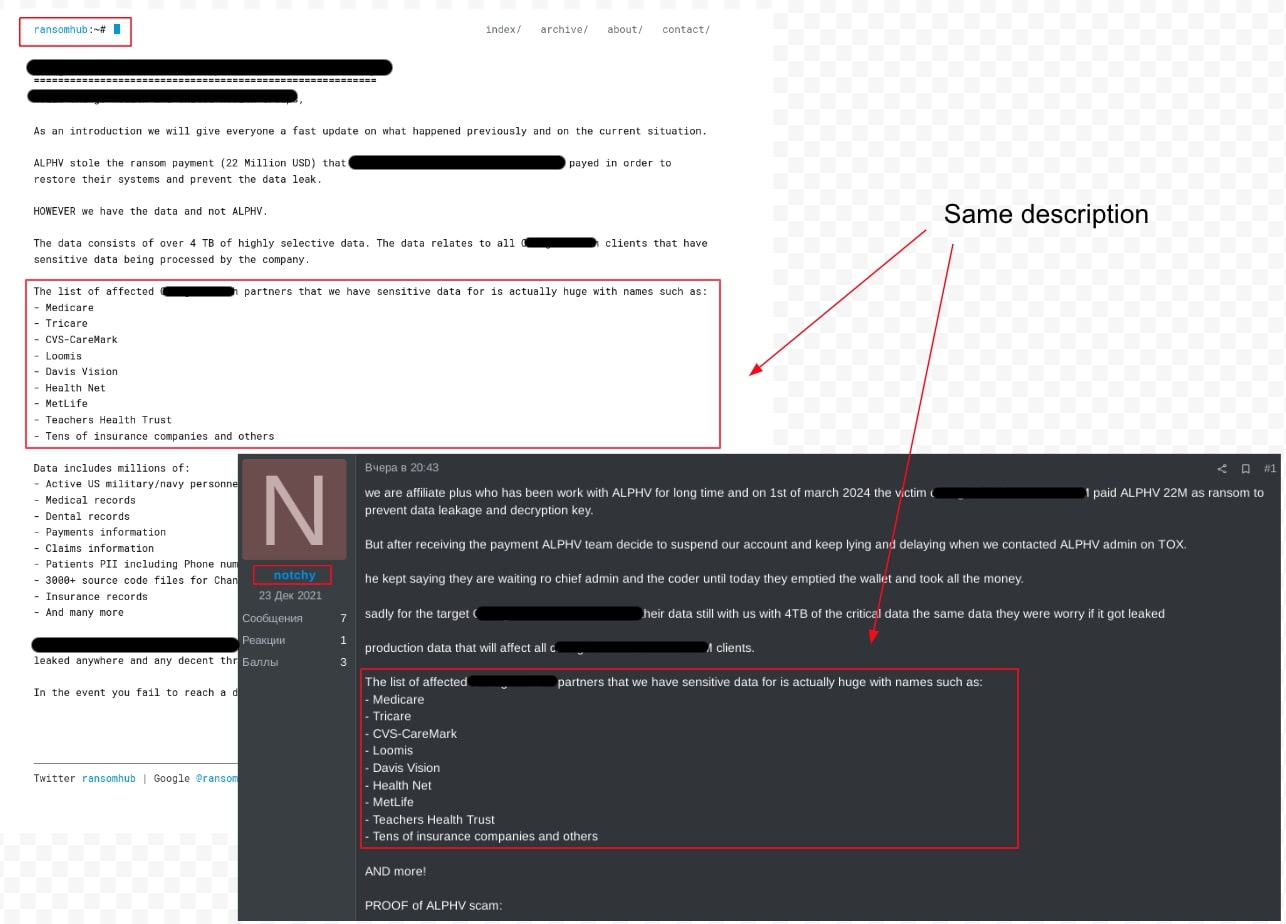
In March 2024, ALPHV RaaS affiliate notchy publicly claimed their pentesting team had been scammed by the ALPHV ransomware operator, despite a long-standing collaboration. According to notchy, the victim organization, a US healthcare provider, paid a $22 million USD ransom. However, notchy and their team were not compensated, and their affiliate accounts were suspended. The actor, notchy, claimed to still possess 4TB of sensitive data belonging to the victim and its partners.
Actor koley, the operator of RansomHub RaaS, which launched its ransomware program in February 2024, advised notchy to retain the victim data. One month later in April 2024, the healthcare provider was added to the RansomHub data leak blog with a description identical to notchy's post on the RAMP underground forum, suggesting that notchy potentially joined RansomHub RaaS, as shown in Figure 4.
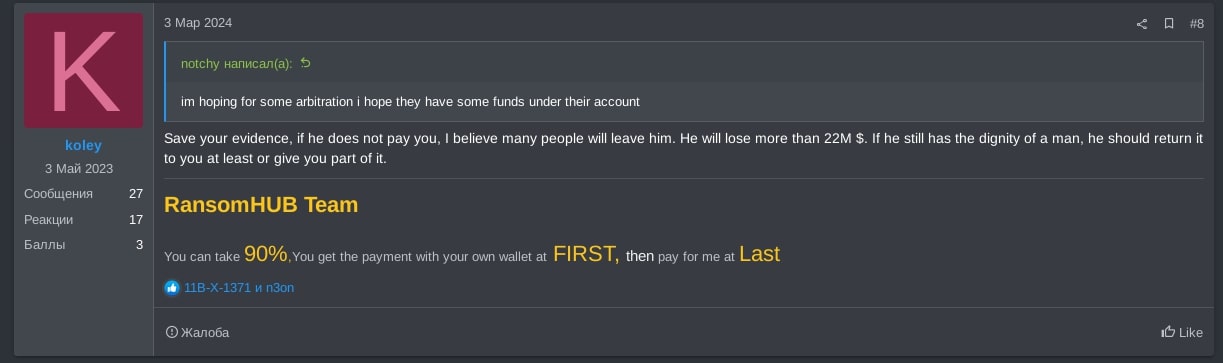
RansomHub operator koley stated if ALPHV RaaS operator ransom had “dignity of a man” they would return the money to notchy and that many affiliates will leave ALPHV as the result of the operator’s actions, as shown in Figure 5.
In April 2024, koley stated the ALPHV-scammed affiliates were actively joining the RansomHub RaaS program.
ALPHV RaaS attempted to resolve the dispute with notchy, requesting patience. However, ALPHV ransomware operator ransom ultimately absconded with the funds, orchestrating an exit scam from their affiliate program. They further disseminated a fabricated FBI takedown notice on their TOR website, falsely claiming their gang's dissolution due to law enforcement intervention.
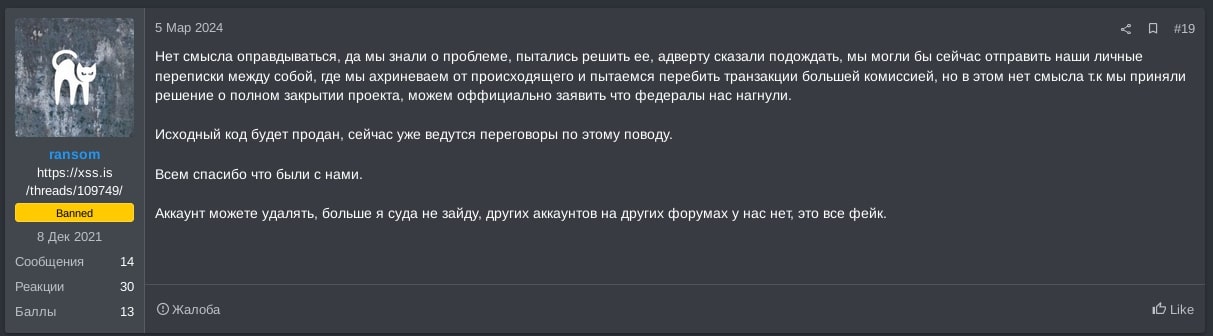
Translation of Figure 6:
None There is no point in making excuses, but we knew about the problem, tried to solve it, the advert was told to wait, we could now send our personal correspondence among ourselves, where we are shocked by what is happening and try to outbid transactions with a larger commission, but this makes no sense because we decided to completely close the project, we can officially declare that the feds screwed us over.
The source code will be sold, negotiations are already underway on this matter.
Thank you all for being with us.
You can delete this account, I won't login here again, we don't have other accounts on other forums, it's all fake if there are others.
Fast forward one year to April 2025. RansomHub RaaS, which was one of the most active ransomware programs of the last year, announced they were attacked and betrayed by certain affiliates within their gang. They called notchy disloyal, saying they brought notchy in after the ALPHV scam, made them money, and in return notchy left RansomHub right before they were attacked, as shown in Figure 7.
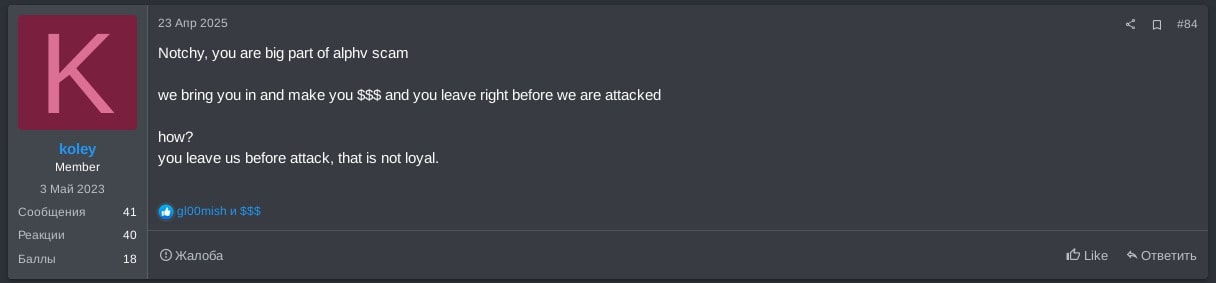
The migration of high-profile affiliates such as notchy from ALPHV RaaS to RansomHub and their subsequent departure from RansomHub prior to them being attacked exemplifies a current trend we are observing in ransomware development. In this lone wolf model, affiliates retain control over victim network access and data.
Should a RaaS operator encounter issues, affiliates readily transition to an alternative RaaS group, indicating a lack of enduring loyalty or commitment to the ransomware brand. Affiliates continue to target victims, extract ransoms, and remit their share to the gang as long as the RaaS operates under mutually beneficial terms. If they face any issues with law enforcement or from competitors causing operational downtime, the affiliates are more than ready to take their targets to a competing RaaS.
Trellix also observed speculation in underground forums where certain threat actors claim RansomHub is a successor to ALPHV ransomware, though we have found no evidence to support the assertion, as shown in Figure 8.
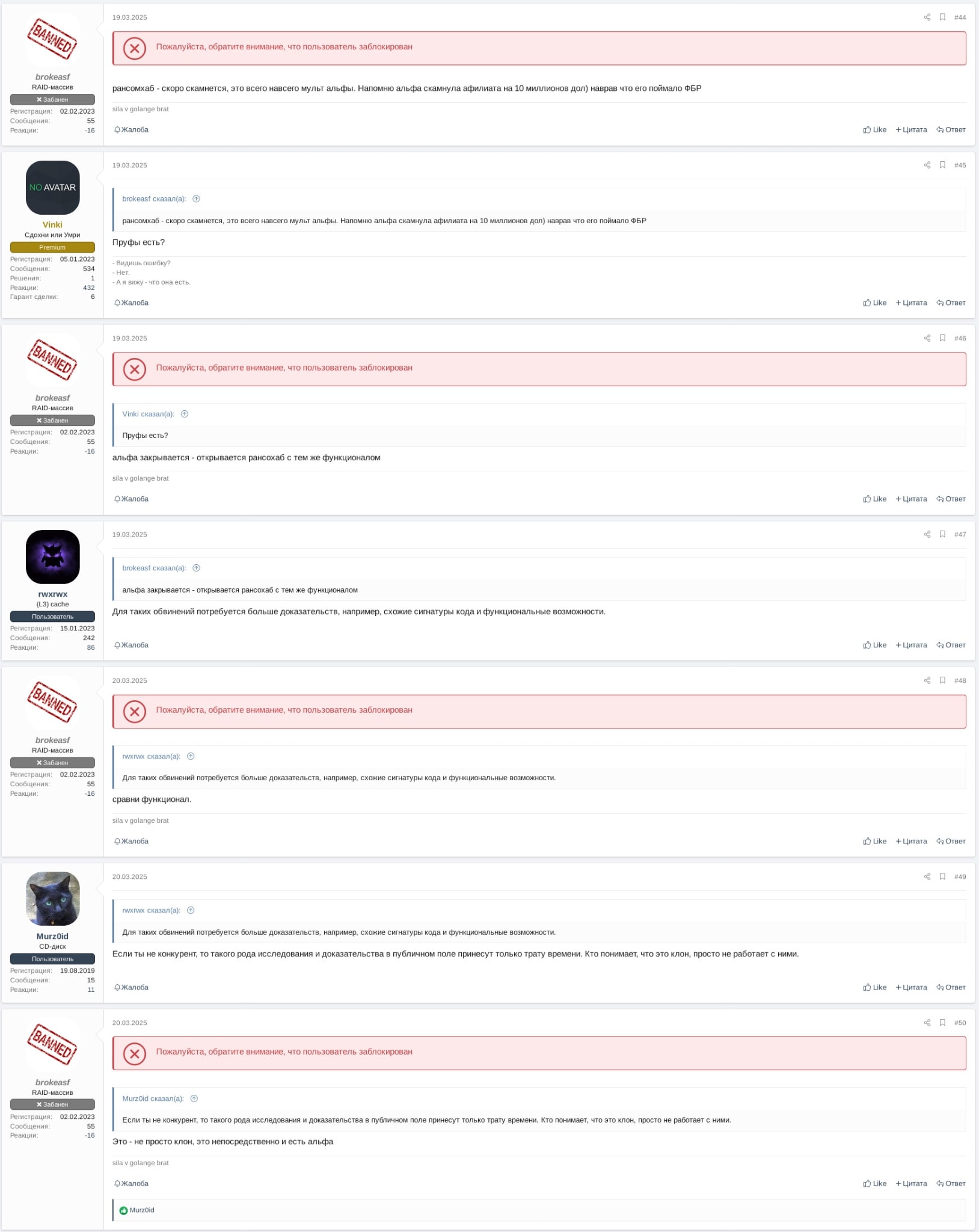
Translation of Figure 8:
None brokeasf: RansomHub will soon get scammed, it is just ALPHV's alternative. Let me remind you that ALPHV scammed an affiliate for 10 million USD) by lying they got caught by FBI
Vinki: Any proofs?
brokeasf: ALPHV closes - RansomHub opens up with the same functionality
Vinki: For such accusations you need more proofs, for example, similar code signatures and functions.
brokeasf: Compare the functionality.
Murz0id: If you are not a competitor then this sort of research and proofs in public will only be a waste of time. Those who understand that it is a clone, will simply stop working with them.
brokeasf: It is not just a clone, it is ALPHV
DragonForce versus Blacklock
Another interesting case is DragonForce RaaS attacking Blacklock (aka Eldorado and Mamona R.I.P.) ransomware gang. In March, 2025 the Blacklock ransomware operator $$$ attempted to rebrand Blacklock ransomware to Mamona R.I.P. RaaS. However, the rebranded ransomware group was almost immediately hacked by the DragonForce gang, as shown in Figure 9.
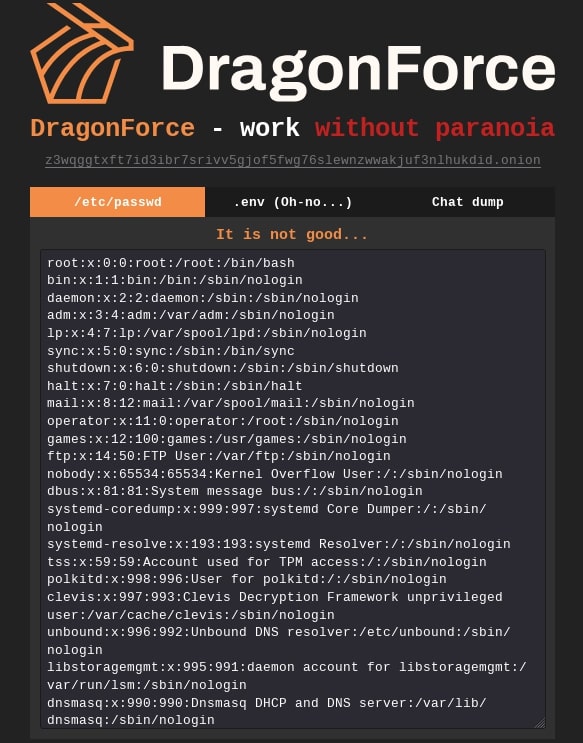
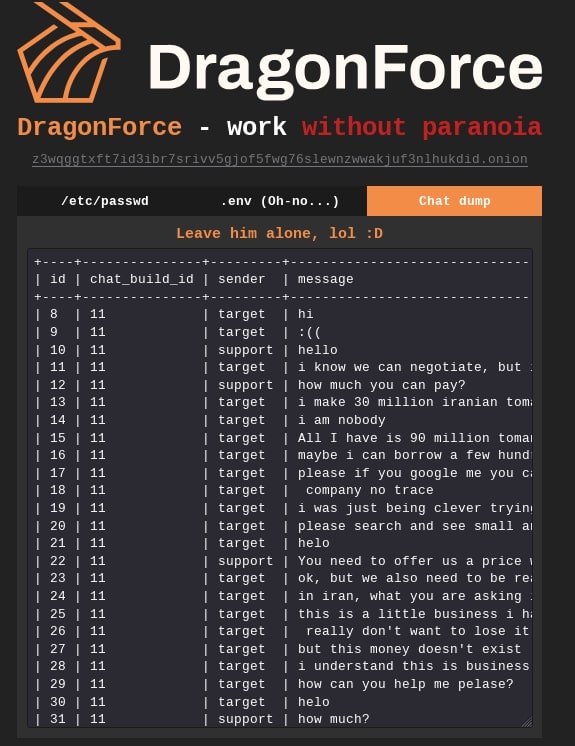
DragonForce RaaS defaced the Mamona R.I.P. and Eldorado ransomware TOR sites with the text “DragonForce - work without paranoia” and published the content of /etc/passwd and .env files obtained from the hacked systems, as well as the sample chat dump between the Mamona R.I.P. support and a target (potential victim organization), as shown in Figure 10.
What is interesting is that $$$ did not accuse DragonForce gang of attacking Blacklock and instead simply acknowledged their infrastructural mistakes, advising it could have been worse and as soon as they get up from their knees, they will inform the underground community on their restored ransomware blog.
In April 2025, their Mamona R.I.P. blog reverted back to Blacklock RaaS. The Mamona rebrand was a failure and had it not had a fateful extension “R.I.P” next to its name, perhaps it would not have had such a short lifespan.
The operator $$$, however, has not stopped with spinoffs and rebranding attempts. In June 2025 they introduced another RaaS called Global ransomware. Trellix Advanced Research Center is continuing to monitor the development of Global ransomware which $$$ claims has an integrated AI-assisted chat — another way to differentiate a RaaS from its rivals.
This was not the only attack from DragonForce RaaS on its competitor infrastructure.
DragonForce versus RansomHub
In March 2025 DragonForce RaaS announced they are now The DragonForce Ransomware Cartel. They stated it is time for change, therefore they are introducing a new direction and a new working model where affiliates can create their own brand without needing to operate under the DragonForce name. By doing so, DragonForce hoped to attract those lone wolves to join their cartel, create a brand of their own, and work to turn their targets into victims without associating with the DragonForce brand.
In April 2025, DragonForce insinuated that RansomHub RaaS, though inactive, moved temporarily to DragonForce infrastructure and that RansomHub was a reliable ransomware partner. They made a demo of RansomHub's TOR pages under DragonForce Ransomware Cartel and offered RansomHub to consider their suggestion to move permanently under DragonForce’s cartel umbrella, as shown in Figure 11.

In late April 2025 and after some period of inactivity on the RAMP forum, RansomHub operator koley posted they had identified traitors within the gang and would be revealing the real identities of some. Additionally, they asked their affiliates to transfer one BTC to a dedicated cryptocurrency address to demonstrate their loyalty and commitment to RansomHub, as shown in Figure 13.
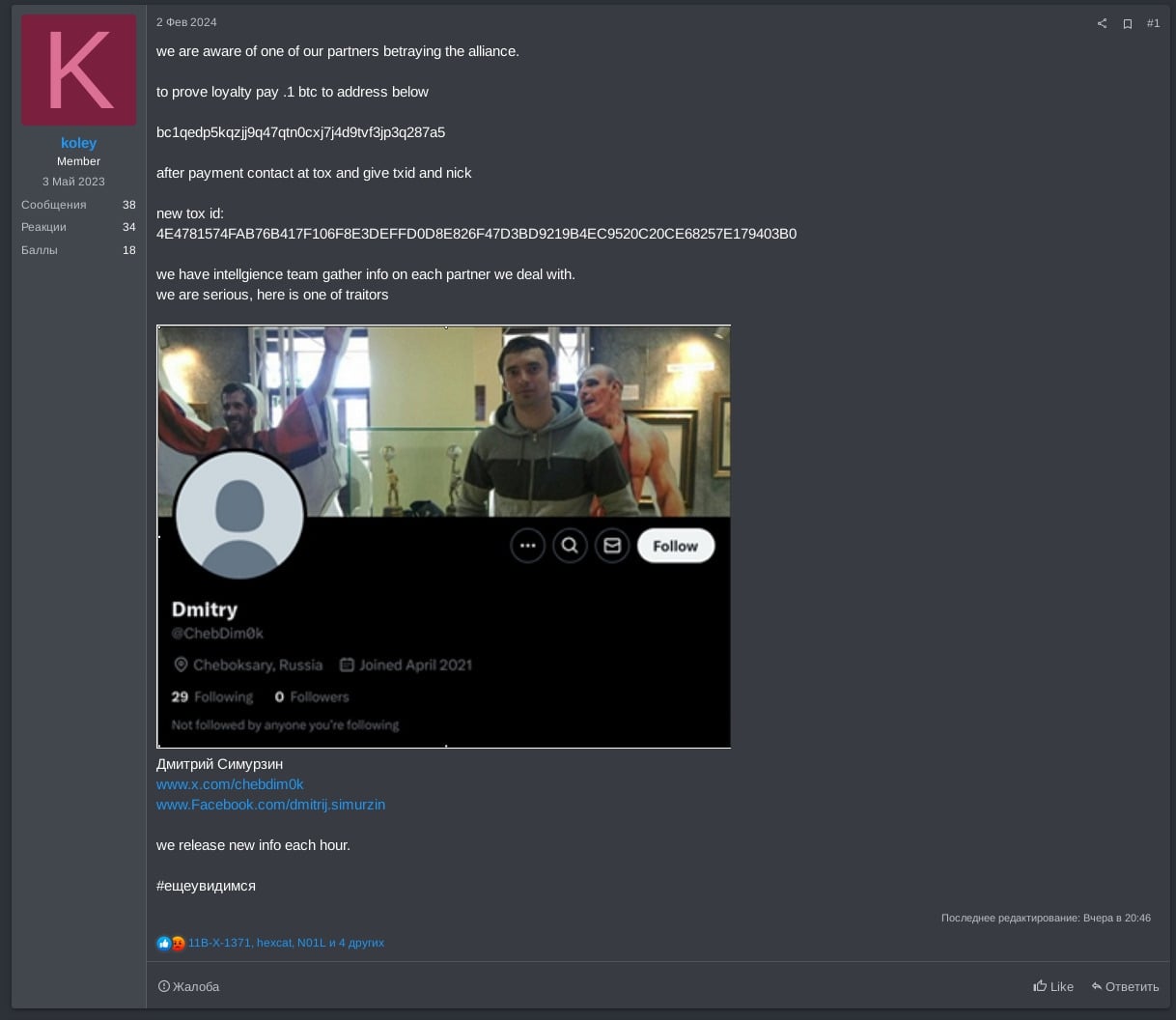
Furthermore, koley mentioned they know DragonForce has contacts within the Federal Security Services (FSB) of Russian, just as RansomHub, saying, “you ran into troubles, this is a war.”
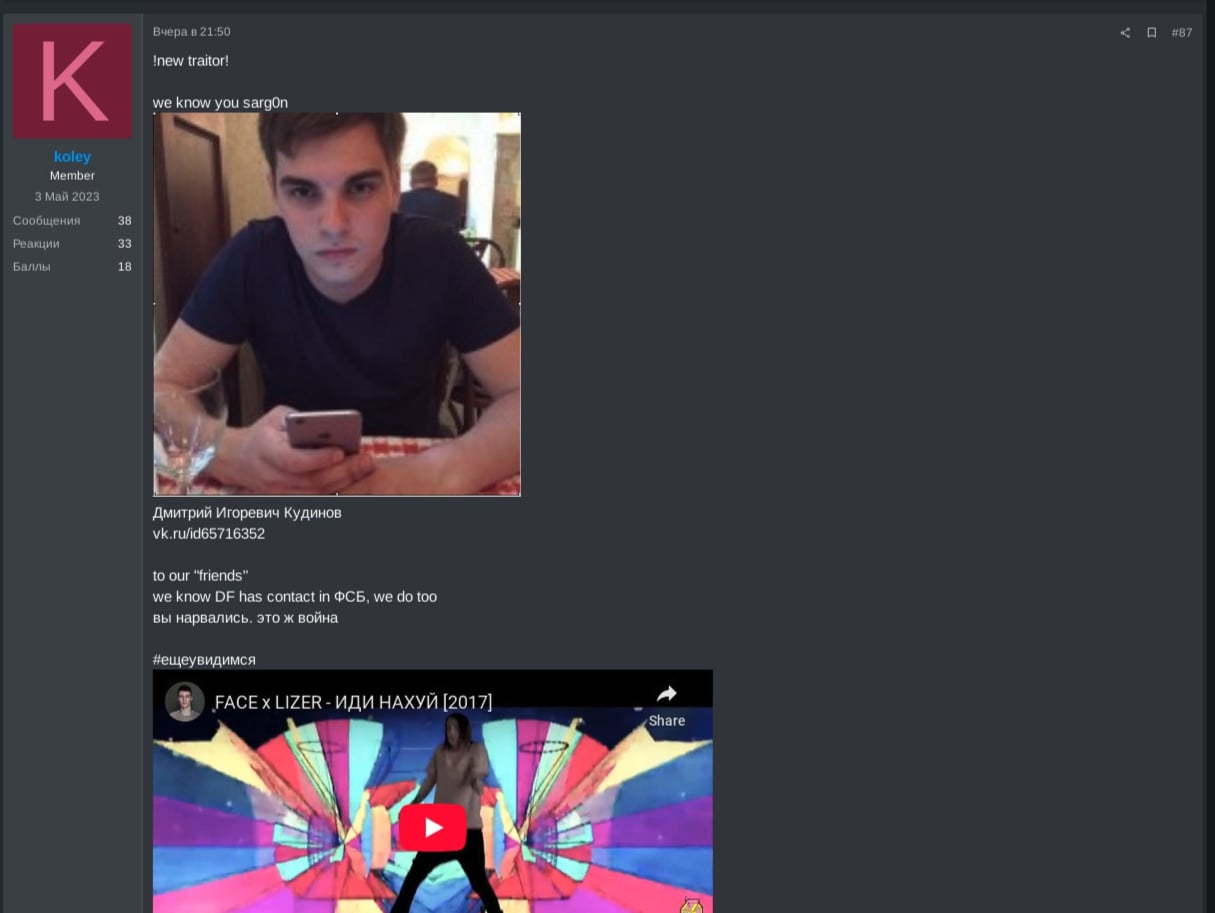
RansomHub operator koley further expressed outrage at DragonForce, accusing them of attacking Mamona RaaS and now RansomHub, referring to the DragonForce statement on Blacklock ransomware’s blog suggesting they “work without paranoia.” koley vehemently denied any affiliation with DragonForce's cartel, dismissing it as “fed honey” (law enforcement honeypot) and highlighting DragonForce's untrustworthiness, especially after their false denial of attacking RansomHub.
In a furious outburst, koley called dragonforce a coward and alleged that DragonForce leverages “feds to steal and shut others,” possibly referring to the FSB cooperation. RansomHub, in contrast, admitted to contacting “feds for traitors” only. The operator koley concluded with a grim warning to DragonForce: no more talks, next time we talk will be over your grave, see you in hell.
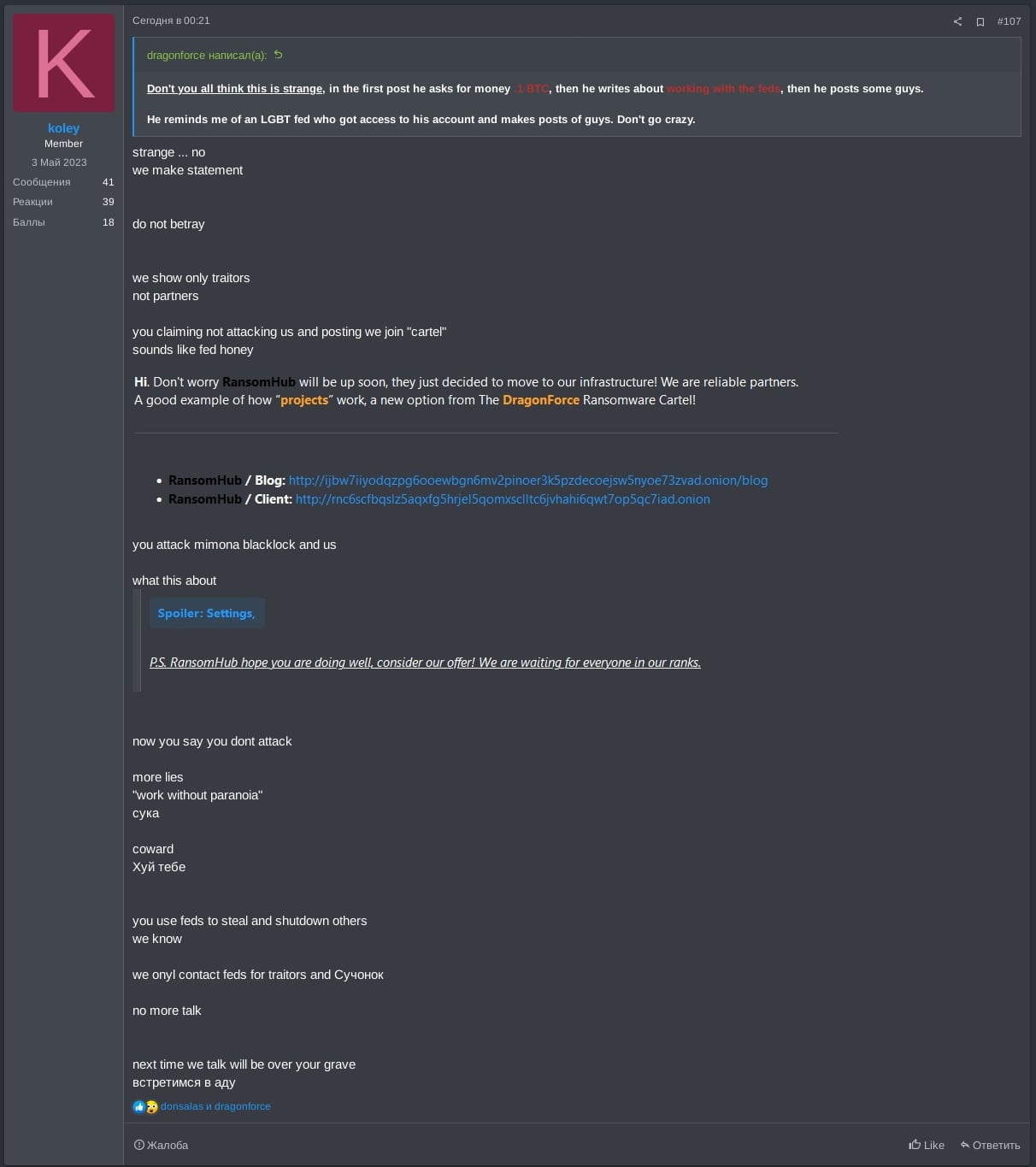
A few days later, koley suggested that DragonForce's TOR sites were down due to internal traitors within the gang. koley further alleged that RansomHub had hacked the DragonForce website in retaliation and insinuated that they had successfully infiltrated and attacked the DragonForce gang from within the RaaS, as shown in Figure 16.
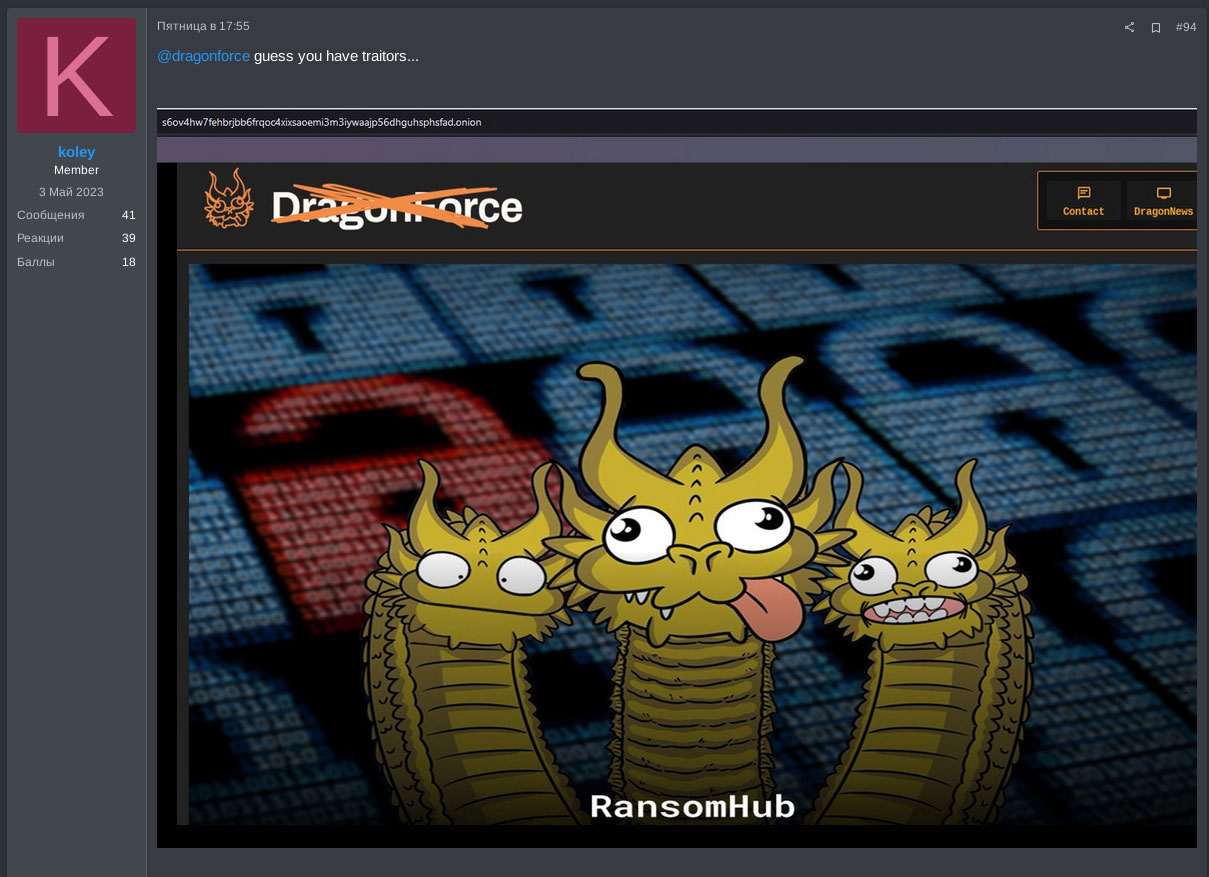
DragonForce reported they quickly restored their TOR infrastructure and they are currently transferring data. They contrasted their situation with RansomHub, whom they claim are forced to expose their partners and cooperate with authorities. DragonForce clarified that any attacks targeting critical infrastructure, hospitals, or CIS countries using their ransomware lockers are provocations by unscrupulous partners. Consequently, DragonForce stated they will strengthen their affiliate rules and limit access issuance to new affiliates.
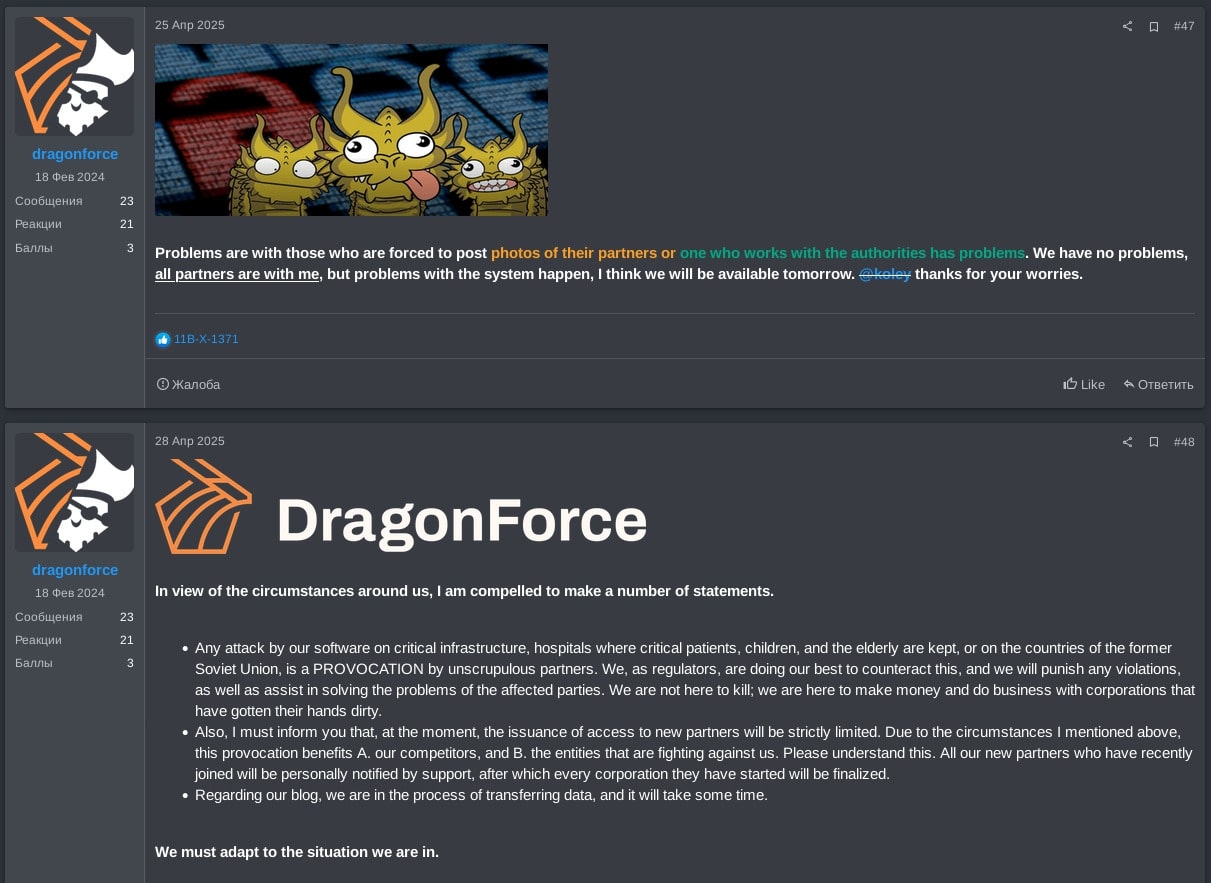
Subsequently, in late June 2025, DragonForce posted their new affiliates rules, where they stated new affiliates either need to be referred by existing members of DragonForce or provide a deposit of $10,000 USD, as shown in Figure 18.
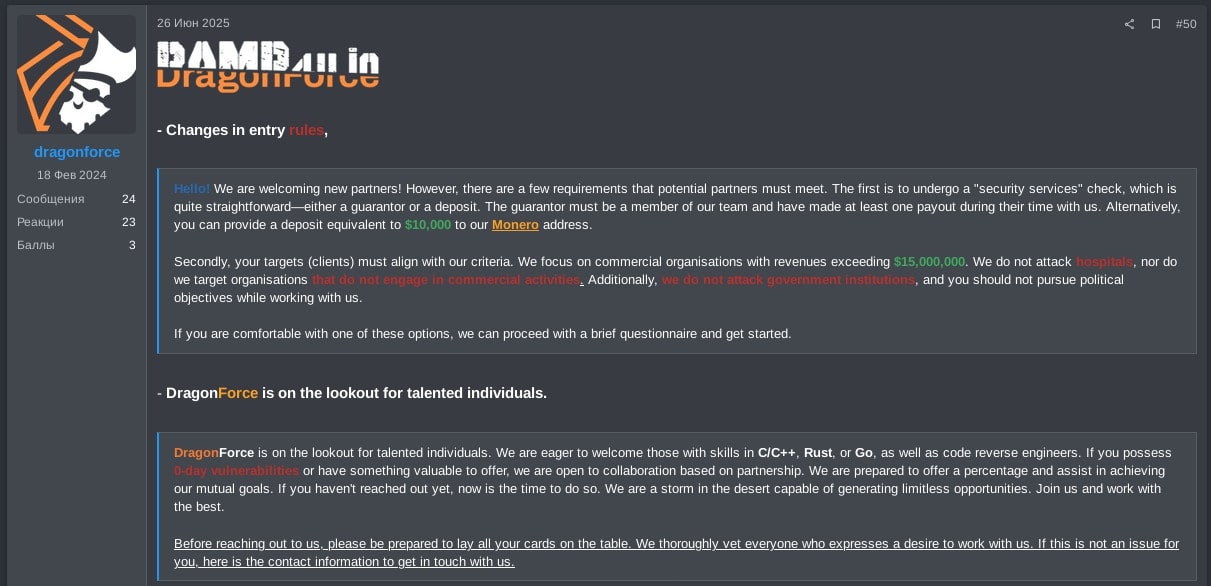
RansomHub, however, appears to have ceased operations, with their last victims posted on TOR sites in April 2025. Similarly, the RAMP threat actor koley has been inactive since April 2025 since declaring war on the DragonForce gang.
It is interesting to note that in early April 2025, an actor named Rjun claimed on the XSS underground forum that the Russian Internal Affairs Ministry thwarted RansomHub's attempted resurgence. This law enforcement intervention was attributed either to an alleged attack on critical infrastructure within CIS countries or a potential internal leak within RansomHub that compromised vital information:
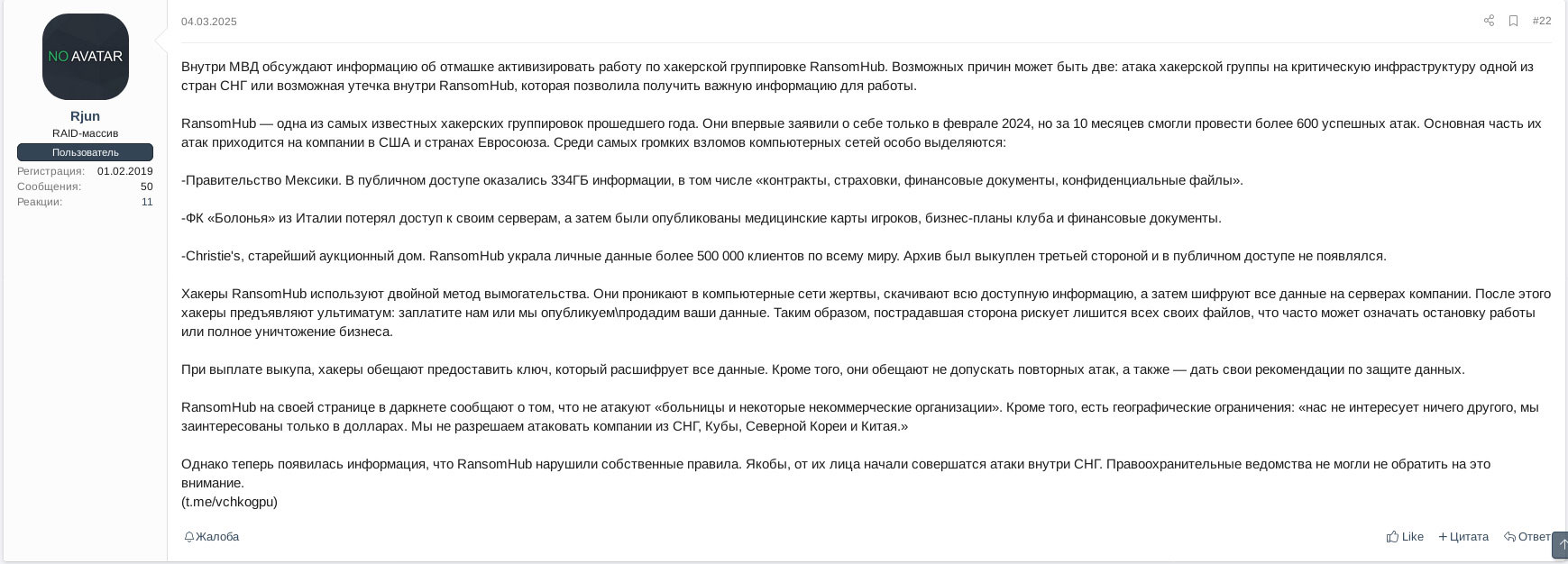
Translation of Figure 19:
None There are discussions within Ministry of Internal Affairs about the go-ahead to activate the work of RansomHub hacker group. There could be two possible reasons: an attack by the hacker group on the critical infrastructure of one of the CIS countries or a possible leak inside RansomHub, which allowed to obtain important information for work.
RansomHub is one of the most famous hacker groups of the past year. They first announced themselves only in February 2024, but in 10 months they were able to carry out more than 600 successful attacks. Most of their attacks are on companies in the United States and the European Union. Among the most high-profile hacks of computer networks, the following stand out:
-The Government of Mexico. 334 GB of information was made publicly available, including 'contracts, insurance, financial documents, confidential files'.
-FC Bologna from Italy lost access to its servers, and then the medical records of players, the club's business plans and financial documents were published.
-Christie's, the oldest auction house. RansomHub stole the personal data of more than 500,000 customers worldwide. The archive was bought by a third party and has not appeared in the public domain.
RansomHub hackers use a double extortion method. They penetrate the victim's computer networks, download all available information, and then encrypt all data on the company's servers. After that, the hackers present an ultimatum: pay us or we will publish/sell your data. Thus, the victims risks losing all their files, which can often mean a work termination or the complete destruction of the business.
When paying the ransom, the hackers promise to provide a key that will decrypt all data. In addition, they promise to prevent repeated attacks, as well as give their recommendations on data protection.
RansomHub states on their dark web page that they do not attack 'hospitals and some non-profit organizations'. In addition, there are geographic restrictions: 'we are not interested in anything else, we are only interested in dollars. We do not allow attacks on companies from the CIS, Cuba, North Korea and China'.
However, now information has emerged that RansomHub has violated its own rules. Allegedly, attacks have begun to be carried out on their behalf within the CIS. Law enforcement agencies could not help but pay attention to this.
(t.me/vchkogpu)
The Trellix Advanced Research Center could not validate the above claim as we suspect Rjun is a rival ransomware operator themselves. However, it is evident that ransomware gangs are intensely competitive, readily setting up rivals, damaging their reputation, and ultimately causing the shutdown of RaaS programs. Additionally, certain ransomware operators appear willing to cooperate with local law enforcement. This cooperation may involve seeking protection and approval for their illicit activities, or providing information about affiliates deemed rivals or traitors.
We are observing conflicts between RaaS programs lead to ransomware gangs restricting access to new affiliates and/or scrutinizing the loyalty of current ones. They fear traitors and competitors who seek to provoke them by infiltrating their RaaS and violating rules (e.g., attacking CIS entities) to undermine them or harm their reputation.
Furthermore, ransomware gangs are growing increasingly vigilant, carefully checking their infrastructure and software before rollout. This is a direct response to competitors known for pentesting the ransomware gangs infrastructure and publicly exposing weaknesses, which deters potential new affiliates from joining.
Qilin versus LockBit
In mid-April 2025, Qilin ransomware operator Haise posted on the RAMP forum they are looking for new affiliates to join their RaaS. LockBit replied saying they don't like the gang’s name which to them sounds like “Culin” or “Cunnilin” and they would not work with a RaaS with such a name.
Haise’s immediate response was to say people do not want to work with a ransomware group which is constantly scamming its affiliates. Haise referred to a scam in January 2024 when LockBit-related monikers were banned from XSS and Exploit forums due to not paying $4 million USD to LockBit affiliate michon for providing corporate access to the victim’s network.
This was controversial and LockBit refused to pay their affiliate. However, RAMP administrators decided to not ban LockBit on the forum, contrary to other two reputable underground forums. Haise’s accusation of LockBit running a scam RaaS flared LockBit up and they demanded Haise provide proof of the scam and create a complaint on the RAMP forum instead of the “bullshit” they say about LockBit gang.
The underground forum fight continued by LockBit stating, “Cunnilini will soon die out, don't ask why, relay this admin panel with auto-registration to your affiliates and don’t enter it yourself, 5 minutes and you are ready to start working.” Haise refrained from creating a black (a complaint on the forum), stating they “don’t see the point to ban anyone. Many affiliates are coming to Qilin and telling us about problems with LockBit and how LockBit scammed them.”
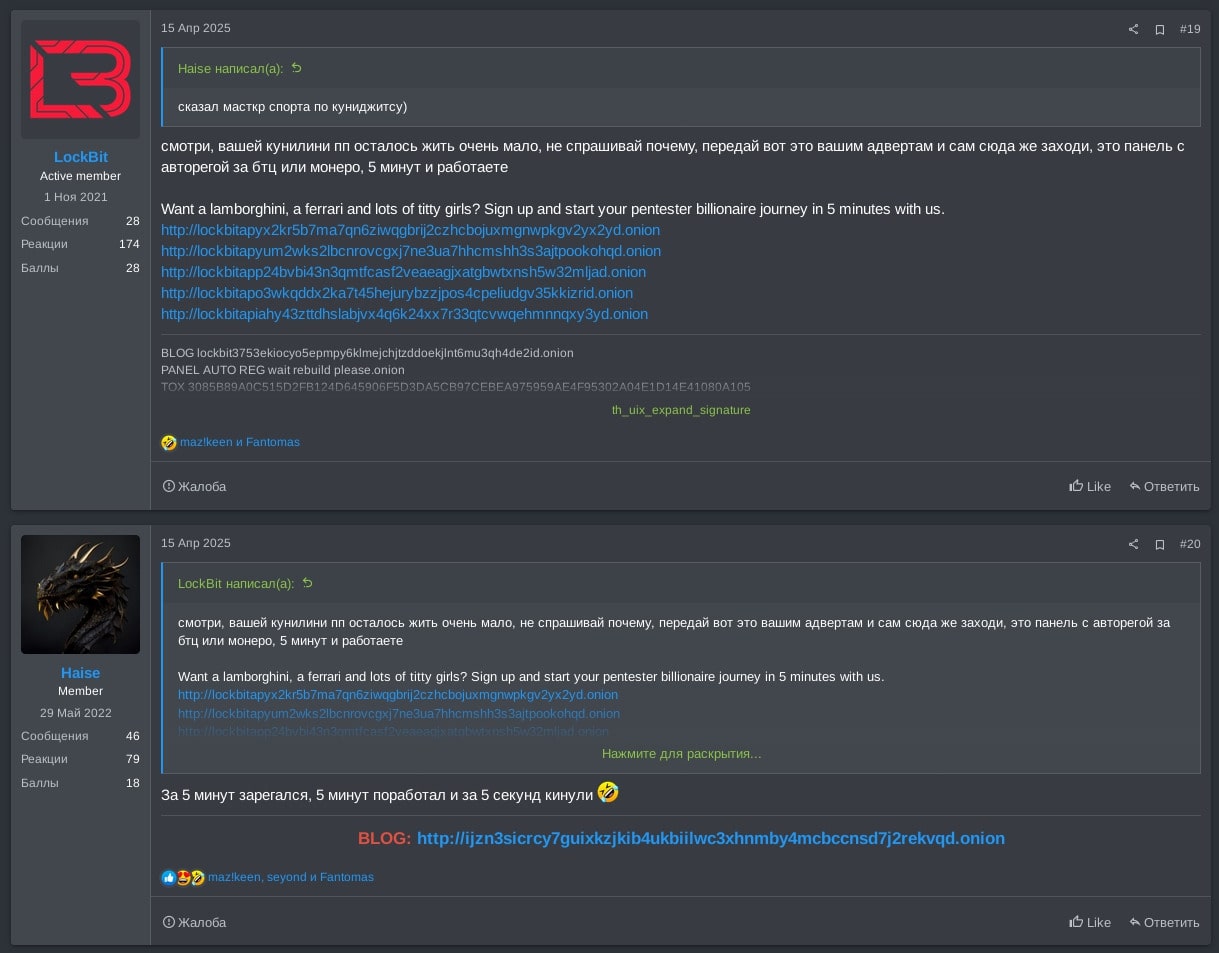
Translation of Figure 20:
None LockBit: Reply to Haise's comment 'Said the master of sport in cunnijutsu)': Look, your cunnilini partner program wont' leave long, don't ask why, tell your adverts and dont enter yourself, this is a panel with auto-registration for BTC or Monero, 5 minutes and you get to work
Haise: Registered within 5 minutes, 5 minutes of working and 5 minutes until you get scammed :rolling_on_the_floor_laughing:
Haise continued, “I am not going to provide proof to anyone. Those who are in ransom theme would know and understand, and the newbies should read the messages and draw their own conclusions.”
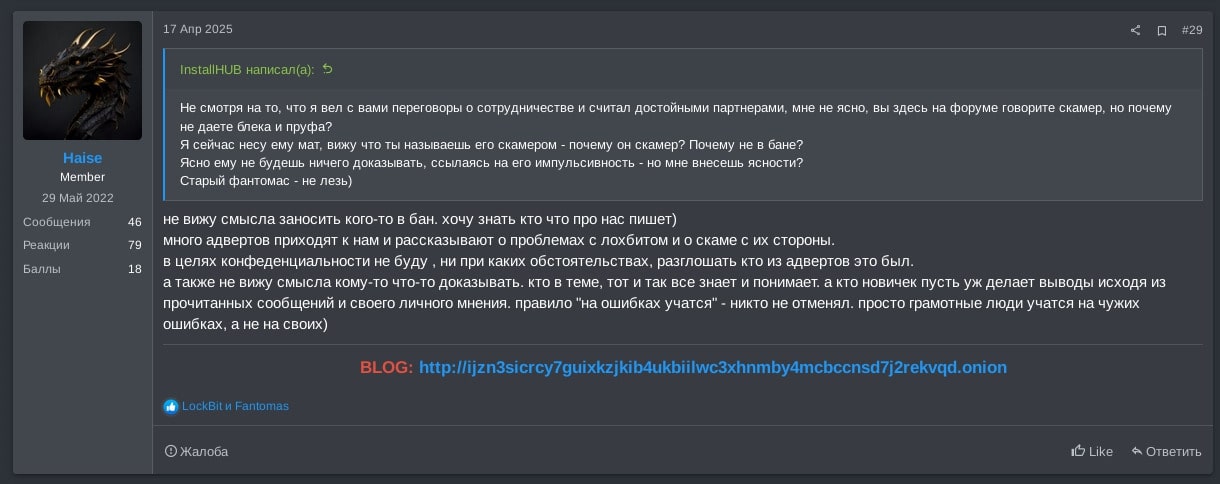
Translation of Figure 21:
None Haise: Reply to InstallHUB's post 'Regardless of our talks on collaboration and me regarding you as a respectable partner, I am puzzled why are you accusing LockBit being a scammer on the forum but don't provide any black or proofs?
I am about to give LockBit data and seeing that you call him a scammer - why is he a scammer? If so, why was not he banned?
It is clear you cannot prove anything to LockBit referring to his impulsiveness - but can you clarify that to me?
Old Fantomas - please stay out of this)'
I don't see any point to ban anyone. I want to know who is writing what about us)
Many adverts come to us and tell about problems with LockBit and the scam from his side.
For confidentiality purposes, under no conditions, I am revealing the advert names.
Also I dont see the point to prove anything to anybody. Everyone who is in the 'theme' already know and understand things. As for the newbies, let them read the messages and make their opinions and draw their own conclusions. Nobody cancelled the rule 'you learn by making mistakes'. It is just smart people learn from mistakes of others and not from their own)
Furthermore, when LockBit’s admin panel got leaked, Haise eagerly jumped into analyzing the leak and was among the first to share their findings in the RAMP general chat box, as shown in Figure 22.
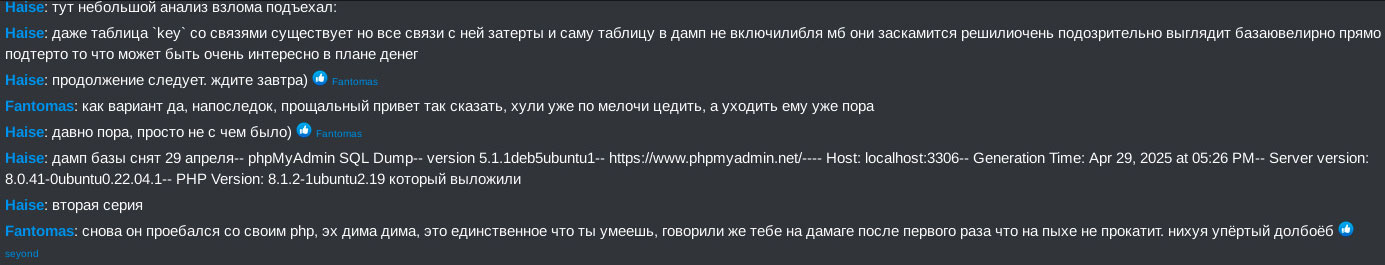
Translation of Figure 22:
None Haise: here a small analysis of the hack:
Haise: even the table 'key' with constrains exists but all links in the table are erased and it was not included in the dump perhaps they decided to exit scam looks very suspicious the db is carefully cleaned from anything which might be interesting in terms of money
Haise: to be continued. wait for tomorrow)
Fantomas: As an option, yes, final hi to say so, why would he sift through small amounts, it is already time for him to go
Haise: Indeed already the high time, he just did not have anything to leave with)
Haise: db dump taken 29 april-- phpMyAdmin SQL Dump-- version 5.1.1deb5ubuntu1-- https://www.phpmyadmin.net/---- Host: localhost:3306-- Generation Time: Apr 29, 2025 at 05:26 PM-- Server version: 8.0.41-0ubuntu0.22.04.1-- PHP Version: 8.1.2-1ubuntu2.19 which was leaked
Haise: second episode
Fantomas: Again he fucked up with his php, eh dima dima, that is the only thing you skilled at, did not people on DaMaGe forum already warn you the first time that you won't go far with php, you stubborn fuck
It's remarkable how ransomware rivals not only clash but are also willing to help out with examining the competitors' infrastructure when leaks occur. They are even willing to assist security researchers in analyzing leaked data to uncover potential issues, inefficiencies, and weaknesses that could undermine ransomware groups and possibly lead to the closure of RaaS operations.
When RaaS operations shut down, often due to exit scams or law enforcement intervention, their ransomware affiliates frequently seek out reputable competitors. A prime example is the alleged law enforcement intervention against RansomHub RaaS, which led many of their affiliates to approach LockBit. LockBit even temporarily set aside their LockBit 5.0 update to handle the influx of requests and quickly capitalize on new opportunities. Similarly, in the ongoing Qilin and LockBit dispute, LockBit publicly asserted Qilin's imminent closure, urging Qilin affiliates to join LockBit RaaS if they “want a Lamborghini.”
Qilin and LockBit are two of the most active ransomware groups currently operating. The Trellix Advanced Research Center is closely monitoring these RaaS groups and interested to observe how their ongoing feud unfolds in the future.
Conclusion
We used to fight families. Now we’re facing franchises and freelancers. But one thing hasn’t changed: when trust breaks down, empires fall.The ongoing disputes within the ransomware underground we have highlighted in this blog are more than just isolated incidents; they are symptomatic of fundamental cracks in the historic RaaS model.
What was once a seemingly cohesive, if illicit, ecosystem is now splintering under the weight of internal distrust and external pressure. The pervasive uncertainty, amplified by successful law enforcement interventions, has eroded the very foundation of cybercriminal collaboration: trust.
This crumbling trust model directly fuels increasing public feuds, betrayals, and retaliatory attacks. As loyalty becomes a liability and self-preservation the primary driver, the consequences extend beyond mere infighting. A significant reduction in trust within the underground inevitably stifles innovation and hampers the collaborative efforts that have historically enabled the rapid evolution and expansion of ransomware operations. In this fragmented landscape, the future of the RaaS model looks increasingly bleak.
In the escalating conflicts among ransomware gangs, survival hinges on innovation, resilience, and adaptability. Only those who can assure their affiliates of “work without paranoia” will endure as trust in RaaS programs continues to erode.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.