Blogs
The latest cybersecurity trends, best practices, security vulnerabilities, and more
Exposing PathWiper: A Deep Dive into DCOM Abuse and Network Erasure With Trellix NDR
By Maulik Maheta and Lishoy Mathew · August 12, 2025
Executive summary
Ukraine’s national energy and telecommunications infrastructure was the primary targets of the PathWiper attack in 2025. The attack was orchestrated via commercial endpoint administration framework, implying that the attackers had pre-existing access to the administrative console. Once initial access had been established, the attacker executed malicious commands to spread PathWiper across connected endpoints, which resulted in the deletion of vital data from key storage volumes.
This blog explores how attackers could use Distributed Component Object Model (DCOM) as a lateral movement technique to distribute PathWiper, and how Trellix Network Detection and Response (NDR) detects and visualizes such activities. The insights provided here are especially relevant for SOC analysts and cybersecurity professionals who aim to understand and defend against similar threats.
Understanding lateral movement
Lateral movement is a technique used by attackers to navigate within a compromised network. Instead of immediately compromising the first system, malicious actors methodically explore the network to identify high-value targets, escalate privileges, and establish persistence. This phase is crucial for adversaries aiming to maximize impact.
Detecting lateral movement in near real-time is essential for limiting the scope of a breach. Products like Trellix NDR play a pivotal role in identifying unusual internal activity and helping defenders visualize the attack path before serious damage occurs.
Understanding DCOM
DCOM is a programming construct that enables a computer to run programs on a remote computer over a network as if they were running locally. DCOM is a proprietary Microsoft software component that enables COM objects to communicate with one another over a network.
DCOM configuration information is stored in the Windows Registry under three identifiers:
- CLSID: The Class Identifier (CLSID) is a Global Unique Identifier (GUID). Windows stores a CLSID for each installed class in a program. When you need to run a class, you must enter the correct CLSID so that Windows can locate the program.
- ProgID: A programmatic identifier (ProgID) is a registry entry that can be associated with a CLSID. Like the CLSID, the ProgID identifies a class but with less precision because it is not guaranteed to be globally unique.
- APPID: An APPID is a GUID (Globally Unique Identifier) that acts as a central point for defining permissions and other DCOM settings for a group of related COM objects.
When an application attempts to activate a COM object remotely via DCOM, it typically uses the ProgID or CLSID to identify the specific object it wants to call. The associated APPID then provides the security settings, such as permissions and authentication levels, for that remote activation and subsequent communication.
Inside PathWiper: Capabilities of a modern wiper malware
PathWiper is a destructive wiper malware designed to cause irreparable damage to an organization's systems by overwriting all data and targeting the master boot record (MBR) and NTFS-related artifacts. Unlike ransomware, which encrypts data for a ransom, wiper malware aims to completely take systems offline by destroying data and making recovery impossible.
PathWiper begins by identifying all possible storage devices that are connected to the endpoint. This involves:
- Physical hard drive names
- Mounted volume names
- Network shared and unshared drive paths
The malware gathers information through standard system APIs and queries specific Windows registry keys, such as 'HKEY_USERS\Network\<drive_letter>| RemovePath', to identify historical or hidden network shares that may not be currently mounted.
PathWiper starts a separate thread for each drive and volume after it has compiled a list of targets. Each thread starts overwriting data with randomly generated bytes, making forensic recovery extremely difficult.
It primarily targets core NTFS file system structures, including:
- Master Boot Record (MBR)
- $MFT (Master File Table)
- $LogFile (Hidden system file within the NTFS)
Before overwriting the artifacts, the wiper attempts to dismount volumes by assigning the 'FSCTL_DISMOUNT_VOLUME IOCTL' to the MountPointManager device object. PathWiper also deletes files on disk by replacing them with randomized bytes.
Attack flow: Drop PathWiper using DCOM lateral movement (Excel Application)
The DCOM communication attack flow between client and server, as well as the PathWiper drop on the compromised machine, are shown in Figure 1.
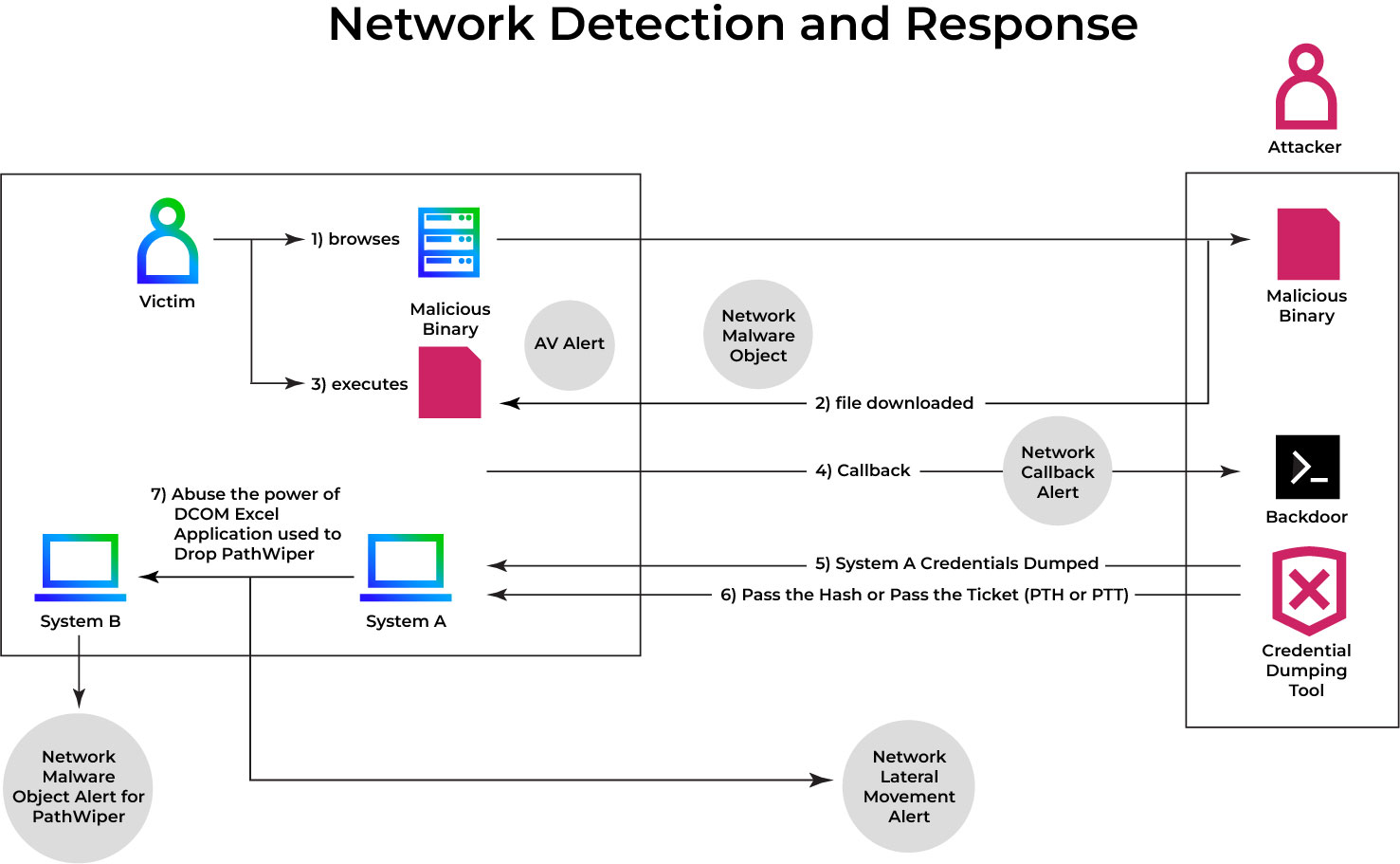
An attacker would need to be able to write to the system PATH and have Microsoft Excel installed on the target system in order to launch a DCOM attack. The steps to a successful attack are as follows:
- The adversary uploads an arbitrary malicious file to the target system with a specifically selected file name (such as "WINPROJ.EXE") inside a specifically chosen PATH.
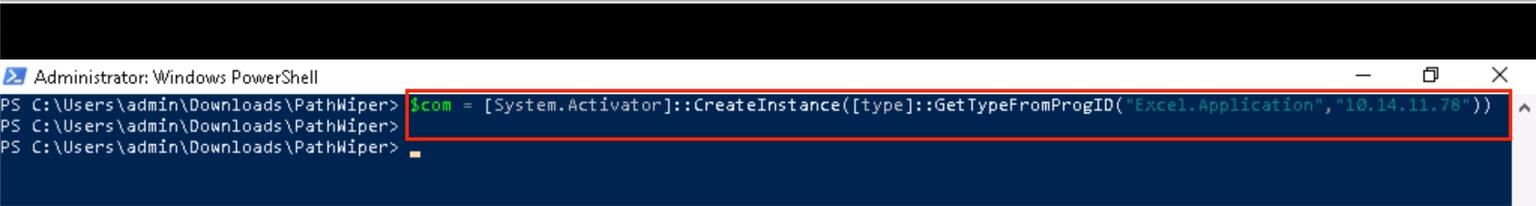
- The adversary creates an Excel instance on a remote system using DCOM.
- Adversary executes ActivateMicrosoftApp method, to achieve execution of fake WINPROJ.EXE.
- On successful attack, Excel.exe would spawn a fake WINPROJ.EXE at the target system
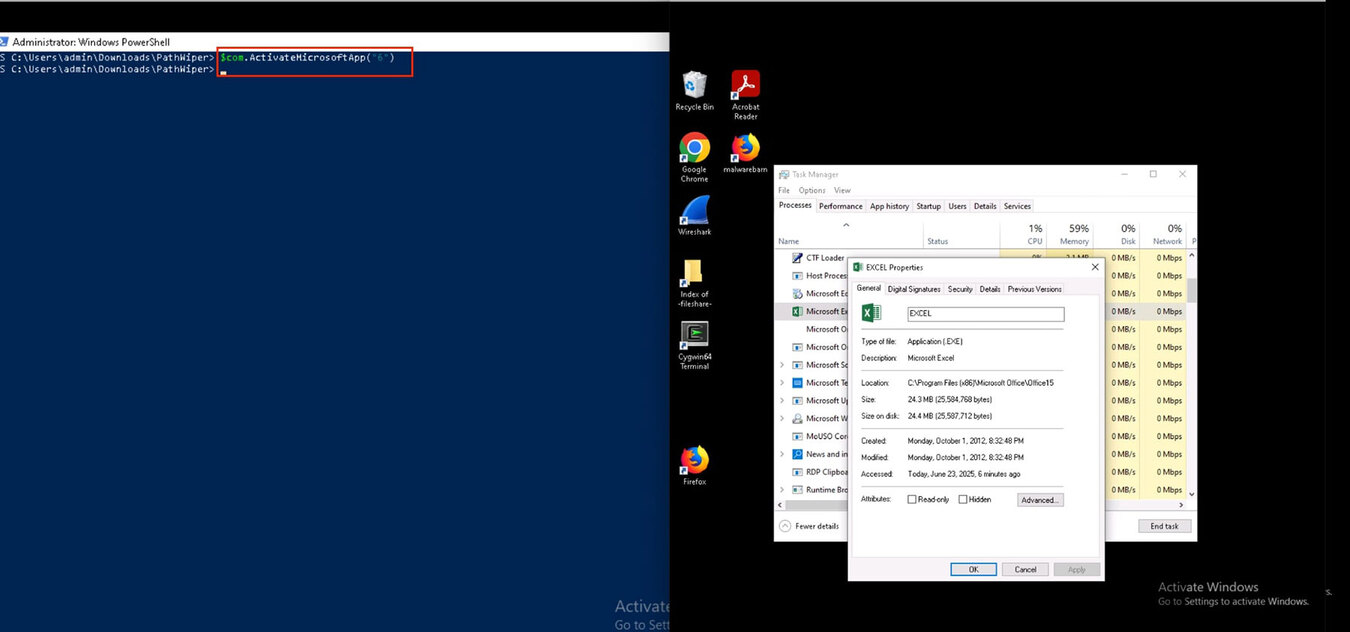
Microsoft still permits the activation of some end-of-life products, such as FoxPro, Schedule Plus, and Office Project. Shell access can be obtained using the ActivateMicrosoftApp() method. While it is unlikely that any of these out-of-date programs will find their way into modern systems, an attacker could take advantage of this vulnerability to implement persistence and lateral movement strategies.
As shown in Figure 2, the ActivateMicrosoftApp() method activates the currently running application or, if the application is not running, launches a new instance of the application as the starting user or the currently logged in user, depending on how DCOM was configured.
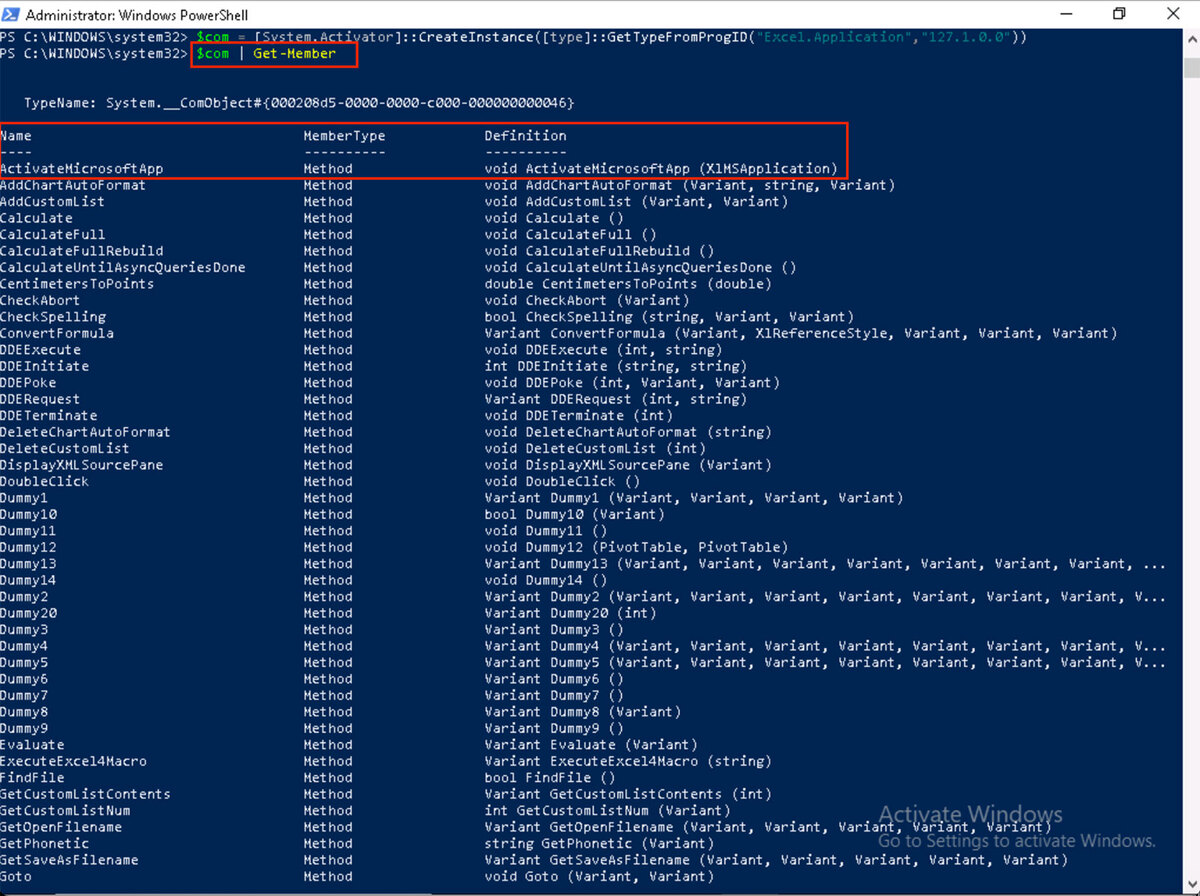
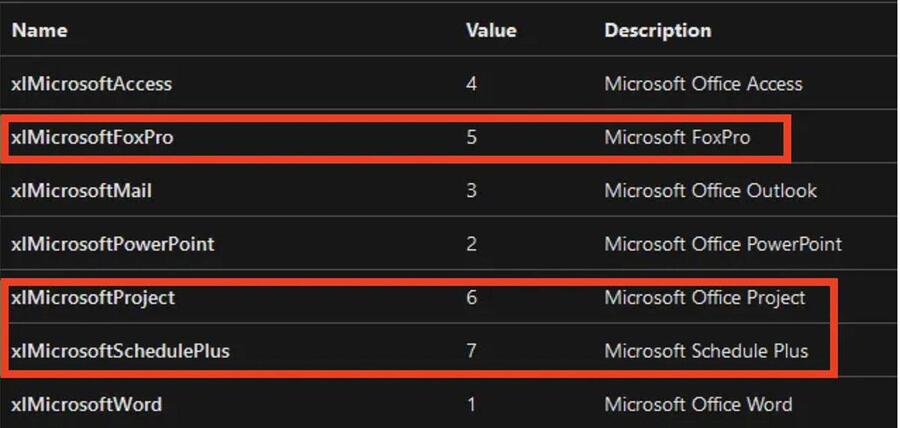
This method looks for the associated binary in the SYSTEM path. Since the program isn't installed, the Excel.exe process returned an error instead of finding the WINPROJ.exe binary file in the system PATH. To take advantage of this, we must first locate write permissions within the system path. The most common location on the PATH where users have write permission is:
C:\users\*\AppData\Local\Microsoft\WindowsApps\
Since January 2010, the Microsoft Project application has been discontinued, and it is less likely that it can be found in modern environments.
Thus, we can upload a binary named "WINPROJ.exe", which, in our case (Figure 4) is the malicious PathWiper sample.
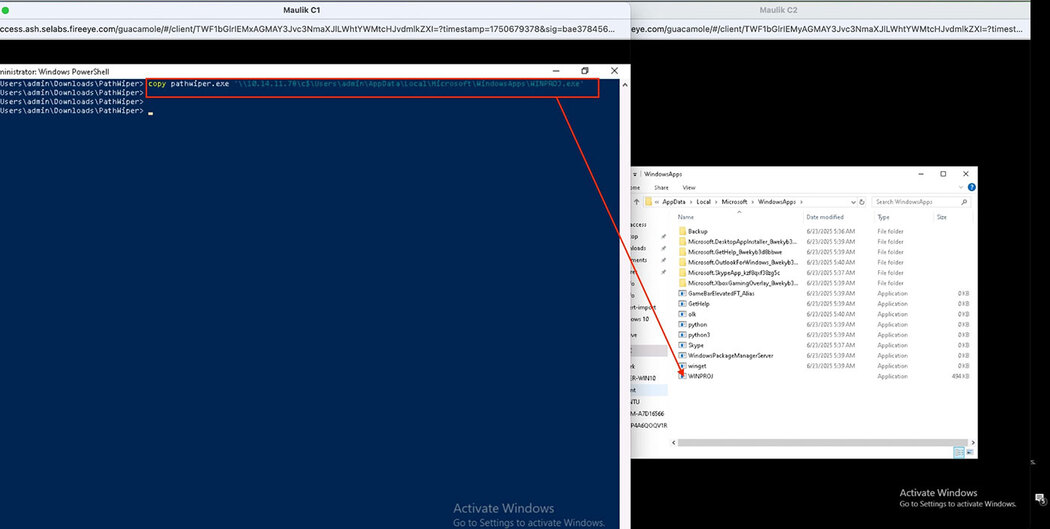
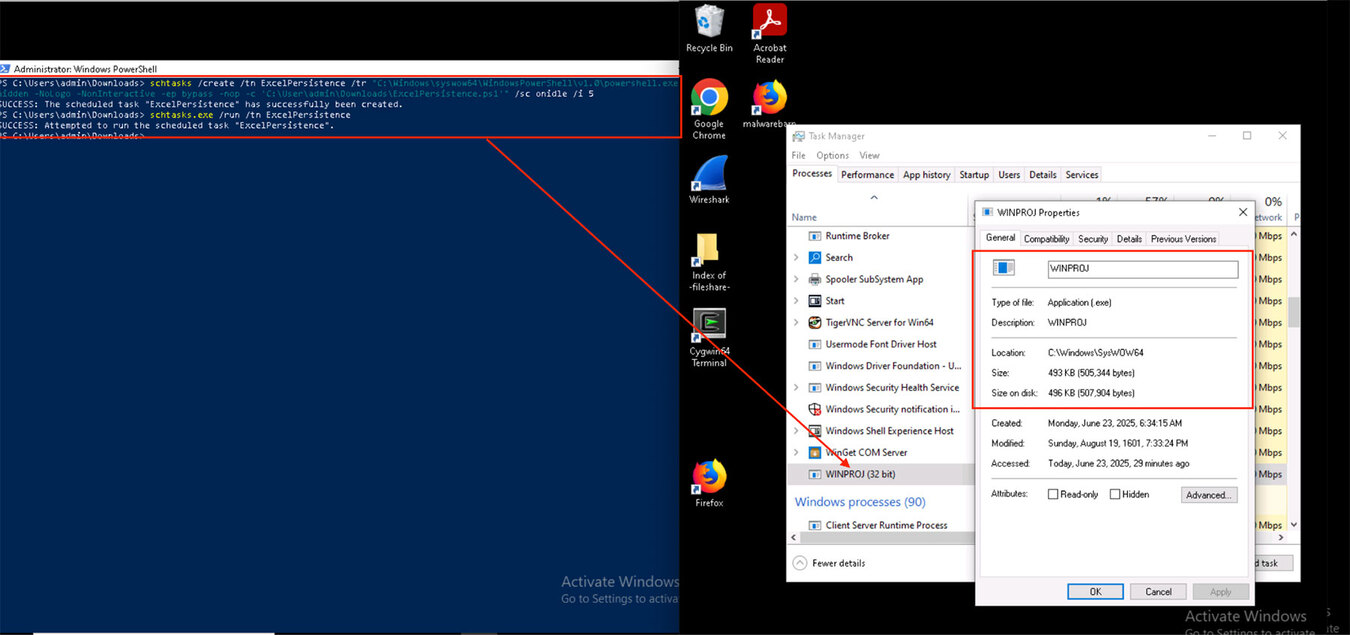
This technique could be used for persistence once access is established. Attackers can use PowerShell to automate and persist their control. For example, they could create a scheduled task that leverages DCOM to run the Excel instance regularly, invoking ActivateMicrosoftApp() to launch their payload (Figure 7). This mechanism can sustain access even after a reboot or session end.
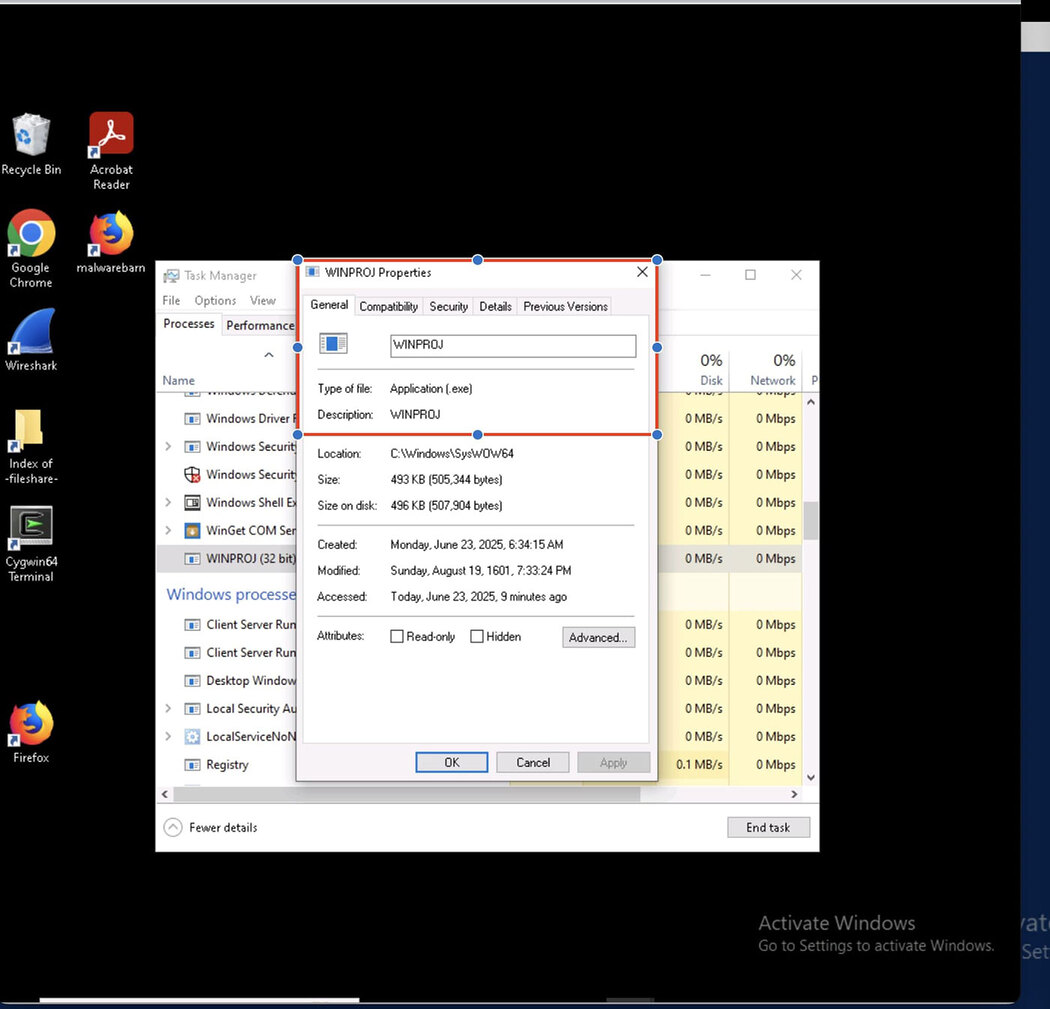
Pathwiper.exe renamed to WINPROJ.exe, was successfully executed on the compromised machine in both persistent and non-persistent execution. Check Figure 8 for more details.
Detection: Trellix Network Detection and Response (NDR)
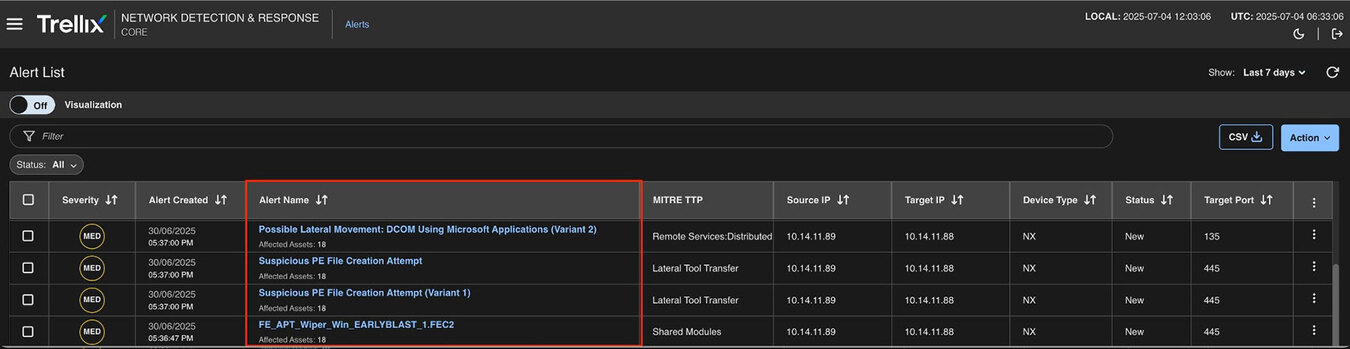
Trellix NDR detected the attack in three major stages, each with its own set of alerts. Figure 9, contains all the alerts related to this attack that assist analysts in understanding how the attack progressed from its initial deployment to lateral movement.
- Malware Object Alerts on NDR (PathWiper.exe aka WINPROJ.exe Sample Dynamic Analysis)
- Suspicious PE File Creation Attempt (Copy PathWiper.exe and rename it WINPROJ.exe on the target machine).
- Lateral Movement: DCOM Execution through Excel (the PathWiper.exe aka WINPROJ.exe payload is launched by calling ActivateMicrosoftApp())
-
Malware Object Alerts on NDR (PathWiper.exe aka WINPROJ.exe Sample Analysis)
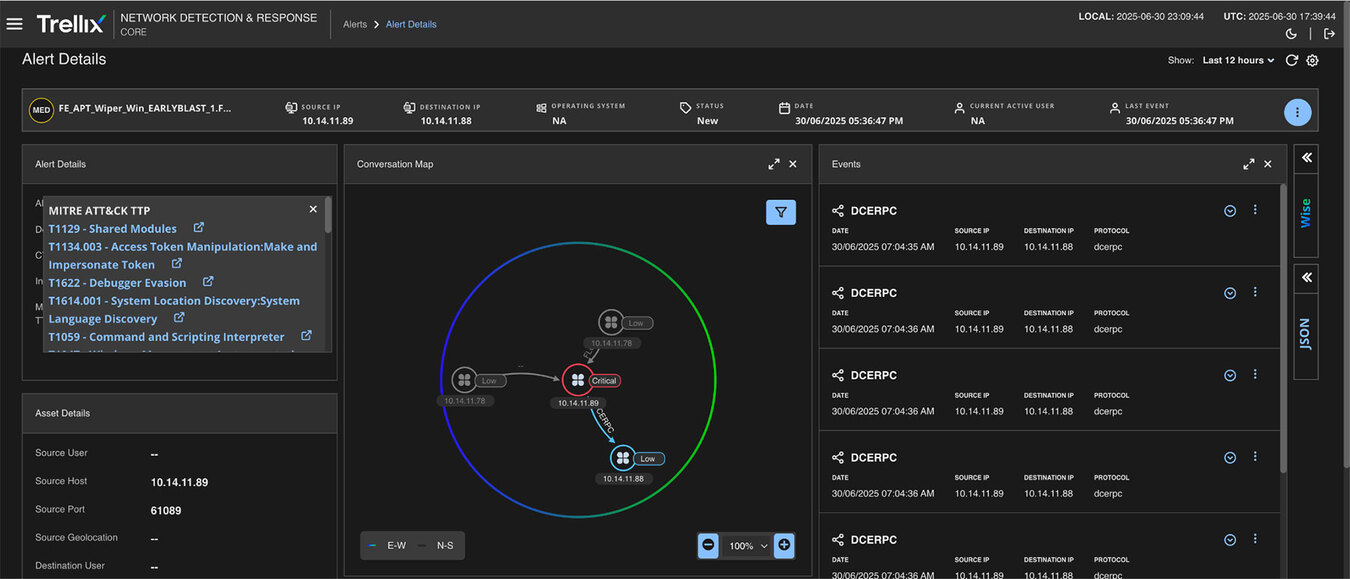
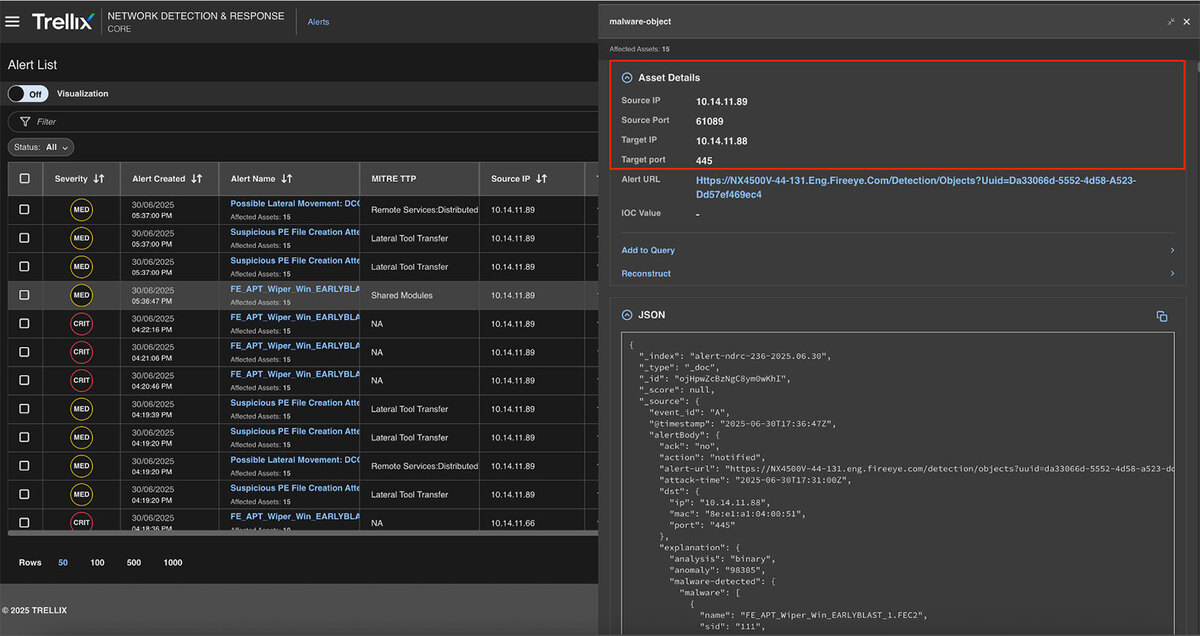
The first alert targeted the malware object itself: WINPROJ.exe, the renamed PathWiper executable. It contained key threat indicators such as MITRE ATT&CK mappings, information about events, network paths, and associated IP addresses. These details provided a clear picture of how the malware interacted with the system and across the network. Please refer to Figure 10 for more information.
Trellix NDR with Trellix Wise
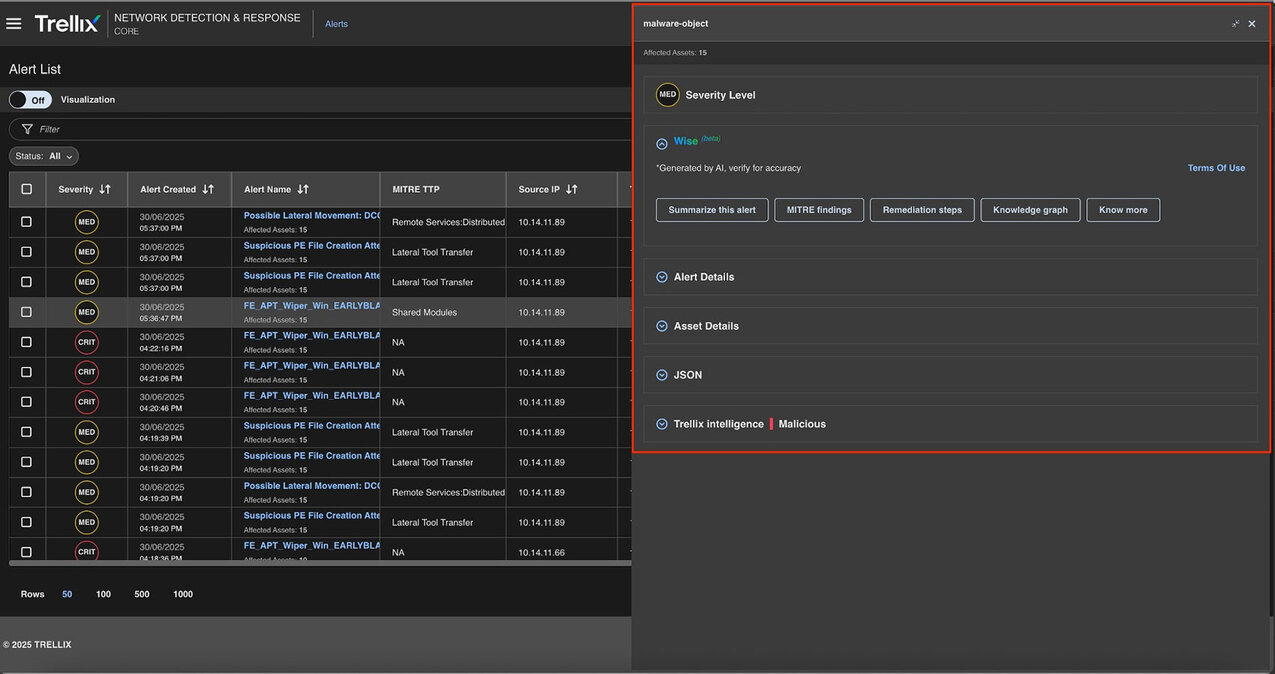
Trellix NDR utilizes Trellix Wise, the AI-powered foundation of our broader Trellix Security Platform, to enhance threat detection and response capabilities. Trellix Wise automates many aspects of alert investigation, reducing false positives and accelerating the time to resolution for security teams. This integration allows organizations to gain greater threat detection accuracy, automate complex tasks, and focus on strategic defenses.
Trellix Wise can provide a user with comprehensive details, such as additional information on the alert, remediation steps, MITRE information, etc. (Figure 11)
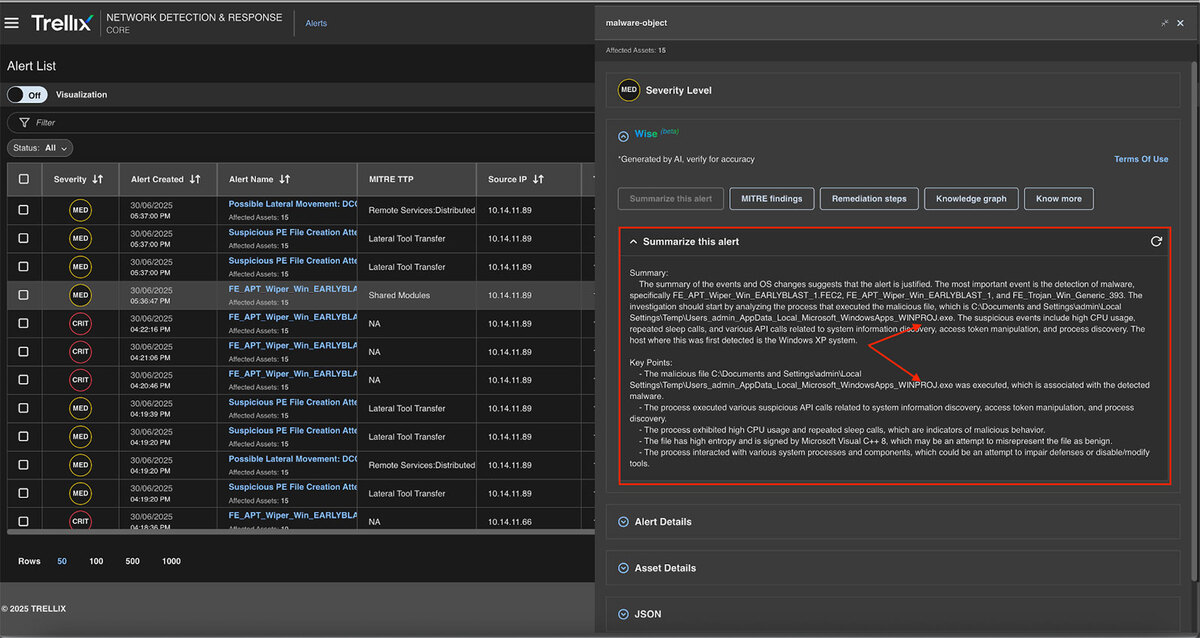
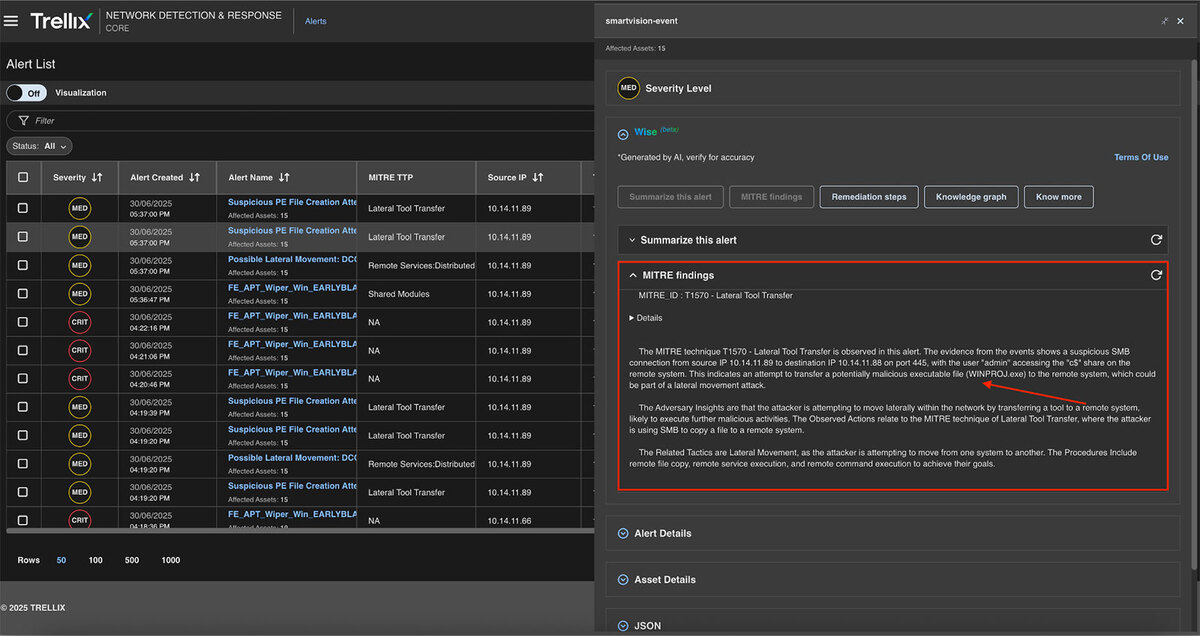
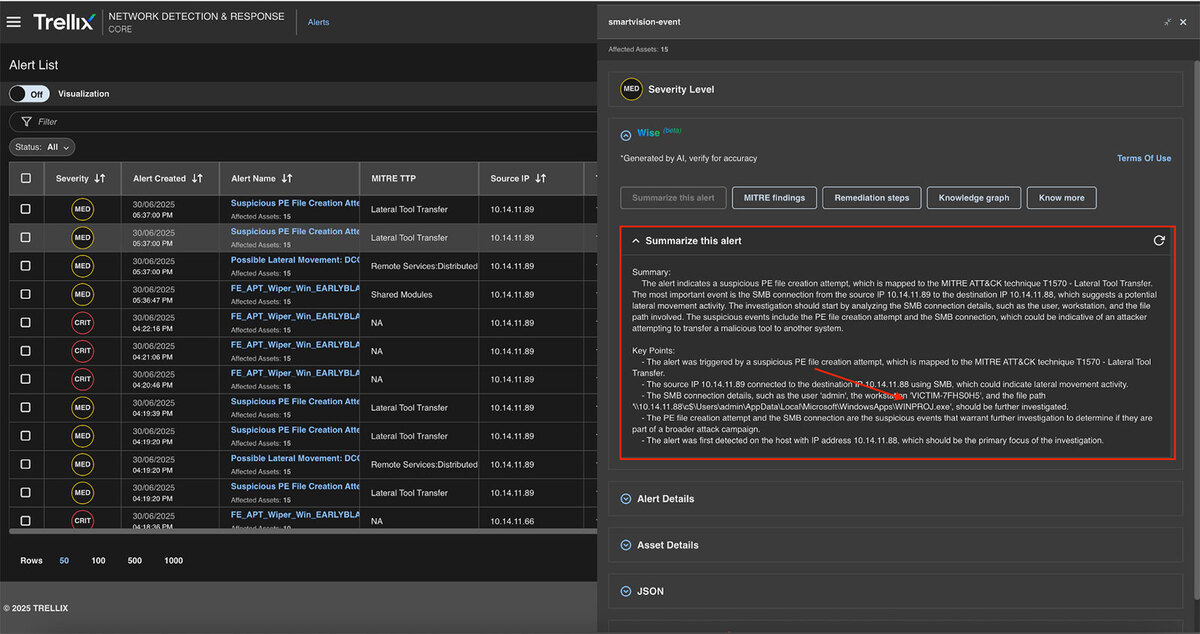
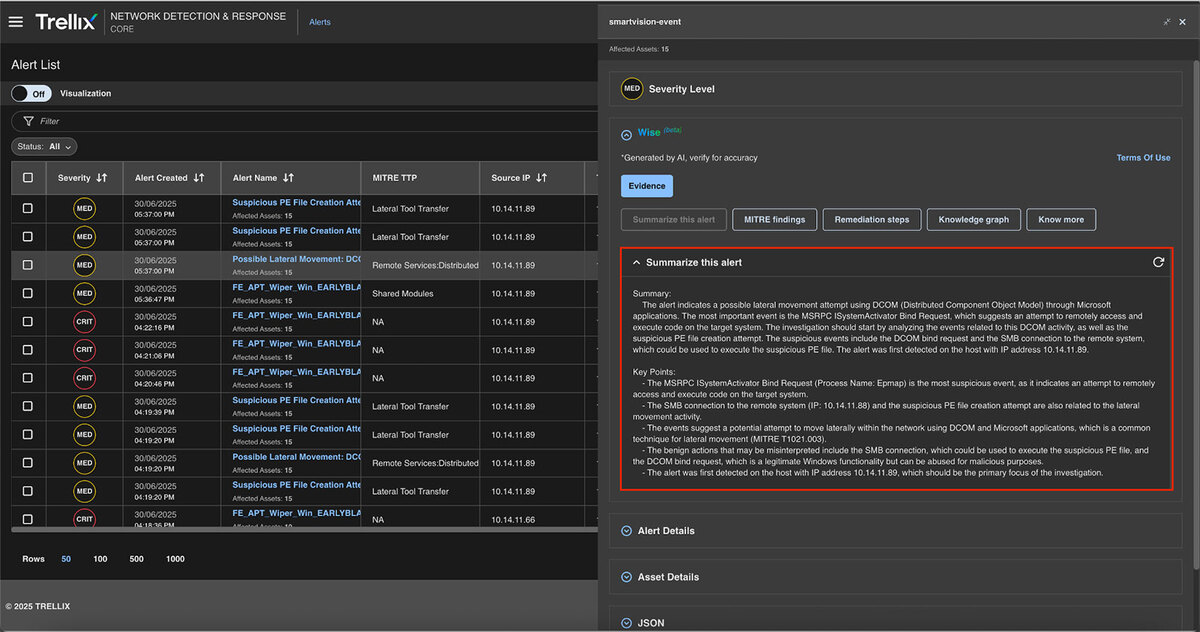
Summarize this alert
This feature summarizes the entire alert into Key Points making it easier for analysts to understand the “What” and “How” aspects of the alert. Refer to Figure 12 for a detailed update.
Asset details
Provides more information about the assets or endpoints involved in the alert.
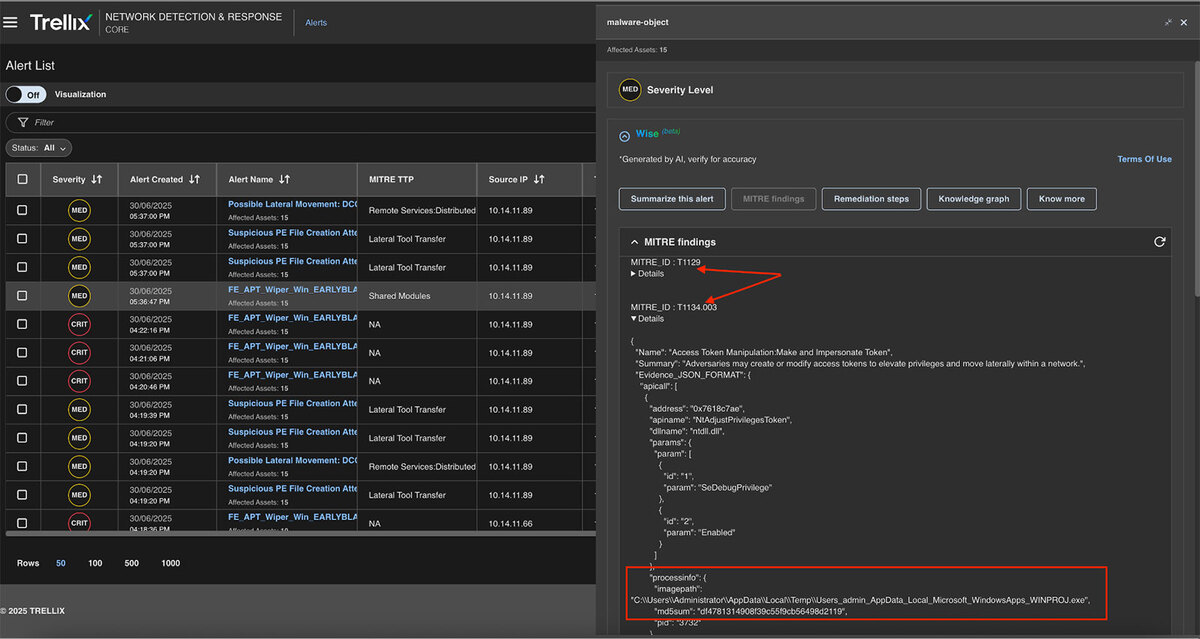
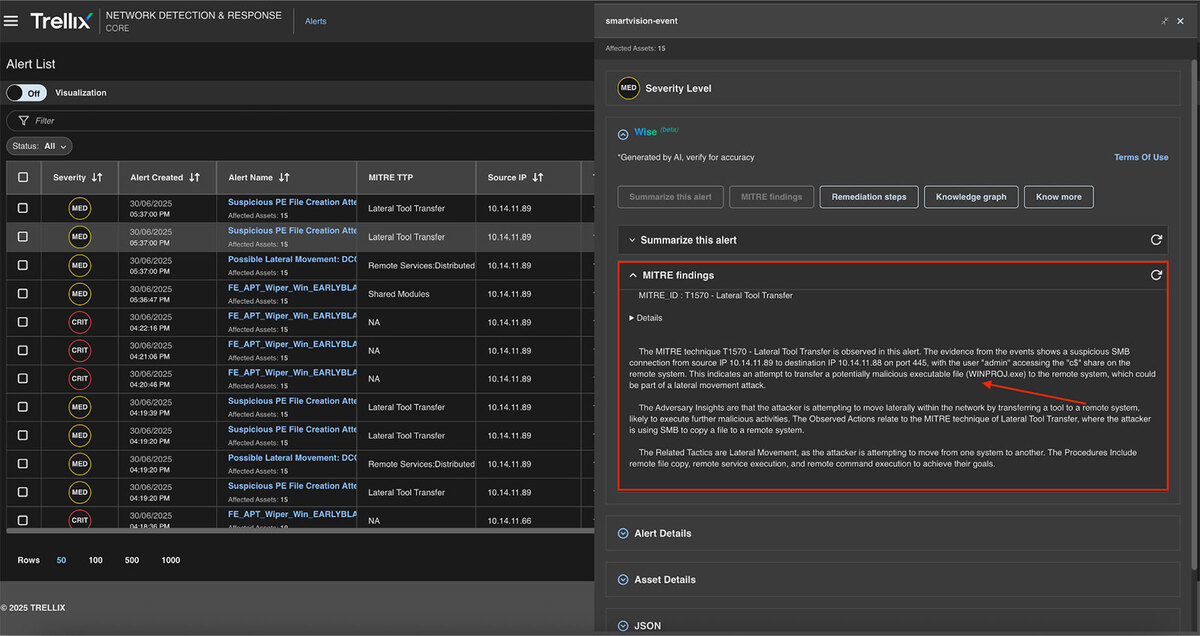
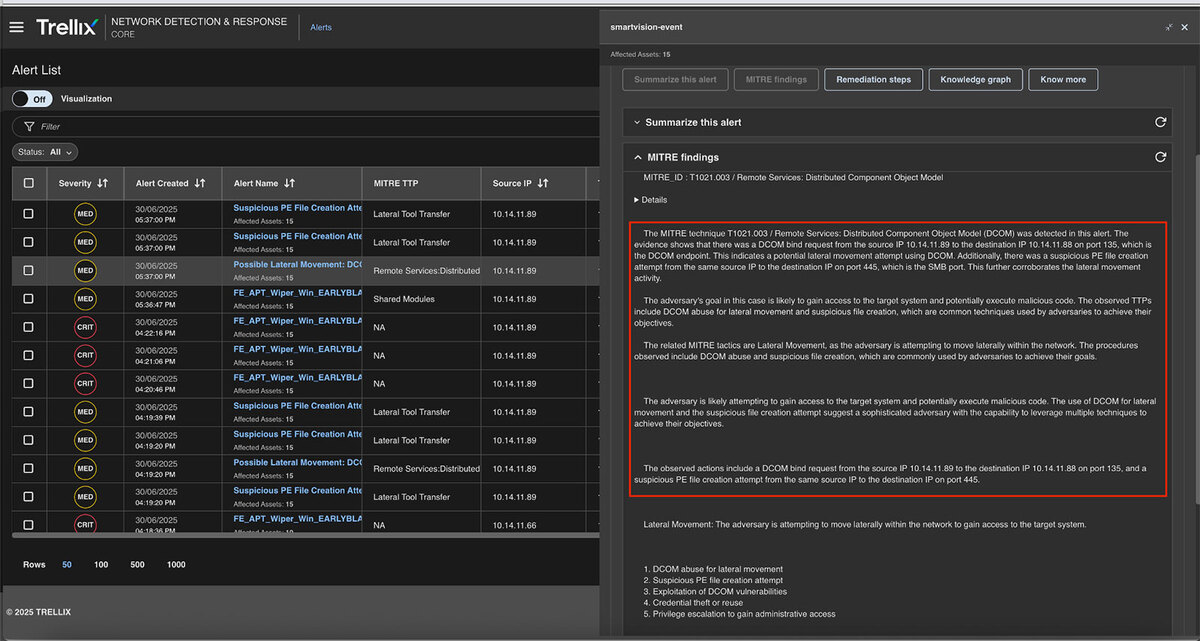
MITRE findings
The MITRE findings provide comprehensive details about the MITRE ID, Category, and associated tactics in addition to detailed information about the generated alerts. See Figure 14 for detailed findings.
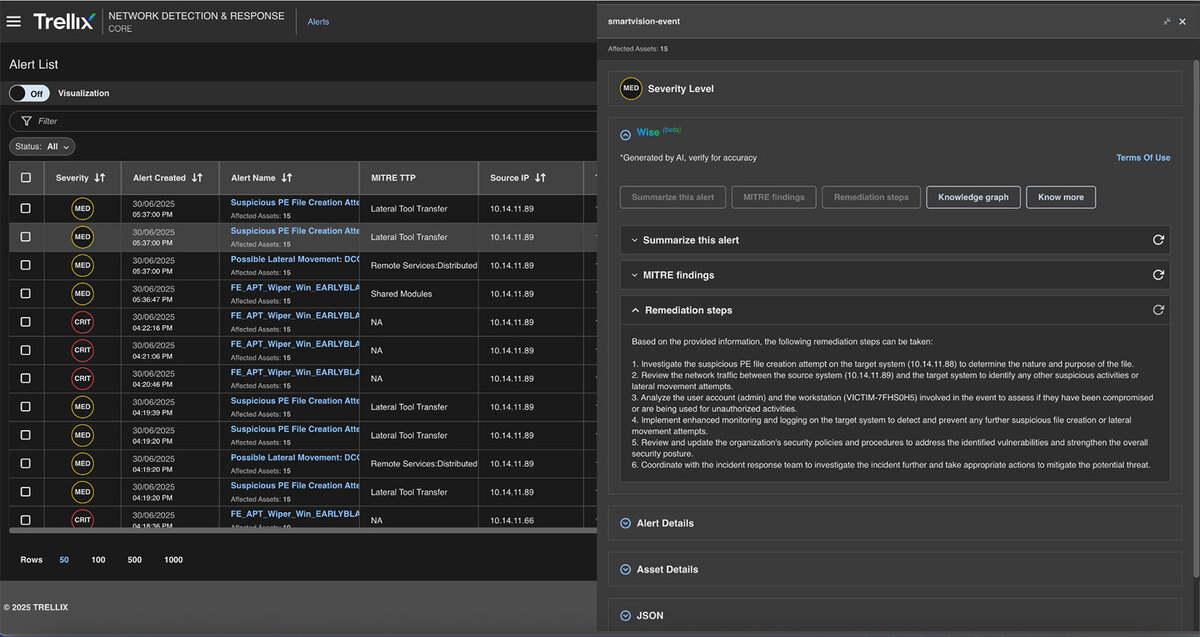
Remediation steps
Advanced analysis modules generate actionable recommendations for remediation and mitigation, correlate threats and vulnerabilities to identify potential attack paths, assess risk levels, and provide prioritized recommendations and remediation. Refer to Figure 15 for a detailed view.
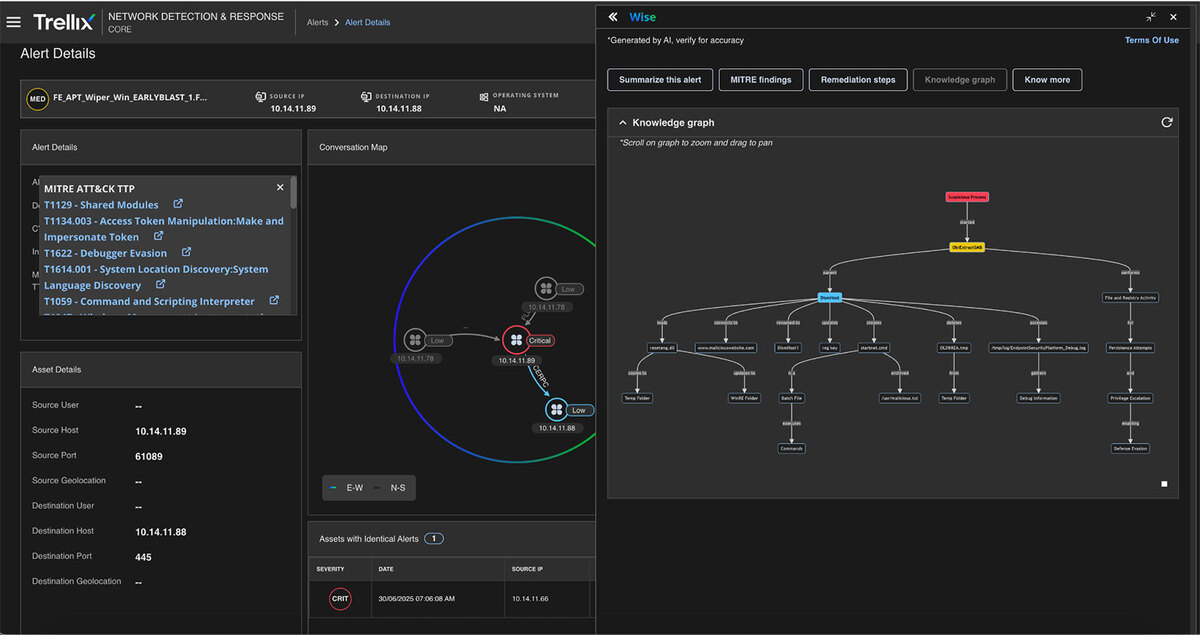
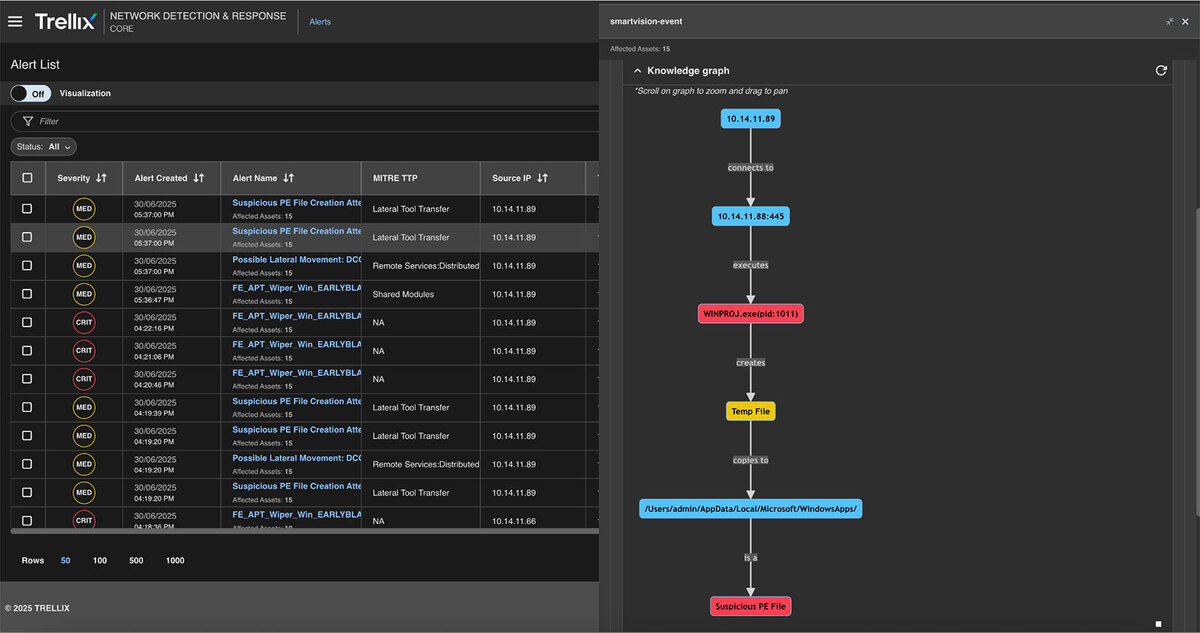
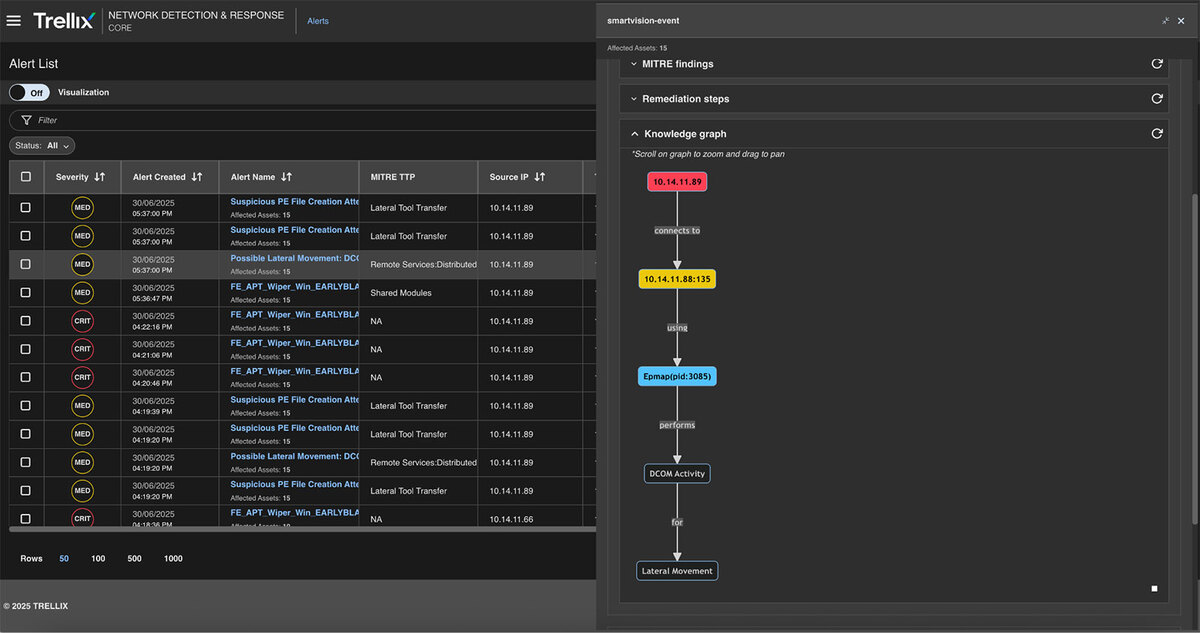
Knowledge graph
The Knowledge graph can transform data from multiple sources into a graph-based model of entities, their attributes, and how they relate. Here, the entire process is connected, including the attacker's IP address, the nature of their activity, and the type of alerting that the Trellix Network Security product generates. Refer to Figure 16 for a detailed update.
-
Suspicious PE File Creation Attempt (Copy PathWiper.exe and rename it WINPROJ.exe on the target machine)
The second alert was generated when the attacker copied PathWiper.exe to the target system and renamed it WINPROJ.exe. This renaming enabled the attacker to use Excel's DCOM behavior to launch the malware under a seemingly legitimate filename.
Trellix Wise provided a summary alert, associated MITRE techniques, mitigation steps, and a graphical overview of how this action fits into the overall attack sequence. This sequence is clearly described in Figures (17-20).
Summarize this alert
MITRE findings
Remediation steps
Knowledge graph
-
Lateral movement: DCOM execution through Excel (the PathWiper.exe aka WINPROJ.exe payload is launched by calling ActivateMicrosoftApp())
The final alert coincided with the lateral movement phase. Once the renamed file was in the correct system path, the attacker used DCOM to remotely execute it via Excel's ActivateMicrosoftApp() method. This enabled the malware to run without human intervention, thereby spreading the attack to other systems.
Trellix Wise provided a summarized alert, associated MITRE techniques, mitigation steps, and a graphical overview of how this action fit into the larger attack sequence (see Figures 21-24).
Summarize this alert
MITRE findings

Remediation steps
Knowledge graph
Conclusion
PathWiper is not just another piece of malware; it is a well-crafted tool that uses legitimate mechanisms such as volume dismounting and registry lookups to quietly infiltrate and wipe out systems. It avoids detection by imitating normal administrative activity until the ultimate damage has been done.
This emphasizes the importance of early visibility, which is where Trellix NDR comes in. Rather than relying on traditional alerts, it monitors your network for unusual behavior, such as remote Excel launches or malicious file copies. When these subtle signals are combined, they create a clear picture of an ongoing attack.
Trellix NDR not only identifies when an attack has occurred, but it also explains how and where it's happening, giving teams the time and insight they need to act before the attack becomes irreversible. That level of clarity is not only useful but also required when dealing with threats like PathWiper.
To learn more about the Trellix NDR platform, take our product tour to see it in action or read more by visiting this page.
Ref:- https://specterops.io/blog/2023/10/30/lateral-movement-abuse-the-power-of-dcom-excel-application/
https://blog.talosintelligence.com/pathwiper-targets-ukraine/
Discover the latest cybersecurity research from the Trellix Advanced Research Center: https://www.trellix.com/advanced-research-center/
RECENT NEWS
-
Mar 02, 2026
Trellix strengthens executive leadership team to accelerate cyber resilience vision
-
Feb 10, 2026
Trellix SecondSight actionable threat hunting strengthens cyber resilience
-
Dec 16, 2025
Trellix NDR Strengthens OT-IT Security Convergence
-
Dec 11, 2025
Trellix Finds 97% of CISOs Agree Hybrid Infrastructure Provides Greater Resilience
-
Oct 29, 2025
Trellix Announces No-Code Security Workflows for Faster Investigation and Response
RECENT STORIES
Latest from our newsroom
Get the latest
Stay up to date with the latest cybersecurity trends, best practices, security vulnerabilities, and so much more.
Zero spam. Unsubscribe at any time.
