ARCHIVED STORY
How FireEye Endpoint Security Protects Against Ransomware (Like DARKSIDE)
By Ryan Delany · May 20, 2021
Although reports indicate that DARKSIDE ransomware operations have shut down, the issue of ransomware itself is only getting worse. We’ve all seen the impact that ransomware can have on critical operations, so organizations across all industries must remain vigilant to reduce risk and combat the threat. Unfortunately, the battle is asymmetrical. Threat groups are constantly shifting their tactics, techniques, and procedures (TTPs) to try to bypass security, and defenders need to keep up.
The recent high-profile attack involving DARKSIDE is an example of ransomware-as-a-service (RaaS). In this model, one group creates and maintains the service and another group uses the service to target victims, sharing any ransoms received with the “service provider.” The attacking group uses the tools just like a developer using open source code. These types of attacks can happen quickly, and organizations need to have the right tools in order to adequately detect and respond to them.
FireEye Endpoint Security uses multiple protection engines and customer deployable modules built from the experience of front-line responders to defend against these types of attacks. The combination of signature-based, machine-learning based, and behavioral-based protection capabilities, the UAC Protect module, and the Process Guard module for FireEye Endpoint Security provide maximum protection for customers. FireEye has verified that all currently available DARKSIDE samples are proactively blocked by FireEye Endpoint Security.
To use Endpoint Security to defeat techniques used by DARKSIDE and other ransomware operators, FireEye recommends enabling the following settings and feature configurations as outlined in this post:
- Malware Protection – Signature-based and Machine-learning based protection
- UAC Protect – Module that protects against User Access Control (UAC) Bypass Attacks
- Process Guard – Module that protects against Credential Dumping
- Real-Time Indicator Detection – Indicator of Compromise detection
Malware Protection
Navigate to Admin -> Policies.
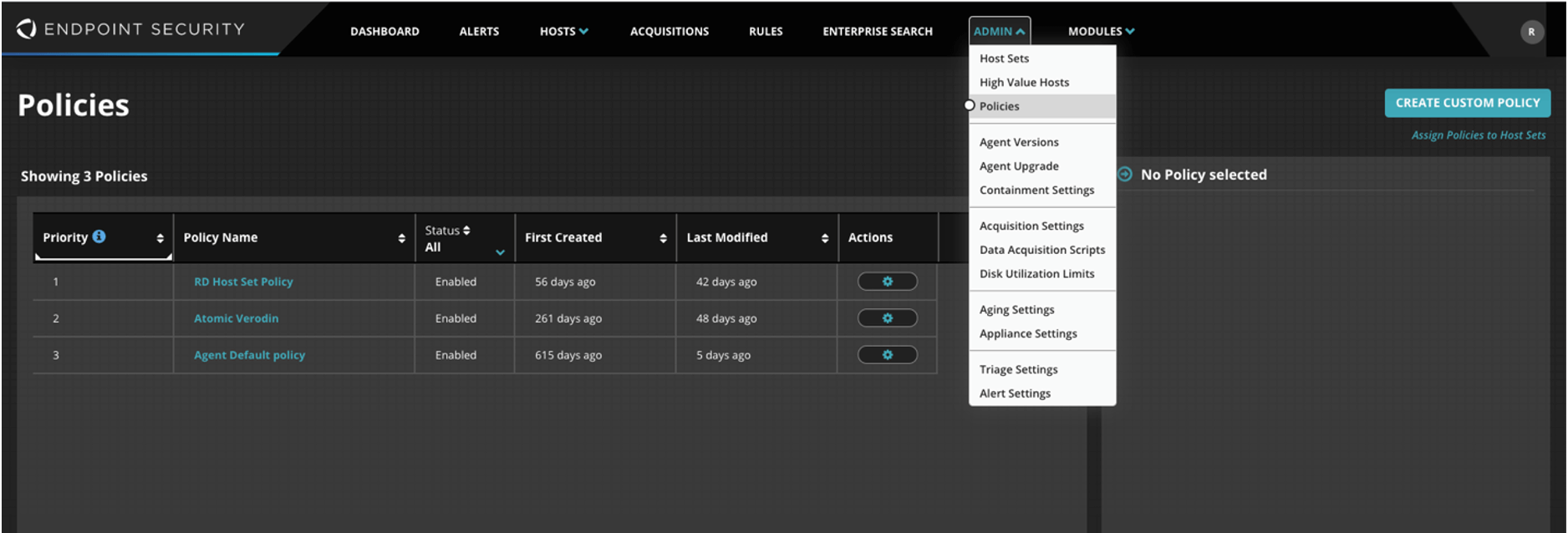
Select the desired policy (or policies).
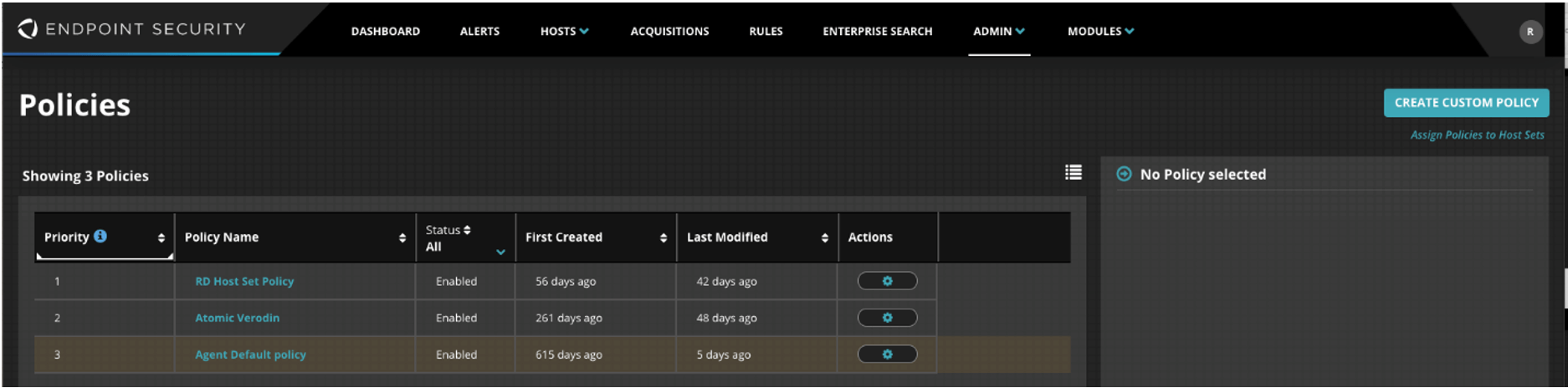
Select Malware Protection.
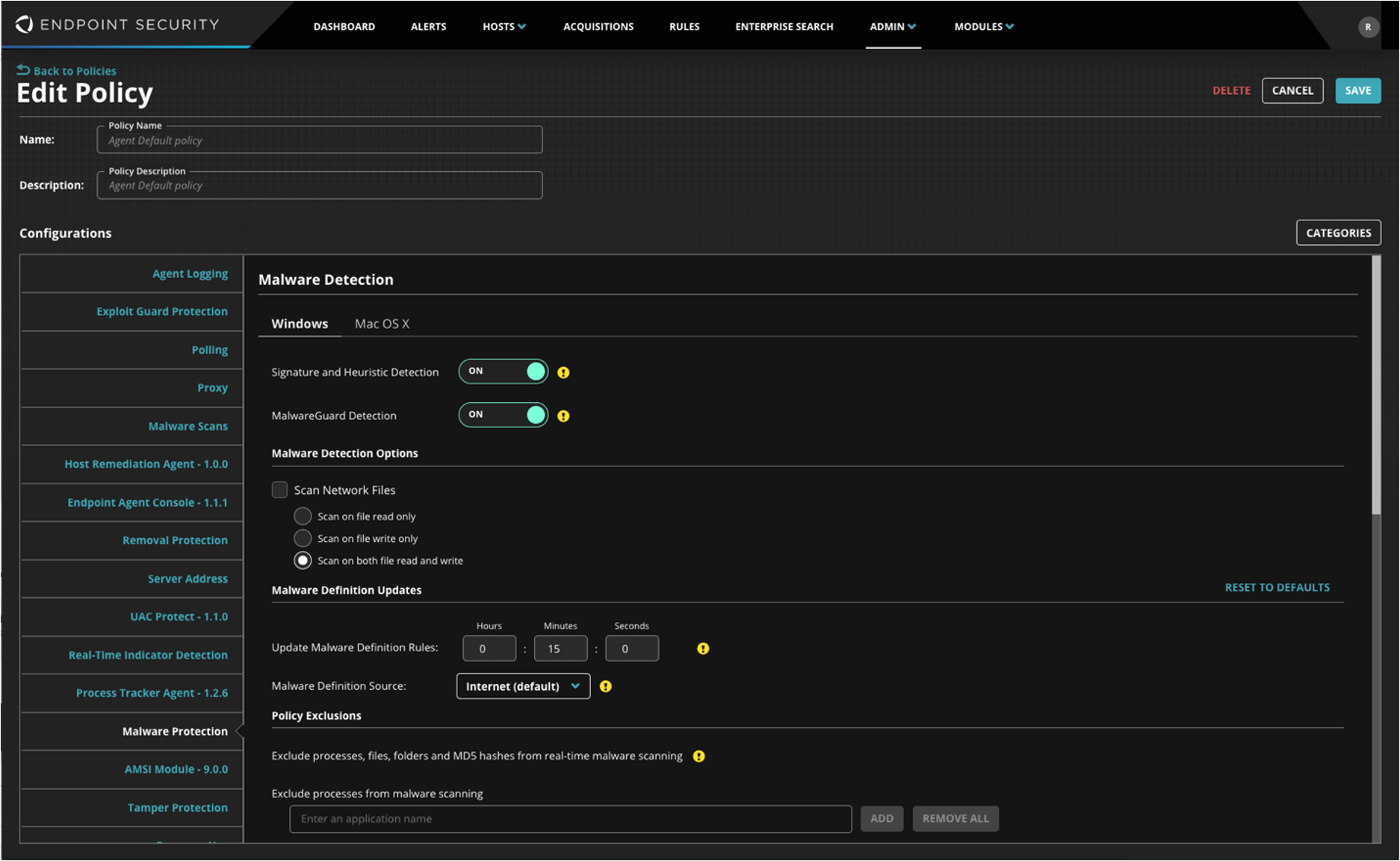
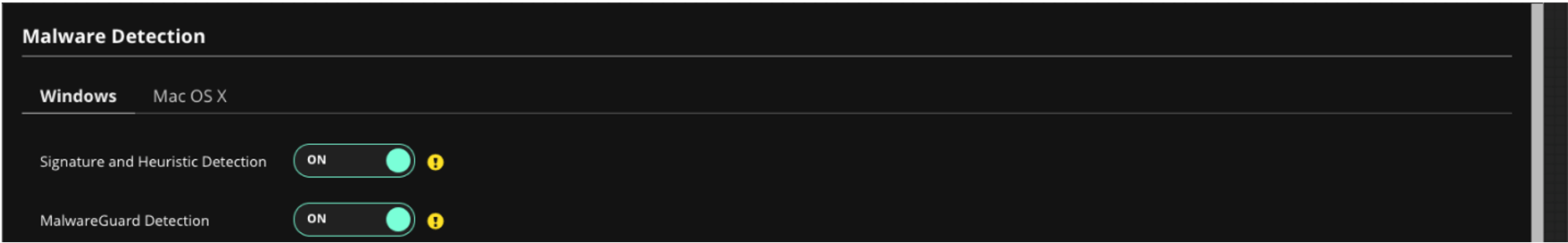
Malware Detection
Switch Signature and Heuristic Detection to ON, and switch MalwareGuard Detection to ON.
Quarantine
Switch Signature and Heuristic Quarantine to ON, and switch MalwareGuard Quarantine to ON.

Click Save.
UAC Protect
DARKSIDE and similar threats also abuse the User Access Control feature of Windows, so it’s important to download, install, and enable the UAC Protect module for FireEye Endpoint Security. This will help reduce the attack surface for DARKSIDE and other types of attacks and increase overall security posture. This video provides information about protecting against UAC Bypass Attacks with UAC Protect for FireEye Endpoint Security.
Download
Visit FireEye Market.

Download UAC Protect.
Install
Navigate to Modules -> HX Module Administration.
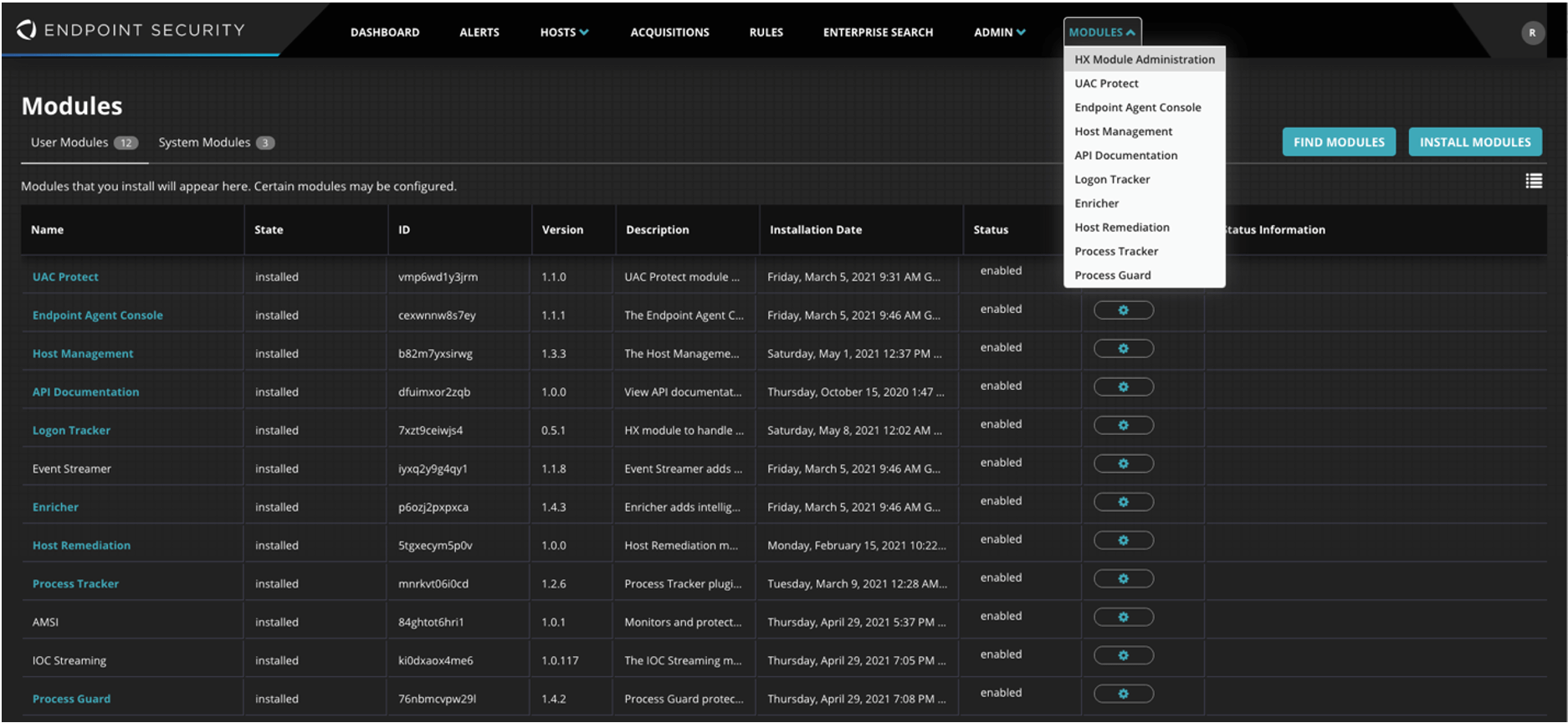
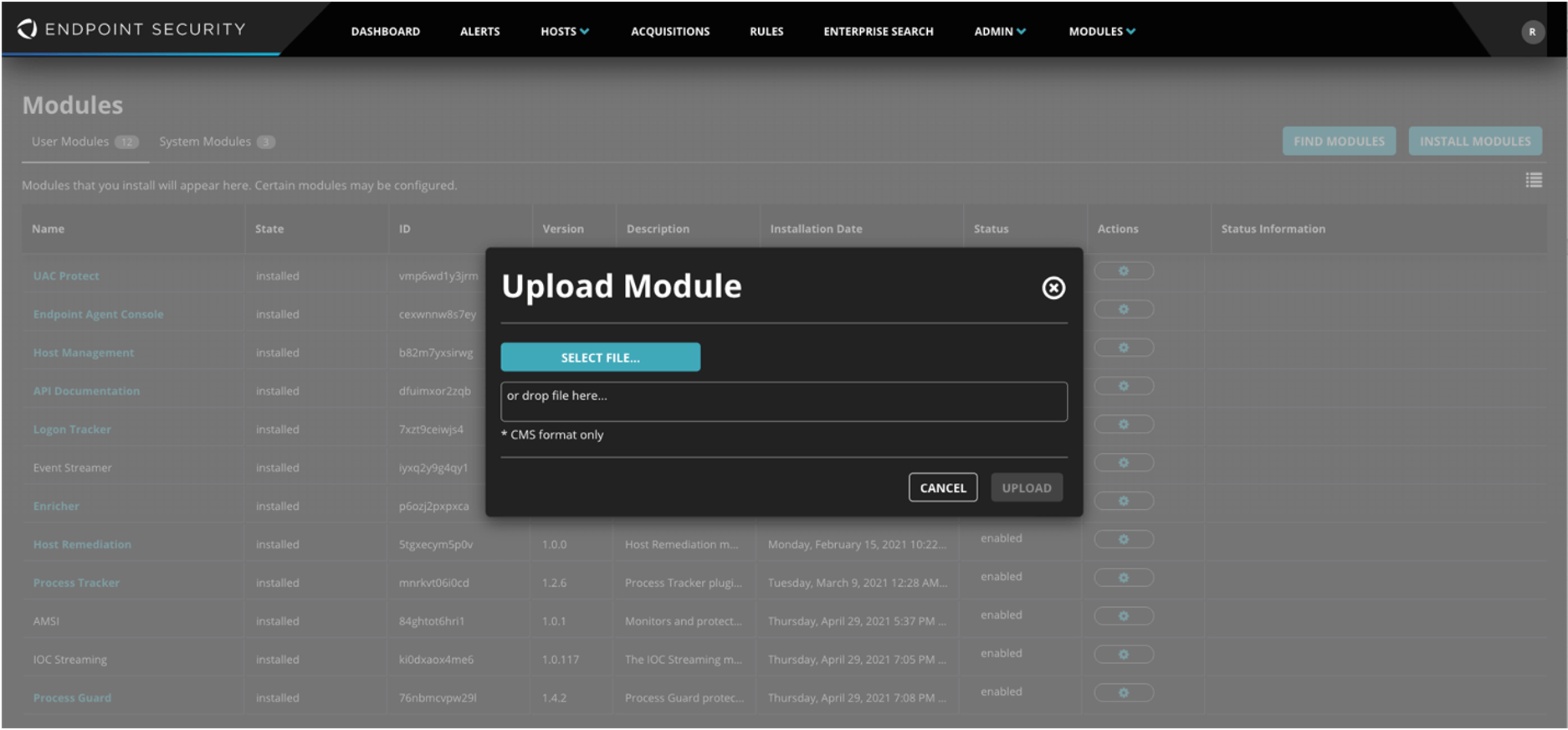
Click INSTALL MODULES and select the UAC Protect module downloaded in the previous step.
Enable
Navigate to Admin -> Policies.
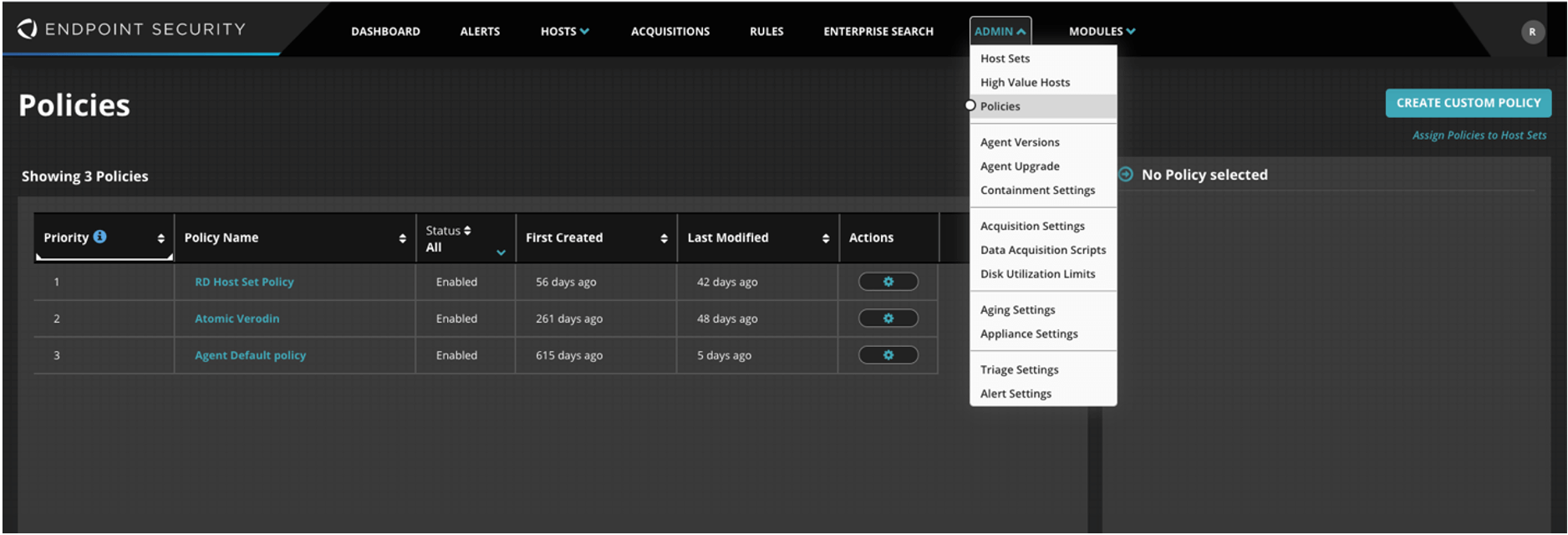
Select the desired policy (or policies).
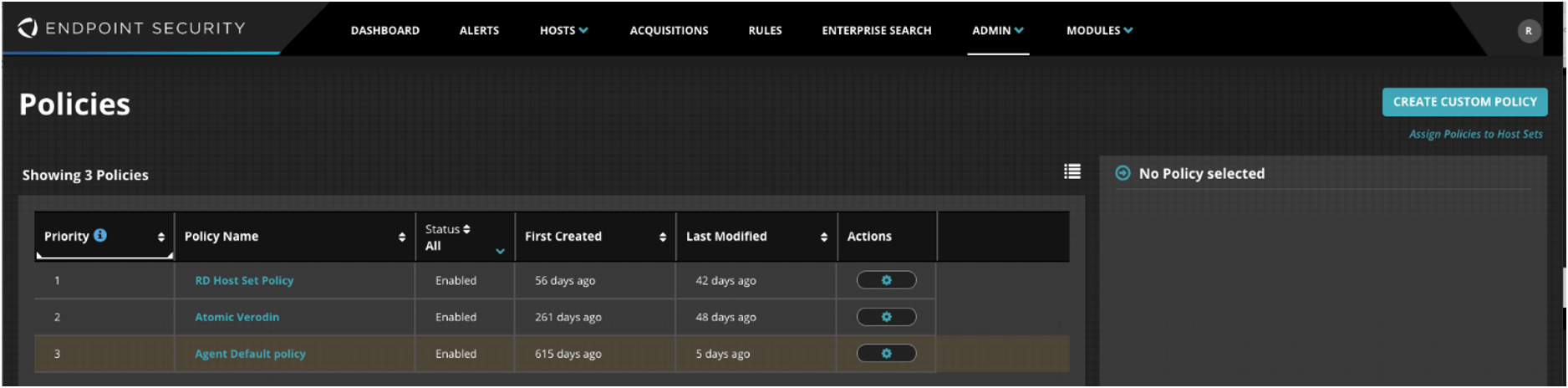
Select UAC Protect and switch Enable module for hosts to On.
Click Save.
Process Guard
Credential dumping is a popular technique used for privilege escalation in many attacks, including those perpetrated by DARKSIDE. The Process Guard module for FireEye Endpoint Security can protect against common credential dumping attacks so it’s important to download, install, and enable the Process Guard module for FireEye Endpoint Security. More information about using Process Guard to protect against these types of attacks is available in this video.
Download
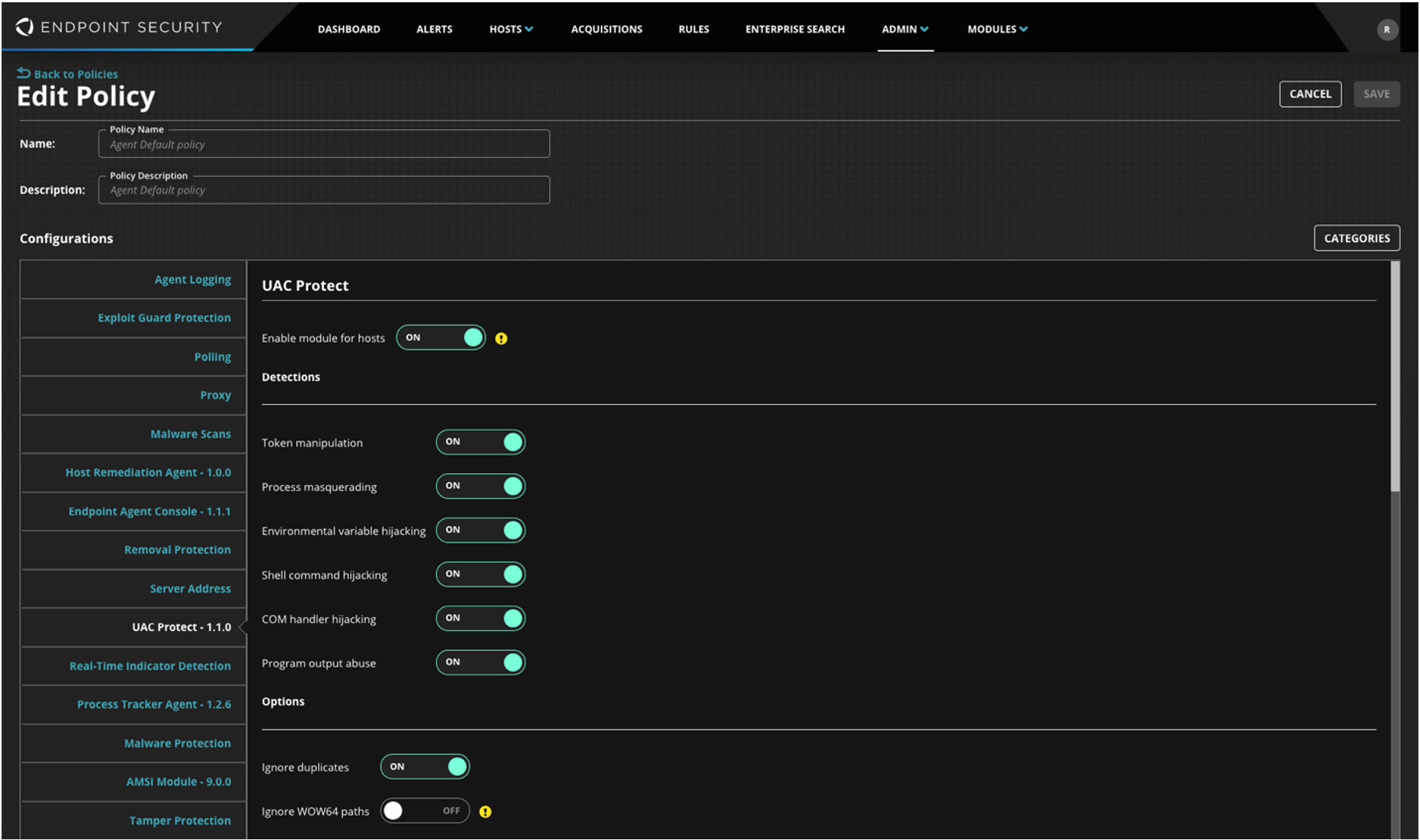
Visit FireEye Market and download Process Guard.
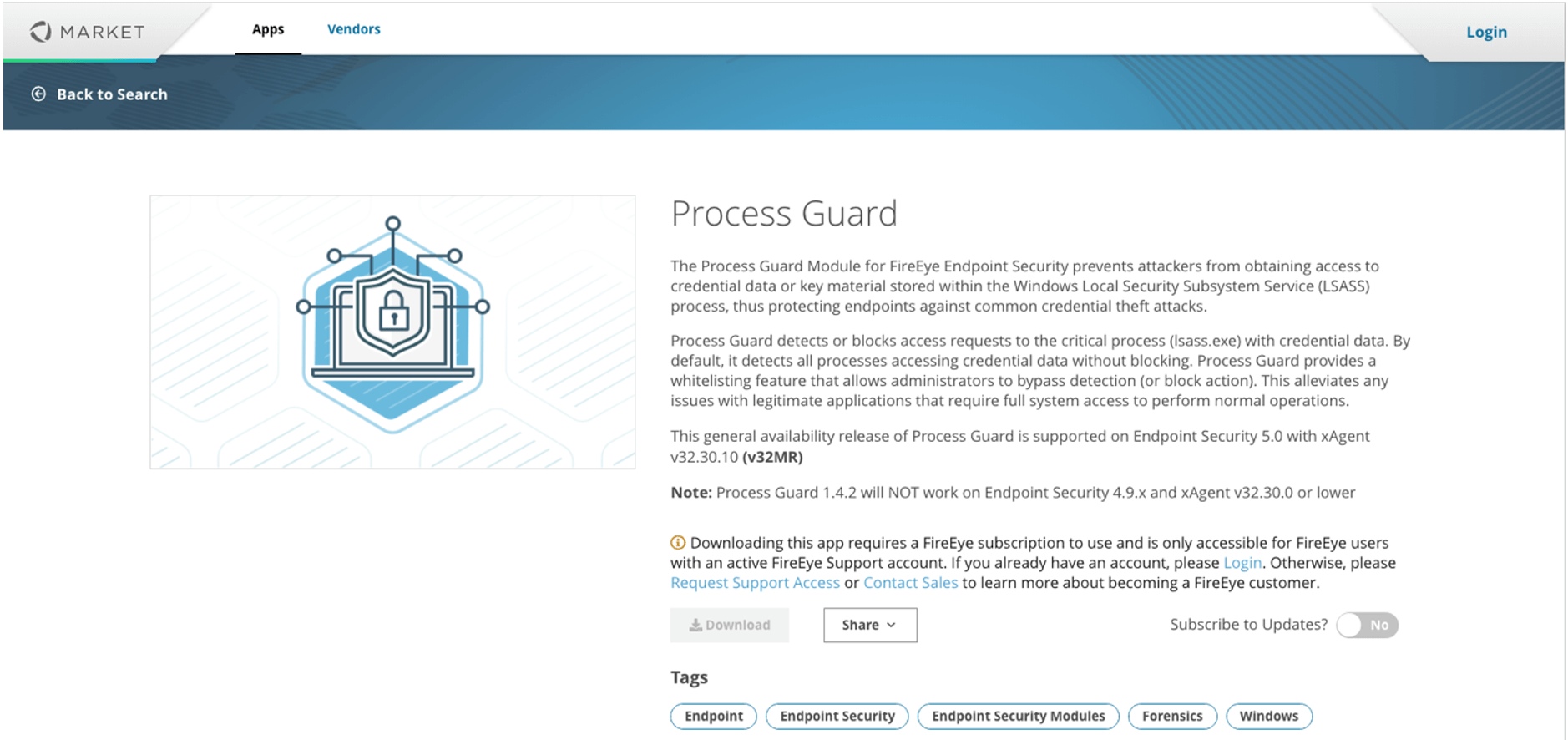
Install
Navigate to Modules -> HX Module Administration.
Click INSTALL MODULES and select the UAC Protect module downloaded in the previous step.
Enable
Navigate to Admin -> Policies.
Select the desired policy (or policies).
Select Process Guard.
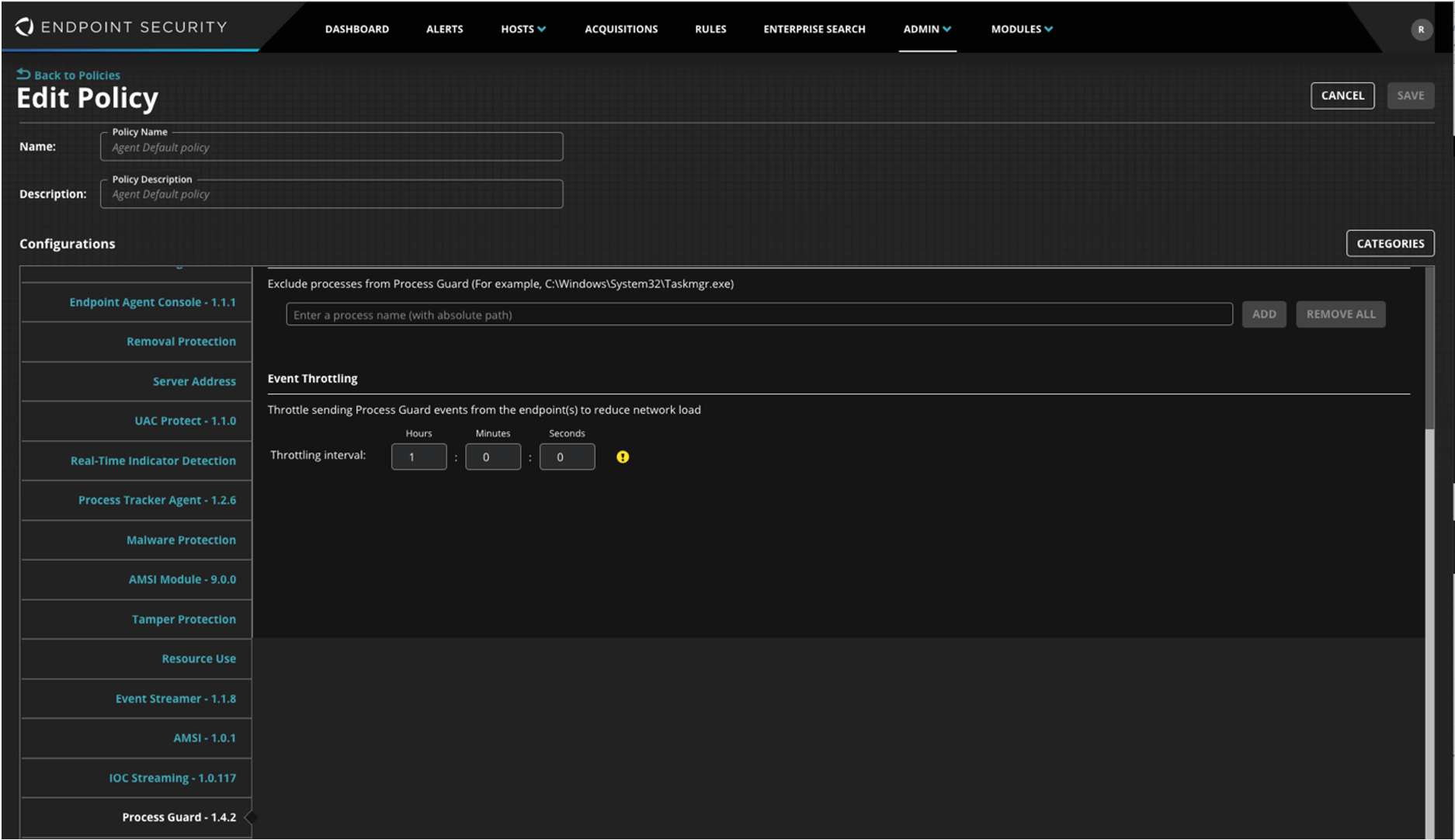
Switch Enable Process Guard on the host to ON, and switch Block on Detection to ON.
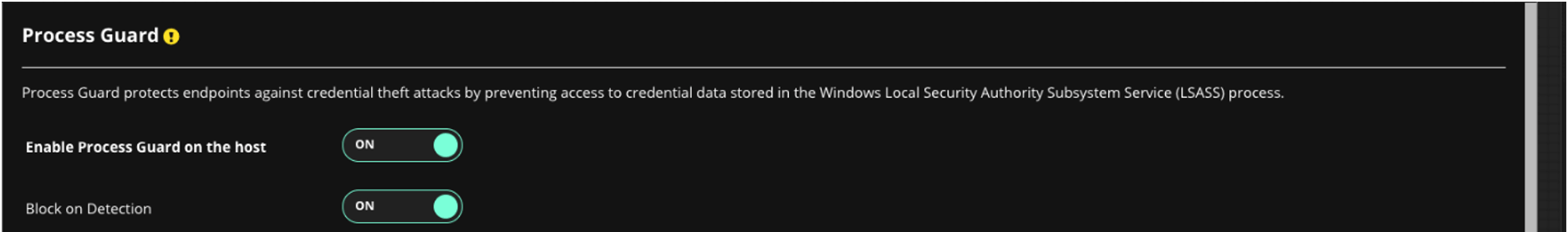
Click Save.
Real-Time Indicator Detection
FireEye Endpoint Security can also be configured to alert based on IOC detections related to DARKSIDE and other similar threats. In order to enable that functionality, follow the steps below to ensure that Real-Time Indicator Detection is enabled in the environment.
Navigate to Admin -> Policies.
Select the desired policy (or policies).
Select Real-Time Indicator Detection and switch Real-Time Indicator Detection to ON.
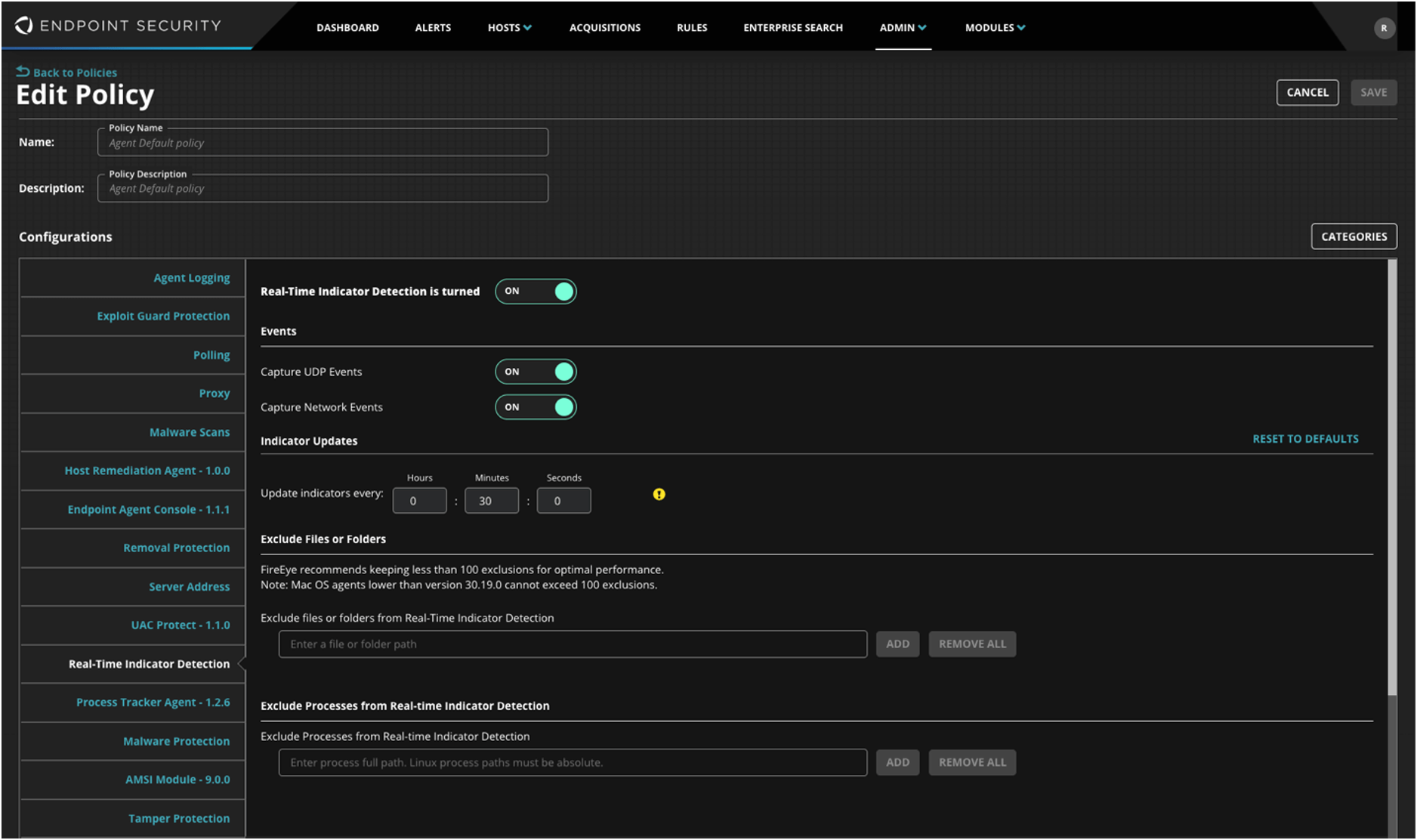
Click Save.
Summary
FireEye Mandiant has been tracking DARKSIDE since August 2020 and proactively providing protection to customers as samples and techniques are discovered on the front lines during investigations by Mandiant. Customers should ensure they have configured and enabled FireEye products to protect against threats such as DARKSIDE using the information in this post. Additionally, Mandiant Managed Defense customers can reach out for assistance in configuring and operating FireEye products to provide maximum protection.
FireEye solutions and Mandiant services offer comprehensive coverage against DARKSIDE and other threats that matter most. Head over to our site to learn more about how FireEye Endpoint Security, Email Security, Network Security, and Helix, the FireEye security operations console, provide a layered approach to security that helps organizations see the bigger picture.
RECENT NEWS
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
-
Oct 28, 2025
Trellix AntiMalware Engine secures I-O Data network attached storage devices
-
Oct 23, 2025
Trellix CyberThreat Report Reveals Blurring Lines Between Nation-State Espionage and Financially Motivated AI Attacks
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.