What Is Ransomware?
Understanding and Preventing Ransomware Attacks
Reviewed by Ryan Delany · September 5, 2025
Ransomware is a type of malicious software, or malware, that encrypts a victim's personal data, making files and the systems that rely on them unusable, until a ransom is paid. Attackers then demand a payment, typically in difficult-to-trace digital currencies like Bitcoin, other cryptocurrencies, or pre-paid voucher services like PaysafeCard, in exchange for a decryption key to restore access to the victim's data.
E-BOOK
The Mind of the CISO: Closing the gap between reaction and readiness
Discover insights on the evolving threat landscape from more than 500 global CISOs.
The primary goal of ransomware is almost always financial gain through extortion. Victims are coerced into paying for the ransomware to be removed, either by receiving a program to decrypt files or an unlock code.
Ransomware is often designed to spread across a network and target database and file servers, and can thus quickly paralyze an entire organization. It is a growing threat, generating billions of dollars in payments to cybercriminals and inflicting significant damage and expenses for businesses and governmental organizations.
According to the recent Trellix “Mind of the CISO” eBook (see above), 93% of CISOs surveyed agree that ransomware is a serious concern, with 90% stating it has increased over the past twelve months. About a quarter of the CISOs surveyed report these groups pose the most risk to their organizations: RansomHub (29%), LockBit3 (26%), KillSec3 (23%), and Medusa (22%).
How ransomware works
- Infection. Ransomware attacks are typically carried out using a Trojan, often disguised as a legitimate file, that the user is tricked into downloading or opening, commonly arriving as an email attachment. However, some strains, like the WannaCry worm, can spread automatically between computers without user interaction. It can also spread through malvertising, social engineering, exploit kits, or drive-by downloading from infected websites.
- Payload and Encryption. Once ransomware enters a computer, it secretly infects it, attacks files, and alters credentials. The most sophisticated payloads encrypt files using strong encryption, ensuring that only the malware author possesses the necessary decryption key.
The attacker makes the decryption key available to the victim only after the ransom is paid. Without access to the decryption key, it is nearly impossible to decrypt the files that are being held for ransom. Some ransomware may also delete volume shadow copies to prevent recovery. - Ransom Demand. After encrypting files, the ransomware displays a message to the victim, outlining the payment amount and instructions to regain access. The ransom can range from a few hundred to millions of dollars. Attackers often use untraceable payment methods to avoid identification. Sometimes, the ransom increases if payment is not made promptly.
- Decryption. Once payment is received, the attacker should decipher the encrypted key with their private key and send it to the victim, allowing the victim to decrypt their data. However, that is not always the case, as seen in recent ransomware campaigns.
Ransomware response steps
If you suspect you’ve been hit with a ransomware attack, it’s important to act quickly. Fortunately, there are a number of steps you can take to give you the best possible chance of minimizing damage and quickly returning to business as usual.
Isolate the Infected Device. Ransomware that affects one device is a moderate inconvenience. Ransomware that is allowed to infect all of your enterprise’s devices is a major catastrophe, and could put you out of business for good. The difference between the two often comes down to reaction time.
To ensure the safety of your network, share drives, and other devices, it’s essential that you disconnect the affected device from the network, internet, and other devices as quickly as possible. The sooner you do so, the less likely it is that other devices will be infected.
Stop the Spread. Because ransomware moves quickly—and the device with ransomware isn’t necessarily Patient Zero— immediate isolation of the infected device won’t guarantee that the ransomware doesn’t exist elsewhere on your network.
To effectively limit its scope, you’ll need to disconnect from the network all devices that are behaving suspiciously, including those operating off-premises—if they’re connected to the network, they present a risk no matter where they are. Shutting down wireless connectivity (Wi-Fi, Bluetooth, etc.) at this point is also a good idea.Assess the Damages. To determine which devices have been infected, check for recently encrypted files with strange file extension names, and look for reports of odd file names or users having trouble opening files. If you discover any devices that haven’t been completely encrypted, they should be isolated and turned off to help contain the attack and prevent further damage and data loss.
Your goal is to create a comprehensive list of all affected systems, including network storage devices, cloud storage, external hard drive storage (including USB thumb drives), laptops, smartphones, and any other possible vectors.
At this point, it’s prudent to lock shares. All of them should be restricted if possible; if not, restrict as many as you can. Doing so will halt any ongoing encryption processes and will also keep additional shares from being infected while remediation occurs.
But before you do that, you’ll want to take a look at the encrypted shares. Doing so can provide a useful piece of information: If one device has a much higher number of open files than usual, you may have just found your Patient Zero. Otherwise…Locate Patient Zero. Tracking the infection becomes considerably easier once you’ve identified the source. To do so, check for any alerts that may have come from your antivirus/antimalware, EDR, or any active monitoring platform.
And because most ransomware enters networks through malicious email links and attachments, which require an end user action, asking people about their activities (such as opening suspicious emails) and what they’ve noticed can be useful as well.
Finally, taking a look at the properties of the files themselves can also provide a clue—the person listed as the owner is likely the entry point. (Keep in mind, however, that there can be more than one Patient Zero!)Report the Ransomware to Authorities. As soon as the ransomware is contained, you’ll want to contact law enforcement, for several reasons. First of all, ransomware is against the law—and like any other crime, it should be reported to the proper authorities.
Secondly, according to the United States Federal Bureau of Investigation, “Law enforcement may be able to use legal authorities and tools that are unavailable to most organizations.” Partnerships with international law enforcement can be leveraged to help find the stolen or encrypted data and bring the perpetrators to justice.
Finally, the attack may have compliance implications: Organizations must be aware of compliance obligations under regulations like GDPR, which may require reporting data breaches to regulatory authorities—such as the ICO—within strict timeframes to avoid significant penalties.Evaluate Your Backups. Now it’s time to begin the response process. The quickest and easiest way to do so is to restore your systems from a backup. Ideally, you’ll have an uninfected and complete backup created recently enough to be beneficial. If so, the next step is to employ an antivirus/antimalware solution to ensure all infected systems and devices are wiped free of ransomware—otherwise it will continue to lock your system and encrypt your files, potentially corrupting your backup.
Once all traces of malware have been eliminated, you’ll be able to restore your systems from this backup and—once you’ve confirmed that all data is restored and all apps and processes are back up and running normally—return to business as usual.
Unfortunately, many organizations do not realize the importance of creating and maintaining backups until they need them and they aren’t there. Because modern ransomware is increasingly sophisticated and resilient, some of those who do create backups soon find out that the ransomware has corrupted or encrypted them, too, rendering them completely useless.Research Your Decryption Options. If you find yourself without a viable backup, there’s still a chance you can get your data back. A growing number of free decryption keys can be found at No More Ransom. If one is available for the variant of ransomware you’re dealing with (and assuming you’ve wiped all traces of malware from your system by now), you’ll be able to use the decryption key to unlock your data.
Even if you’re fortunate enough to find a decryptor, however, you’re not done yet—you can still expect hours or days of downtime as you work on remediation.
- Move On. Unfortunately, if you have no viable backups and cannot locate a decryption key, your only option may be to cut your losses and start from scratch. Rebuilding won’t be a quick or inexpensive process, but once you’ve exhausted your other options, it’s the best you can do.
Types of ransomware
- Encrypting Ransomware (Cryptoware). This type encrypts files on the system's hard drive, making them difficult to decrypt without the key. Hybrid encryption, combining symmetric and asymmetric methods, is often used to increase effectiveness and resolve vulnerabilities found in older, single-method encryption.
- Non-encrypting Ransomware. This includes methods that restrict system access without encrypting files, such as screen lockers that display a full-screen message demanding payment. Some may display fake warnings from law enforcement, falsely claiming the system was used for illegal activities.
- Leakware/Doxware. This type of attack threatens to publish stolen sensitive information from the victim's computer system unless a ransom is paid, rather than denying access. This is a form of "double extortion."
- Mobile Ransomware. These payloads typically block access to the device rather than encrypting data, as mobile data is often easily restored via online synchronization. They commonly target Android devices via APK files and may attempt to gain device administrator privileges.
- Scareware. This malware uses social engineering with pop-ups to convince victims they have a virus or other issue, directing them to download fake software or pay a fee.
Why is ransomware spreading?
Ransomware attacks and their variants are rapidly evolving to counter preventive technologies for several reasons:
- Cybercriminals are leveraging readily available malware kits to generate new malicious code, driven by significant financial incentives.
- The use of known good generic interpreters to create cross-platform ransomware. For example, Ransom32 uses Node.js with a JavaScript payload.
- The use of new techniques, such as encrypting the complete disk instead of selected files.
Today’s thieves don’t even have to be tech savvy. Ransomware marketplaces have sprouted up online, offering malware strains for any would-be cybercrook and generating extra profit for the malware authors, who often ask for a cut in the ransom proceeds.
How do ransomware perpetrators evade detection?
Pinpointing the individuals behind ransomware attacks is a significant challenge due to a confluence of factors that shield cybercriminals from detection and prosecution.
- Global Reach and Jurisdictional Issues. Ransomware attackers can be located anywhere in the world. They often operate in regions that lack strong cybercrime laws or do not cooperate closely with international law enforcement. This creates “safe havens” where criminals can act with reduced risk of extradition or legal repercussions.
- Anonymity and Dark Web Tools. Cybercriminals rely on technologies designed to conceal their identities, such as the Tor network and other encrypted communication channels. These tools mask the origin of internet traffic, making it difficult to link an online persona to a specific individual or location.
- Cryptocurrency and Money Laundering. Ransom demands are almost always in cryptocurrency (e.g., Bitcoin, etc.). While not untraceable, these currencies are often laundered through mixers and crypto exchanges with lax regulations. This makes the money trail more difficult—but not impossible—to follow.
- Use of Obfuscation and “Bulletproof” Hosting. Criminals frequently use hosting providers that ignore or fail to enforce takedown requests. These so-called “bulletproof” services allow attackers to hide malicious command-and-control servers or data drop points beyond the reach of law enforcement.
- Technical Sophistication. Ransomware groups often have the resources to employ advanced techniques. They may use multilayered attacks, exploit zero-day vulnerabilities, or conduct extensive recon on targeted networks before deploying malware. This level of technical skill helps them avoid detection and cover their tracks.
- Frequent shifting of infrastructure. Attackers regularly move their infrastructure (servers, domains, and IP addresses), making them a fast-moving target. By the time law enforcement identifies a server or domain, criminals may have already moved operations elsewhere.
- Organized crime networks. Ransomware is sometimes part of a larger organized crime operation. In these scenarios, attackers are well-funded, maintain a supply chain of specialists (developers, negotiators, money launderers), and can replace compromised assets quickly if part of their operation is shut down.
- Delayed reporting and under-reporting. Victims may delay or avoid reporting ransomware attacks out of fear of reputational damage or concern over legal implications (e.g., data privacy regulations). This limited visibility reduces the amount of evidence available to investigators.
What is ransomware-as-a-service (RaaS)?
Ransomware as a service (RaaS) is a cybercrime economic model that allows malware developers to earn money for their creations without the need to distribute their threats. Other criminals buy their wares and launch the infections, while paying the developers a percentage of their take.
The developers run relatively few risks, and their customers do most of the work. Some instances of ransomware as a service use subscriptions, while others require registration to gain access to the ransomware.
Top ransomware concerns
Ransomware attacks pose a multitude of risks and complex challenges businesses face when targeted and extorted:
- Data Encryption and Loss. Ransomware encrypts critical data, making it inaccessible without the decryption key, which attackers often provide only after receiving payment. Even if you pay the ransom, there's no guarantee that you'll fully recover your data, and some might be permanently lost.
- Double Extortion. Many ransomware attacks now involve stealing sensitive data before encrypting it. Attackers then threaten to release the stolen data if the ransom isn't paid, increasing pressure on victims.
- Business Disruption. Ransomware attacks can cripple operations by preventing access to critical systems and data, leading to lost productivity and potential customer dissatisfaction.
- Reputational Damage. Public disclosure of a ransomware attack can significantly harm a company's image, especially if sensitive customer data is leaked.
- Legal and Regulatory Implications. Depending on the type of data compromised in a ransomware attack, companies may face legal consequences and regulatory penalties for data breaches.
How to defend against ransomware
To avoid ransomware and mitigate damage if you are attacked, follow these tips:
- Educate and Train Employees. Employees are the first line of defense against ransomware. Stress the importance of strong cyber hygiene and vigilance in spotting potential threats. Implement rigorous training programs to educate employees to recognize phishing attempts and suspicious emails, and promote safe online behavior while discouraging risky actions.
- Implement a Zero-Trust Strategy. Adopting a zero-trust approach to security means trusting no one by default. Verification and continuous authentication are essential components of this strategy. Microsegmentation can help isolate critical assets from potential threats.
- Enhance Email Security. Email is the primary vector for initial access in ransomware attacks. To enhance email security, deploy email filtering and anti-phishing measures. Regularly train employees on email security best practices to ensure they can identify and respond to threats effectively.
- Maintain Offline Backups. Ensure data recovery in case of a ransomware attack by regularly backing up critical data. Keep these backups offline and isolated to prevent them from being compromised. Regularly test data restoration procedures to ensure they work as intended.
- Create an Incident Response Plan. Being prepared to respond swiftly and effectively to a ransomware incident is crucial. Develop a clear incident response plan that outlines roles and responsibilities. Regularly update and test the plan to ensure it functions as intended in a crisis.
- Fortify Your Endpoints with Endpoint Detection and Response (EDR). Protect your devices and networks with advanced endpoint security. Implement real-time monitoring and response capabilities, utilize behavior-based threat detection, and be prepared to isolate infected devices to prevent lateral movement within your network.
- Keep Systems Up to Date and Patch Known Vulnerabilities. Regularly update your software and systems to stay ahead of attackers. Apply patches promptly to fix known security vulnerabilities, and conduct vulnerability scanning and assessment regularly to identify and address potential weaknesses.
Why you shouldn’t pay the ransom
When faced with the possibility of weeks or months of recovery, it might be tempting to give in to a ransom demand. But there are a number of reasons why this is a bad idea:
- It may violate U.S. sanctions or other regulations. While paying a ransom is not against U.S. federal law, several states such as Florida, North Carolina, and Tennessee have laws restricting or prohibiting payments of ransom by public sector organizations.
- You may never get a decryption key. When you pay a ransomware demand, you’re supposed to get a decryption key in return. But when you conduct a ransomware transaction, you’re depending on the integrity of criminals. Many people and organizations have paid the ransom only to receive nothing in return—they’re then out many thousands or millions of dollars, and they still have to rebuild their systems from scratch.
- You could get repeat ransom demands. Once you pay a ransom, the cybercriminals who deployed the ransomware know you’re at their mercy. They may give you a working key if you’re willing to pay a little (or a lot) more.
- You may receive a decryption key that works—kind of. The creators of ransomware aren’t in the file recovery business; they’re in the moneymaking business. In other words, the decryptor you receive may be just good enough for the criminals to say they held up their end of the deal. Moreover, it’s not unheard of for the encryption process itself to corrupt some files beyond repair. If this happens, even a good decryption key will be unable to unlock your files—they’re gone forever.
- You may be painting a target on your back. Once you pay a ransom, criminals know you’re a good investment. An organization that has a proven history of paying the ransom is a more attractive target than a new target that may or may not pay.
What’s going to stop the same group of criminals from attacking again in a year or two, or logging onto a forum and announcing to other cybercriminals that you’re an easy mark? A recent Infosecurity Magazine article reports that 78% of organizations who pay a ransom demand are hit by a second ransomware attack, often by the same threat actor. - Even if everything somehow ends up fine, you’re still funding criminal activity. Say you pay the ransom, receive a good decryptor key, and get everything back up and running. This is merely the best worst-case scenario (and not just because you’re out a lot of money).
When you pay the ransom, you’re funding criminal activities. Putting aside the obvious moral implications, you’re reinforcing the idea that ransomware is a business model that works. (Think about it—if no one ever paid the ransom, do you think they’d keep putting out ransomware?)
Bolstered by their success and their outsized payday, these criminals will continue wreaking havoc on unsuspecting businesses, and will continue putting time and money into developing newer and even more nefarious strains of ransomware—one of which may find its way onto your devices in the future.
The CyberThreat Report
Insights gleaned from a global network of
experts, sensors, telemetry, and intelligence
Trellix: Critical coverage across the entire ransomware kill chain
Trellix provides critical coverage for all stages of a sophisticated ransomware campaign—from reconnaissance to recovery—offering unmatched visibility and reduced time to detection and response.
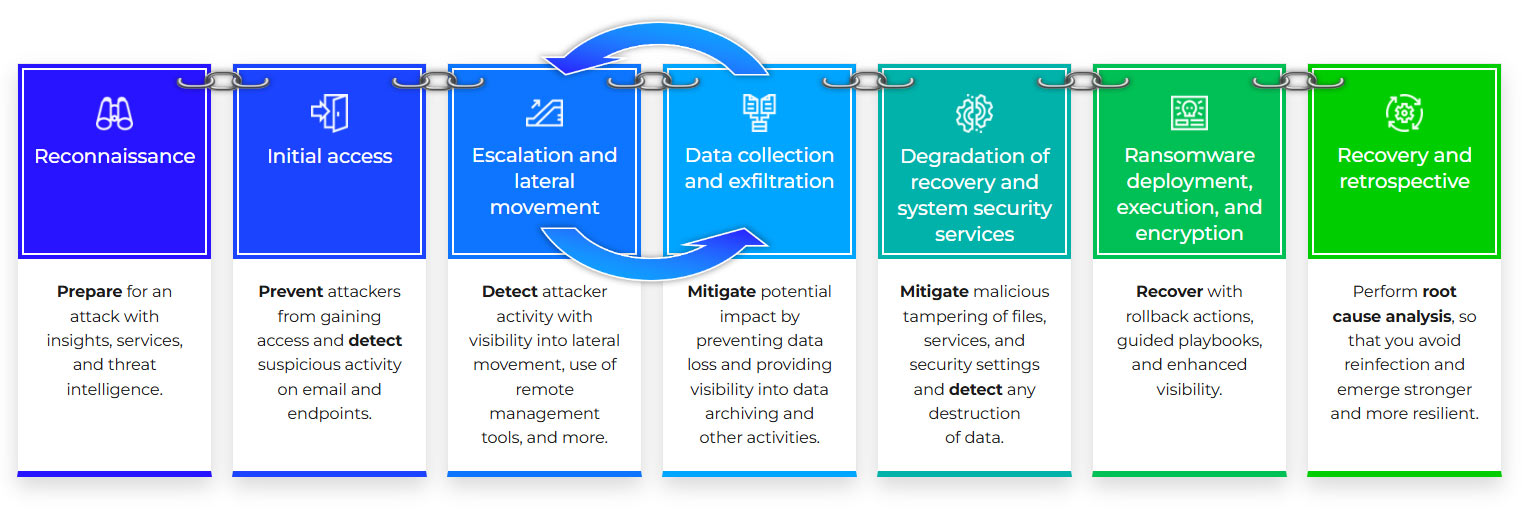
Minimize Time to Detect and Respond
With Trellix, you can minimize the mean time to detect (MTTD) and respond (MTTR) to ransomware threats. The Trellix Security Platform offers AI-powered speed, reducing cost and increasing SOC analysts’ productivity with automatic prioritization, guided response, rollback actions, and ready-to-use playbooks. It includes solutions for endpoint security and network security.
Leverage Rich Threat Intelligence
The Trellix Advanced Research Center analyzed more than 9,000 real-world ransomware attacks to develop a kill chain model that helps combat ransomware and reduce time to value, cost, complexity, and overall risk. Leverage rich threat intelligence from the Trellix Advanced Research Center to decrease false positives and ensure your SOC spends time fighting attackers instead of chasing alerts.
Get quick time to value with a comprehensive, open platform
The AI-powered Trellix Security Platform provides comprehensive native controls, offering a one-platform, best-of-breed tool to replace five or more point products. The open platform integrates over 1,000 third-party data sources, providing quick time to value with more than 500 out-of-the-box integrations.
Ransomware FAQ
- Educate Employees: Train employees on strong cyber hygiene and safe online behavior, and teach them how to recognize phishing.
- Implement Zero-Trust: Adopt a zero-trust approach with continuous verification. Use microsegmentation to isolate critical assets.
- Enhance Email Security: Deploy email filtering and anti-phishing measures, and train employees on email security best practices.
- Maintain Offline Backups: Regularly back up critical data offline. Keep offline data isolated, and test restoration procedures.
- Create an Incident Response Plan: Develop, update, and test a clear plan for ransomware incidents.
- Fortify Endpoints with EDR: Protect devices with real-time monitoring and behavior-based detection, and be prepared to isolate infected devices.
- Keep Systems Updated: Regularly update software, apply patches promptly, and conduct vulnerability scanning.
Paying ransomware is generally not recommended for a number of reasons:
- No Guarantee of Decryption: Payment doesn't ensure data recovery; attackers may not provide a working key, or it might be faulty.
- Encourages Criminals: Paying validates the criminal business model, incentivizing more attacks and funding illicit activities like terror organizations or rogue nation-states.
- Escalating Costs: While the direct ransom cost is high, the overall cost of remediation (downtime, lost opportunity, device costs) is significantly higher. Some ransomware even increases the ransom if payment is not made promptly.
There are a number of steps you should take to respond to a ransomware attack:
- Isolate Infected Devices: Disconnect affected devices from the network, internet, and other devices immediately to prevent wider infection.
- Stop the Spread: Isolate all suspiciously behaving devices, even off-premises ones, and shut down wireless connectivity.
- Assess the Damages: Identify infected devices by checking for encrypted files and user issues. Isolate and turn off unencrypted but affected devices. Create a comprehensive list of all affected systems, including network and cloud storage, external drives, laptops, and smartphones. Lock shares to halt encryption and prevent further infection. Examine encrypted shares to potentially identify Patient Zero.
- Locate Patient Zero: Track the source by checking alerts from security platforms (antivirus/antimalware, EDR). Interview users about suspicious activities (e.g., opening malicious emails). File properties can also indicate the owner as the entry point.
- Report to Authorities: Once contained, contact law enforcement. Ransomware is a crime and should be reported. Law enforcement has tools unavailable to most organizations and can leverage international partnerships. Compliance regulations (like GDPR) may also require reporting data breaches.
- Evaluate Backups: Restore systems from an uninfected, recent backup if available. Use antivirus/antimalware to wipe infected systems before restoring. Confirm all data and apps are normal before resuming business..
- Research Decryption Options: If you have no viable backup, check No More Ransom for free decryption keys after malware removal. Expect downtime even with a decryptor.
- Move On: If backups fail and no decryption key is found, rebuilding from scratch may be the only option, though it's time-consuming and expensive.
Ransomware resources

Get a comprehensive framework for integrating threat intelligence, proactive hunting methodologies, and advanced detection engineering into modern security operations.

Proactively predict and prioritize security threats. Deliver threat detections and map them to endpoints, campaigns, and more to help prevent attacks.

We analyze cybersecurity threats, emerging vulnerabilities, and defense strategies to help you stay ahead of cyber risks.
Reviewed by Tom Stitt, who serves as Director of Network Security Product Marketing at Trellix, leading strategy for Network Detection and Response solutions. With over two decades of cybersecurity experience at companies including Cisco, ExtraHop, BitSight, and IBM, Tom specializes in product launches, market positioning, and alliance partnerships across enterprise security markets.